Biohazard
端口扫描
root@ip-10-10-71-215:~/biohazard# nmap -sTCV -p 21,22,80 --min-rate 1000 10.10.18.40
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-13 02:24 BST
Nmap scan report for ip-10-10-18-40.eu-west-1.compute.internal (10.10.18.40)
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c9:03:aa:aa:ea:a9:f1:f4:09:79:c0:47:41:16:f1:9b (RSA)
| 256 2e:1d:83:11:65:03:b4:78:e9:6d:94:d1:3b:db:f4:d6 (ECDSA)
|_ 256 91:3d:e4:4f:ab:aa:e2:9e:44:af:d3:57:86:70:bc:39 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Beginning of the end
MAC Address: 02:94:10:79:9E:E9 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.82 seconds
80
这道题类似于迷宫解密就吧思路贴出来
21 - FTP
获得 ftp 密码之后进行登陆,在其中发现几个文件
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxrwx 2 1002 1002 4096 Sep 20 2019 .
drwxrwxrwx 2 1002 1002 4096 Sep 20 2019 ..
-rw-r--r-- 1 0 0 7994 Sep 19 2019 001-key.jpg
-rw-r--r-- 1 0 0 2210 Sep 19 2019 002-key.jpg
-rw-r--r-- 1 0 0 2146 Sep 19 2019 003-key.jpg
-rw-r--r-- 1 0 0 121 Sep 19 2019 helmet_key.txt.gpg
-rw-r--r-- 1 0 0 170 Sep 20 2019 important.txt
这三个照片存在文件隐写, 将其提取出来后进行解密 CyberChef 使用得到的内容作为 gpg 文件密码
┌──(jtz㉿JTZ)-[~/Desktop/Temp/thm/Biohazard/ftp]
└─$ gpg -d helmet_key.txt.gpg
gpg: AES256.CFB 加密过的数据
gpg: 以 1 个密码加密
helmet_key{458493193501d2b94bbab2e727f8db4b}
在查看 important.txt 文件时告诉我一个隐藏目录, 使用上面的 flag 作为 key 进行访问最终得到两个文件
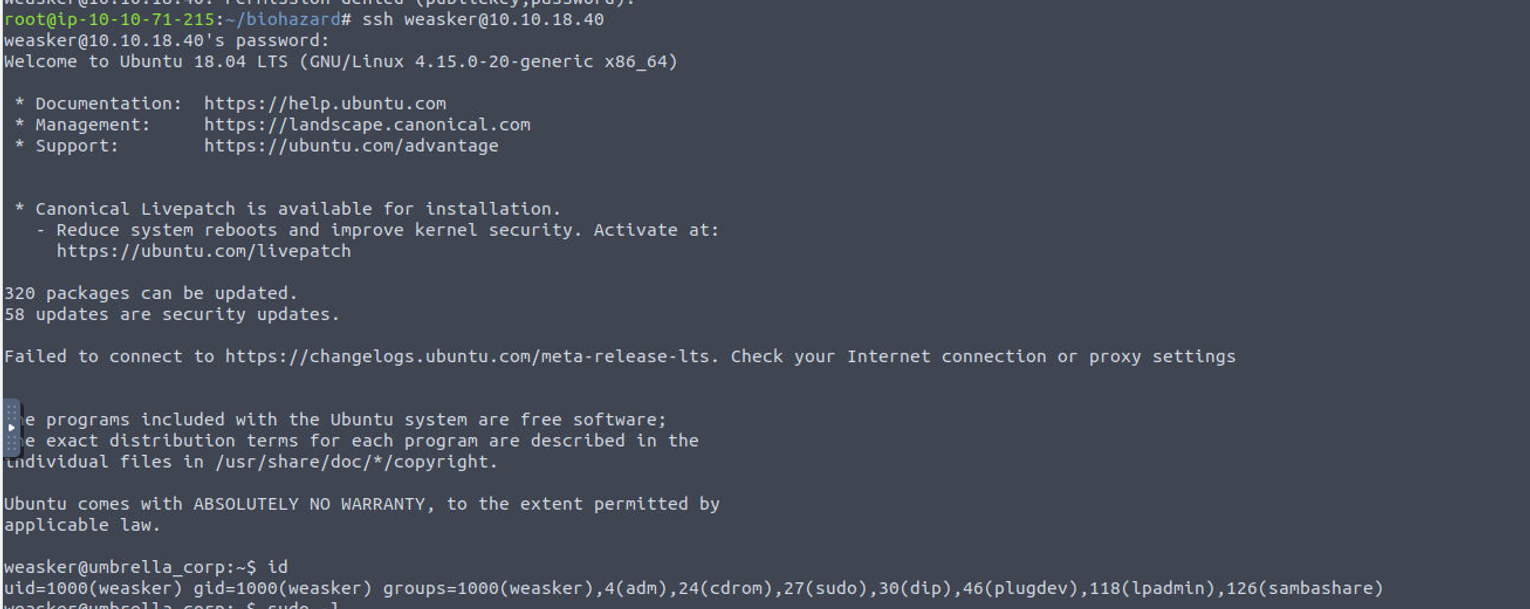
weasker login password, stars_members_are_my_guinea_pig
SSH password: T_virus_rules
后渗透
weasker
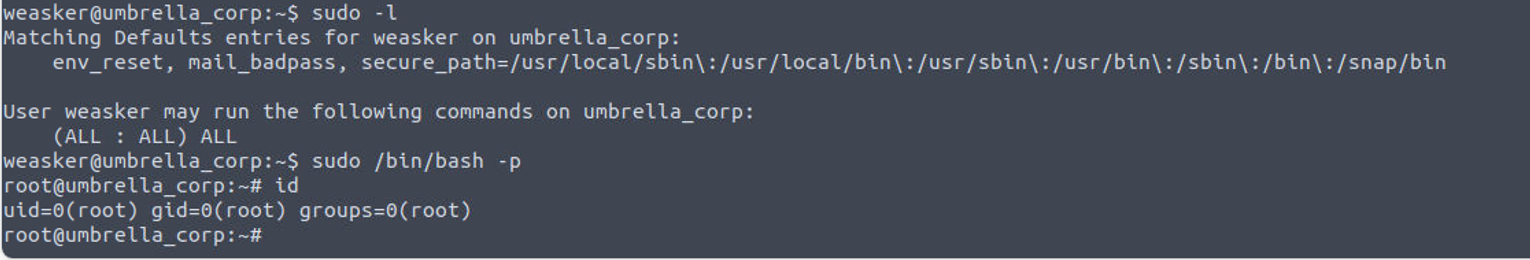
weasker —> root
用户具有 SUDO 特权直接执行即可